Subwords: Automata, Embedding Problems, and Verification
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A Declarative Characterization of Different Types of Multicomponent
A Declarative Characterization of Different Types of Multicomponent Tree Adjoining Grammars† Laura Kallmeyer ([email protected]) Collaborative Research Center 833, University of T¨ubingen, Nauklerstr. 35, D-72074 T¨ubingen, Germany. Abstract. Multicomponent Tree Adjoining Grammars (MCTAGs) are a formalism that has been shown to be useful for many natural language applications. The definition of non-local MCTAG however is problematic since it refers to the process of the derivation itself: a simultaneity constraint must be respected concerning the way the members of the elementary tree sets are added. Looking only at the result of a derivation (i.e., the derived tree and the derivation tree), this simultaneity is no longer visible and therefore cannot be checked. I.e., this way of characterizing MCTAG does not allow to abstract away from the concrete order of derivation. In this paper, we propose an alternative definition of MCTAG that characterizes the trees in the tree language of an MCTAG via the properties of the derivation trees (in the underlying TAG) the MCTAG licences. We provide similar characterizations for various types of MCTAG. These characterizations give a better understanding of the formalisms, they allow a more systematic comparison of different types of MCTAG, and, furthermore, they can be exploited for parsing. Keywords: Tree Adjoining Grammar, MCTAG, multicomponent rewriting, Simple Range Concatenation Grammar 1. Introduction 1.1. Tree Adjoining Grammars Tree Adjoining Grammar (TAG, see Joshi and Schabes, 1997) is a tree- rewriting formalism. A TAG consists of a finite set of trees (elementary trees). The nodes of these trees are labelled with nonterminals and ter- minals (terminals only label leaf nodes). -
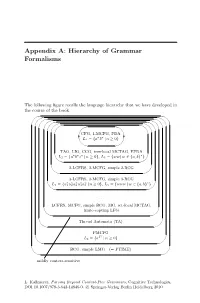
Appendix A: Hierarchy of Grammar Formalisms
Appendix A: Hierarchy of Grammar Formalisms The following figure recalls the language hierarchy that we have developed in the course of the book. '' $$ '' $$ '' $$ ' ' $ $ CFG, 1-MCFG, PDA n n L1 = {a b | n ≥ 0} & % TAG, LIG, CCG, tree-local MCTAG, EPDA n n n ∗ L2 = {a b c | n ≥ 0}, L3 = {ww | w ∈{a, b} } & % 2-LCFRS, 2-MCFG, simple 2-RCG & % 3-LCFRS, 3-MCFG, simple 3-RCG n n n n n ∗ L4 = {a1 a2 a3 a4 a5 | n ≥ 0}, L5 = {www | w ∈{a, b} } & % ... LCFRS, MCFG, simple RCG, MG, set-local MCTAG, finite-copying LFG & % Thread Automata (TA) & % PMCFG 2n L6 = {a | n ≥ 0} & % RCG, simple LMG (= PTIME) & % mildly context-sensitive L. Kallmeyer, Parsing Beyond Context-Free Grammars, Cognitive Technologies, DOI 10.1007/978-3-642-14846-0, c Springer-Verlag Berlin Heidelberg 2010 216 Appendix A For each class the different formalisms and automata that generate/accept exactly the string languages contained in this class are listed. Furthermore, examples of typical languages for this class are added, i.e., of languages that belong to this class while not belonging to the next smaller class in our hier- archy. The inclusions are all proper inclusions, except for the relation between LCFRS and Thread Automata (TA). Here, we do not know whether the in- clusion is a proper one. It is possible that both devices yield the same class of languages. Appendix B: List of Acronyms The following table lists all acronyms that occur in this book. (2,2)-BRCG Binary bottom-up non-erasing RCG with at most two vari- ables per left-hand side argument 2-SA Two-Stack Automaton -

LR Parsing for LCFRS
algorithms Article LR Parsing for LCFRS Laura Kallmeyer * and Wolfgang Maier Department for Computational Linguistics, Institute for Language and Information, Heinrich-Heine Universität Düsseldorf, Universitätsstr. 1, 40225 Düsseldorf, Germany; [email protected] * Correspondence: [email protected]; Tel.: +49-211-8113-899 Academic Editor: Henning Fernau Received: 21 March 2016; Accepted: 18 August 2016; Published: 27 August 2016 Abstract: LR parsing is a popular parsing strategy for variants of Context-Free Grammar (CFG). It has also been used for mildly context-sensitive formalisms, such as Tree-Adjoining Grammar. In this paper, we present the first LR-style parsing algorithm for Linear Context-Free Rewriting Systems (LCFRS), a mildly context-sensitive extension of CFG which has received considerable attention in the last years in the context of natural language processing. Keywords: parsing; automata; LCFRS 1. Introduction In computational linguistics, the modeling of discontinuous structures in natural language, i.e., of structures that span two or more non-adjacent portions of the input string, is an important issue. In recent years, Linear Context-Free Rewriting System (LCFRS) [1] has emerged as a formalism which is useful for this task. LCFRS is a mildly context-sensitive [2] extension of CFG in which a single non-terminal can cover k N continuous blocks of terminals. CFG is a special case of LCFRS where 2 k = 1. In CFG, only embedded structures can be modelled. In LCFRS, in contrast, yields can be intertwined. The schematically depicted derivation trees in Figure1 illustrate the different domains of locality of CFG and LCFRS. As can be seen, in the schematic CFG derivation, X contributes a continuous component b to the full yield. -

