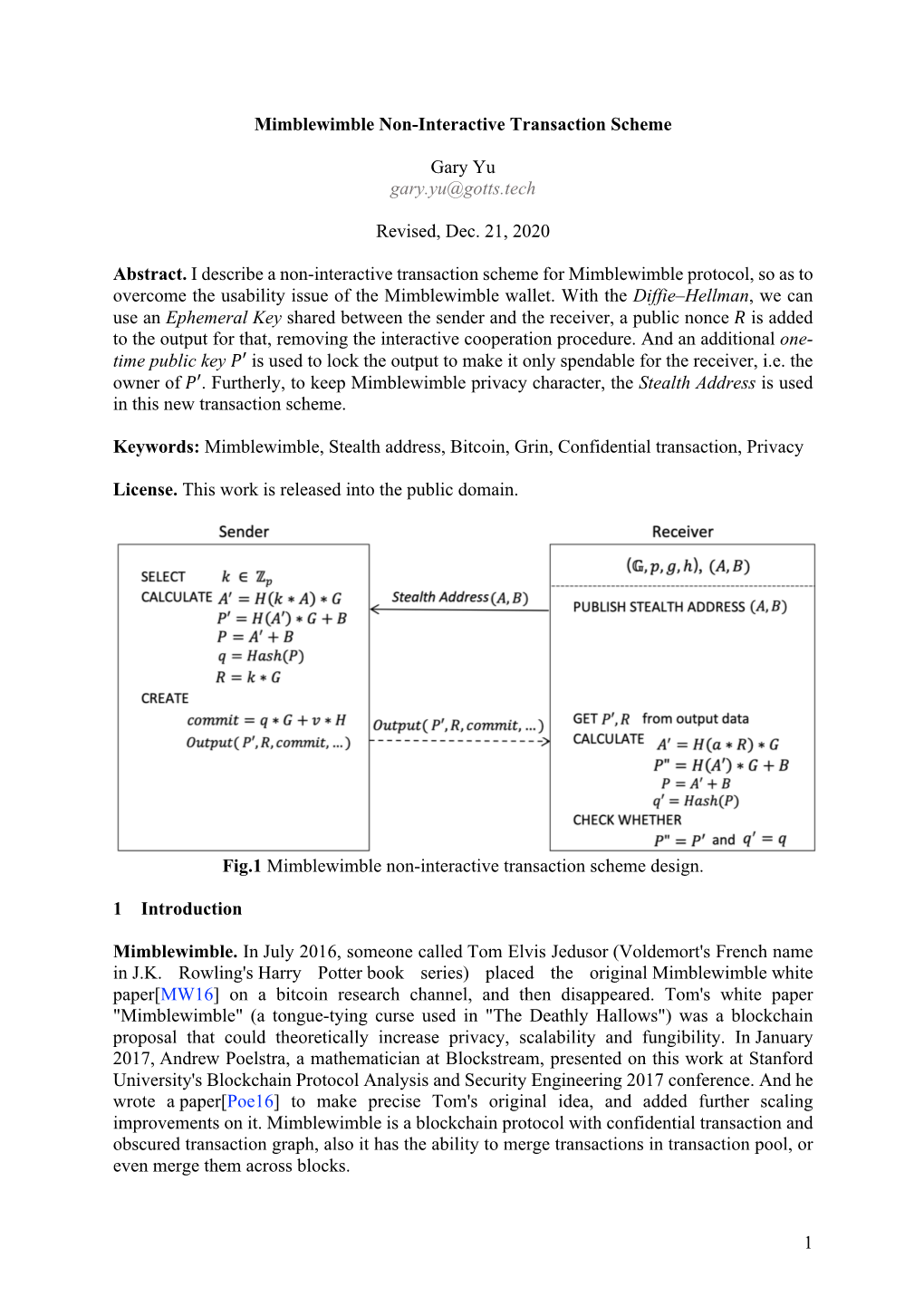
Mimblewimble Non-Interactive Transaction Scheme
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Rev. Rul. 2019-24 ISSUES (1) Does a Taxpayer Have Gross Income Under
26 CFR 1.61-1: Gross income. (Also §§ 61, 451, 1011.) Rev. Rul. 2019-24 ISSUES (1) Does a taxpayer have gross income under § 61 of the Internal Revenue Code (Code) as a result of a hard fork of a cryptocurrency the taxpayer owns if the taxpayer does not receive units of a new cryptocurrency? (2) Does a taxpayer have gross income under § 61 as a result of an airdrop of a new cryptocurrency following a hard fork if the taxpayer receives units of new cryptocurrency? BACKGROUND Virtual currency is a digital representation of value that functions as a medium of exchange, a unit of account, and a store of value other than a representation of the United States dollar or a foreign currency. Foreign currency is the coin and paper money of a country other than the United States that is designated as legal tender, circulates, and is customarily used and accepted as a medium of exchange in the country of issuance. See 31 C.F.R. § 1010.100(m). - 2 - Cryptocurrency is a type of virtual currency that utilizes cryptography to secure transactions that are digitally recorded on a distributed ledger, such as a blockchain. Units of cryptocurrency are generally referred to as coins or tokens. Distributed ledger technology uses independent digital systems to record, share, and synchronize transactions, the details of which are recorded in multiple places at the same time with no central data store or administration functionality. A hard fork is unique to distributed ledger technology and occurs when a cryptocurrency on a distributed ledger undergoes a protocol change resulting in a permanent diversion from the legacy or existing distributed ledger. -

