Open Final Thesis.Pdf
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Instrumental Regression in Partially Linear Models
10-167 Research Group: Econometrics and Statistics September, 2009 Instrumental Regression in Partially Linear Models JEAN-PIERRE FLORENS, JAN JOHANNES AND SEBASTIEN VAN BELLEGEM INSTRUMENTAL REGRESSION IN PARTIALLY LINEAR MODELS∗ Jean-Pierre Florens1 Jan Johannes2 Sebastien´ Van Bellegem3 First version: January 24, 2008. This version: September 10, 2009 Abstract We consider the semiparametric regression Xtβ+φ(Z) where β and φ( ) are unknown · slope coefficient vector and function, and where the variables (X,Z) are endogeneous. We propose necessary and sufficient conditions for the identification of the parameters in the presence of instrumental variables. We also focus on the estimation of β. An incorrect parameterization of φ may generally lead to an inconsistent estimator of β, whereas even consistent nonparametric estimators for φ imply a slow rate of convergence of the estimator of β. An additional complication is that the solution of the equation necessitates the inversion of a compact operator that has to be estimated nonparametri- cally. In general this inversion is not stable, thus the estimation of β is ill-posed. In this paper, a √n-consistent estimator for β is derived under mild assumptions. One of these assumptions is given by the so-called source condition that is explicitly interprated in the paper. Finally we show that the estimator achieves the semiparametric efficiency bound, even if the model is heteroscedastic. Monte Carlo simulations demonstrate the reasonable performance of the estimation procedure on finite samples. Keywords: Partially linear model, semiparametric regression, instrumental variables, endo- geneity, ill-posed inverse problem, Tikhonov regularization, root-N consistent estimation, semiparametric efficiency bound JEL classifications: Primary C14; secondary C30 ∗We are grateful to R. -
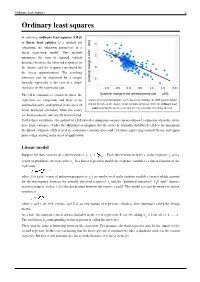
Ordinary Least Squares 1 Ordinary Least Squares
Ordinary least squares 1 Ordinary least squares In statistics, ordinary least squares (OLS) or linear least squares is a method for estimating the unknown parameters in a linear regression model. This method minimizes the sum of squared vertical distances between the observed responses in the dataset and the responses predicted by the linear approximation. The resulting estimator can be expressed by a simple formula, especially in the case of a single regressor on the right-hand side. The OLS estimator is consistent when the regressors are exogenous and there is no Okun's law in macroeconomics states that in an economy the GDP growth should multicollinearity, and optimal in the class of depend linearly on the changes in the unemployment rate. Here the ordinary least squares method is used to construct the regression line describing this law. linear unbiased estimators when the errors are homoscedastic and serially uncorrelated. Under these conditions, the method of OLS provides minimum-variance mean-unbiased estimation when the errors have finite variances. Under the additional assumption that the errors be normally distributed, OLS is the maximum likelihood estimator. OLS is used in economics (econometrics) and electrical engineering (control theory and signal processing), among many areas of application. Linear model Suppose the data consists of n observations { y , x } . Each observation includes a scalar response y and a i i i vector of predictors (or regressors) x . In a linear regression model the response variable is a linear function of the i regressors: where β is a p×1 vector of unknown parameters; ε 's are unobserved scalar random variables (errors) which account i for the discrepancy between the actually observed responses y and the "predicted outcomes" x′ β; and ′ denotes i i matrix transpose, so that x′ β is the dot product between the vectors x and β. -

