Computer Security for Business and Home: Best Practices
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Anyconnect および Host Scan のアンチウイルス/アンチスパイウェア
AnyConnect および Host Scan のアンチウイルス/アンチスパイウェア/ファイアウォール サポート表 AnyConnect ポスチャ モジュールにより、AnyConnect Secure Mobility クライアントはホストにインス トールされているオペレーティング システム、およびアンチウイルス、アンチスパイウェア、ファイアウォールの 各ソフトウェアを識別できます。 Host Scan アプリケーションはポスチャ モジュールのコンポーネントに含まれ る、こうした情報を収集するアプリケーションです。 AnyConnect 3.0 より、Host Scan パッケージは AnyConnect Secure Mobility クライアントおよび Cisco Secure Desktop(CSD)の共有コンポーネントになっています。 それ以前は、Host Scan パッケージは CSD を インストールすることによってのみ利用可能になるコンポーネントの 1 つでした。 Host Scan パッケージを CSD から分離したのは、CSD の一部として提供されていたときよりも、ユー ザが頻繁に Host Scan サポート表を更新できるようにするためです。 このサポート表には、ユーザが動的なア クセス ポリシーで使用しているアンチウイルス/アンチスパイウェア/ファイアウォール アプリケーションの製品 名とバージョン情報が記載されています。 シスコでは、Host Scan パッケージに Host Scan アプリケーション、 Host Scan サポート表、および他のコンポーネントを含めて提供しています。 Host Scan サポート表のリスト アンチウイルス アプリケーション総合リスト アンチスパイウェア アプリケーション総合リスト ファイアウォール アプリケーション総合リスト Windows 用アンチウイルス Windows 用アンチスパイウェア Windows 用ファイアウォール Linux 用アンチウイルス Linux 用ファイアウォール Mac OS 用アンチウイルス Mac OS 用アンチスパイウェア Mac OS 用ファイアウォール A B C D E F G H I J K L M N O P Q R S T U V W X Y Z AA AB AC AD AE ファイル データ ファ バージョ データ ファイ データ ファイル データ ファイ エンジンのバー RTP の RTP の 前回のスキャン スキャン/クリー システムのフル アンイン GUI のアク トレイ アイコンの トレイ アイコン 有効期 脅威ログの取 スキャン プログラ フル スキャンの進捗 インストール ディ 一括スキャ メモリ スキャ アンチウイルス製品名 ライブ更新 サービス GUI の表示 のスキャ 有効日の取得 更新の進捗表示 プログラム言語の取得 イル dir の取 市場での別名 ン ルの時刻 のバージョン ルの署名 ジョン チェック 設定 時刻 ニング スキャン ストール ティブ化 表示 の非表示 限 得 ムの実行 表示 レクトリの取得 ン ン 1 ン 得 2 3 360Safe.com 4 360 Antivirus 1.x 9989999898888898 8888 8 9 8 9 9 9 88 5 360杀毒 1.x 9999988898888898 8889 8 8 8 9 9 9 88 6 AEC, spol. s r.o. 7 TrustPort Antivirus 2.x 8888998899888999 9888 8 9 8 9 8 988 8 Agnitum Ltd. -

A Simple Malware Test Environment
International Journal of Computer and Information Technology (ISSN: 2279 – 0764) Volume 02– Issue 04, July 2013 A Simple Malware Test Environment Sam Lundie and Daniel Rolf School of Computing and Information Systems University of Tasmania Launceston, Tasmania, Australia e-mail: {slundie, Daniel.Rolf} @utas.edu.au Abstract— Malware does not need to compromise the operating not-present fraud increased by 38% for the calendar year system kernel in order to provide an untrustworthy browsing 2010, with 35.6 cents in every $1,000 dollars falling victim experience for the user. This paper describes a simple, virtual to fraud [1]. However, similar figures for fraud perpetrated machine-based, malware test environment built using freeware against Online Banking are much harder to obtain as banks and open source software. The system was designed to allow are seemingly reluctant to divulge loss figures. The the high-level behaviour of a piece of malware to be studied quickly and conveniently by monitoring network, process and Symantec Corporation has claimed that cybercrime has file activity. The system proved effective when trialled against surpassed illegal drug trafficking as a criminal money- different samples of the well-known malware Zeus and was maker [2]. verified further by tests conducted with the commercially available anti-malware products PC-Tools and Trusteer. It has been estimated that Zeus is guilty of approximately Although tests were conducted with variants of the Zeus 44% of all banking malware infections [3]. In August 2009 malware, the techniques discussed in this paper are equally Gunter Ollmann the VP for research at Damaballa [4] applicable to any other malware and can be used to quickly positioned the Zeus malware as the number one botnet assess the effectiveness of potential anti-malware solutions. -

