BIOS Data ACPI Table (BDAT)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

No-Longer-Foreign: Teaching an ML Compiler to Speak C “Natively”
Electronic Notes in Theoretical Computer Science 59 No. 1 (2001) URL: http://www.elsevier.nl/locate/entcs/volume59.html 16 pages No-Longer-Foreign: Teaching an ML compiler to speak C “natively” Matthias Blume 1 Lucent Technologies, Bell Laboratories Abstract We present a new foreign-function interface for SML/NJ. It is based on the idea of data- level interoperability—the ability of ML programs to inspect as well as manipulate C data structures directly. The core component of this work is an encoding of the almost 2 complete C type sys- tem in ML types. The encoding makes extensive use of a “folklore” typing trick, taking advantage of ML’s polymorphism, its type constructors, its abstraction mechanisms, and even functors. A small low-level component which deals with C struct and union declarations as well as program linkage is hidden from the programmer’s eye by a simple program-generator tool that translates C declarations to corresponding ML glue code. 1 An example Suppose you are an ML programmer who wants to link a program with some C rou- tines. The following example (designed to demonstrate data-level interoperability rather than motivate the need for FFIs in the first place) there are two C functions: input reads a list of records from a file and findmin returns the record with the smallest i in a given list. The C library comes with a header file ixdb.h that describes this interface: typedef struct record *list; struct record { int i; double x; list next; }; extern list input (char *); extern list findmin (list); Our ml-nlffigen tool translates ixdb.h into an ML interface that corre- sponds nearly perfectly to the original C interface. -

What I Wish I Knew When Learning Haskell
What I Wish I Knew When Learning Haskell Stephen Diehl 2 Version This is the fifth major draft of this document since 2009. All versions of this text are freely available onmywebsite: 1. HTML Version http://dev.stephendiehl.com/hask/index.html 2. PDF Version http://dev.stephendiehl.com/hask/tutorial.pdf 3. EPUB Version http://dev.stephendiehl.com/hask/tutorial.epub 4. Kindle Version http://dev.stephendiehl.com/hask/tutorial.mobi Pull requests are always accepted for fixes and additional content. The only way this document will stayupto date and accurate through the kindness of readers like you and community patches and pull requests on Github. https://github.com/sdiehl/wiwinwlh Publish Date: March 3, 2020 Git Commit: 77482103ff953a8f189a050c4271919846a56612 Author This text is authored by Stephen Diehl. 1. Web: www.stephendiehl.com 2. Twitter: https://twitter.com/smdiehl 3. Github: https://github.com/sdiehl Special thanks to Erik Aker for copyediting assistance. Copyright © 20092020 Stephen Diehl This code included in the text is dedicated to the public domain. You can copy, modify, distribute and perform thecode, even for commercial purposes, all without asking permission. You may distribute this text in its full form freely, but may not reauthor or sublicense this work. Any reproductions of major portions of the text must include attribution. The software is provided ”as is”, without warranty of any kind, express or implied, including But not limitedtothe warranties of merchantability, fitness for a particular purpose and noninfringement. In no event shall the authorsor copyright holders be liable for any claim, damages or other liability, whether in an action of contract, tort or otherwise, Arising from, out of or in connection with the software or the use or other dealings in the software. -