Linear Regression
DATA MINING 2 Linear and Logistic Regression Riccardo Guidotti a.a. 2019/2020 Regression • Given a dataset containing N observations Xi, Yi i = 1, 2, …, N • Regression is the task of learning a target function f that maps each input attribute set X into a output Y. • The goal is to find the target function that can fit the input data with minimum error. • The error function can be expressed as • Absolute Error = ∑! |�! − �(�!)| " • Squared Error = ∑!(�! − � �! ) residuals Linear Regression Y • Linear regression is a linear approach to modeling the relationship between a dependent variable Y and one or more independent (explanatory) variables X. • The case of one explanatory variable is called simple linear regression. • For more than one explanatory variable, the process is called multiple linear X regression. • For multiple correlated dependent variables, the process is called multivariate linear regression. What does it mean to predict Y? • Look at X = 5. There are many different Y values at X=5. • When we say predict Y at X =5, we are really asking: • What is the expected value (average) of Y at X = 5? What does it mean to predict Y? • Formally, the regression function is given by E(Y|X=x). This is the expected value of Y at X=x. • The ideal or optimal predictor of Y based on X is thus • f(X) = E(Y | X=x) Simple Linear Regression Dependent Independent Variable Variable Linear Model: Y = mX + b � = �!� + �" Slope Intercept (bias) • In general, such a relationship may not hold exactly for the largely unobserved population • We call the unobserved deviations from Y the errors. -

PARAMETER DETERMINATION for TIKHONOV REGULARIZATION PROBLEMS in GENERAL FORM∗ 1. Introduction. We Are Concerned with the Solut
PARAMETER DETERMINATION FOR TIKHONOV REGULARIZATION PROBLEMS IN GENERAL FORM∗ Y. PARK† , L. REICHEL‡ , G. RODRIGUEZ§ , AND X. YU¶ Abstract. Tikhonov regularization is one of the most popular methods for computing an approx- imate solution of linear discrete ill-posed problems with error-contaminated data. A regularization parameter λ > 0 balances the influence of a fidelity term, which measures how well the data are approximated, and of a regularization term, which dampens the propagation of the data error into the computed approximate solution. The value of the regularization parameter is important for the quality of the computed solution: a too large value of λ > 0 gives an over-smoothed solution that lacks details that the desired solution may have, while a too small value yields a computed solution that is unnecessarily, and possibly severely, contaminated by propagated error. When a fairly ac- curate estimate of the norm of the error in the data is known, a suitable value of λ often can be determined with the aid of the discrepancy principle. This paper is concerned with the situation when the discrepancy principle cannot be applied. It then can be quite difficult to determine a suit- able value of λ. We consider the situation when the Tikhonov regularization problem is in general form, i.e., when the regularization term is determined by a regularization matrix different from the identity, and describe an extension of the COSE method for determining the regularization param- eter λ in this situation. This method has previously been discussed for Tikhonov regularization in standard form, i.e., for the situation when the regularization matrix is the identity. -

Multiple Discriminant Analysis
1 MULTIPLE DISCRIMINANT ANALYSIS DR. HEMAL PANDYA 2 INTRODUCTION • The original dichotomous discriminant analysis was developed by Sir Ronald Fisher in 1936. • Discriminant Analysis is a Dependence technique. • Discriminant Analysis is used to predict group membership. • This technique is used to classify individuals/objects into one of alternative groups on the basis of a set of predictor variables (Independent variables) . • The dependent variable in discriminant analysis is categorical and on a nominal scale, whereas the independent variables are either interval or ratio scale in nature. • When there are two groups (categories) of dependent variable, it is a case of two group discriminant analysis. • When there are more than two groups (categories) of dependent variable, it is a case of multiple discriminant analysis. 3 INTRODUCTION • Discriminant Analysis is applicable in situations in which the total sample can be divided into groups based on a non-metric dependent variable. • Example:- male-female - high-medium-low • The primary objective of multiple discriminant analysis are to understand group differences and to predict the likelihood that an entity (individual or object) will belong to a particular class or group based on several independent variables. 4 ASSUMPTIONS OF DISCRIMINANT ANALYSIS • NO Multicollinearity • Multivariate Normality • Independence of Observations • Homoscedasticity • No Outliers • Adequate Sample Size • Linearity (for LDA) 5 ASSUMPTIONS OF DISCRIMINANT ANALYSIS • The assumptions of discriminant analysis are as under. The analysis is quite sensitive to outliers and the size of the smallest group must be larger than the number of predictor variables. • Non-Multicollinearity: If one of the independent variables is very highly correlated with another, or one is a function (e.g., the sum) of other independents, then the tolerance value for that variable will approach 0 and the matrix will not have a unique discriminant solution. -

