Copyrighted Material
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

PC Magazine Fighting Spyware Viruses And
01_577697 ffirs.qxd 12/7/04 11:49 PM Page i PC Magazine® Fighting Spyware, Viruses, and Malware Ed Tittel TEAM LinG - Live, Informative, Non-cost and Genuine ! 01_577697 ffirs.qxd 12/7/04 11:49 PM Page ii PC Magazine® Fighting Spyware, Viruses, and Malware Published by Wiley Publishing, Inc. 10475 Crosspoint Boulevard Indianapolis, IN 46256-5774 www.wiley.com Copyright © 2005 by Wiley Publishing Published simultaneously in Canada ISBN: 0-7645-7769-7 Manufactured in the United States of America 10 9 8 7 6 5 4 3 2 1 1B/RW/RS/QU/IN No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without either the prior written permission of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 646-8600. Requests to the Publisher for permission should be addressed to the Legal Department, Wiley Publishing, Inc., 10475 Crosspoint Blvd., Indianapolis, IN 46256, (317) 572-3447, fax (317) 572-4355, e-mail: [email protected]. Limit of Liability/Disclaimer of Warranty: The publisher and the author make no representations or warranties with respect to the accuracy or completeness of the contents of this work and specifically disclaim all warranties, including without limitation warranties of fitness for a particular purpose. No warranty may be created or extended by sales or promotional materials. -

Windows NT Network Management: Reducing Total Cost of Ownership - 9 - Performance Monitoring
Windows NT ...: Reducing Total Cost of Ownership - Chapter 9 - Performance Monitorin Page 1 of 13 [Figures are not included in this sample chapter] Windows NT Network Management: Reducing Total Cost of Ownership - 9 - Performance Monitoring AN OLD ADAGE SAYS, "IF YOU can’t measure it, you can’t manage it." Even if you can measure something, how can you tell if your changes are making a difference if you don’t have baseline information? It’s important to monitor a server’s or work- station’s performance to maximize your investment in these tools. If a user complains that her computer is too slow, you often need more information to fix the problem. For example, if the problem is loading Web pages on a computer using an analog modem, the modem is probably limiting the system’s performance. However, if the computer is an older model, certain operations may wait for the CPU to finish processing. In this case, a complete system upgrade may be the best solution. The usefulness of performance monitoring goes far beyond handling user expectations. A network and systems administrator can use information obtained by analyzing the operations of existing hardware, software, and networking devices to predict the timing of upgrades, justify the cost of replacing and upgrading devices, and assist in troubleshooting. Performance monitoring ultimately reduces TCO and is a vital part of managing any IT environment. Performance monitoring helps answer important questions about your current environment. For example, you may want to know which activity specifically uses the most resources in your environment. If you determine that it is loading Web pages, then upgrading the RAM or the CPU speed of client machines may not help much. -
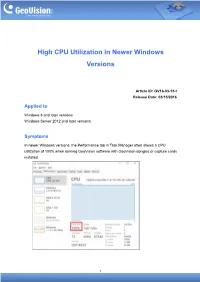
High CPU Utilization in Newer Windows Versions
High CPU Utilization in Newer Windows Versions Article ID: GV16-03-15-t Release Date: 03/15/2016 Applied to Windows 8 and later versions Windows Server 2012 and later versions Symptoms In newer Windows versions, the Performance tab in Task Manager often shows a CPU utilization of 100% when running GeoVision software with GeoVision dongles or capture cards installed. 1 Explanation In newer Windows versions, the CPU utilization takes into account of the CPU speed and is not calculated the same way as the CPU usage seen in Windows 7 and older versions. A 100% CPU utilization in Windows 10 is not the same as a 100% CPU usage in Windows 7. When running GeoVision software with GeoVision dongles or capture cards, the power saving mode of the computer is automatically disabled in order to avoid stability issues. Do not restore the power plan to default settings, which will enable the power saving mode again, even though the CPU utilization will appear lower in the Performance tab of Task Manager due to the lower CPU speed used during power saving mode. Looking Up the CPU Usage There are two ways to see the actual CPU usage in newer Windows versions. Method 1: Using Windows’ Performance Monitor 1. Click Start, type perfmon in the Search box, and then press Enter. 2. Under Monitoring Tools, click Performance Monitor. The CPU usage is displayed. 2 Method 2: Using System Idle Process in Task Manager 1. Open Task Manager (Ctrl-Alt-Delete) and click the Details tab. 2. Look for System Idle Process in the list and subtract its CPU usage from 100% to obtain the current CPU usage. -

