Network Forensics: a Comprehensive Review of Tools and Techniques
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A Decryption Process for Android Database Forensics
International Journal of Computer Sciences and Engineering Open Access Research Paper Vol.-7, Issue-3, March 2019 E-ISSN: 2347-2693 A Decryption Process for Android Database Forensics Nibedita Chakraborty1*, Krishna Punwar2 1,2Dept. of Information Technology and Telecommunication, Raksha Shakti University, Ahmedabad, India *Corresponding Author: [email protected], Tel.: 7980118774 DOI: https://doi.org/10.26438/ijcse/v7i3.2326 | Available online at: www.ijcseonline.org Accepted: 18/Mar/2019, Published: 31/Mar/2019 Abstract— Nowadays, Databases are mostly usable in business applications and financial transactions in Banks. Most of the database servers stores confidential and sensitive information of a mobile device. Database forensics is the part of digital forensics especially for the investigation of different databases and the sensitive information stored on a database. Mobile databases are totally different from the major database and are very platform independent as well. Even if they are not attached to the central database, they can still linked with the major database to drag and change the information stored on this. SQLite Database is mostly needed by Android application development. SQLite is a freely available database management system which is specially used to perform relational functional and it comes inbuilt with android to perform database functions on android appliance. This paper will show how a message can be decrypted by using block cipher modes and which mode is more secured and fast. Keywords—Database Forensics,Mobile Device ,Android,SQLite, Modes, Tools I. INTRODUCTION In android mobile phone device, SQLite is mainly based on ACID properties docile relational database management Database is an assemble form of interrelated data which is system. -

Implementing Cisco Cyber Security Operations
2019 CLUS Implementing Cisco Cyber Security Operations Paul Ostrowski / Patrick Lao / James Risler Cisco Security Content Development Engineers LTRCRT-2222 2019 CLUS Cisco Webex Teams Questions? Use Cisco Webex Teams to chat with the speaker after the session How 1 Find this session in the Cisco Live Mobile App 2 Click “Join the Discussion” 3 Install Webex Teams or go directly to the team space 4 Enter messages/questions in the team space Webex Teams will be moderated cs.co/ciscolivebot#LTRCRT-2222 by the speaker until June 16, 2019. 2019 CLUS © 2019 Cisco and/or its affiliates. All rights reserved. Cisco Public 3 Agenda • Goals and Objectives • Prerequisite Knowledge & Skills (PKS) • Introduction to Security Onion • SECOPS Labs and Topologies • Access SECFND / SECOPS eLearning Lab Training Environment • Lab Evaluation • Cisco Cybersecurity Certification and Education Offerings 2019 CLUS LTRCRT-2222 © 2019 Cisco and/or its affiliates. All rights reserved. Cisco Public 4 Goals and Objectives: • Today's organizations are challenged with rapidly detecting cybersecurity breaches in order to effectively respond to security incidents. Cybersecurity provides the critical foundation organizations require to protect themselves, enable trust, move faster, add greater value and grow. • Teams of cybersecurity analysts within Security Operations Centers (SOC) keep a vigilant eye on network security monitoring systems designed to protect their organizations by detecting and responding to cybersecurity threats. • The goal of Cisco’s CCNA Cyber OPS (SECFND / SECOPS) courses is to teach the fundamental skills required to begin a career working as an associate/entry-level cybersecurity analyst within a threat centric security operations center. • This session will provide the student with an understanding of Security Onion as an open source network security monitoring tool (NSM). -

Design Document for IP Fabrics
Design Document for IP Fabrics Author: May06-15 (Network Forensic UI) Andy Heintz (Communication Leader) Abraham Devine (Webmaster) Altay Ozen (Team Leader and Team Key Concept Holder) Dr. Joseph Zambreno (Adviser) Curt Schwaderer (Client) Version Date Author Change 1.0 10/26 AH Created initial version of design document 2.0 11/23 AH Created final version of design document Table of Contents 1 Problem Statement.................................................................................................................... 3 2 System Design ........................................................................................................................... 4 2.1 System Requirements................................................................................................................................ 4 2.2 Functional Requirements .......................................................................................................................... 4 2.3 Functional Decomposition ........................................................................................................................ 5 2.4 System Analysis ....................................................................................................................................... 6 3 Detailed Design ......................................................................................................................... 7 3.1 Input / Output Specification ..................................................................................................................... -

