Heap Overflows and Double-Free Attacks
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Architecture of Decentvm
The Architecture of the DecentVM Towards a Decentralized Virtual Machine for Many-Core Computing Annette Bieniusa Johannes Eickhold Thomas Fuhrmann University of Freiburg, Germany Technische Universitat¨ Munchen,¨ Germany [email protected] fjeick,[email protected] Abstract We have accomplished these goals by combining an off-line Fully decentralized systems avoid bottlenecks and single points transcoder with a virtual machine that executes modified bytecode. of failure. Thus, they can provide excellent scalability and very The transcoder performs the verification and statically links the robust operation. The DecentVM is a fully decentralized, distributed required classes of an application or library. Thereby, the resulting virtual machine. Its simplified instruction set allows for a small binary – a so-called blob – is significantly smaller than the original VM code footprint. Its partitioned global address space (PGAS) class files, and its execution requires a significantly less complex memory model helps to easily create a single system image (SSI) virtual machine. Both these effects result in the low memory across many processors and processor cores. Originally, the VM was footprint of DecentVM. designed for networks of embedded 8-bit processors. Meanwhile, All libraries that are required by an application are identified via it also aims at clusters of many core processors. This paper gives a cryptographic hashes. Thus, an application’s code can be deployed brief overview of the DecentVM architecture. as if it was a statically linked executable. The software vendor can thus test the executable as it runs on the customer site without Categories and Subject Descriptors C.1.4 [Processor Architec- interference from different library versions. -

Dynamically Loaded Classes As Shared Libraries: an Approach to Improving Virtual Machine Scalability
Dynamically Loaded Classes as Shared Libraries: an Approach to Improving Virtual Machine Scalability Bernard Wong Grzegorz Czajkowski Laurent Daynès University of Waterloo Sun Microsystems Laboratories 200 University Avenue W. 2600 Casey Avenue Waterloo, Ontario N2L 3G1, Canada Mountain View, CA 94043, USA [email protected] {grzegorz.czajkowski, laurent.daynes}@sun.com Abstract machines sold today have sufficient amount of memory to hold a few instances of the Java virtual machine (JVMTM) Sharing selected data structures among virtual [2]. However, on servers hosting many applications, it is machines of a safe language can improve resource common to have many instances of the JVM running utilization of each participating run-time system. The simultaneously, often for lengthy periods of time. challenge is to determine what to share and how to share Aggregate memory requirement can therefore be large, it in order to decrease start-up time and lower memory and meeting it by adding more memory is not always an footprint without compromising the robustness of the option. In these settings, overall memory footprint must be system. Furthermore, the engineering effort required to kept to a minimum. For personal computer users, the main implement the system must not be prohibitive. This paper irritation is due to long start-up time, as they expect good demonstrates an approach that addresses these concerns TM responsiveness from interactive applications, which in in the context of the Java virtual machine. Our system contrast is of little importance in enterprise computing. transforms packages into shared libraries containing C/C++ programs typically do not suffer from excessive classes in a format matching the internal representation memory footprint or lengthy start-up time. -

Proceedings of the Third Virtual Machine Research and Technology Symposium
USENIX Association Proceedings of the Third Virtual Machine Research and Technology Symposium San Jose, CA, USA May 6–7, 2004 © 2004 by The USENIX Association All Rights Reserved For more information about the USENIX Association: Phone: 1 510 528 8649 FAX: 1 510 548 5738 Email: [email protected] WWW: http://www.usenix.org Rights to individual papers remain with the author or the author's employer. Permission is granted for noncommercial reproduction of the work for educational or research purposes. This copyright notice must be included in the reproduced paper. USENIX acknowledges all trademarks herein. MCI-Java: A Modified Java Virtual Machine Approach to Multiple Code Inheritance Maria Cutumisu, Calvin Chan, Paul Lu and Duane Szafron Department of Computing Science, University of Alberta {meric, calvinc, paullu, duane}@cs.ualberta.ca Abstract Java has multiple inheritance of interfaces, but only single inheritance of code via classes. This situation results in duplicated code in Java library classes and application code. We describe a generalization to the Java language syntax and the Java Virtual Machine (JVM) to support multiple inheritance of code, called MCI-Java. Our approach places multiply-inherited code in a new language construct called an implementation, which lies between an interface and a class in the inheritance hierarchy. MCI-Java does not support multiply-inherited data, which can cause modeling and performance problems. The MCI-Java extension is implemented by making minimal changes to the Java syntax, small changes to a compiler (IBM Jikes), and modest localized changes to a JVM (SUN JDK 1.2.2). The JVM changes result in no measurable performance overhead in real applications. -

