Jamf Pro Administrator's Guide Version 10.26.0 © Copyright 2002-2020 Jamf
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Deploying Ios and Tvos Devices Using Apple Configurator 2 and Jamf Pro
Deploying iOS and tvOS Devices Using Apple Configurator 2 and Jamf Pro Technical Paper Jamf Pro 10.9.0 or Later 7 October 2020 © copyright 2002-2020 Jamf. All rights reserved. Jamf has made all efforts to ensure that this guide is accurate. Jamf 100 Washington Ave S Suite 1100 Minneapolis, MN 55401-2155 (612) 605-6625 Jamf, the Jamf Logo, JAMF SOFTWARE®, and the JAMF SOFTWARE Logo® are registered or common law trademarks of JAMF SOFTWARE, LLC in the U.S. and other countries. Apple, Apple Configurator 2, the Apple logo, Apple TV, iTunes, Mac, macOS, OS X, and tvOS are trademarks of Apple Inc., registered in the United States and other countries. IOS is a trademark or registered trademark of Cisco in the U.S. and other countries. All other product and service names mentioned herein are either registered trademarks or trademarks of their respective companies. Contents Contents 4 Introduction 4 What's in This Guide 4 Additional Resources 5 Choosing a Deployment Method 6 Supervision Identities 6 Use a Supervision Identity from Apple Configurator 2 7 Create and Use a Supervision Identity from Jamf Pro 8 Automated Enrollment 8 Requirements 8 Deploying Devices Using Automated Enrollment 11 Manual Enrollment with an Enrollment URL 11 Requirements 11 Deploy Devices Using Manual Enrollment with an Enrollment URL 13 Further Considerations 14 Manual Enrollment with an Enrollment Profile 14 Requirements 14 Create an Enrollment Profile 14 Create and Upload the Supervision Identity 14 Create the "Prepare" Blueprint 15 Create the "Enroll" Blueprint 15 Deploy Devices Using Manual Enrollment with an Enrollment Profile 3 Introduction What's in This Guide This guide provides step-by-step instructions for deploying iOS and tvOS devices using Apple Configurator 2 and Jamf Pro. -

View Managing Devices and Corporate Data On
Overview Managing Devices & Corporate Data on iOS Overview Overview Contents Businesses everywhere are empowering their employees with iPhone and iPad. Overview Management Basics The key to a successful mobile strategy is balancing IT control with user Separating Work and enablement. By personalizing iOS devices with their own apps and content, Personal Data users take greater ownership and responsibility, leading to higher levels of Flexible Management Options engagement and increased productivity. This is enabled by Apple’s management Summary framework, which provides smart ways to manage corporate data and apps discretely, seamlessly separating work data from personal data. Additionally, users understand how their devices are being managed and trust that their privacy is protected. This document offers guidance on how essential IT control can be achieved while at the same time keeping users enabled with the best tools for their job. It complements the iOS Deployment Reference, a comprehensive online technical reference for deploying and managing iOS devices in your enterprise. To refer to the iOS Deployment Reference, visit help.apple.com/deployment/ios. Managing Devices and Corporate Data on iOS July 2018 2 Management Basics Management Basics With iOS, you can streamline iPhone and iPad deployments using a range of built-in techniques that allow you to simplify account setup, configure policies, distribute apps, and apply device restrictions remotely. Our simple framework With Apple’s unified management framework in iOS, macOS, tvOS, IT can configure and update settings, deploy applications, monitor compliance, query devices, and remotely wipe or lock devices. The framework supports both corporate-owned and user-owned as well as personally-owned devices. -

Nextcloud User Manual Release Latest
Nextcloud User Manual Release latest The Nextcloud developers May 16, 2021 Contents 1 Nextcloud latest user manual introduction1 2 What’s new for users in Nextcloud latest3 3 The Nextcloud Web interface7 3.1 Web browser requirements........................................7 3.2 Navigating the main user interface....................................8 4 Files & synchronization 11 4.1 Accessing your files using the Nextcloud Web interface........................ 11 4.2 Accessing Nextcloud files using WebDAV................................ 17 4.3 Managing deleted files.......................................... 28 4.4 Desktop and mobile synchronization.................................. 29 4.5 Encrypting your Nextcloud files on the server.............................. 29 4.6 File Sharing............................................... 32 4.7 Federated Shares............................................. 36 4.8 Making anonymous uploads....................................... 38 4.9 Large file uploads............................................ 40 4.10 Storage quota............................................... 40 4.11 Version control.............................................. 41 4.12 Projects.................................................. 41 4.13 Transfer Ownership........................................... 44 5 Groupware 47 5.1 Using the Contacts app.......................................... 47 5.2 Using the Calendar app......................................... 50 5.3 Synchronizing with Android....................................... 58 5.4 Synchronizing -