Hands-On Network Forensics, FIRST 2015
2015-04-30 WWW.FORSVARSMAKTEN.SE Hands-on Network Forensics Workshop Preparations: 1. Unzip the virtual machine from NetworkForensics_ VirtualBox.zip on your EXTENSIVE USE OF USB thumb drive to your local hard drive COMMAND LINE 2. Start VirtualBox and run the Security Onion VM IN THIS WORKSHOP 3. Log in with: user/password 1 FM CERT 2015-04-30 WWW.FORSVARSMAKTEN.SE Hands-on Network Forensics Erik Hjelmvik, Swedish Armed Forces CERT FIRST 2015, Berlin 2 FM CERT 2015-04-30 WWW.FORSVARSMAKTEN.SE Hands-on Network Forensics Workshop Preparations: 1. Unzip the virtual machine from NetworkForensics_ VirtualBox.zip on your EXTENSIVE USE OF USB thumb drive to your local hard drive COMMAND LINE 2. Start VirtualBox and run the Security Onion VM IN THIS WORKSHOP 3. Log in with: user/password 3 FM CERT 2015-04-30 WWW.FORSVARSMAKTEN.SE ”Password” Ned 4 FM CERT 2015-04-30 WWW.FORSVARSMAKTEN.SE SysAdmin: Homer 5 FM CERT 2015-04-30 WWW.FORSVARSMAKTEN.SE PR /Marketing: Krusty the Clown 6 FM CERT 2015-04-30 WWW.FORSVARSMAKTEN.SE Password Ned AB = pwned.se 7 FM CERT 2015-04-30 WWW.FORSVARSMAKTEN.SE pwned.se Network [INTERNET] | Default Gateway 192.168.0.1 PASSWORD-NED-XP www.pwned.se | 192.168.0.53 192.168.0.2 [TAP]--->Security- | | | Onion -----+------+---------+---------+----------------+------- | | Homer-xubuntu Krustys-PC 192.168.0.51 192.168.0.54 8 FM CERT 2015-04-30 WWW.FORSVARSMAKTEN.SE Security Onion 9 FM CERT 2015-04-30 WWW.FORSVARSMAKTEN.SE Paths (also on Cheat Sheet) • PCAP files: /nsm/sensor_data/securityonion_eth1/dailylogs/ • Argus files: -

Network Intell: Enabling the Non-Expert Analysis of Large Volumes of Intercepted Network Traffic
Chapter 1 NETWORK INTELL: ENABLING THE NON- EXPERT ANALYSIS OF LARGE VOLUMES OF INTERCEPTED NETWORK TRAFFIC Erwin van de Wiel, Mark Scanlon and Nhien-An Le-Khac Abstract In criminal investigations, telecommunication wiretaps have become a common technique used by law enforcement. While phone-based wire- tapping is well documented and the procedure for their execution are well known, the same cannot be said for Internet taps. Lawfully inter- cepted network traffic often contains a lot of encrypted traffic making it increasingly difficult to find useful information inside the traffic cap- tured. The advent of Internet-of-Things further complicates the pro- cess for non-technical investigators. The current level of complexity of intercepted network traffic is close to a point where data cannot be analysed without supervision of a digital investigator with advanced network knowledge. Current investigations focus on analysing all traffic in a chronological manner and are predominately conducted on the data contents of the intercepted traffic. This approach often becomes overly arduous when the amount of data to be analysed becomes very large. In this paper, we propose a novel approach to analyse large amounts of intercepted network traffic based on network metadata. Our approach significantly reduces the duration of the analysis and also produces an arXiv:1712.05727v2 [cs.CR] 27 Jan 2018 insight view of analysing results for the non-technical investigator. We also test our approach with a large sample of network traffic data. Keywords: Network Investigation, Big Data Forensics, Intercepted Network Traffic, Internet tap, Network Metadata Analysis, Non-Technical Investigator. 1. Introduction Lawful interception is a method that is used by the police force in some countries in almost all middle-to high-level criminal investigations. -