Idris: a Functional Programming Language with Dependent Types
Programming Languages and Compiler Construction Department of Computer Science Christian-Albrechts-University of Kiel Seminar Paper Idris: A Functional Programming Language with Dependent Types Author: B.Sc. Finn Teegen Date: 20th February 2015 Advised by: M.Sc. Sandra Dylus Contents 1 Introduction1 2 Fundamentals2 2.1 Universes....................................2 2.2 Type Families..................................2 2.3 Dependent Types................................3 2.4 Curry-Howard Correspondence........................4 3 Language Overview5 3.1 Simple Types and Functions..........................5 3.2 Dependent Types and Functions.......................6 3.3 Implicit Arguments...............................7 3.4 Views......................................8 3.5 Lazy Evaluation................................8 3.6 Syntax Extensions...............................9 4 Theorem Proving 10 4.1 Propositions as Types and Terms as Proofs................. 10 4.2 Encoding Intuitionistic First-Order Logic................... 12 4.3 Totality Checking................................ 14 5 Conclusion 15 ii 1 Introduction In conventional Hindley-Milner based programming languages, such as Haskell1, there is typically a clear separation between values and types. In dependently typed languages, however, this distinction is less clear or rather non-existent. In fact, types can depend on arbitrary values. Thus, they become first-class citizens and are computable like any other value. With types being allowed to contain values, they gain the possibility to describe prop- erties of their own elements. The standard example for dependent types is the type of lists of a given length - commonly referred to as vectors - where the length is part of the type itself. When starting to encode properties of values as types, the elements of such types can be seen as proofs that the stated property is true. -

COSC 6385 Computer Architecture - Multi-Processors (IV) Simultaneous Multi-Threading and Multi-Core Processors Edgar Gabriel Spring 2011
COSC 6385 Computer Architecture - Multi-Processors (IV) Simultaneous multi-threading and multi-core processors Edgar Gabriel Spring 2011 Edgar Gabriel Moore’s Law • Long-term trend on the number of transistor per integrated circuit • Number of transistors double every ~18 month Source: http://en.wikipedia.org/wki/Images:Moores_law.svg COSC 6385 – Computer Architecture Edgar Gabriel 1 What do we do with that many transistors? • Optimizing the execution of a single instruction stream through – Pipelining • Overlap the execution of multiple instructions • Example: all RISC architectures; Intel x86 underneath the hood – Out-of-order execution: • Allow instructions to overtake each other in accordance with code dependencies (RAW, WAW, WAR) • Example: all commercial processors (Intel, AMD, IBM, SUN) – Branch prediction and speculative execution: • Reduce the number of stall cycles due to unresolved branches • Example: (nearly) all commercial processors COSC 6385 – Computer Architecture Edgar Gabriel What do we do with that many transistors? (II) – Multi-issue processors: • Allow multiple instructions to start execution per clock cycle • Superscalar (Intel x86, AMD, …) vs. VLIW architectures – VLIW/EPIC architectures: • Allow compilers to indicate independent instructions per issue packet • Example: Intel Itanium series – Vector units: • Allow for the efficient expression and execution of vector operations • Example: SSE, SSE2, SSE3, SSE4 instructions COSC 6385 – Computer Architecture Edgar Gabriel 2 Limitations of optimizing a single instruction -

Constrained Type Families (Extended Version)
Constrained Type Families (extended version) J. GARRETT MORRIS, e University of Edinburgh and e University of Kansas 42 RICHARD A. EISENBERG, Bryn Mawr College We present an approach to support partiality in type-level computation without compromising expressiveness or type safety. Existing frameworks for type-level computation either require totality or implicitly assume it. For example, type families in Haskell provide a powerful, modular means of dening type-level computation. However, their current design implicitly assumes that type families are total, introducing nonsensical types and signicantly complicating the metatheory of type families and their extensions. We propose an alternative design, using qualied types to pair type-level computations with predicates that capture their domains. Our approach naturally captures the intuitive partiality of type families, simplifying their metatheory. As evidence, we present the rst complete proof of consistency for a language with closed type families. CCS Concepts: •eory of computation ! Type structures; •So ware and its engineering ! Func- tional languages; Additional Key Words and Phrases: Type families, Type-level computation, Type classes, Haskell ACM Reference format: J. Garre Morris and Richard A. Eisenberg. 2017. Constrained Type Families (extended version). PACM Progr. Lang. 1, 1, Article 42 (January 2017), 38 pages. DOI: hp://dx.doi.org/10.1145/3110286 1 INTRODUCTION Indexed type families (Chakravarty et al. 2005; Schrijvers et al. 2008) extend the Haskell type system with modular type-level computation. ey allow programmers to dene and use open mappings from types to types. ese have given rise to further extensions of the language, such as closed type families (Eisenberg et al. -

