15.3 AJAX 633 Making Asynchronous Requests 636 Complete Control Over AJAX 642 Cross-Origin Resource Sharing (CORS) 643
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Advances in the Application of Information and Communication Technologies in Healthcare at the Patient's Home
Advances in the application of information and communication technologies in healthcare at the patient's home Valentina Isetta Aquesta tesi doctoral està subjecta a la llicència Reconeixement- CompartIgual 3.0. Espanya de Creative Commons. Esta tesis doctoral está sujeta a la licencia Reconocimiento - CompartirIgual 3.0. España de Creative Commons. This doctoral thesis is licensed under the Creative Commons Attribution-ShareAlike 3.0. Spain License. ADVANCES IN THE APPLICATION OF INFORMATION AND COMMUNICATION TECHNOLOGIES IN HEALTH CARE AT THE PATIENT'S HOME Memòria presentada per Valentina Isetta per optar al títol de Doctora Director de la tesi: Dr. Ramon Farré Ventura Unitat de Biofísica i Bioenginyeria Facultat de Medicina Universitat de Barcelona If you put your mind to it, you can accomplish anything. Marty McFly, “Back to the future”, 1985 ACKNOWLEDGMENTS I would like to thank all the people that supported me in these intense years of work. First of all, my gratitude goes to Prof. Ramon Farré, for his solid trust since my early beginning in Barcelona and for seeing in me a researcher that I never imagined I could be. Many thanks to Dr. Josep M. Montserrat, for his irreplaceable mentoring in the clinical world and for his advice and affection. Thanks also to all his medical and nursing staff of the Sleep Lab of the Hospital Clinic of Barcelona, where I have learned a lot and I have felt as another team member. A special thank to Carmen Lopez, for her affectionate help and splendid work to create “Petits a casa”. Without her tenacity and the collaboration of all nursing and medical staff of the Hospital de Sant Pau Neonatology department this successful service to the community would not exist. -

Modern Javascript: Develop and Design Larry Ullman
TEMPORAry SPINE WIDTH: 0.000” Designer-Developers are hot commodities today. But how do you build your development chops fast enough to join their ranks? With Peachpit’s Develop and Design series for visual learners. Modern Modern JavaScript DEVELOP AND DESIGN Modern JavaScript JavaScript IT’S TIME FOR A CURRENT, DEFINITIVE JAVASCRIPT BOOK, “A breath of fresh air in the over-complicated and in this comprehensive beginner’s guide, bestselling author world of JavaScript books. This is one I’ll keep DEVELOP AND DESIGN close by!” Larry Ullman teaches the language as it is implemented today. Jay Blanchard Larry demonstrates how to build upon JavaScript’s ease of use, Web developer and consultant and author of while demystifying its often-cryptic syntax, especially for those Applied jQuery: Develop and Design who have not programmed before. This book enforces modern JavaScript’s best practices and embraces key Web development THIS BOOK INCLUDES: approaches such as progressive enhancement and unobtrusive J Easy step-by-step instruction, ample scripting. The author demonstrates loads of real-world code illustrations, and clear examples DEVELOP and makes it freely available for download. J Real-world techniques to build your You’ll learn about JavaScript itself and the relationship between skills JavaScript and HTML. Next you’ll explore variables, common J Insight into best practices from a operators, and control structures. Then you’ll create functions, veteran Web expert AND handle events, and do more with HTML forms. You’ll master J Emphasis on strategies for creating Ajax, work with frameworks, and use JavaScript with PHP to reliable code that will work on all of create a complete example. -