Computer Security Administration
Information Security Group Information + Technology Services University of Toronto Endpoint Security Policy System A Network Access Control System with Vulnerability Detection and User Remediation Evgueni Martynov UNIX Systems Group Mike Wiseman Computer Security Administration Endpoint Security Policy System Table of Contents Acknowledgements............................................................................. 3 Change History .................................................................................... 4 Summary ............................................................................................. 5 Overview .............................................................................................. 5 Network Isolation ............................................................................... 6 Vulnerability Detection ....................................................................... 6 User Remediation ................................................................................ 8 Administering ESP ............................................................................... 8 ESP Operations Experience ................................................................ 9 Appendix I – Installation and Configuration of ESP server ........... 10 Using init.sh ..................................................................................... 10 Post-Installation ................................................................................ 11 Configuring an ESP Server to Work with an ESP Agent ....................... -

Personal Firewalls Are a Necessity for Solo Users
Personal firewalls are a necessity for solo users COMPANY PRODUCT PLATFORM NOTES PRICE Aladdin Knowledge Systems Ltd. SeSafe Desktop Windows Combines antivirus with content filtering, blocking and $72 Arlington Heights, Ill. monitoring 847-808-0300 www.ealaddin.com Agnitum Inc. Outpost Firewall Pro Windows Blocks ads, sites, programs; limits access by specific times $40 Nicosia, Cyprus www.agnitum.com Computer Associates International Inc. eTrust EZ Firewall Windows Basic firewall available only by download $40/year Islandia, N.Y. 631-342-6000 my-etrust.com Deerfield Canada VisNetic Firewall Windows Stateful, packet-level firewall for workstations, mobile $101 (Canadian) St. Thomas, Ontario for Workstations users or telecommuters 519-633-3403 www.deerfieldcanada.ca Glucose Development Corp. Impasse Mac OS X Full-featured firewall with real-time logging display $10 Sunnyvale, Calif. www.glu.com Intego Corp. NetBarrier Personal Firewall Windows Full-featured firewall with cookie and ad blocking $50 Miami 512-637-0700 NetBarrier 10.1 Mac OS X Full-featured firewall $60 www.intego.com NetBarrier 2.1 Mac OS 8 and 9 Full-featured firewall $60 Internet Security Systems Inc. BlackIce Windows Consumer-oriented PC firewall $30 Atlanta 404-236-2600 RealSecure Desktop Windows Enterprise-grade firewall system for remote, mobile and wireless users Varies blackice.iss.net/ Kerio Technologies Inc. Kerio Personal Firewall Windows Bidirectional, stateful firewall with encrypted remote-management option $39 Santa Clara, Calif. 408-496-4500 www.kerio.com Lava Software Pty. Ltd. AdWare Plus Windows Antispyware blocks some advertiser monitoring but isn't $27 Falköping, Sweden intended to block surveillance utilities 46-0-515-530-14 www.lavasoft.de Network Associates Inc. -

Hostscan 4.8.01064 Antimalware and Firewall Support Charts
HostScan 4.8.01064 Antimalware and Firewall Support Charts 10/1/19 © 2019 Cisco and/or its affiliates. All rights reserved. This document is Cisco public. Page 1 of 76 Contents HostScan Version 4.8.01064 Antimalware and Firewall Support Charts ............................................................................... 3 Antimalware and Firewall Attributes Supported by HostScan .................................................................................................. 3 OPSWAT Version Information ................................................................................................................................................. 5 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.890.0 for Windows .................................................. 5 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.890.0 for Windows ........................................................ 44 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.824.0 for macos .................................................... 65 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.824.0 for macOS ........................................................... 71 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.730.0 for Linux ...................................................... 73 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.730.0 for Linux .............................................................. 76 ©201 9 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. -