486/25/33 EISA System Board User's Manual
PREFACE Thank you for purchasing 486EI EISA/VESA system board. This document helps configure and install the system board. The document is prepared with our best knowledge; however, we make no representation or warranty concerning the contents or use of this manual, and specifically disclaim any expressly implied warranties or merchant ability or fitness of any particular purpose. The information in this document is subject to change without notice. This document contains information protected by copyright. All rights are reserved. No part of this document may be used or reproduced in any forms or by any means, or stored in a database or retrieval system, without prior written permission. TRADEMARKS IBM, PC, XT, and AT are trademarks of International Business Machines Corp. UNIX is a trademark of AT&T Bell Labs. DOS, OS/2 and XENIX are trademarks of Microsoft Corp. 8086, 80286, i386, i486 , i486DX, i486DX2, i486DX4, i486SX, and i487SX, Intel OverDrive Processor are trademarks of Intel Corp. TECHNICAL REFERENCE . I486 Microprocessor (Intel Order No: 240440-002) . I486 Microprocessor Programmer’s Reference Manual (Intel Order No. 240486-001) . SIS 85C411 EISA System Chipset Data Book . The EISA Specification published by: BCPR Services, Incorporated . The VESA VL Bus Specification published by: Video Electronics Standard Association 486EI EISA&VESA System Board User's Manual Page 1 TABLE OF CONTENTS PREFACE CHAPTER 1: INTRODUCTION PRODUCT OVERVIEW FEATURES CPU SUPPORT CACHE MEMORY SYSTEM MEMORY DRAM SYSTEM BIOS SHADOW RAM SYSTEM CHIPSET -

Twelf User's Guide
Twelf User’s Guide Version 1.4 Frank Pfenning and Carsten Schuermann Copyright c 1998, 2000, 2002 Frank Pfenning and Carsten Schuermann Chapter 1: Introduction 1 1 Introduction Twelf is the current version of a succession of implementations of the logical framework LF. Previous systems include Elf (which provided type reconstruction and the operational semantics reimplemented in Twelf) and MLF (which implemented module-level constructs loosely based on the signatures and functors of ML still missing from Twelf). Twelf should be understood as research software. This means comments, suggestions, and bug reports are extremely welcome, but there are no guarantees regarding response times. The same remark applies to these notes which constitute the only documentation on the present Twelf implementation. For current information including download instructions, publications, and mailing list, see the Twelf home page at http://www.cs.cmu.edu/~twelf/. This User’s Guide is pub- lished as Frank Pfenning and Carsten Schuermann Twelf User’s Guide Technical Report CMU-CS-98-173, Department of Computer Science, Carnegie Mellon University, November 1998. Below we state the typographic conventions in this manual. code for Twelf or ML code ‘samp’ for characters and small code fragments metavar for placeholders in code keyboard for input in verbatim examples hkeyi for keystrokes math for mathematical expressions emph for emphasized phrases File names for examples given in this guide are relative to the main directory of the Twelf installation. For example ‘examples/guide/nd.elf’ may be found in ‘/usr/local/twelf/examples/guide/nd.elf’ if Twelf was installed into the ‘/usr/local/’ directory. -