Marketing Cloud Published: August 12, 2021
Marketing Cloud Published: August 12, 2021 The following are notices required by licensors related to distributed components (mobile applications, desktop applications, or other offline components) applicable to the services branded as ExactTarget or Salesforce Marketing Cloud, but excluding those services currently branded as “Radian6,” “Buddy Media,” “Social.com,” “Social Studio,”“iGoDigital,” “Predictive Intelligence,” “Predictive Email,” “Predictive Web,” “Web & Mobile Analytics,” “Web Personalization,” or successor branding, (the “ET Services”), which are provided by salesforce.com, inc. or its affiliate ExactTarget, Inc. (“salesforce.com”): @formatjs/intl-pluralrules Copyright (c) 2019 FormatJS Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation files (the "Software"), to deal in the Software without restriction, including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense, and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do so, subject to the following conditions: The above copyright notice and this permission notice shall be included in all copies or substantial portions of the Software. THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER -

THE FUTURE of SCREENS from James Stanton a Little Bit About Me
THE FUTURE OF SCREENS From james stanton A little bit about me. Hi I am James (Mckenzie) Stanton Thinker / Designer / Engineer / Director / Executive / Artist / Human / Practitioner / Gardner / Builder / and much more... Born in Essex, United Kingdom and survived a few hair raising moments and learnt digital from the ground up. Ok enough of the pleasantries I have been working in the design field since 1999 from the Falmouth School of Art and onwards to the RCA, and many companies. Ok. less about me and more about what I have seen… Today we are going to cover - SCREENS CONCEPTS - DIGITAL TRANSFORMATION - WHY ASSETS LIBRARIES - CODE LIBRARIES - COST EFFECTIVE SOLUTION FOR IMPLEMENTATION I know, I know, I know. That's all good and well, but what does this all mean to a company like mine? We are about to see a massive change in consumer behavior so let's get ready. DIGITAL TRANSFORMATION AS A USP Getting this correct will change your company forever. DIGITAL TRANSFORMATION USP-01 Digital transformation (DT) – the use of technology to radically improve performance or reach of enterprises – is becoming a hot topic for companies across the globe. VERY DIGITAL CHANGING NOT VERY DIGITAL DIGITAL TRANSFORMATION USP-02 Companies face common pressures from customers, employees and competitors to begin or speed up their digital transformation. However they are transforming at different paces with different results. VERY DIGITAL CHANGING NOT VERY DIGITAL DIGITAL TRANSFORMATION USP-03 Successful digital transformation comes not from implementing new technologies but from transforming your organisation to take advantage of the possibilities that new technologies provide. -

Making Speech Recognition Work on the Web Christopher J. Varenhorst
Making Speech Recognition Work on the Web by Christopher J. Varenhorst Submitted to the Department of Electrical Engineering and Computer Science in partial fulfillment of the requirements for the degree of Masters of Engineering in Computer Science and Engineering at the MASSACHUSETTS INSTITUTE OF TECHNOLOGY May 2011 c Massachusetts Institute of Technology 2011. All rights reserved. Author.................................................................... Department of Electrical Engineering and Computer Science May 20, 2011 Certified by . James R. Glass Principal Research Scientist Thesis Supervisor Certified by . Scott Cyphers Research Scientist Thesis Supervisor Accepted by . Christopher J. Terman Chairman, Department Committee on Graduate Students Making Speech Recognition Work on the Web by Christopher J. Varenhorst Submitted to the Department of Electrical Engineering and Computer Science on May 20, 2011, in partial fulfillment of the requirements for the degree of Masters of Engineering in Computer Science and Engineering Abstract We present an improved Audio Controller for Web-Accessible Multimodal Interface toolkit { a system that provides a simple way for developers to add speech recognition to web pages. Our improved system offers increased usability and performance for users and greater flexibility for developers. Tests performed showed a %36 increase in recognition response time in the best possible networking conditions. Preliminary tests shows a markedly improved users experience. The new Wowza platform also provides a means of upgrading other Audio Controllers easily. Thesis Supervisor: James R. Glass Title: Principal Research Scientist Thesis Supervisor: Scott Cyphers Title: Research Scientist 2 Contents 1 Introduction and Background 7 1.1 WAMI - Web Accessible Multimodal Toolkit . 8 1.1.1 Existing Java applet . 11 1.2 SALT . -