An Overview and Application of Discriminant Analysis in Data Analysis
IOSR Journal of Mathematics (IOSR-JM) e-ISSN: 2278-5728, p-ISSN: 2319-765X. Volume 11, Issue 1 Ver. V (Jan - Feb. 2015), PP 12-15 www.iosrjournals.org An Overview and Application of Discriminant Analysis in Data Analysis Alayande, S. Ayinla1 Bashiru Kehinde Adekunle2 Department of Mathematical Sciences College of Natural Sciences Redeemer’s University Mowe, Redemption City Ogun state, Nigeria Department of Mathematical and Physical science College of Science, Engineering &Technology Osun State University Abstract: The paper shows that Discriminant analysis as a general research technique can be very useful in the investigation of various aspects of a multi-variate research problem. It is sometimes preferable than logistic regression especially when the sample size is very small and the assumptions are met. Application of it to the failed industry in Nigeria shows that the derived model appeared outperform previous model build since the model can exhibit true ex ante predictive ability for a period of about 3 years subsequent. Keywords: Factor Analysis, Multiple Discriminant Analysis, Multicollinearity I. Introduction In different areas of applications the term "discriminant analysis" has come to imply distinct meanings, uses, roles, etc. In the fields of learning, psychology, guidance, and others, it has been used for prediction (e.g., Alexakos, 1966; Chastian, 1969; Stahmann, 1969); in the study of classroom instruction it has been used as a variable reduction technique (e.g., Anderson, Walberg, & Welch, 1969); and in various fields it has been used as an adjunct to MANOVA (e.g., Saupe, 1965; Spain & D'Costa, Note 2). The term is now beginning to be interpreted as a unified approach in the solution of a research problem involving a com-parison of two or more populations characterized by multi-response data. -

Linear Regression
eesc BC 3017 statistics notes 1 LINEAR REGRESSION Systematic var iation in the true value Up to now, wehav e been thinking about measurement as sampling of values from an ensemble of all possible outcomes in order to estimate the true value (which would, according to our previous discussion, be well approximated by the mean of a very large sample). Givenasample of outcomes, we have sometimes checked the hypothesis that it is a random sample from some ensemble of outcomes, by plotting the data points against some other variable, such as ordinal position. Under the hypothesis of random selection, no clear trend should appear.Howev er, the contrary case, where one finds a clear trend, is very important. Aclear trend can be a discovery,rather than a nuisance! Whether it is adiscovery or a nuisance (or both) depends on what one finds out about the reasons underlying the trend. In either case one must be prepared to deal with trends in analyzing data. Figure 2.1 (a) shows a plot of (hypothetical) data in which there is a very clear trend. The yaxis scales concentration of coliform bacteria sampled from rivers in various regions (units are colonies per liter). The x axis is a hypothetical indexofregional urbanization, ranging from 1 to 10. The hypothetical data consist of 6 different measurements at each levelofurbanization. The mean of each set of 6 measurements givesarough estimate of the true value for coliform bacteria concentration for rivers in a region with that urbanization level. The jagged dark line drawn on the graph connects these estimates of true value and makes the trend quite clear: more extensive urbanization is associated with higher true values of bacteria concentration. -