Session Arrows: a Session-Type Based Framework for Parallel Code Generation
MENG INDIVIDUAL PROJECT IMPERIAL COLLEGE LONDON DEPARTMENT OF COMPUTING Session Arrows: A Session-Type Based Framework For Parallel Code Generation Supervisor: Prof. Nobuko Yoshida Author: Dr. David Castro-Perez Shuhao Zhang Second Marker: Dr. Iain Phillips June 19, 2019 Abstract Parallel code is notorious for its difficulties in writing, verification and maintenance. However, it is of increasing importance, following the end of Moore’s law. Modern pro- grammers are expected to utilize the power of multi-core CPUs and face the challenges brought by parallel programs. This project builds an embedded framework in Haskell to generate parallel code. Combining the power of multiparty session types with parallel computation, we create a session typed monadic language as the middle layer and use Arrow, a general interface to computation as an abstraction layer on top of the language. With the help of the Arrow interface, we convert the data-flow of the computation to communication and generate parallel code according to the communication pattern between participants involved in the computation. Thanks to the addition of session types, not only the generated code is guaranteed to be deadlock-free, but also we gain a set of local types so that it is possible to reason about the communication structure of the parallel computation. In order to show that the framework is as expressive as usual programming lan- guages, we write several common parallel computation patterns and three algorithms to benchmark using our framework. They demonstrate that users can express computa- tion similar to traditional sequential code and gain, for free, high-performance parallel code in low-level target languages such as C. -
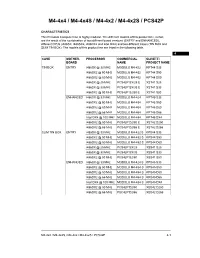
M4-4X4 / M4-4X4s / M4-4X2 / M4-4X2s / PCS42P
M4-4x4 / M4-4x4S / M4-4x2 / M4-4x2S / PCS42P CHARACTERISTICS This Personal Computer line is highly modular. The different models of this product line, in fact, are the result of the combination of two different board versions (ENTRY and ENHANCED), different CPUs (i486SX, i486SX2, i486DX2 and Intel DX4) and two different cases (TIN BOX and SLIM TIN BOX). The models of this product line are listed in the following table. 4 CASE MOTHER- PROCESSOR COMMERCIAL OLIVETTI BOARD NAME PROJECT NAME TIN BOX ENTRY i486SX @ 33 MHz MODULO M4-422 KPT44 S33 i486SX2 @ 50 MHz MODULO M4-432 KPT44 S50 i486DX2 @ 50 MHz MODULO M4-452 KPT44 D50 i486SX @ 25 MHz PCS42P SX/25 E XST41 S25 i486SX @ 33 MHz PCS42P SX/33 E XST41 S33 i486SX2 @ 50 MHz PCS42P S2/50 E XST41 S50 ENHANCED i486SX @ 33 MHz MODULO M4-424 KPT45 S33 i486SX2 @ 50 MHz MODULO M4-434 KPT45 S50 i486DX2 @ 50 MHz MODULO M4-454 KPT45 D50 i486DX2 @ 66 MHz MODULO M4-464 KPT45 D66 Intel DX4 @ 100 MHz MODULO M4-484 KPT45 DX4 i486DX2 @ 50 MHz PCS42P D2/50 E XST42 D250 i486DX2 @ 66 MHz PCS42P D2/66 E XST42 D266 SLIM TIN BOX ENTRY i486SX @ 33 MHz MODULO M4-422 S KPS44 S33 i486SX2 @ 50 MHz MODULO M4-432 S KPS44 S50 i486DX2 @ 50 MHz MODULO M4-452 S KPS44 D50 i486SX @ 25 MHz PCS42P SX/25 XSS41 S25 i486SX @ 33 MHz PCS42P SX/33 XSS41 S33 i486SX2 @ 50 MHz PCS42P S2/50 XSS41 S50 ENHANCED i486SX @ 33 MHz MODULO M4-424 S KPS45 S33 i486SX2 @ 50 MHz MODULO M4-434 S KPS45 S50 i486DX2 @ 50 MHz MODULO M4-454 S KPS45 D50 i486DX2 @ 66 MHz MODULO M4-464 S KPS45 D66 Intel DX4 @ 100 MHz MODULO M4-484 S KPS45 DX4 i486DX2 @ 50 MHz -