Part 1 Digital Forensics Module Jaap Van Ginkel Silvio Oertli
Part 1 Digital Forensics Module Jaap van Ginkel Silvio Oertli July 2016 Agenda • Part 1: Introduction – Definitions / Processes • Part 2: Theory in Practice – From planning to presentation • Part 3: Live Forensics – How to acquire a memory image – Investigate the image • Part 4: Advanced Topics – Tools – Where to go from here – And more 2 Disclaimer§ • A one or two-day course on forensics will not make you a forensics expert. – Professionals spend most of their working time performing forensic analysis and thus become an expert. • All we can offer is to shed some light on a quickly developing and broad field and a chance to look at some tools. • We will mostly cover Open Source Forensic Tools. 3 Introduction Forensics in History 4 Forensics – History 2000 BC 1200 BC 5 Introduction Definitions / Processes 6 Forensics – The Field digital forensics Computer Forensics Disk Forensics Mobil Forensics Memory Forensics Datenbase Forensics Live Forensics Network Forensics 7 Forensics - Definition • Digital Forensics [1]: – Digital forensics (sometimes known as digital forensic science) is a branch of forensic science encompassing the recovery and investigation of material found in digital devices, often in relation to computer crime. • Computer Forensics [2]: – Computer forensics (sometimes known as computer forensic science) is a branch of digital forensic science pertaining to legal evidence found in computers and digital storage media. The goal of computer forensics is to examine digital media in a forensically sound manner with the aim of identifying, preserving, recovering, analyzing and presenting facts and opinions about the information. 8 Forensics - Definitions • Network Forensics [3]: – Network forensics is a sub-branch of digital forensics relating to the monitoring and analysis of computer network traffic for the purposes of information gathering, legal evidence, or intrusion detection.[1] Unlike other areas of digital forensics, network investigations deal with volatile and dynamic information. -

CIT 485: Network Forensics
CIT 485/585 Network Forensics The primary objective of this assignment is to learn a process for investigating security incidents and to give students practice analyzing such an incident using captured network data. 1S TUDENT LEARNING OUTCOMES 1. Describe digital evidence and how the type of legal dispute affects evidence used to resolve it. 2. Describe the steps of the OSCAR network forensics methodology. 3. Identify and decode protocols used on non-standard ports. 4. Investigate suspicious network data for malicious activity. 2D IGITAL EVIDENCE Digital evidence refers to any data collected in digital form from any computer, whether that computer is a desktop, mobile device, game console, printer, or IoT device. A primary goal of digital forensics is ensuring evidence integrity, the preservation of evidence in its original form. Evidence integrity is supported by a chain of custody, a set of documentation that describes the acquisition, copying, and analysis of digital evidence. As analysis of digital data often changes that data (reading a file will not modify the file itself but will change the last accessed time on the file), cryptographic checksums such as SHA-256 are often used to ensure that copies of digital evidence match the original evidence. Details of digital evidence handling are discussed in CIT 430: Computer Forensics. Digital evidence in a criminal case is returned through an inventory of items take through a search warrant. Any devices that may contain an embedded computer can contain digital evidence. Defense attorneys can request an invetory of items and obtain forensic copies of the data from those devices. -
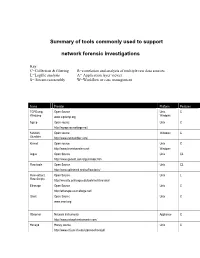
Network Forensic Tools Sidebar
Summary of tools commonly used to support network forensic investigations Key: C=Collection & filtering R=correlation and analysis of multiple raw data sources L=Logfile analysis A= Application layer viewer S= Stream reassembly W=Workflow or case management Name Provider Platform Features TCPDump, Open Source Unix, C Windump www.tcpdump.org Windows Ngrep Open source Unix C http://ngrep.sourceforge.net/ Network Open source Windows C Stumbler http://www.netstumbler.com/ Kismet Open source Unix C http://www.kismetwireless.net Windows Argus Open Source Unix CL http://www.qosient.com/argus/index.htm Flow-tools Open Source Unix CL http://www.splintered.net/sw/flow-tools/ Flow-extract, Open Source Unix L Flow Scripts http://security.uchicago.edu/tools/net-forensics/ Etherape Open Source Unix C http://etherape.sourceforge.net/ Snort Open Source Unix C www.snort.org Observer Network Instruments Appliance C http://www.networkinstruments.com/ Honeyd Honey source Unix C http://www.citi.umich.edu/u/provos/honeyd/ Ethereal Open Source Windows CLS www.Ethereal.com Unix Etherpeek Wild Packets, Inc. Windows CLS www.wildpackets.com SecureNet Intrusion Inc. Windows with CS http://www.intrusion.com collector appliance FLAG Open Source Unix L Forensic and http://www.dsd.gov.au/library/software/flag/ Log Analysis GUI ACID Analysis Console for Intrusion Databases Unix L http://www.andrew.cmu.edu/~rdanyliw/snort/snortacid.html Shadow http://www.nswc.navy.mil/ISSEC/CID/index.html Unix LS DeepNines and http://www.deepnines.com/sleuth9.html Unix CSR Sleuth9 Infinistream -