Zen Flash Gallery Userguide
Zen Flash Gallery version 1.1 User Guide 0 Contents Starting the Work 2 Publishing the gallery on your website 2 Configuring the Gallery 4 XML File Format 5 Gallery Parameters 6 Localization 8 1 Starting the Work To start working simply paste object’s HTML into your page and setup xml configuration file. You can place configuration file anywhere on your server. Publishing the gallery on your website To ensure smooth operation of a gallery on your website you need to have the following files: 1. SWF-file (GalleryName.swf) – flash gallery file 2. XML-file (gallery.xml) – gallery configuration file 3. HTML-file (GalleryName.html) – this file shows how to paste the gallery code into the HTML-page on your site where you plan to use the gallery. 4. <Images> folder where you should place your images. 5. SWFObject.js – a special JavaScript for the correct display of your gallery. In the gallery distribution file (the downloaded archive) there is already a working example for which you can change the settings as you see fit and upload it to your site. Let’s analyze the gallery publishing procedure step by step: 1. On your computer open the folder where you extracted the gallery distribution file. 2. Copy an image that you want to use in your gallery to <Images> folder (some sample images are saved there already, which you may delete). 3. Set the appearance of your gallery, define the path to the images in your gallery and write the names of the files with your images in the settings file (XML-file). -

Slideshowpro for Flash Customization Guide
SlideShowPro for Flash Customization Guide (Version 1.8.x) Contents Introduction.......................................................................................................................................................................................3 Customization.basics....................................................................................................................................................................4 How.to:.SlideShowPro.for.Flash.Button.Packs..................................................................................................................5 How.to:.Custom.navigation.buttons...................................................................................................................................... 7 How.to:.Embed.SWF.in.a.separate.HTML.document.....................................................................................................9 How.to:.External.navigation.....................................................................................................................................................12 How.To:.Change.default.English.text....................................................................................................................................13 How.to:.Prevent.XML.caching................................................................................................................................................. 14 How.to:.Dynamically.assign.an.XML.file..............................................................................................................................15 -

Enterprise Development with Flex
Enterprise Development with Flex Enterprise Development with Flex Yakov Fain, Victor Rasputnis, and Anatole Tartakovsky Beijing • Cambridge • Farnham • Köln • Sebastopol • Taipei • Tokyo Enterprise Development with Flex by Yakov Fain, Victor Rasputnis, and Anatole Tartakovsky Copyright © 2010 Yakov Fain, Victor Rasputnis, and Anatole Tartakovsky.. All rights reserved. Printed in the United States of America. Published by O’Reilly Media, Inc., 1005 Gravenstein Highway North, Sebastopol, CA 95472. O’Reilly books may be purchased for educational, business, or sales promotional use. Online editions are also available for most titles (http://my.safaribooksonline.com). For more information, contact our corporate/institutional sales department: (800) 998-9938 or [email protected]. Editor: Mary E. Treseler Indexer: Ellen Troutman Development Editor: Linda Laflamme Cover Designer: Karen Montgomery Production Editor: Adam Zaremba Interior Designer: David Futato Copyeditor: Nancy Kotary Illustrator: Robert Romano Proofreader: Sada Preisch Printing History: March 2010: First Edition. Nutshell Handbook, the Nutshell Handbook logo, and the O’Reilly logo are registered trademarks of O’Reilly Media, Inc. Enterprise Development with Flex, the image of red-crested wood-quails, and related trade dress are trademarks of O’Reilly Media, Inc. Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in this book, and O’Reilly Media, Inc. was aware of a trademark claim, the designations have been printed in caps or initial caps. While every precaution has been taken in the preparation of this book, the publisher and authors assume no responsibility for errors or omissions, or for damages resulting from the use of the information con- tained herein. -

