Hash Table Notes
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Linear Probing with Constant Independence
Linear Probing with Constant Independence Anna Pagh∗ Rasmus Pagh∗ Milan Ruˇzic´ ∗ ABSTRACT 1. INTRODUCTION Hashing with linear probing dates back to the 1950s, and Hashing with linear probing is perhaps the simplest algo- is among the most studied algorithms. In recent years it rithm for storing and accessing a set of keys that obtains has become one of the most important hash table organiza- nontrivial performance. Given a hash function h, a key x is tions since it uses the cache of modern computers very well. inserted in an array by searching for the first vacant array Unfortunately, previous analyses rely either on complicated position in the sequence h(x), h(x) + 1, h(x) + 2,... (Here, and space consuming hash functions, or on the unrealistic addition is modulo r, the size of the array.) Retrieval of a assumption of free access to a truly random hash function. key proceeds similarly, until either the key is found, or a Already Carter and Wegman, in their seminal paper on uni- vacant position is encountered, in which case the key is not versal hashing, raised the question of extending their anal- present in the data structure. Deletions can be performed ysis to linear probing. However, we show in this paper that by moving elements back in the probe sequence in a greedy linear probing using a pairwise independent family may have fashion (ensuring that no key x is moved beyond h(x)), until expected logarithmic cost per operation. On the positive a vacant array position is encountered. side, we show that 5-wise independence is enough to ensure Linear probing dates back to 1954, but was first analyzed constant expected time per operation. -

CSC 344 – Algorithms and Complexity Why Search?
CSC 344 – Algorithms and Complexity Lecture #5 – Searching Why Search? • Everyday life -We are always looking for something – in the yellow pages, universities, hairdressers • Computers can search for us • World wide web provides different searching mechanisms such as yahoo.com, bing.com, google.com • Spreadsheet – list of names – searching mechanism to find a name • Databases – use to search for a record • Searching thousands of records takes time the large number of comparisons slows the system Sequential Search • Best case? • Worst case? • Average case? Sequential Search int linearsearch(int x[], int n, int key) { int i; for (i = 0; i < n; i++) if (x[i] == key) return(i); return(-1); } Improved Sequential Search int linearsearch(int x[], int n, int key) { int i; //This assumes an ordered array for (i = 0; i < n && x[i] <= key; i++) if (x[i] == key) return(i); return(-1); } Binary Search (A Decrease and Conquer Algorithm) • Very efficient algorithm for searching in sorted array: – K vs A[0] . A[m] . A[n-1] • If K = A[m], stop (successful search); otherwise, continue searching by the same method in: – A[0..m-1] if K < A[m] – A[m+1..n-1] if K > A[m] Binary Search (A Decrease and Conquer Algorithm) l ← 0; r ← n-1 while l ≤ r do m ← (l+r)/2 if K = A[m] return m else if K < A[m] r ← m-1 else l ← m+1 return -1 Analysis of Binary Search • Time efficiency • Worst-case recurrence: – Cw (n) = 1 + Cw( n/2 ), Cw (1) = 1 solution: Cw(n) = log 2(n+1) 6 – This is VERY fast: e.g., Cw(10 ) = 20 • Optimal for searching a sorted array • Limitations: must be a sorted array (not linked list) binarySearch int binarySearch(int x[], int n, int key) { int low, high, mid; low = 0; high = n -1; while (low <= high) { mid = (low + high) / 2; if (x[mid] == key) return(mid); if (x[mid] > key) high = mid - 1; else low = mid + 1; } return(-1); } Searching Problem Problem: Given a (multi)set S of keys and a search key K, find an occurrence of K in S, if any. -

4 Hash Tables and Associative Arrays
4 FREE Hash Tables and Associative Arrays If you want to get a book from the central library of the University of Karlsruhe, you have to order the book in advance. The library personnel fetch the book from the stacks and deliver it to a room with 100 shelves. You find your book on a shelf numbered with the last two digits of your library card. Why the last digits and not the leading digits? Probably because this distributes the books more evenly among the shelves. The library cards are numbered consecutively as students sign up, and the University of Karlsruhe was founded in 1825. Therefore, the students enrolled at the same time are likely to have the same leading digits in their card number, and only a few shelves would be in use if the leadingCOPY digits were used. The subject of this chapter is the robust and efficient implementation of the above “delivery shelf data structure”. In computer science, this data structure is known as a hash1 table. Hash tables are one implementation of associative arrays, or dictio- naries. The other implementation is the tree data structures which we shall study in Chap. 7. An associative array is an array with a potentially infinite or at least very large index set, out of which only a small number of indices are actually in use. For example, the potential indices may be all strings, and the indices in use may be all identifiers used in a particular C++ program.Or the potential indices may be all ways of placing chess pieces on a chess board, and the indices in use may be the place- ments required in the analysis of a particular game. -