Security Checklist
WHITE PAPER Security Checklist Implementing the Center for Internet Security Benchmark Recommendations for securing iPad and iPhone. The Center for Internet Security (CIS) benchmark for iOS is widely regarded as a comprehensive checklist for organizations to follow to secure iPad and iPhone devices. This white paper explains how to implement the independent organization’s recommendations. To see how Jamf Now can help secure and manage your iOS devices, visit www.jamf.com. WHO IS THE CIS? The Center for Internet Security, Inc. (CIS) is a 501c3 nonprofit organization focused on enhancing the cybersecurity readiness and response of public and private sector entities. HOW THE CIS BENCHMARK WAS CREATED The CIS Benchmark was created using a consensus review process comprised of subject matter experts. Consensus participants provide perspective from a diverse set of backgrounds including consulting, software development, audit and compliance, security research, operations, government and legal. Each CIS benchmark undergoes two phases of consensus review. The first phase occurs during initial benchmark development. During this phase, subject matter experts convene to discuss, create and test working drafts of the benchmark. This discussion occurs until consensus has been reached on benchmark recommendations. The second phase begins after the benchmark has been published. During this phase, all feedback provided by the Internet community is reviewed by the consensus team for incorporation in the benchmark. If you are interested in participating in the consensus process, please visit https://www.cisecurity.org/communities/. CIS Management Basics WHAT IS MDM? WHAT ARE BLUEPRINTS? WHAT IS APNs? Mobile device management (MDM) Blueprints define settings on Apple Apple Push Notification service is Apple’s built-in management devices and are distributed to the (APNs) is required for iPad and iPhone framework for iOS, iPadOS, macOS devices via Jamf Now. -

Jamf Pro Server
Jamf Pro Administrator's Guide Version 10.1.0 © copyright 2002-2017 Jamf. All rights reserved. Divide is a trademark or registered trademark of Divide, Inc. Jamf has made all efforts to ensure that this guide is accurate. eDirectory is a trademark of Novell, Inc. in the United States and other countries. Jamf 100 Washington Ave S Suite 1100 Google, Android, Google Chrome, and Google Minneapolis, MN 55401-2155 Play are trademarks or registered trademarks of (612) 605-6625 Google Inc. Intel and McAfee Endpoint Protection are either Under the copyright laws, this publication may registered trademarks or trademarks of the Intel not be copied, in whole or in part, without the Corporation in the United States and other written consent of Jamf. countries. The CASPER SUITE, COMPOSER®, Likewise is a trademark of Likewise Software. the COMPOSER Logo®, Jamf, the Jamf Logo, JAMF SOFTWARE®, the JAMF SOFTWARE Logo®, Linux is a registered trademark of Linus Torvalds RECON®, and the RECON Logo® are registered or in the United States and other countries. common law trademarks of JAMF SOFTWARE, LLC in the U.S. and other countries. Microsoft, Microsoft Intune, Active Directory, Azure, Excel, OneNote, Outlook, PowerPoint, ADmitMac is a registered trademark of Thursby Silverlight, Windows, Windows Server, and all Software Systems, Inc. references to Microsoft software are either registered trademarks or trademarks of Adobe, Adobe AIR, Adobe Bridge, Adobe Microsoft Corporation in the United States Premier Pro, Acrobat, After Effects, Creative and/or other countries. Suite, Dreamweaver, Fireworks, Flash Player, Illustrator, InDesign, Lightroom, Photoshop, Mozilla and Firefox are registered trademarks of Prelude, Shockwave, and all references to Adobe the Mozilla Foundation. -

Firstclass 12.1 New Features
New In FirstClass® 12.1 The FirstClass Collaboration Server is a powerful, secure and highly scalable collaboration platform that bridges the chasm between in-person and digital communication through a rich online experience. 64-bit Sync Services FirstClass® GO WebDAV URL Support Providing bi-directional wireless Access to your stuff. Anytime, WebDAV allows clients to syncing of calendars, tasks, and Anywhere. Available on iOS, perform remote Web content contacts to mobile devices Android and Windows devices. authoring operations within FirstClass Web Services Multi-Word Filter External Integration Server CalDAV Support Filter on every word you type in External Integration Services (EIS) CalDAV support provides users the "Filter" field, rather than gives your users access to their the ability to subscribe or share treating these words as one data on external calendars, such as FirstClass® Calendars via CalDAV. phrase. Google calendars. Like/Rank Posts LightBox Enhancements Assigning Calendar Tasks Users will now have the ability Users now have the ability to open Users will now have the ability to to Like/Dislike or Rank postings items such as documents and assign calendar tasks to other in a Community or Conference images in a Lightbox with added users and to be able to view their (permissions based) tools to scale, rotate and more. status with a simple to use interface. Synergy with Desktop Share Button Microsoft Surface Client Client features Added support for Contact Securely share posts and items Introducing, FirstClass® GO for Databases, Volume with a single click in Microsoft Surface. Preferences, Auto open objects FirstClass® Web Services 12.1 and more in FirstClass® Web Same powerful features on a Services 12.1 totally new platform.. -