Two Characterisation Results of Multiple Context-Free Grammars and Their Application to Parsing
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Technische Universität Dresden: Qucosa Two characterisation results of multiple context-free grammars and their application to parsing Dissertation zur Erlangung des akademischen Grades Doctor rerum naturalium (Dr. rer. nat.) vorgelegt an der Technische Universität Dresden Fakultät Informatik eingereicht am 5. Juli 2019 von Dipl.-Inf. Tobias Denkinger geboren am 07. 12. 1989 in Rodewisch im Vogtland Gutachter: • Prof. Dr.-Ing. habil. Dr. h.c./Univ. Szeged Heiko Vogler, Technische Universität Dresden (Betreuer) • Dr. Mark-Jan Nederhof, University of St Andrews Fachreferentin: • Prof. Dr. Laura Kallmeyer, Heinrich-Heine-Universität Düsseldorf Verteidigt am: 27. September 2019 in Dresden Acknowledgements Firstly, I would like to thank my supervisor Heiko Vogler for his patience and for all the hours we spent at the blackboard discussing details I would otherwise have missed. I thank Mark-Jan Nederhof for his advice over the years and for agreeing to review this thesis. I am grateful to my current and former colleagues for creating a great work environment at the Chair for Foundations of Programming. In particular, I thank Toni Dietze for always having time to discuss my problems, no matter how technical they were; Johannes Osterholzer for his guidance and for answering countless questions of mine; my office mates Luisa Herrmann and Thomas Ruprecht for letting me bounce ideas off of them and for challenging my(frequently wrong) assumptions; and Kerstin Achtruth for helping me navigate the arcane ways of a university administration. I thank my proofreaders Frederic Dörband, Kilian Gebhardt, Luisa Herrmann, Richard Mörbitz, Nadine Palme, and Thomas Ruprecht for taking the time andfor helping me fix a lot of mistakes. -

An Infinite Automaton Characterization of Double Exponential Time⋆
An Infinite Automaton Characterization of Double Exponential Time⋆ Salvatore La Torre1, P. Madhusudan2, and Gennaro Parlato1,2 1 Universit`adi Salerno, Italy 2 University of Illinois, Urbana-Champaign, USA Abstract. Infinite-state automata are a new invention: they are automata that have an infinite number of states represented by words, transitions defined us- ing rewriting, and with sets of initial and final states. Infinite-state automata have gained recent interest due to a remarkable result by Morvan and Stirling, which shows that automata with transitions defined using rational rewriting precisely capture context-sensitive (NLINSPACE) languages. In this paper, we show that infinite automata defined using a form of multi-stack rewriting precisely defines double exponential time (more precisely, 2ETIME, the class of problems solvable 2O(n) in 2 time). The salient aspect of this characterization is that the automata have no ostensible limits on time nor space, and neither direction of containment with respect to 2ETIME is obvious. In this sense, the result captures the complex- ity class qualitatively, by restricting the power of rewriting. 1 Introduction The theory of infinite-state automata is a new area of research (see [21] for a recent survey). Infinite-state automata (not to be confused with finite state automata on infinite words) are automata with infinitely many states that can read finite words and accept or reject them, in much the same way as finite-state automata would. In order to represent infinite-state automata using finite means, the states, the transitions, and the initial and final state sets are represented symbolically. The infinite-state automata we study in this paper are defined by using words to represent the states of the automaton.Let us fix a finite alphabet Σ as the input alphabet for the infinite-state automata. -

Using Discrete-Event Systems for the Automatic Generation of Concurrency Control for Dynamic Threads
Using Discrete-Event Systems for the Automatic Generation of Concurrency Control for Dynamic Threads by Anthony R. Auer A thesis submitted to the School of Computing in conformity with the requirements for the degree of Master of Science Queen’s University Kingston, Ontario, Canada May 2010 Copyright © Anthony R. Auer, 2010 Library and Archives Bibliothèque et Canada Archives Canada Published Heritage Direction du Branch Patrimoine de l’édition 395 Wellington Street 395, rue Wellington Ottawa ON K1A 0N4 Ottawa ON K1A 0N4 Canada Canada Your file Votre référence ISBN: 978-0-494-69987-4 Our file Notre référence ISBN: 978-0-494-69987-4 NOTICE: AVIS: The author has granted a non- L’auteur a accordé une licence non exclusive exclusive license allowing Library and permettant à la Bibliothèque et Archives Archives Canada to reproduce, Canada de reproduire, publier, archiver, publish, archive, preserve, conserve, sauvegarder, conserver, transmettre au public communicate to the public by par télécommunication ou par l’Internet, prêter, telecommunication or on the Internet, distribuer et vendre des thèses partout dans le loan, distribute and sell theses monde, à des fins commerciales ou autres, sur worldwide, for commercial or non- support microforme, papier, électronique et/ou commercial purposes, in microform, autres formats. paper, electronic and/or any other formats. The author retains copyright L’auteur conserve la propriété du droit d’auteur ownership and moral rights in this et des droits moraux qui protège cette thèse. Ni thesis. Neither the thesis nor la thèse ni des extraits substantiels de celle-ci substantial extracts from it may be ne doivent être imprimés ou autrement printed or otherwise reproduced reproduits sans son autorisation.