Implementing the Map ADT Outline
Implementing the Map ADT Outline ´ The Map ADT ´ Implementation with Java Generics ´ A Hash Function ´ translation of a string key into an integer ´ Consider a few strategies for implementing a hash table ´ linear probing ´ quadratic probing ´ separate chaining hashing ´ OrderedMap using a binary search tree The Map ADT ´A Map models a searchable collection of key-value mappings ´A key is said to be “mapped” to a value ´Also known as: dictionary, associative array ´Main operations: insert, find, and delete Applications ´ Store large collections with fast operations ´ For a long time, Java only had Vector (think ArrayList), Stack, and Hashmap (now there are about 67) ´ Support certain algorithms ´ for example, probabilistic text generation in 127B ´ Store certain associations in meaningful ways ´ For example, to store connected rooms in Hunt the Wumpus in 335 The Map ADT ´A value is "mapped" to a unique key ´Need a key and a value to insert new mappings ´Only need the key to find mappings ´Only need the key to remove mappings 5 Key and Value ´With Java generics, you need to specify ´ the type of key ´ the type of value ´Here the key type is String and the value type is BankAccount Map<String, BankAccount> accounts = new HashMap<String, BankAccount>(); 6 put(key, value) get(key) ´Add new mappings (a key mapped to a value): Map<String, BankAccount> accounts = new TreeMap<String, BankAccount>(); accounts.put("M",); accounts.put("G", new BankAcnew BankAccount("Michel", 111.11)count("Georgie", 222.22)); accounts.put("R", new BankAccount("Daniel", -

Prefix Hash Tree an Indexing Data Structure Over Distributed Hash
Prefix Hash Tree An Indexing Data Structure over Distributed Hash Tables Sriram Ramabhadran ∗ Sylvia Ratnasamy University of California, San Diego Intel Research, Berkeley Joseph M. Hellerstein Scott Shenker University of California, Berkeley International Comp. Science Institute, Berkeley and and Intel Research, Berkeley University of California, Berkeley ABSTRACT this lookup interface has allowed a wide variety of Distributed Hash Tables are scalable, robust, and system to be built on top DHTs, including file sys- self-organizing peer-to-peer systems that support tems [9, 27], indirection services [30], event notifi- exact match lookups. This paper describes the de- cation [6], content distribution networks [10] and sign and implementation of a Prefix Hash Tree - many others. a distributed data structure that enables more so- phisticated queries over a DHT. The Prefix Hash DHTs were designed in the Internet style: scala- Tree uses the lookup interface of a DHT to con- bility and ease of deployment triumph over strict struct a trie-based structure that is both efficient semantics. In particular, DHTs are self-organizing, (updates are doubly logarithmic in the size of the requiring no centralized authority or manual con- domain being indexed), and resilient (the failure figuration. They are robust against node failures of any given node in the Prefix Hash Tree does and easily accommodate new nodes. Most impor- not affect the availability of data stored at other tantly, they are scalable in the sense that both la- nodes). tency (in terms of the number of hops per lookup) and the local state required typically grow loga- Categories and Subject Descriptors rithmically in the number of nodes; this is crucial since many of the envisioned scenarios for DHTs C.2.4 [Comp. -

Hash Tables & Searching Algorithms
Search Algorithms and Tables Chapter 11 Tables • A table, or dictionary, is an abstract data type whose data items are stored and retrieved according to a key value. • The items are called records. • Each record can have a number of data fields. • The data is ordered based on one of the fields, named the key field. • The record we are searching for has a key value that is called the target. • The table may be implemented using a variety of data structures: array, tree, heap, etc. Sequential Search public static int search(int[] a, int target) { int i = 0; boolean found = false; while ((i < a.length) && ! found) { if (a[i] == target) found = true; else i++; } if (found) return i; else return –1; } Sequential Search on Tables public static int search(someClass[] a, int target) { int i = 0; boolean found = false; while ((i < a.length) && !found){ if (a[i].getKey() == target) found = true; else i++; } if (found) return i; else return –1; } Sequential Search on N elements • Best Case Number of comparisons: 1 = O(1) • Average Case Number of comparisons: (1 + 2 + ... + N)/N = (N+1)/2 = O(N) • Worst Case Number of comparisons: N = O(N) Binary Search • Can be applied to any random-access data structure where the data elements are sorted. • Additional parameters: first – index of the first element to examine size – number of elements to search starting from the first element above Binary Search • Precondition: If size > 0, then the data structure must have size elements starting with the element denoted as the first element. In addition, these elements are sorted. -