Using SMART for Customized Monitoring of Windows Services
Using SMART for Customized Monitoring of Windows Services Gregory A. Pluta Larry Brumbaugh William Yurcik National Center for Supercomputing Applications (NCSA) University of Illinois at Urbana-Champaign {gpluta,ljbrumb,byurcik}@ncsa.uiuc.edu ABSTRACT We focus on examining and working with an important category of computer software called Services, which are provided as a part of newer Microsoft Windows operating systems. A typical Windows user transparently utilizes many of these services but is frequently unaware of their existence. Since some services have the potential to create significant problems when they are executing, it is important for a system administrator to identify which services are running on the network, the types of processing done by each service, and any interrelationships among the various services. This information can then be used to improve the overall integrity of both the individual computer where a questionable service is running and in aggregate an entire network of computers. NCSA has developed an application called SMART (Services Monitoring And Reporting Tool) that can be used to identify and display all services currently running in the network. A commercial program called Hyena remotely monitors the services on all computers attached to the network and exports this information to SMART. SMART produces various outputs that the system administrator can analyze and then determine appropriate actions to take. In particular, SMART provides a color coordinated user interface to quickly identify and classify both potentially hazardous services and also unknown services. Keywords: Windows services, Windows processes, host intrusion detection systems (IDS), host monitoring, network security monitoring, security situational awareness 1. -

Windows Task Manager" (Taskmgr.Exe)
CSNB224 Tutorial 5 Objective: • To observe the behaviour of processes using Task Manager ______________________________________________________________ Task manager is one of the tools that can be used to manage system processes and applications. Task manager is a program used to provide information about the processes and programs running on a computer, as well as the general status of the computer. It can also be used to terminate processes and programs, as well as change the processes' priority. In Windows operating systems, the task manager is a program named "Windows Task Manager" (taskmgr.exe). Task Manager can be started with: 1. Press Ctrl+Shift+Esc 2. Press Ctrl+Alt+Del, and then select the Task Manager button 3. Enter taskmgr into the Run utility or a command prompt 4. Right-click on the taskbar and select Task Manager from the pop-up menu There are three important tabs in Task Manager Window: 1. Application 2. Processes 3. Performance Application It shows the status of the programs that are currently running on the system. Application status tells you if the application is running normally or if the application has gone off into the ozone. A status of Not Responding is an indicator that an application may be frozen and you may want to end its related task. You can use the buttons on the bottom of this tab as follows: • End Task: Stop an application • Switch To: Switch to an application and make it active • New Task: Start a new program and then enter a command to run the application. 1 Processes It shows the processes that are currently running. -

Running Head: LAB REPORT 1 Lab Report Objective • the 5.3.1.5 Lab Is
Running head: LAB REPORT 1 Lab Report Objective • The 5.3.1.5 lab is aimed at exploring the peculiarities of the Task Manager and managing the Task Manager processes. • The 5.3.1.7 lab is aimed at the peculiarities of the Task Manager and managing the Task Manager processes. • The In 5.3.2.5 lab is aimed at learning how to create Windows XP Professional user accounts. Procedures The equipment required for the lab 5.3.1.5 is a computer with installed Windows 7. During the lab we learnt how to use the Windows Task Manager in order to switch to the browser, how a new task can be added and what the procedure of ending up is. We got to know the statuses of each service from the Windows task Manager, i.e. stopped or running. Furthermore, we got aware of the preferences that show System, Physical Memory and Kernel Memory. The task manager displays the network link speed. In addition, we know that it is possible to see the statuses of the displayed users. Finally, we learnt how to log off. We used “show process all users” among the clickable processes in Task Manager and saw all of them. We also tried changing the task manager mode into compact and changed the order from descending to ascending and visa versa. Having located the Internet Explorer, we learnt how to change the normal priority to the above normal one. I was supposed also to select the columns; however, my version did not support that function. -