Design and Implementation of a Scala Compiler Backend Targeting the Low Level Virtual Machine Geoffrey Reedy
University of New Mexico UNM Digital Repository Computer Science ETDs Engineering ETDs 5-1-2014 Design and Implementation of a Scala Compiler Backend Targeting the Low Level Virtual Machine Geoffrey Reedy Follow this and additional works at: https://digitalrepository.unm.edu/cs_etds Recommended Citation Reedy, Geoffrey. "Design and Implementation of a Scala Compiler Backend Targeting the Low Level Virtual Machine." (2014). https://digitalrepository.unm.edu/cs_etds/67 This Thesis is brought to you for free and open access by the Engineering ETDs at UNM Digital Repository. It has been accepted for inclusion in Computer Science ETDs by an authorized administrator of UNM Digital Repository. For more information, please contact [email protected]. Geoffrey Reedy Candidate Computer Science Department This thesis is approved, and it is acceptable in quality and form for publication: Approved by the Thesis Committee: Darko Stefanovic , Chairperson Jed Crandall Matthew Lakin Design and Implementation of a Scala Compiler Backend Targeting the Low Level Virtual Machine by Geoffrey Reedy B.S., Computer Science, University of Missouri — Rolla, 2004 THESIS Submitted in Partial Fulfillment of the Requirements for the Degree of Master of Science Computer Science The University of New Mexico Albuquerque, New Mexico May, 2014 ©2014, Geoffrey Reedy iii Design and Implementation of a Scala Compiler Backend Targeting the Low Level Virtual Machine by Geoffrey Reedy B.S., Computer Science, University of Missouri — Rolla, 2004 M.S., Computer Science, University of New Mexico, 2014 Abstract The Scala programming language successfully blends object-oriented and functional programming. The current implementation of Scala is tied to the Java Virtual Machine (JVM) which constrains the implementation and deployment targets. -

Java and C CSE351, Summer 2018
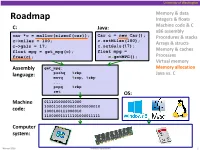
L23: Java and C CSE351, Summer 2018 Java and C CSE 351 Summer 2018 Instructor: Justin Hsia Teaching Assistants: Josie Lee Natalie Andreeva Teagan Horkan https://xkcd.com/801/ L23: Java and C CSE351, Summer 2018 Administrivia Lab 5 due Friday (8/17) at 11:59 pm . Hard deadline Course evaluations now open . See Piazza post @120 for links Final Exam: Friday in lecture . Review Session: Wed, 8/15, 5‐6:30 pm in EEB 045 . You get ONE double‐sided handwritten 8.5 11” cheat sheet 2 L23: Java and C CSE351, Summer 2018 Roadmap C: Java: Memory & data car *c = malloc(sizeof(car)); Car c = new Car(); Integers & floats c->miles = 100; c.setMiles(100); x86 assembly c->gals = 17; c.setGals(17); Procedures & stacks float mpg = get_mpg(c); float mpg = Executables free(c); c.getMPG(); Arrays & structs Memory & caches Assembly get_mpg: Processes language: pushq %rbp movq %rsp, %rbp Virtual memory ... Memory allocation popq %rbp Java vs. C ret OS: Machine 0111010000011000 100011010000010000000010 code: 1000100111000010 110000011111101000011111 Computer system: 3 L23: Java and C CSE351, Summer 2018 Java vs. C Reconnecting to Java (hello CSE143!) . But now you know a lot more about what really happens when we execute programs We’ve learned about the following items in C; now we’ll see what they look like for Java: . Representation of data . Pointers / references . Casting . Function / method calls including dynamic dispatch 4 L23: Java and C CSE351, Summer 2018 Worlds Colliding CSE351 has given you a “really different feeling” about what computers do and how programs execute We have occasionally contrasted to Java, but CSE143 may still feel like “a different world” . -