Statistical Foundations of Data Science
Statistical Foundations of Data Science Jianqing Fan Runze Li Cun-Hui Zhang Hui Zou i Preface Big data are ubiquitous. They come in varying volume, velocity, and va- riety. They have a deep impact on systems such as storages, communications and computing architectures and analysis such as statistics, computation, op- timization, and privacy. Engulfed by a multitude of applications, data science aims to address the large-scale challenges of data analysis, turning big data into smart data for decision making and knowledge discoveries. Data science integrates theories and methods from statistics, optimization, mathematical science, computer science, and information science to extract knowledge, make decisions, discover new insights, and reveal new phenomena from data. The concept of data science has appeared in the literature for several decades and has been interpreted differently by different researchers. It has nowadays be- come a multi-disciplinary field that distills knowledge in various disciplines to develop new methods, processes, algorithms and systems for knowledge dis- covery from various kinds of data, which can be either low or high dimensional, and either structured, unstructured or semi-structured. Statistical modeling plays critical roles in the analysis of complex and heterogeneous data and quantifies uncertainties of scientific hypotheses and statistical results. This book introduces commonly-used statistical models, contemporary sta- tistical machine learning techniques and algorithms, along with their mathe- matical insights and statistical theories. It aims to serve as a graduate-level textbook on the statistical foundations of data science as well as a research monograph on sparsity, covariance learning, machine learning and statistical inference. For a one-semester graduate level course, it may cover Chapters 2, 3, 9, 10, 12, 13 and some topics selected from the remaining chapters. -

S41598-018-25035-1.Pdf
www.nature.com/scientificreports OPEN An Innovative Approach for The Integration of Proteomics and Metabolomics Data In Severe Received: 23 October 2017 Accepted: 9 April 2018 Septic Shock Patients Stratifed for Published: xx xx xxxx Mortality Alice Cambiaghi1, Ramón Díaz2, Julia Bauzá Martinez2, Antonia Odena2, Laura Brunelli3, Pietro Caironi4,5, Serge Masson3, Giuseppe Baselli1, Giuseppe Ristagno 3, Luciano Gattinoni6, Eliandre de Oliveira2, Roberta Pastorelli3 & Manuela Ferrario 1 In this work, we examined plasma metabolome, proteome and clinical features in patients with severe septic shock enrolled in the multicenter ALBIOS study. The objective was to identify changes in the levels of metabolites involved in septic shock progression and to integrate this information with the variation occurring in proteins and clinical data. Mass spectrometry-based targeted metabolomics and untargeted proteomics allowed us to quantify absolute metabolites concentration and relative proteins abundance. We computed the ratio D7/D1 to take into account their variation from day 1 (D1) to day 7 (D7) after shock diagnosis. Patients were divided into two groups according to 28-day mortality. Three diferent elastic net logistic regression models were built: one on metabolites only, one on metabolites and proteins and one to integrate metabolomics and proteomics data with clinical parameters. Linear discriminant analysis and Partial least squares Discriminant Analysis were also implemented. All the obtained models correctly classifed the observations in the testing set. By looking at the variable importance (VIP) and the selected features, the integration of metabolomics with proteomics data showed the importance of circulating lipids and coagulation cascade in septic shock progression, thus capturing a further layer of biological information complementary to metabolomics information. -

Regularized Radial Basis Function Models for Stochastic Simulation
Proceedings of the 2014 Winter Simulation Conference A. Tolk, S. Y. Diallo, I. O. Ryzhov, L. Yilmaz, S. Buckley, and J. A. Miller, eds. REGULARIZED RADIAL BASIS FUNCTION MODELS FOR STOCHASTIC SIMULATION Yibo Ji Sujin Kim Department of Industrial and Systems Engineering National University of Singapore 119260, Singapore ABSTRACT We propose a new radial basis function (RBF) model for stochastic simulation, called regularized RBF (R-RBF). We construct the R-RBF model by minimizing a regularized loss over a reproducing kernel Hilbert space (RKHS) associated with RBFs. The model can flexibly incorporate various types of RBFs including those with conditionally positive definite basis. To estimate the model prediction error, we first represent the RKHS as a stochastic process associated to the RBFs. We then show that the prediction model obtained from the stochastic process is equivalent to the R-RBF model and derive the associated mean squared error. We propose a new criterion for efficient parameter estimation based on the closed form of the leave-one-out cross validation error for R-RBF models. Numerical results show that R-RBF models are more robust, and yet fairly accurate compared to stochastic kriging models. 1 INTRODUCTION In this paper, we aim to develop a radial basis function (RBF) model to approximate a real-valued smooth function using noisy observations obtained via black-box simulations. The observations are assumed to capture the information on the true function f through the commonly-used additive error model, d y = f (x) + e(x); x 2 X ⊂ R ; 2 where the random noise is characterized by a normal random variable e(x) ∼ N 0;se (x) , whose variance is determined by a continuously differentiable variance function se : X ! R. -