Network Forensics
Network Forensics Michael Sonntag Institute of Networks and Security What is it? Evidence taken from the “network” In practice this means today the Internet (or LAN) In special cases: Telecommunication networks (as long as they are not yet changed to VoIP!) Typically not available “after the fact” Requires suspicions and preparation in advance Copying the communication content At the source (=within the suspects computer): “Online search” This could also be a webserver, e.g. if it contains illegal content “Source” does NOT mean that this is the client/initiator of communication/… At the destination: See some part of the traffic Only if unavoidable or the only interesting part Somewhere on the way of the (all?) traffic: ISP, physically tapping the wires, home routers etc. Network Forensics 2 Problems of network forensics “So you have copied some Internet traffic – but how is it linked to the suspect?” The IP addresses involved must be tied to individual persons This might be easy (location of copying) or very hard “When did it take place?” Packet captures typically have only relative timestamps But there may be lots of timestamps in the actual traffic! As supporting evidence to some external documentation “Is it unchanged?” These are merely packets; their content can be changed Although it is possible to check e.g. checksums, this is a lot of work and normally not done Treat as any other digital evidence Hash value + Chain of Custody; work on copies only Network Forensics 3 Scenario Suspect: Mallory Malison; released -

Digital Forensics Based Analysis of Mobile Phones
Journal of Android and IOS Applications and Testing Volume 4 Issue 3 Digital Forensics Based Analysis of Mobile Phones Pooja V Chavan PG Student, Department of Computer Engineering, K. J. Somaiya College of Engineering, Mumbai, Maharashtra, India Email: [email protected] DOI: Abstract Now-a-day’s ratio of mobile phone is increasing day by day. Digital forensics methodology is use to recover and investigate data that found in a digital devices. Mobile phone usage is more that’s why not only judicial events occurred but also mobile forensics and subdivision of digital forensics are emerged. Some hardware and software are used for mobile phone investigations. Keywords: Digital forensics, digital devices, mobile phone INTRODUCTION because electronic device have a variety of Forensic science’s subdivision is a digital different operating system, technology, forensic, is a one type of process. The storage structure, Features. First identify main objective of this process to find the crime after that digital forensic work evidence in digital devices [1]. Digital on four important steps (Figure 1): forensics are used for the analysis of data, such as audio, video, pictures, etc. After • Collection: The collected of evidence the analysis of electronic devices data that like fingerprints, broken fingernails help for legal process. The usage of blood and body fluids. advanced technology is increasing rapidly. • Examination: The examination of Electronic device have a variety of product process is depending on evidence. like tablet, flash memory, memory card, • Analysis: The crime scenes obtain SD card, etc. When forensic analysis is different digital evidence, analysis is performed at that time data should be done on storage evidence this secure. -

Guide to Computer Forensics and Investigations Fourth Edition
Guide to Computer Forensics and Investigations Fourth Edition Chapter 11 Virtual Machines, Network Forensics, and Live Acquisitions Objectives • Describe primary concerns in conducting forensic examinations of virtual machines • Describe the importance of network forensics • Explain standard procedures for performing a live acquisition • Explain standard procedures for network forensics • Describe the use of network tools Guide to Computer Forensics and Investigations 2 Virtual Machines Overview • Virtual machines are important in today’s networks. • Investigators must know how to detect a virtual machine installed on a host, acquire an image of a virtual machine, and use virtual machines to examine malware. Virtual Machines Overview (cont.) • Check whether virtual machines are loaded on a host computer. • Check Registry for clues that virtual machines have been installed or uninstalled. Network Forensics Overview • Network forensics – Systematic tracking of incoming and outgoing traffic • To ascertain how an attack was carried out or how an event occurred on a network • Intruders leave trail behind • Determine the cause of the abnormal traffic – Internal bug – Attackers Guide to Computer Forensics and Investigations 5 Securing a Network • Layered network defense strategy – Sets up layers of protection to hide the most valuable data at the innermost part of the network • Defense in depth (DiD) – Similar approach developed by the NSA – Modes of protection • People • Technology • Operations Guide to Computer Forensics and Investigations -

Contents in Detail
CONTENTS IN DETAIL ACKNOWLEDGMENTS xv INTRODUCTION xvii Why This Book? .....................................................................................................xvii Concepts and Approach ........................................................................................xviii How to Use This Book ............................................................................................. xix About the Sample Capture Files ................................................................................ xx The Rural Technology Fund ....................................................................................... xx Contacting Me ........................................................................................................ xx 1 PACKET ANALYSIS AND NETWORK BASICS 1 Packet Analysis and Packet Sniffers ............................................................................. 2 Evaluating a Packet Sniffer ............................................................................ 2 How Packet Sniffers Work............................................................................. 3 How Computers Communicate.................................................................................... 4 Protocols ..................................................................................................... 4 The Seven-Layer OSI Model .......................................................................... 5 Data Encapsulation .....................................................................................