A Glance Into the Eye Pyramid Technical Article V2
A glance into the Eye Pyramid RĂZVAN OLTEANU Security Reasercher We keep you safe and we keep it simple. 01 Introduction On January 11, 2017 Italian news agency AGI, published a court order regarding cyber-attacks against high ranking Italian government members and Italian institutions. The attacks were conducted by two Italian brothers to get financial information that would help them gain an advantage when trading on financial markets. Overview The campaign was carried out over several years starting in 2008 and continuing into 2010, 2011, 2012 and 2014. The mechanism the brothers used to distribute their malware was simple; targeted spear-phishing emails aimed at victims who had already been selected. The emails con- tained a malware attachment, which once opened harvested information from the victims’ computers. This information consisted of pictures, documents, archives, presenta- tions, email contacts, email bodies, usernames, passwords, keystrokes, web pages content and databases. Technical details The malware was written in VisualBasic.net and was obfuscated twice using common obfuscators: Dotfuscator and Skater .NET which can be easily reversed. The malware stored its sensitive data – license keys, URLs and paths – by encrypting with the Triple DES algorithm using the MD5 of a provided password as key and SHA256 of the pass- word as initialization vector. A glance into the Eye Pyramid 01 02 Figure 1 Security applications To remain unnoticed, it tried to disable any security application installed on the victim’s computer. Targeted -
Firewall Software for Windows Xp
Firewall software for windows xp Windows Free Download. Windows 10/8/7, Vista and XP. Block unwanted traffic. Become "ZoneAlarm remains an Editor's Choice for firewall protection. It does. The best protection for Windows XP. Select the antivirus protection that suits you best: ZoneAlarm Pro Antivirus & Firewall for XP, Download >. ZoneAlarm. COMODO offers Free Firewall download for Windows. A multi-layered Live Expert help; Firewall Protection; Antivirus Software 10 / 8 / 7 / Vista / XP SP2. Get award winning free firewall software from Comodo. Download World's #1 Free Firewall that finds threats and protects your PC Supported OS: XP 32bit, Vista/Win7/Win8/Win/Win10 32 bit & 64 bit / MB RAM / MB space. License: Free; OS: Windows XP Windows Vista Windows Windows Windows 10 Firewall Control is a program that has been developed by. Windows 10 Firewall Control is a program that has been developed by License: Free; OS: Windows XP Windows Vista Windows 7 Windows 8. The firewall that Microsoft introduced with the Windows XP SP2 service pack provides a basic level of protection from external attacks: it blocks. AVS Firewall works in Windows 8, 7, Vista, and XP. Note: During setup, AVS Firewall will install their registry cleaner software if you don't deselect it manually. Freeware - Download free Firewall software programs. OS: Windows XP//Vista//7, Linux, MacOS. In: Security/Privacy >. If you are using Windows 7 or Windows 8, you can use the built-in Windows firewall program. Windows XP and Vista firewall was not that great but Microsoft has. Windows has an effective built-in firewall, your home network adds that included firewall protection goes all the way back to Windows XP? Firewall programs to protect your PC. -

Acer Lanscope Agent 2.2.25.84 Acer Lanscope Agent 2.2.25.84 X64
Acer LANScope Agent 2.2.25.84 Acer LANScope Agent 2.2.25.84 x64 Adaptive Security Analyzer 2.0 AEC TrustPort Antivirus 2.8.0.2237 AEC TrustPort Personal Firewall 4.0.0.1305 AhnLab SpyZero 2007 and SmartUpdate AhnLab V3 Internet Security 7.0 Platinum Enterprise AhnLab V3 Internet Security 7.0 Platinum Enterprise x64 ArcaVir Antivir/Internet Security 09.03.3201.9 Ashampoo AntiSpyware 2 v 2.05 Ashampoo AntiVirus AtGuard 3.2 Authentium Command Anti-Malware v 5.0.5 AVG Identity Protection 8.5 BitDefender Antivirus 2008 BitDefender Antivirus Plus 10.247 BitDefender Client Professional Plus 8.0.2 BitDefender Antivirus Plus 10 BitDefender Standard Edition 7.2 (Fr) Bit Defender Professional Edition 7.2 (Fr) BitDefender 8 Professional Plus BitDefender 8 Professional (Fr) BitDefender 8 Standard BitDefender 8 Standard (Fr) BitDefender 9 Professional Plus BitDefender 9 Standard BitDefender for FileServers 2.1.11 BitDefender Free Edition 2009 12.0.12.0 BitDefender Antivirus 2009 12.0.10 BitDefender 2009 12.0.11.5 BitDefender Internet Security 2008 BitDefender Internet Security 2009 12.0.8 BitDefender 2009 Internet Security 12.0.11.5 BitDefender Internet Security v10.108 BitDefender Total Security 2008 BitDefender 2009 Total Security 12.0.11.5 CA AntiVirus 2008 CA Anti-Virus r8.1 / CA eTrustITM Agent r8.1 CA eTrustITM 8.1 CA eTrustITM 8.1.00 CA eTrustITM Agent 8.0.403 CA eTrust Pestpatrol 5.0 CA HIPS Managed Client 1.0 CA eTrust Antivirus 7.1.0194 CA PC Security Suite 6.0 \ Private PC Security Suite 6.0 CA PC Security Suite 6.0.00 Cipafilter Client Tools -