Simple Linear Regression
The simple linear model Represents the dependent variable, yi, as a linear function of one Regression Analysis: Basic Concepts independent variable, xi, subject to a random “disturbance” or “error”, ui. yi β0 β1xi ui = + + Allin Cottrell The error term ui is assumed to have a mean value of zero, a constant variance, and to be uncorrelated with its own past values (i.e., it is “white noise”). The task of estimation is to determine regression coefficients βˆ0 and βˆ1, estimates of the unknown parameters β0 and β1 respectively. The estimated equation will have the form yˆi βˆ0 βˆ1x = + 1 OLS Picturing the residuals The basic technique for determining the coefficients βˆ0 and βˆ1 is Ordinary Least Squares (OLS). Values for the coefficients are chosen to minimize the sum of the ˆ ˆ squared estimated errors or residual sum of squares (SSR). The β0 β1x + estimated error associated with each pair of data-values (xi, yi) is yi uˆ defined as i uˆi yi yˆi yi βˆ0 βˆ1xi yˆi = − = − − We use a different symbol for this estimated error (uˆi) as opposed to the “true” disturbance or error term, (ui). These two coincide only if βˆ0 and βˆ1 happen to be exact estimates of the regression parameters α and β. The estimated errors are also known as residuals . The SSR may be written as xi 2 2 2 SSR uˆ (yi yˆi) (yi βˆ0 βˆ1xi) = i = − = − − Σ Σ Σ The residual, uˆi, is the vertical distance between the actual value of the dependent variable, yi, and the fitted value, yˆi βˆ0 βˆ1xi. -

Multicollinearity Diagnostics in Statistical Modeling and Remedies to Deal with It Using SAS
Multicollinearity Diagnostics in Statistical Modeling and Remedies to deal with it using SAS Harshada Joshi Session SP07 - PhUSE 2012 www.cytel.com 1 Agenda • What is Multicollinearity? • How to Detect Multicollinearity? Examination of Correlation Matrix Variance Inflation Factor Eigensystem Analysis of Correlation Matrix • Remedial Measures Ridge Regression Principal Component Regression www.cytel.com 2 What is Multicollinearity? • Multicollinearity is a statistical phenomenon in which there exists a perfect or exact relationship between the predictor variables. • When there is a perfect or exact relationship between the predictor variables, it is difficult to come up with reliable estimates of their individual coefficients. • It will result in incorrect conclusions about the relationship between outcome variable and predictor variables. www.cytel.com 3 What is Multicollinearity? Recall that the multiple linear regression is Y = Xβ + ϵ; Where, Y is an n x 1 vector of responses, X is an n x p matrix of the predictor variables, β is a p x 1 vector of unknown constants, ϵ is an n x 1 vector of random errors, 2 with ϵi ~ NID (0, σ ) www.cytel.com 4 What is Multicollinearity? • Multicollinearity inflates the variances of the parameter estimates and hence this may lead to lack of statistical significance of individual predictor variables even though the overall model may be significant. • The presence of multicollinearity can cause serious problems with the estimation of β and the interpretation. www.cytel.com 5 How to detect Multicollinearity? 1. Examination of Correlation Matrix 2. Variance Inflation Factor (VIF) 3. Eigensystem Analysis of Correlation Matrix www.cytel.com 6 How to detect Multicollinearity? 1.