Ur/Web: a Simple Model for Programming the Web
Ur/Web: A Simple Model for Programming the Web The MIT Faculty has made this article openly available. Please share how this access benefits you. Your story matters. Citation Chlipala, Adam. "Ur/Web: A Simple Model for Programming the Web." The 42nd ACM SIGPLAN-SIGACT Symposium on Principles of Programming Languages (POPL '15), January 15-17, 2015, Mumbai, India. As Published http://dl.acm.org/citation.cfm?id=2676726 Publisher Association for Computing Machinery (ACM) Version Author's final manuscript Citable link http://hdl.handle.net/1721.1/92321 Terms of Use Creative Commons Attribution-Noncommercial-Share Alike Detailed Terms http://creativecommons.org/licenses/by-nc-sa/4.0/ Ur/Web: A Simple Model for Programming the Web Adam Chlipala rtifact Comple * A t * te n * te A is W s E * e n l l C o L D MIT CSAIL C o P * * c u e m s O E u e e P n R t v e [email protected] o d t * y * s E a a l d u e a t Abstract for network communication, and on a language or API like SQL The World Wide Web has evolved gradually from a document de- for storing persistent, structured data on servers. Code fragments livery platform to an architecture for distributed programming. This in these different languages are often embedded within each other largely unplanned evolution is apparent in the set of interconnected in complex ways, and the popular Web development tools provide languages and protocols that any Web application must manage. little help in catching inconsistencies. -

A Verifying Compiler for Embedded Networked Systems Kalyan Chakradhar Regula Clemson University, [email protected]
Clemson University TigerPrints All Theses Theses 8-2010 A Verifying Compiler for Embedded Networked Systems Kalyan chakradhar Regula Clemson University, [email protected] Follow this and additional works at: https://tigerprints.clemson.edu/all_theses Part of the Computer Sciences Commons Recommended Citation Regula, Kalyan chakradhar, "A Verifying Compiler for Embedded Networked Systems" (2010). All Theses. 899. https://tigerprints.clemson.edu/all_theses/899 This Thesis is brought to you for free and open access by the Theses at TigerPrints. It has been accepted for inclusion in All Theses by an authorized administrator of TigerPrints. For more information, please contact [email protected]. A Verifying Compiler for Embedded Networked Systems A Thesis Presented to the Graduate School of Clemson University In Partial Fulfillment of the Requirements for the Degree Master Of Science Computer Science by Kalyan Chakradhar Regula August 2010 Accepted by: Dr. Jason O. Hallstrom, Committee Chair Dr. Murali Sitaraman Dr. Brain Malloy Abstract Embedded networked devices are required to produce dependable outputs and communicate with peer devices given limited computing resources. These devices monitor and control processes within the physical world. They are used in applications related to environmental monitoring, telecommunications, social networking, and also life-critical applications in domains such as health care, aeronautics, and automotive manufacturing. For such applications, software errors can be costly - both in terms of financial and human costs. Therefore, software programs installed on these devices must meet the appropriate requirements. To guarantee this, one must verify that the implemented code meets the corresponding specifications. Manual trial-and-error validation of such applications, especially life-critical software programs, is not a feasible option. -

Type Theory & Functional Programming
Type Theory & Functional Programming Simon Thompson Computing Laboratory, University of Kent March 1999 c Simon Thompson, 1999 Not to be reproduced i ii To my parents Preface Constructive Type theory has been a topic of research interest to computer scientists, mathematicians, logicians and philosophers for a number of years. For computer scientists it provides a framework which brings together logic and programming languages in a most elegant and fertile way: program development and verification can proceed within a single system. Viewed in a different way, type theory is a functional programming language with some novel features, such as the totality of all its functions, its expressive type system allowing functions whose result type depends upon the value of its input, and sophisticated modules and abstract types whose interfaces can contain logical assertions as well as signature information. A third point of view emphasizes that programs (or functions) can be extracted from proofs in the logic. Up until now most of the material on type theory has only appeared in proceedings of conferences and in research papers, so it seems appropriate to try to set down the current state of development in a form accessible to interested final-year undergraduates, graduate students, research workers and teachers in computer science and related fields – hence this book. The book can be thought of as giving both a first and a second course in type theory. We begin with introductory material on logic and functional programming, and follow this by presenting the system of type theory itself, together with many examples. As well as this we go further, looking at the system from a mathematical perspective, thus elucidating a number of its important properties.