CSE 220: Systems Programming
Memory Allocation CSE 220: Systems Programming Ethan Blanton Department of Computer Science and Engineering University at Buffalo Introduction The Heap Void Pointers The Standard Allocator Allocation Errors Summary Allocating Memory We have seen how to use pointers to address: An existing variable An array element from a string or array constant This lecture will discuss requesting memory from the system. © 2021 Ethan Blanton / CSE 220: Systems Programming 2 Introduction The Heap Void Pointers The Standard Allocator Allocation Errors Summary Memory Lifetime All variables we have seen so far have well-defined lifetime: They persist for the entire life of the program They persist for the duration of a single function call Sometimes we need programmer-controlled lifetime. © 2021 Ethan Blanton / CSE 220: Systems Programming 3 Introduction The Heap Void Pointers The Standard Allocator Allocation Errors Summary Examples int global ; /* Lifetime of program */ void foo () { int x; /* Lifetime of foo () */ } Here, global is statically allocated: It is allocated by the compiler It is created when the program starts It disappears when the program exits © 2021 Ethan Blanton / CSE 220: Systems Programming 4 Introduction The Heap Void Pointers The Standard Allocator Allocation Errors Summary Examples int global ; /* Lifetime of program */ void foo () { int x; /* Lifetime of foo () */ } Whereas x is automatically allocated: It is allocated by the compiler It is created when foo() is called ¶ It disappears when foo() returns © 2021 Ethan Blanton / CSE 220: Systems Programming 5 Introduction The Heap Void Pointers The Standard Allocator Allocation Errors Summary The Heap The heap represents memory that is: allocated and released at run time managed explicitly by the programmer only obtainable by address Heap memory is just a range of bytes to C. -

G22.2110-003 Programming Languages - Fall 2012 Lecture 12
G22.2110-003 Programming Languages - Fall 2012 Lecture 12 Thomas Wies New York University Review Last lecture I Modules Outline I Classes I Encapsulation and Inheritance I Initialization and Finalization I Dynamic Method Binding I Abstract Classes I Simulating First-Class Functions Sources: I PLP, ch. 9 I PLP, ch. 3.6.3 What is OOP? (part I) The object idea: I bundling of data (data members) and operations (methods) on that data I restricting access to the data An object contains: I data members: arranged as a set of named fields I methods: routines which take the object they are associated with as an argument (known as member functions in C++) A class is a construct which defines the data and methods associated with all of its instances (objects). What is OOP? (part II) The inheritance and dynamic binding ideas: I inheritance: classes can be extended: I by adding new fields I by adding new methods I by overriding existing methods (changing behavior) If class B extends class A, we say that B is a subclass (or a derived or child class) of A, and A is a superclass (or a base or a parent class) of B. I dynamic binding: wherever an instance of a class is required, we can also use an instance of any of its subclasses; when we call one of its methods, the overridden versions are used. Information Hiding in Classes Like modules, classes can restrict access to their data and methods. Unlike modules, classes must take inheritance into account in their access control. -
Memory Allocation Pushq %Rbp Java Vs
University of Washington Memory & data Roadmap Integers & floats C: Java: Machine code & C x86 assembly car *c = malloc(sizeof(car)); Car c = new Car(); Procedures & stacks c.setMiles(100); c->miles = 100; Arrays & structs c->gals = 17; c.setGals(17); float mpg = get_mpg(c); float mpg = Memory & caches free(c); c.getMPG(); Processes Virtual memory Assembly get_mpg: Memory allocation pushq %rbp Java vs. C language: movq %rsp, %rbp ... popq %rbp ret OS: Machine 0111010000011000 100011010000010000000010 code: 1000100111000010 110000011111101000011111 Computer system: Winter 2016 Memory Allocation 1 University of Washington Memory Allocation Topics Dynamic memory allocation . Size/number/lifetime of data structures may only be known at run time . Need to allocate space on the heap . Need to de-allocate (free) unused memory so it can be re-allocated Explicit Allocation Implementation . Implicit free lists . Explicit free lists – subject of next programming assignment . Segregated free lists Implicit Deallocation: Garbage collection Common memory-related bugs in C programs Winter 2016 Memory Allocation 2 University of Washington Dynamic Memory Allocation Programmers use dynamic memory allocators (such as malloc) to acquire virtual memory at run time . For data structures whose size (or lifetime) is known only at runtime Dynamic memory allocators manage an area of a process’ virtual memory known as the heap User stack Top of heap (brk ptr) Heap (via malloc) Uninitialized data (.bss) Initialized data (.data) Program text (.text) 0 Winter 2016 Memory Allocation 3 University of Washington Dynamic Memory Allocation Allocator organizes the heap as a collection of variable-sized blocks, which are either allocated or free . Allocator requests pages in heap region; virtual memory hardware and OS kernel allocate these pages to the process . -