Improve SQL Server Performance and Lower Costs with Kingston Technology DC500M Enterprise Solid-State Drives
Improve SQL Server Performance and Lower Costs with Kingston Technology DC500M Enterprise Solid-State Drives October 2019 Written by Bill Ramos, Director of Technical Product Management, DB Best Technology. Technical reviewers: Hazem Awadallah, Systems Engineer, Kingston Technology Contents Executive Summary .................................................................................................................................... 3 The Problem: SQL Server 2008 End of Support .......................................................................................... 6 The Solution: Replace HDD drives with Kingston Technology Data Center DC500 Enterprise Solid-State Drives (SSDs) and upgrade to SQL Server 2017 .......................................................................................... 7 Hardware ................................................................................................................................................ 9 Software ............................................................................................................................................... 10 Benchmarking Testing Scenarios ............................................................................................................. 12 Test Results .............................................................................................................................................. 15 Results: SQL Server 2008 R2 with 16 vCores on HDD ........................................................................... 15 -

Failover Cluster Validation Report Page 1 of 56
Failover Cluster Validation Report Page 1 of 56 Failover Cluster Validation Report Node: hyperv1.kerberos.dnuk.lan Validated Node: hyperv2.kerberos.dnuk.lan Validated Started 10/29/2014 4:02:16 PM Completed 10/29/2014 4:05:20 PM The Validate a Configuration Wizard must be run after any change is made to the configuration of the cluster or hardware. For more information, see http://go.microsoft.com/fwlink/p/?LinkId=280145. Results by Category Name Result Summary Description Hyper-V Configuration Success Inventory Success Network Success Storage Success System Configuration Success Hyper-V Configuration Name Result Description List Information About Servers Running Hyper-V Success Validate Compatibility of Virtual Fibre Channel SANs for Hyper-V Success Validate Hyper-V Memory Resource Pool Compatibility Success Validate Hyper-V Network Resource Pool And Virtual Switch Success Compatibility Validate Hyper-V Processor Resource Pool Compatibility Success Validate Hyper-V Role Installed Success Validate Hyper-V Storage Resource Pool Compatibility Success Validate Matching Processor Manufacturers Success Inventory Name Result Description List BIOS Information Success List Environment Variables Success List Fibre Channel Host Bus Adapters Success List iSCSI Host Bus Adapters Success List Memory Information Success List Operating System Information Success List Plug and Play Devices Success List Running Processes Success 10/29/2014 Failover Cluster Validation Report Page 2 of 56 List SAS Host Bus Adapters Success List Services Information Success -

Green Computing
18 Learn the discipline, pursue the art, and contribute ideas at www.architecturejournal.net input for better outcomes Green Computing Environmentally Architecture Journal Profile: Sustainable Infrastructure Udi Dahan Design Green IT in Practice: Green Maturity Model Profiling Energy Usage for SQL Server Consolidation for Virtualization Efficient Consumption in Microsoft IT Application Patterns Project Genome: Wireless Sensor for Green IT Network for Data Center Cooling Contents 18 Foreword 1 by Diego Dagum Environmentally Sustainable Infrastructure Design 2 by Lewis Curtis A comprehensive understanding of environmental sustainability needs for IT infrastructure system design. Green Maturity Model for Virtualization 9 by Kevin Francis and Peter Richardson The authors present a study on the maturity of virtualization practices and offer a sustainability roadmap for organizations planning a green agenda. Application Patterns for Green IT 16 by Dan Rogers and Ulrich Homann A complete analysis on power-efficient applications design, considering tools that help the architect achieve scalability without deriving in energy waste. Architecture Journal Profile: Udi Dahan 22 For this issue’s interview, we catch up with Udi Dahan, noted expert on SOA and .NET development, and four-time Microsoft MVP. Profiling Energy Usage for Efficient Consumption 24 by Rajesh Chheda, Dan Shookowsky, Steve Stefanovich, and Joe Toscano This article suggests that tracking energy consumption at every level will become the factor of success for green architecture practitioners. Project Genome: Wireless Sensor Network for Data Center Cooling 28 by Jie Liu, Feng Zhao, Jeff O’Reilly, Amaya Souarez, Michael Manos, Chieh-Jan Mike Liang, and Andreas Terzis Learn about a research project on an interesting adaptive cooling technique. -