Benchmarking of Parental Control Tools for the Online Protection of Children
The study aims to benchmark the main functionalities, effectiveness and usability of most currently used filtering software from a technical and ‘fit-for-purpose’ point of view, without any commercial or profit-related concern. The European Union, the European Commission or any person acting on their behalf are not responsible for the accurateness, completeness, use of the information contained in this Study, nor shall they be liable for any loss, including consequential loss, that might derive from such use or from the findings of the Study themselves. The opinions expressed in this study are those of the authors and do not necessarily reflect the views of the European Commission. Although the authors exercised all reasonable efforts to ensure the accuracy and the quality of the contents of this publication, the Consortium assumes no liability for any inadvertent error or omission that may appear in this publication. Product and company names mentioned herein are trademarks or registered trademarks of their respective owners. The readers are hereby advised and notified that they are under obligation to understand and know the same, and ensure due compliance as required. Please acknowledge that in the tables reporting the testing results, tools name may be shorten for ease of reading. The full name, author and version are provided within the TOOL LIST section. Copyrights: the findings of the study, the report and its content and all the complement material is the sole and exclusive property of the European Commission. Main references -
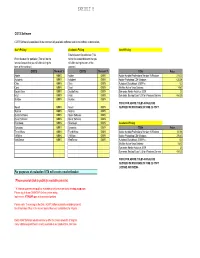
Dell VITA RFP- Revised COTS Pricing 12-17-08
COTS Software COTS Software is considered to be commercially available software read to run without customization, Gov't Pricing Academic Pricing Gov't Pricing Enter discount for publisher (This Enter discount for publisher (This will be the will be the lowest discount that you lowest discount that you will offer during the will offer during the term of the term of the contract) contract) COTS Discount % COTS Discount % Title Price Adobe 0.00% Adobe 0.00% Adobe Acrobat Professional Version 9 Windows 218.33 Autodesk 0.00% Autodesk 0.00% Adobe Photoshop CS4 Windows 635.24 Citrix 0.00% Citrix 0.00% Autodesk Sketchbook 2009 Pro 120 Corel 0.00% Corel 0.00% McAfee Active Virus Defense 14.87 DoubleTake 0.00% DoubleTake 0.00% Symantec Norton Antivirus 2009 25 Intuit 0.00% Intuit 0.00% Symantec Backup Exec 12.5 for Windows Servers 454.25 McAfee 0.00% McAfee 0.00% PRICE FOR ABOVE TITLES SHOULD BE Novell 0.00% Novell 0.00% QUOTED FOR PURCHASE OF ONE (1) COPY Nuance 0.00% Nuance 0.00% Quark Software 0.00% Quark Software 0.00% Quest Software 0.00% Quest Software 0.00% Riverdeep 0.00% Riverdeep 0.00% Academic Pricing Symantec 0.00% Symantec 0.00% Title Price Trend Micro 0.00% Trend Micro 0.00% Adobe Acrobat Professional Version 9 Windows 131.03 VMWare 0.00% VMWare 0.00% Adobe Photoshop CS4 Windows 276.43 WebSense 0.00% WebSense 0.00% Autodesk Sketchbook 2009 Pro 120 McAfee Active Virus Defense 14.87 Symantec Norton Antivirus 2009 25 Symantec Backup Exec 12.5 for Windows Servers 454.25 PRICE FOR ABOVE TITLES SHOULD BE QUOTED FOR PURCHASE OF ONE (1) COPY LICENSE AND MEDIA For purposes of evaluation VITA will create a market basket. -

Listener Q&A #8
Transcript of Episode #44 Listener Feedback Q&A #8 Description: Steve and Leo discuss questions asked by listeners of their previous episodes. They tie up loose ends, explore a wide range of topics that are too small to fill their own episode, clarify any confusion from previous installments, and present real world “application notes" for any of the security technologies and issues they have previously discussed. High quality (64 kbps) mp3 audio file URL: http://media.GRC.com/sn/SN-044.mp3 Quarter size (16 kbps) mp3 audio file URL: http://media.GRC.com/sn/sn-044-lq.mp3 Leo Laporte: Bandwidth for Security Now! is provided by AOL Radio at AOL.com/podcasting. This is Security Now! with Steve Gibson, Episode 44 for June 15, 2006: Your questions, Steve’s answers. Security Now! is brought to you by Astaro, makers of the Astaro Security Gateway, on the web at www.astaro.com. I smell a mod 4 episode. I do indeed. Leo Laporte here, Steve Gibson in Irvine, and it’s Episode 44. And as far as I can tell, that’s divisible by 4. Steve Gibson: That’s like a double mod 4. Leo: That’s a double mod 4. Steve: Yeah. Leo: So we get our usual 20 questions. Steve: It’s even mod 11. Leo: Mod 11, mod 4, mod 2, mod 0... Steve: Mod 22. Yeah. Leo: All right. You math showoff. Let’s get to the questions, unless there’s anything we want to cover from our last episode, where we talked all about ports. -