Unleashing the Power of Allocator-Aware Software
P2126R0 2020-03-02 Pablo Halpern (on behalf of Bloomberg): [email protected] John Lakos: [email protected] Unleashing the Power of Allocator-Aware Software Infrastructure NOTE: This white paper (i.e., this is not a proposal) is intended to motivate continued investment in developing and maturing better memory allocators in the C++ Standard as well as to counter misinformation about allocators, their costs and benefits, and whether they should have a continuing role in the C++ library and language. Abstract Local (arena) memory allocators have been demonstrated to be effective at improving runtime performance both empirically in repeated controlled experiments and anecdotally in a variety of real-world applications. The initial development and subsequent maintenance effort of implementing bespoke data structures using custom memory allocation, however, are typically substantial and often untenable, especially in the limited timeframes that urgent business needs impose. To address such recurring performance needs effectively across the enterprise, Bloomberg has adopted a consistent, ubiquitous allocator-aware software infrastructure (AASI) based on the PMR-style1 plug-in memory allocator protocol pioneered at Bloomberg and adopted into the C++17 Standard Library. In this paper, we highlight the essential mechanics and subtle nuances of programing on top of Bloomberg’s AASI platform. In addition to delineating how to obtain performance gains safely at minimal development cost, we explore many of the inherent collateral benefits — such as object placement, metrics gathering, testing, debugging, and so on — that an AASI naturally affords. After reading this paper and surveying the available concrete allocators (provided in Appendix A), a competent C++ developer should be adequately equipped to extract substantial performance and other collateral benefits immediately using our AASI. -

P1083r2 | Move Resource Adaptor from Library TS to the C++ WP
P1083r2 | Move resource_adaptor from Library TS to the C++ WP Pablo Halpern [email protected] 2018-11-13 | Target audience: LWG 1 Abstract When the polymorphic allocator infrastructure was moved from the Library Fundamentals TS to the C++17 working draft, pmr::resource_adaptor was left behind. The decision not to move pmr::resource_adaptor was deliberately conservative, but the absence of resource_adaptor in the standard is a hole that must be plugged for a smooth transition to the ubiquitous use of polymorphic_allocator, as proposed in P0339 and P0987. This paper proposes that pmr::resource_adaptor be moved from the LFTS and added to the C++20 working draft. 2 History 2.1 Changes from R1 to R2 (in San Diego) • Paper was forwarded from LEWG to LWG on Tuesday, 2018-10-06 • Copied the formal wording from the LFTS directly into this paper • Minor wording changes as per initial LWG review • Rebased to the October 2018 draft of the C++ WP 2.2 Changes from R0 to R1 (pre-San Diego) • Added a note for LWG to consider clarifying the alignment requirements for resource_adaptor<A>::do_allocate(). • Changed rebind type from char to byte. • Rebased to July 2018 draft of the C++ WP. 3 Motivation It is expected that more and more classes, especially those that would not otherwise be templates, will use pmr::polymorphic_allocator<byte> to allocate memory. In order to pass an allocator to one of these classes, the allocator must either already be a polymorphic allocator, or must be adapted from a non-polymorphic allocator. The process of adaptation is facilitated by pmr::resource_adaptor, which is a simple class template, has been in the LFTS for a long time, and has been fully implemented. -