Introduction to Hash Table and Hash Function
Introduction to Hash Table and Hash Function This is a short introduction to Hashing mechanism Introduction Is it possible to design a search of O(1)– that is, one that has a constant search time, no matter where the element is located in the list? Let’s look at an example. We have a list of employees of a fairly small company. Each of 100 employees has an ID number in the range 0 – 99. If we store the elements (employee records) in the array, then each employee’s ID number will be an index to the array element where this employee’s record will be stored. In this case once we know the ID number of the employee, we can directly access his record through the array index. There is a one-to-one correspondence between the element’s key and the array index. However, in practice, this perfect relationship is not easy to establish or maintain. For example: the same company might use employee’s five-digit ID number as the primary key. In this case, key values run from 00000 to 99999. If we want to use the same technique as above, we need to set up an array of size 100,000, of which only 100 elements will be used: Obviously it is very impractical to waste that much storage. But what if we keep the array size down to the size that we will actually be using (100 elements) and use just the last two digits of key to identify each employee? For example, the employee with the key number 54876 will be stored in the element of the array with index 76. -

Balanced Search Trees and Hashing Balanced Search Trees
Advanced Implementations of Tables: Balanced Search Trees and Hashing Balanced Search Trees Binary search tree operations such as insert, delete, retrieve, etc. depend on the length of the path to the desired node The path length can vary from log2(n+1) to O(n) depending on how balanced or unbalanced the tree is The shape of the tree is determined by the values of the items and the order in which they were inserted CMPS 12B, UC Santa Cruz Binary searching & introduction to trees 2 Examples 10 40 20 20 60 30 40 10 30 50 70 50 Can you get the same tree with 60 different insertion orders? 70 CMPS 12B, UC Santa Cruz Binary searching & introduction to trees 3 2-3 Trees Each internal node has two or three children All leaves are at the same level 2 children = 2-node, 3 children = 3-node CMPS 12B, UC Santa Cruz Binary searching & introduction to trees 4 2-3 Trees (continued) 2-3 trees are not binary trees (duh) A 2-3 tree of height h always has at least 2h-1 nodes i.e. greater than or equal to a binary tree of height h A 2-3 tree with n nodes has height less than or equal to log2(n+1) i.e less than or equal to the height of a full binary tree with n nodes CMPS 12B, UC Santa Cruz Binary searching & introduction to trees 5 Definition of 2-3 Trees T is a 2-3 tree of height h if T is empty (height 0), OR T is of the form r TL TR Where r is a node that contains one data item and TL and TR are 2-3 trees, each of height h-1, and the search key of r is greater than any in TL and less than any in TR, OR CMPS 12B, UC Santa Cruz Binary searching & introduction to trees 6 Definition of 2-3 Trees (continued) T is of the form r TL TM TR Where r is a node that contains two data items and TL, TM, and TR are 2-3 trees, each of height h-1, and the smaller search key of r is greater than any in TL and less than any in TM and the larger search key in r is greater than any in TM and smaller than any in TR. -