Windows Antivirus Support Chart for Hostscan 3.1.06073 Product Name
Windows Antivirus Support Chart for HostScan 3.1.06073 Marketing Product Data File Engine Live Version Check RTP Set RTP Language Alias Name Time Version Update Names 360Safe.co m 360 1.x ✔ ✔ ✔ ✔ ✔ English 360杀毒 Antivirus 360 3.x ✔ ✘ ✔ ✘ ✘ English Antivirus 360 Total 4.x ✔ ✔ ✔ ✘ ✘ English Security Chinese 360 360杀毒 1.x ✔ ✔ ✔ ✘ ✘ Simplified Antivirus Chinese 360 360杀毒 2.x ✔ ✔ ✔ ✘ ✘ Simplified Antivirus Chinese 360杀毒 3.x ✘ ✘ ✔ ✘ ✘ Simplified Chinese 360 360杀毒 4.x ✘ ✘ ✔ ✘ ✘ Simplified Antivirus Chinese 360 360杀毒 5.x ✘ ✘ ✔ ✘ ✘ Simplified Antivirus Other 360Safe.co x ✘ ✘ ✘ ✘ ✘ English m Antivirus AEC, spol. s r.o. TrustPort 2.x ✘ ✘ ✔ ✔ ✘ English Antivirus Other AEC, spol. s r.o. x ✘ ✘ ✘ ✘ ✘ English Antivirus Agnitum Ltd. Outpost Antivirus 7.x ✔ ✔ ✔ ✔ ✘ English Pro Outpost Antivirus 8.x ✔ ✔ ✔ ✔ ✘ English Pro Outpost Antivirus 9.x ✔ ✔ ✔ ✔ ✔ English Pro Outpost Outpost Security Antivirus 6.x ✔ ✔ ✔ ✔ ✘ English Suite Pro Pro 2009 2009 Outpost Security 7.x ✘ ✘ ✔ ✘ ✘ English Suite Free Outpost Security 7.x ✔ ✔ ✔ ✔ ✘ English Suite Pro Outpost Security 8.x ✔ ✔ ✔ ✔ ✔ English Suite Pro Outpost Security 9.x ✔ ✔ ✔ ✔ ✔ English Suite Pro Other Agnitum x ✘ ✘ ✘ ✘ ✘ English Ltd. Antivirus AhnLab, Inc. AhnLab Security 2.x ✔ ✔ ✘ ✔ ✘ English Pack AhnLab V3 Internet 7.x ✔ ✔ ✔ ✔ ✘ English Security 2007 AhnLab V3 Internet Security 7.x ✔ ✔ ✔ ✔ ✘ English 2007 Platinum AhnLab V3 Internet Security 7.x ✔ ✔ ✔ ✔ ✘ English 2008 Platinum AhnLab V3 Internet Security 7.x ✔ ✔ ✔ ✔ ✔ English 2009 Platinum AhnLab V3 Internet Security 7.0 7.x ✔ ✔ ✔ ✔ ✘ English Platinum Enterprise AhnLab V3 Internet 8.x ✔ ✔ ✔ ✔ ✔ English Security 8.0 AhnLab V3 Internet 9.x ✔ ✔ ✔ ✔ ✔ English Security 9.0 AhnLab V3 VirusBlock Internet 7.x ✔ ✔ ✘ ✔ ✘ English Security 2007 AhnLab V3 VirusBlock Internet Security 7.x ✔ ✔ ✔ ✘ ✔ English 2007 Platinum Enterprise V3 Click 1.x ✔ ✘ ✘ ✘ ✘ English V3 Lite 1.x ✔ ✔ ✔ ✔ ✔ Korean V3 Lite 3.x ✔ ✔ ✔ ✘ ✘ Korean V3 VirusBlock 6.x ✔ ✔ ✘ ✘ ✘ English 2005 V3 ウイルスブ NA ✔ ✔ ✘ ✔ ✘ Japanese ロック V3Pro 2004 6.x ✔ ✔ ✔ ✔ ✘ English Other AhnLab, x ✘ ✘ ✘ ✘ ✘ English Inc.