The Slab Allocator: an Object-Caching Kernel Memory Allocator
The Slab Allocator: An Object-Caching Kernel Memory Allocator Jeff Bonwick Sun Microsystems Abstract generally superior in both space and time. Finally, Section 6 describes the allocator’s debugging This paper presents a comprehensive design over- features, which can detect a wide variety of prob- view of the SunOS 5.4 kernel memory allocator. lems throughout the system. This allocator is based on a set of object-caching primitives that reduce the cost of allocating complex objects by retaining their state between uses. These 2. Object Caching same primitives prove equally effective for manag- Object caching is a technique for dealing with ing stateless memory (e.g. data pages and temporary objects that are frequently allocated and freed. The buffers) because they are space-efficient and fast. idea is to preserve the invariant portion of an The allocator’s object caches respond dynamically object’s initial state — its constructed state — to global memory pressure, and employ an object- between uses, so it does not have to be destroyed coloring scheme that improves the system’s overall and recreated every time the object is used. For cache utilization and bus balance. The allocator example, an object containing a mutex only needs also has several statistical and debugging features to have mutex_init() applied once — the first that can detect a wide range of problems throughout time the object is allocated. The object can then be the system. freed and reallocated many times without incurring the expense of mutex_destroy() and 1. Introduction mutex_init() each time. An object’s embedded locks, condition variables, reference counts, lists of The allocation and freeing of objects are among the other objects, and read-only data all generally qual- most common operations in the kernel. -

A Buffer Overflow Study
A Bu®er Overflow Study Attacks & Defenses Pierre-Alain FAYOLLE, Vincent GLAUME ENSEIRB Networks and Distributed Systems 2002 Contents I Introduction to Bu®er Overflows 5 1 Generalities 6 1.1 Process memory . 6 1.1.1 Global organization . 6 1.1.2 Function calls . 8 1.2 Bu®ers, and how vulnerable they may be . 10 2 Stack overflows 12 2.1 Principle . 12 2.2 Illustration . 12 2.2.1 Basic example . 13 2.2.2 Attack via environment variables . 14 2.2.3 Attack using gets . 16 3 Heap overflows 18 3.1 Terminology . 18 3.1.1 Unix . 18 3.1.2 Windows . 18 3.2 Motivations and Overview . 18 3.3 Overwriting pointers . 19 3.3.1 Di±culties . 20 3.3.2 Interest of the attack . 20 3.3.3 Practical study . 20 3.4 Overwriting function pointers . 24 3.4.1 Pointer to function: short reminder . 24 3.4.2 Principle . 24 3.4.3 Example . 25 3.5 Trespassing the heap with C + + . 28 3.5.1 C++ Background . 28 3.5.2 Overwriting the VPTR . 31 3.5.3 Conclusions . 32 3.6 Exploiting the malloc library . 33 3.6.1 DLMALLOC: structure . 33 3.6.2 Corruption of DLMALLOC: principle . 34 II Protection solutions 37 4 Introduction 38 1 5 How does Libsafe work? 39 5.1 Presentation . 39 5.2 Why are the functions of the libC unsafe ? . 39 5.3 What does libsafe provide ? . 40 6 The Grsecurity Kernel patch 41 6.1 Open Wall: non-executable stack .