Hitachi Command Suite Tuning Manager Operating System Reports
Hitachi Command Suite Tuning Manager 8.7 Operating System Reports Reference This document describes how to use the Hitachi Tuning Manager. MK-95HC112-24 October 2019 © 2014, 2019 Hitachi, Ltd. All rights reserved. No part of this publication may be reproduced or transmitted in any form or by any means, electronic or mechanical, including copying and recording, or stored in a database or retrieval system for commercial purposes without the express written permission of Hitachi, Ltd., or Hitachi Vantara Corporation (collectively "Hitachi"). Licensee may make copies of the Materials provided that any such copy is (i) created as an essential step in utilization of the Software as licensed and is used in no other manner; or (ii) used for archival purposes. Licensee may not make any other copies of the Materials. "Materials" mean text, data, photographs, graphics, audio, video and documents. Hitachi reserves the right to make changes to this Material at any time without notice and assumes no responsibility for its use. The Materials contain the most current information available at the time of publication. Some of the features described in the Materials might not be currently available. Refer to the most recent product announcement for information about feature and product availability, or contact Hitachi Vantara Corporation at https://support.hitachivantara.com/en_us/contact-us.html. Notice: Hitachi products and services can be ordered only under the terms and conditions of the applicable Hitachi agreements. The use of Hitachi products is governed by the terms of your agreements with Hitachi Vantara Corporation. By using this software, you agree that you are responsible for: 1) Acquiring the relevant consents as may be required under local privacy laws or otherwise from authorized employees and other individuals; and 2) Verifying that your data continues to be held, retrieved, deleted, or otherwise processed in accordance with relevant laws. -

Svchost Exe 99 Cpu Usage Fix
Svchost exe 99 cpu usage fix click here to download So what is www.doorway.ru? Identifying the actual services and programs that are So let's say one of them is running at an excessively high CPU usage of A few solutions you might need when diagnosing and troubleshooting svchost. exe (netsvcs) high CPU usage problem in Windows 7, 8 or. Abnormally high CPU usage from www.doorway.ru [SOLVED] the computer again and trying a manual fix I found in a forum somewhere else). In many occasions, I have troubleshooted the www.doorway.ru (netsvcs) problem by using different solutions to resolve the problem depending on. This creates a big problem. In this article, I will explain you all about www.doorway.ru Also, I will teach how to fix its high CPU usage problem. www.doorway.ru (netsvcs) is a important Windows Host Process located in C: WindowsSystem32 which is a dependency of several Windows related. Page 1 of 3 - www.doorway.ru using % CPU - posted in Windows XP Home http ://www.doorway.ru Task Manager 'System Idle Process' kept hitting 99%CPU (although. High CPU or memory usage of www.doorway.ru services can be caused by be the cause of the abnormal high CPU usage in your PC. To fix it. Windows 10 comes with one mysterious processes called www.doorway.ru that always runs in the background and uses more CPU power. Hello, recently I have discovered a problem with high CPU usage, which appeared to be something or right click in task manager the www.doorway.ru running high and select ''go to services'' and Should solve it in most cases. -
Copyrighted Material
Index Note to the Reader: Throughout this index boldfaced page numbers indicate primary discussions of a topic. Italicized page numbers indicate illustrations. Active Directory Installation Wizard, 21–31, 23–30 Active Directory-integrated zones, 459 A Active Directory services database, 758 /a switch in WINNT, 89 Active Directory users, 155, 790 /abovenormal switch, 702 Active Directory Users and Computer utility Accelerated Graphics Port (AGP), 790 defined, 790 access control entries (ACEs), 372–373, 373, 790 for groups access control lists (ACLs), 372–373, 372–373, 790 creating, 197–198, 197 Access Control Settings dialog box, 531, 531 properties of, 199–202, 199–201 access for Active Directory users, 188 for user accounts Access This Computer from the Network right, 232 creating, 182–184, 182–183 access tokens properties of, 184–191, 185–191 creating, 371–372 active partitions, 730 defined, 790 Active Server Pages (ASP), 483 Accessed property, 725 AD (Active Directory), 3 accessibility features, 102 defined, 790 Account Is Disabled option, 169, 172 group policies within, 215–218 account lockout policy, 790 installing, 21–31, 23–30 Account Lockout Duration policy, 225 logical organization of, 22 Account Lockout Policy folder, 221 structure of, 215–216 Account Lockout Threshold policy, 225 Terminal Services for, 561 Account Operators group, 157 Adapter tab, 123 account policies. See policies adapters Account Policies folder, 221 defined, 790 Account Policies template, 252 network. See network adapters Account tab, 186–189, 187 video