Third Party Library Attributions
Third Party Library Attributions Table of Contents 1. Summary 2. PureWeb® Software Third Party Library Attributions 3. PureWeb iOS Client Libraries 3.1. Cocoa Lumberjack Framework 3.2. Sodium Crypto Library 4. ResolutionMD Server Libraries 4.1. Apache Commons 4.2. Apache PDFBox 4.3. Apache HttpComponents 4.4. Arial Unicode Font 4.5. Auto 4.6. Boost 4.7. Bootstrap 4.8. Cairo 4.9. CanJS 4.10. Curl 4.11. dcm4che2 4.12. dcm4che3 4.13. dcm4che5 4.14. DCMTK 4.15. Drools Expert 4.16. Eclipse Implementation of JAXB 4.17. Eclipse Metro 4.18. Eclipse ORB 4.19. Eclipse Project for JAX-WS 4.20. FFmpeg 4.21. FreeMarker 4.22. Freetype 4.23. FTGL 4.24. Glew 4.25. google-api-java-client 4.26. google-api-java-client-services 4.27. google-code-prettify 4.28. google-http-java-client 4.29. google-oauth-java-client 4.30. grcp-java 4.31. guava 4.32. html5shiv 4.33. HAPI 4.34. ICU 4.35. ITK 4.36. Java implementation of JSON Web Token (JWT) 4.37. Jersey 4.38. Joda-Time 4.39. jQuery 4.40. jQuery File Upload Plugin 4.41. jQuery Hashchange 4.42. jQuery UI 4.43. JSON Web Token support for the JVM 4.44. jsoup Java HTML Parser 4.45. Lo-Dash 4.46. libpng 4.47. llvm 4.48. logback 4.49. Mesa 3D Graphics Library 4.50. minizip 4.51. PixelMed 4.52. opencensus-java 4.53. requirejs 4.54. SLF4J 4.55. wysihtml5 4.56. zlib 5. -
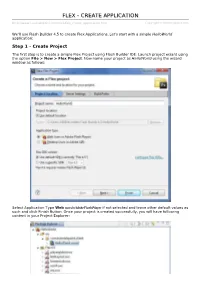
Flex Create Application
FFLLEEXX -- CCRREEAATTEE AAPPPPLLIICCAATTIIOONN http://www.tutorialspoint.com/flex/flex_create_application.htm Copyright © tutorialspoint.com We'll use Flash Builder 4.5 to create Flex Applications. Let's start with a simple HelloWorld application: Step 1 - Create Project The first step is to create a simple Flex Project using Flash Builder IDE. Launch project wizard using the option File > New > Flex Project. Now name your project as HelloWorld using the wizard window as follows: Select Application Type Web runsinAdobeFlashPlayer if not selected and leave other default values as such and click Finish Button. Once your project is created successfully, you will have following content in your Project Explorer: Here is brief description of all important folders: Folder Location table table- bordered Source code mxml/asclasses files. We've created com/tutorialspoint/client folder structure containing the client-side specific java classes responsible for client UI display. bin-debug This is the output part, it represents the actual deployable web application. history folder contains support files for history management of Flex application. framework_xxx.swf, flex framework files to be used by flex application. HelloWorld.html, wrapper/host HTML File for flex application. HelloWorld.swf, our flex based application. playerProductInstall.swf, flash player express installer. spark_xxx.swf, library for spark component support. swfobject.js, javascript responsible to load HelloWorld.swf in HelloWorld.html. It checks flash player version and passes initialization parameter to HelloWorld.swf file. textLayout_xxx.swf, library for text component support. html- template This represents the configurable web application. Flash Builder compiles files from html-template to bin-debug folder. history folder contains support files for history management of Flex application. -