Reference Guide
Reference Guide Mulberry Internet Email and Calendar Client Version 4.0 Cyrus Daboo mailto:[email protected] Pittsburgh PA http://www.mulberrymail.com USA 2Information in this document is subject to change without notice. You are free to use this document in any way you wish provided full attribution of the original author is given. Document Revision 405.000 © 2006 Cyrus Daboo. All Rights Reserved. Pittsburgh PA USA Mulberry is a registered trademark. All other companies and product names are trademarks or registered trademarks of their respective holders. Contents 1. INTRODUCTION................................................................................. 15 2. GETTING STARTED............................................................................ 16 2.1 SYSTEM REQUIREMENTS .......................................................................................................... 16 2.2 INSTALLING MULBERRY........................................................................................................... 17 2.3 GETTING HELP......................................................................................................................... 18 2.4 STARTING MULBERRY .............................................................................................................. 18 2.5 DRAG AND DROP ...................................................................................................................... 20 2.6 CONTEXTUAL MENUS............................................................................................................. -
Download Calendar Program Windows 10 5 Best Free Open Source Calendar Software for Windows
download calendar program windows 10 5 Best Free Open Source Calendar Software for Windows. Here is a list of best free open source calendar software for Windows. These are free desktop calendar software which come with open source license. You can freely download and study source code of these calendar software and even manipulate the source code. These calendar software let you view the calendar in monthly, daily, weekly, or yearly view. You can also add and schedule important events on particular dates in a month. All of these software provide appointment editor tool to add and manage multiple appointments with date and time, reminder settings, priority, etc. You also get a feature to add and manage various contacts in a few of these software. Additionally, you can create a to-do list in these software to keep up with your daily tasks. You can also add essential notes and memos on particular dates. In one of these software, you can also import iCalendar files to add calendar events. Also, for students, there is a nice software with features including time table and booklet creator. Other than that, you get various useful features in these software which include task categories creator, email alert generator, setup calendar appearance, reminder tone, etc. In general, these are featured open source calendar software which are useful in keeping up with the dates and managing important tasks. My favorite Free Open Source Calendar Software for Windows: BORG Calendar is a good desktop calendar software which comes with a lot of handy tools including appointment editor, tasks creator, memos creator, checklists maker, etc. -

Jamf Pro Installation and Configuration Guide for Mac Version 10.5.0 © Copyright 2002-2018 Jamf
Jamf Pro Installation and Configuration Guide for Mac Version 10.5.0 © copyright 2002-2018 Jamf. All rights reserved. Jamf has made all efforts to ensure that this guide is accurate. Jamf 100 Washington Ave S Suite 1100 Minneapolis, MN 55401-2155 (612) 605-6625 Under the copyright laws, this publication may not be copied, in whole or in part, without the written consent of Jamf. Amazon and Amazon RDS are trademarks of Amazon.com, Inc. or its affiliates in the United States and/or other countries. Apache Tomcat and Tomcat are trademarks of the Apache Software Foundation. Apple, Mac, macOS, OS X, and Safari are trademarks of Apple, Inc. registered in the U.S. and other countries. The CASPER SUITE, COMPOSER®, the COMPOSER Logo®, Jamf, the Jamf Logo, JAMF SOFTWARE®, the JAMF SOFTWARE Logo®, RECON®, and the RECON Logo® are registered or common law trademarks of JAMF SOFTWARE, LLC in the U.S. and other countries. Chrome and Google are trademarks or registered trademarks of Google Inc. Firefox is a registered trademark of the Mozilla Foundation. Intel is a registered trademark of the Intel Corporation in the U.S. and other countries. Java and MySQL are registered trademarks of Oracle and/or its affiliates. Other names may be trademarks of their respective owners. Microsoft, Microsoft Edge, and Windows are either registered trademarks or trademarks of Microsoft Corporation in the United States and other countries. Ubuntu is a registered trademark of Canonical Ltd. All other product and service names mentioned herein are either registered trademarks or trademarks of their respective companies. -
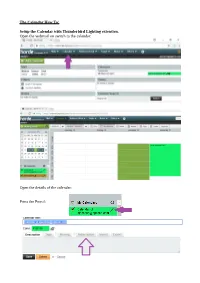
The Calendar How To: Setup the Calendar with Thunderbird Lighting
The Calendar How To: Setup the Calendar with Thunderbird Lighting extention. Open the webmail en switch to the calendar: Open the details of the calendar: Press the Pensil: Select the top line and press ctrl+C to copy this line. Now open Thunderbird and press the calendar icon: Press the right mouse button with the cursor at the arrow possition: Create a new calendar: On the network: Press CTRL+V to paste the calendar url from Horde in the box below: The URL starts with: https://webmail.opticon.com/horde/rpc.php/calendars/[email protected]/calendar~ and then a bunch of random characters (different for each calendar) Give the calendar a name and select a nice colour: It will ask for your credentials: The calendar is now ready, press the synchronise button The Calendar events from Horde are now shown in your Thunderbird Calendar (Lightning): But you can also add an item in Thunderbird and see it back in the Calender of Horde: Add an new Event: Make sure that you use the online calendar and not the default “home” calendar !! Now Sync the calendar. And see the result inHorde: Setup of the calendar in Outlook. Outlook by itself is not able to work with a CalDav Calendar, but somebody has created a nice plugin: Outlook CalDav Synchronizer (http://caldavsynchronizer.org/) And even better it is free and open source. You can download it from here: https://sourceforge.net/projects/outlookcaldavsynchronizer/ Download only the zip file, do not press any other button on the SourceForge page. First close Outlook. -