Hash Tables Hash Tables a "Faster" Implementation for Map Adts
Hash Tables Hash Tables A "faster" implementation for Map ADTs Outline What is hash function? translation of a string key into an integer Consider a few strategies for implementing a hash table linear probing quadratic probing separate chaining hashing Big Ohs using different data structures for a Map ADT? Data Structure put get remove Unsorted Array Sorted Array Unsorted Linked List Sorted Linked List Binary Search Tree A BST was used in OrderedMap<K,V> Hash Tables Hash table: another data structure Provides virtually direct access to objects based on a key (a unique String or Integer) key could be your SID, your telephone number, social security number, account number, … Must have unique keys Each key is associated with–mapped to–a value Hashing Must convert keys such as "555-1234" into an integer index from 0 to some reasonable size Elements can be found, inserted, and removed using the integer index as an array index Insert (called put), find (get), and remove must use the same "address calculator" which we call the Hash function Hashing Can make String or Integer keys into integer indexes by "hashing" Need to take hashCode % array size Turn “S12345678” into an int 0..students.length Ideally, every key has a unique hash value Then the hash value could be used as an array index, however, Ideal is impossible Some keys will "hash" to the same integer index Known as a collision Need a way to handle collisions! "abc" may hash to the same integer array index as "cba" Hash Tables: Runtime Efficient Lookup time does not grow when n increases A hash table supports fast insertion O(1) fast retrieval O(1) fast removal O(1) Could use String keys each ASCII character equals some unique integer "able" = 97 + 98 + 108 + 101 == 404 Hash method works something like… Convert a String key into an integer that will be in the range of 0 through the maximum capacity-1 Assume the array capacity is 9997 hash(key) AAAAAAAA 8482 zzzzzzzz 1273 hash(key) A string of 8 chars Range: 0 .. -
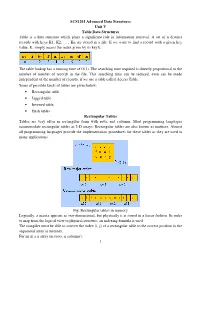
SCS1201 Advanced Data Structures Unit V Table Data Structures Table Is a Data Structure Which Plays a Significant Role in Information Retrieval
SCS1201 Advanced Data Structures Unit V Table Data Structures Table is a data structure which plays a significant role in information retrieval. A set of n distinct records with keys K1, K2, …., Kn are stored in a file. If we want to find a record with a given key value, K, simply access the index given by its key k. The table lookup has a running time of O(1). The searching time required is directly proportional to the number of number of records in the file. This searching time can be reduced, even can be made independent of the number of records, if we use a table called Access Table. Some of possible kinds of tables are given below: • Rectangular table • Jagged table • Inverted table. • Hash tables Rectangular Tables Tables are very often in rectangular form with rows and columns. Most programming languages accommodate rectangular tables as 2-D arrays. Rectangular tables are also known as matrices. Almost all programming languages provide the implementation procedures for these tables as they are used in many applications. Fig. Rectangular tables in memory Logically, a matrix appears as two-dimensional, but physically it is stored in a linear fashion. In order to map from the logical view to physical structure, an indexing formula is used. The compiler must be able to convert the index (i, j) of a rectangular table to the correct position in the sequential array in memory. For an m x n array (m rows, n columns): 1 Each row is indexed from 0 to m-1 Each column is indexed from 0 to n – 1 Item at (i, j) is at sequential position i * n + j Row major order: Assume that the base address is the first location of the memory, so the th Address a ij =storing all the elements in the first(i-1) rows + the number of elements in the i th row up to the j th coloumn = (i-1)*n+j Column major order: Address of a ij = storing all the elements in the first(j-1)th column + The number of elements in the j th column up to the i th rows. -

Pseudorandom Data and Universal Hashing∗
CS369N: Beyond Worst-Case Analysis Lecture #6: Pseudorandom Data and Universal Hashing∗ Tim Roughgardeny April 14, 2014 1 Motivation: Linear Probing and Universal Hashing This lecture discusses a very neat paper of Mitzenmacher and Vadhan [8], which proposes a robust measure of “sufficiently random data" and notes interesting consequences for hashing and some related applications. We consider hash functions from N = f0; 1gn to M = f0; 1gm. Canonically, m is much smaller than n. We abuse notation and use N; M to denote both the sets and the cardinalities of the sets. Since a hash function h : N ! M is effectively compressing a larger set into a smaller one, collisions (distinct elements x; y 2 N with h(x) = h(y)) are inevitable. There are many way of resolving collisions. One that is common in practice is linear probing, where given a data element x, one starts at the slot h(x), and then proceeds to h(x) + 1, h(x) + 2, etc. until a suitable slot is found. (Either an empty slot if the goal is to insert x; or a slot that contains x if the goal is to search for x.) The linear search wraps around the table (from slot M − 1 back to 0), if needed. Linear probing interacts well with caches and prefetching, which can be a big win in some application. Recall that every fixed hash function performs badly on some data set, since by the Pigeonhole Principle there is a large data set of elements with equal hash values. Thus the analysis of hashing always involves some kind of randomization, either in the input or in the hash function. -

Collisions There Is Still a Problem with Our Current Hash Table
18.1 Hashing 1061 Since our mapping from element value to preferred index now has a bit of com- plexity to it, we might turn it into a method that accepts the element value as a parameter and returns the right index for that value. Such a method is referred to as a hash function , and an array that uses such a function to govern insertion and deletion of its elements is called a hash table . The individual indexes in the hash table are also sometimes informally called buckets . Our hash function so far is the following: private int hashFunction(int value) { return Math.abs(value) % elementData.length; } Hash Function A method for rapidly mapping between element values and preferred array indexes at which to store those values. Hash Table An array that stores its elements in indexes produced by a hash function. Collisions There is still a problem with our current hash table. Because our hash function wraps values to fit in the array bounds, it is now possible that two values could have the same preferred index. For example, if we try to insert 45 into the hash table, it maps to index 5, conflicting with the existing value 5. This is called a collision . Our imple- mentation is incomplete until we have a way of dealing with collisions. If the client tells the set to insert 45 , the value 45 must be added to the set somewhere; it’s up to us to decide where to put it. Collision When two or more element values in a hash table produce the same result from its hash function, indicating that they both prefer to be stored in the same index of the table.