Wordpress and Flash 10X Cookbook [Spannagle &
Wordpress and Flash 10x Cookbook Over 50 simple and incredibly effective recipes to take control of dynamic Flash content in Wordpress Peter Spannagle Sarah Soward BIRMINGHAM - MUMBAI Wordpress and Flash 10x Cookbook Copyright © 2010 Packt Publishing All rights reserved. No part of this book may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, without the prior written permission of the publisher, except in the case of brief quotations embedded in critical articles or reviews. Every effort has been made in the preparation of this book to ensure the accuracy of the information presented. However, the information contained in this book is sold without warranty, either express or implied. Neither the authors, Packt Publishing, nor its dealers or distributors will be held liable for any damages caused or alleged to be caused directly or indirectly by this book. Packt Publishing has endeavored to provide trademark information about all the companies and products mentioned in this book by the appropriate use of capitals. However, Packt Publishing cannot guarantee the accuracy of this information. First published: April 2010 Production Reference: 1140410 Published by Packt Publishing Ltd. 32 Lincoln Road Olton Birmingham, B27 6PA, UK. ISBN 978-1-847198-82-2 www.packtpub.com Cover Image by Vinayak Chittar ([email protected]) Credits Authors Editorial Team Leader Peter Spannagle Akshara Aware Sarah Soward Project Team Leader Reviewers Lata Basantani Ali Raza Project Coordinator Patrick Rushton Srimoyee Ghoshal Sonia Munoz Proofreader Acquisition Editor Joel T. Johnson Usha Iyer Production Coordinator Development Editor Adline Swetha Jesuthas Chaitanya Apte Cover Work Technical Editor Adline Swetha Jesuthas Ajay Shanker Indexer Monica Ajmera Mehta About the Authors Peter Spannagle is a WordPress consultant, technology trainer, and Web 2.0 designer. -

Protokoly Pro Komunikaci Klient ˚U Na Platformˇe Flash
MASARYKOVA UNIVERZITA F}w¡¢£¤¥¦§¨ AKULTA INFORMATIKY !"#$%&'()+,-./012345<yA| Protokoly pro komunikaci klient ˚una platformˇeFlash BAKALÁRSKA PRÁCA Tomáš Mizerák Brno, jar 2010 Prehlásenie Prehlasujem, že táto bakalárska práca je mojím pôvodným autorským dielom, ktoré som vypracoval samostatne. Všetky zdroje, pramene a literatúru, ktoré som pri vypracovaní používal alebo z nich ˇcerpal,v práci riadne citujem s uvedením úplného odkazu na prís- lušný zdroj. Vedúci práce: RNDr. David Šafránek, Ph.D. ii Pod’akovanie Dakujemˇ svojmu vedúcemu bakalárskej práce RNDr. Davidovi Šafránkovi, Ph.D. za pomoc, ochotu a strpenie, ktoré mi venoval pri tvorbe tejto práce. Taktiež d’akujem svojej rodine za podporu poˇcascelého štúdia a všetkým, ktorí mi akýmkol’vek spôsobom pomohli pri spracovaní tejto bakalárskej práce. iii Zhrnutie Vd’aka vysokej rozšírenosti technológie Flash a výkonu dnešných poˇcítaˇcovmôžeme im- plementovat’ aplikácie a hry bez nutnosti inštalácie. Táto práca zh´rˇnaspôsoby komunikácie klientov Flash a prehl’ad dostupných protokolov. V rámci práce boli jednoduchým nástro- jom otestované dva najrozšírenejšie protokoly pre Flash – HTTP a RTMP. Súˇcast’ou práce je ukážková aplikácia využívajúca RTMP pre spojenie klient-server a RTMFP pre peer-to-peer komunikáciu. iv Abstract Because of the great expansion of Flash technology and thanks to the performance of mod- ern computers we’re able to implement applications and games without the necessity of installing them. This thesis includes various possibilities of communication between Flash clients and an overview of available protocols. As a part of this thesis two most common protocols for Flash – HTTP and RTMP – were tested by a simple custom tool. The practical part is a demo application which uses RTMP for a client-server and RTMFP for peer-to-peer communication.