Installation and Configuration Guide
Installation and Configuration Guide SOGo v5.1.1 Table of Contents 1. About this Guide . 2 2. Introduction . 3 2.1. Architecture and Compatibility . 3 3. System Requirements . 6 3.1. Assumptions . 6 3.2. Minimum Hardware Requirements. 6 3.3. Operating System Requirements . 7 4. Installation . 9 4.1. Software Downloads . 9 4.2. Software Installation . 10 5. Configuration. 11 5.1. GNUstep Environment Overview . 11 5.2. Preferences Hierarchy . 11 5.3. General Preferences . 12 5.4. Authentication using LDAP. 24 5.5. LDAP Attributes Indexing . 31 5.6. LDAP Attributes Mapping . 32 5.7. Authenticating using C.A.S.. 33 5.8. Authenticating using SAML2 . 35 5.9. Database Configuration . 35 5.10. Authentication using SQL . 40 5.11. SMTP Server Configuration . 43 5.12. IMAP Server Configuration. 44 5.13. Web Interface Configuration . 47 5.14. SOGo Configuration Summary. 57 5.15. Multi-domains Configuration . 58 5.16. Apache Configuration . 60 5.17. Starting Services . 61 5.18. Cronjob — EMail reminders. 61 5.19. Cronjob — Vacation messages activation and expiration . 62 6. Managing User Accounts . 63 6.1. Creating the SOGo Administrative Account . 63 6.2. Creating a User Account . 63 7. Microsoft Enterprise ActiveSync . 65 8. Microsoft Enterprise ActiveSync Tuning . 68 9. S/MIME Support in SOGo . 70 10. Using SOGo. 71 10.1. SOGo Web Interface. 71 10.2. Mozilla Thunderbird and Lightning . 71 10.3. Apple Calendar (macOS, iOS, iPadOS). 72 10.4. Apple AddressBook . 72 10.5. Microsoft ActiveSync . 73 11. Upgrading . 74 12. Additional Information . 76 13. Commercial Support and Contact Information . -

Sharing & Synchronizing Files and Calendars
Sharing & Synchronizing files and calendars - the private cloud services of the institute A presentation by Stefan Schneider 3/17/16 Motivation for providing an institute cloud ● Enables to work flexible with divers mobile devices ● Working at different offices ( PIK / home / official journeys) ● Easy exchange of files ● Calendars reachable from all-around ● Data stay at the PIK 3/17/16 2/49 Independence from location 3/17/16 3/49 Accessing the cloud services https://cloud.pik-potsdam.de 3/17/16 4/49 Reasons for synchronization ● Greater mobility – Easy access to own and shared files for official trips or expeditions ● Data is available from a wide range of kinds of devices ● Staying up to date with synchronized shared team calendars 3/17/16 5/49 Available clients ● Desktop clients: OS X, Windows, Linux ● Mobile file-sync clients: Apple App, Google Play ● Desktop calendar clients: Thunderbird Lightning ● Calendar synchronization via CalDav-Sync to custom calendar-apps ● Further synchronizing Android apps: OwnCloud Bookmarks, ownNote 3/17/16 6/49 Mobile Clients (Android) 3/17/16 7/49 Means of collaboration ● A place for quick exchange of common office data (for papers, E-books, poster, presentations, pictures) ● Collaborative working with shared documents that are synchronized to the computer one is working with ● Survey of dates- creating of team calendars and synchronization to devices with a CalDAV-client 3/17/16 8/49 Details about the institute's cloud ● Available with PIK standard account ● Synchronization of files for Windows, OS