White Paper of Bitcoin Ultimatum Introduction
White Paper of Bitcoin Ultimatum Introduction 1. Problematic of the Blockchain 4. Bitcoin Ultimatum Architecture industry 4.1. Network working principle 1.1. Transactions Anonymity 4.1.1. Main Transaction Types 1.2. Insufficient Development of Key Aspects of the 4.1.1.1. Public transactions Technology 4.1.1.2. Private transactions 1.3. Centralization 4.1.2. Masternode Network 1.4. Mining pools and commission manipulation 4.2. How to become a validator or masternode in 1.5. Decrease in Transaction Speeds BTCU 4.3. Network Scaling Principle 2. BTCU main solutions and concepts 4.4. Masternodes and Validators Ranking System 4.5. Smart Contracts 2.1. Consensus algorithm basis 4.6. Anonymization principle 2.2. Leasing and Staking 4.7. Staking and Leasing 2.3. Projects tokenization and DeFi 4.7.1. Staking 2.4. Transactions Privacy 4.7.2. Leasing 2.5. Atomic Swaps 4.7.2 Multileasing 4.8. BTCU Technical Specifications 3. Executive Summary 4.8.1. Project Stack 4.8.2. Private key generation algorithm 5. Bitcoin Ultimatum Economy 5.1. Initial Supply and Airdrop 5.2. Leasing Economy 5.3. Masternodes and Validators Commission 5.4. Transactions Fee 6. Project Roadmap 7. Legal Introduction The cryptocurrency market is inextricably tied to the blockchain – its fundamental and underlying technology. The modern market is brimming with an abundance of blockchain protocols, algorithms, and concepts, all of which have fostered the development of a wide variety of services and applications. The modern blockchain market offers users an alternative to both established financial systems and ecosystems/infrastructures of applications and services. -

Blockchain & Cryptocurrency Regulation
Blockchain & Cryptocurrency Regulation Third Edition Contributing Editor: Josias N. Dewey Global Legal Insights Blockchain & Cryptocurrency Regulation 2021, Third Edition Contributing Editor: Josias N. Dewey Published by Global Legal Group GLOBAL LEGAL INSIGHTS – BLOCKCHAIN & CRYPTOCURRENCY REGULATION 2021, THIRD EDITION Contributing Editor Josias N. Dewey, Holland & Knight LLP Head of Production Suzie Levy Senior Editor Sam Friend Sub Editor Megan Hylton Consulting Group Publisher Rory Smith Chief Media Officer Fraser Allan We are extremely grateful for all contributions to this edition. Special thanks are reserved for Josias N. Dewey of Holland & Knight LLP for all of his assistance. Published by Global Legal Group Ltd. 59 Tanner Street, London SE1 3PL, United Kingdom Tel: +44 207 367 0720 / URL: www.glgroup.co.uk Copyright © 2020 Global Legal Group Ltd. All rights reserved No photocopying ISBN 978-1-83918-077-4 ISSN 2631-2999 This publication is for general information purposes only. It does not purport to provide comprehensive full legal or other advice. Global Legal Group Ltd. and the contributors accept no responsibility for losses that may arise from reliance upon information contained in this publication. This publication is intended to give an indication of legal issues upon which you may need advice. Full legal advice should be taken from a qualified professional when dealing with specific situations. The information contained herein is accurate as of the date of publication. Printed and bound by TJ International, Trecerus Industrial Estate, Padstow, Cornwall, PL28 8RW October 2020 PREFACE nother year has passed and virtual currency and other blockchain-based digital assets continue to attract the attention of policymakers across the globe. -

On the Security of Electroneum Cloud Mining
This Selfie Does Not Exist: On the Security of Electroneum Cloud Mining Alexander Marsalek1, Edona Fasllija2 and Dominik Ziegler3 1Secure Information Technology Center Austria, Vienna, Austria 2Institute for Applied Information Processing and Communications (IAIK), Graz University of Technology, Graz, Austria 3Know-Center GmbH, Graz, Austria Keywords: Electroneum Cloud Mining, Cryptocurrency, Impersonation Attack, Image Manipulation. Abstract: The Electroneum cryptocurrency provides a novel mining experience called “cloud mining”, which enables iOS and Android users to regularly earn cryptocurrency tokens by simply interacting with the Electroneum app. Besides other security countermeasures against automated attacks, Electroneum requires the user to up- load selfies with a predefined gesture or a drawing of a symbol as a prerequisite for the activation of the mining process. In this paper, we show how a malicious user can circumvent all of these security features and thus create and maintain an arbitrary number of fake accounts. Our impersonation attack particularly focuses on creating non-existing selfies by relying on Generative Adversarial Network (GAN) techniques during account initialization. Furthermore, we employ reverse engineering to develop a bot that simulates the genuine Elec- troneum app and is capable of operating an arbitrary number of illegitimate accounts on one Android device, enabling the malicious user to obtain an unfairly large payout. 1 INTRODUCTION Rivet, 2019). Due to these effects, both Google and Apple prohibit cryptocurrency mining apps from their During 2017, the first and most popular cryptocurrency, application stores (Apple, 2019; Google, 2018), limiting Bitcoin, experienced an astonishing 13-fold increase in the accessibility of the average smartphone users to crypto mining. Despite this fact, several projects like value (Corcoran, 2017). -

NFT Yearly Report 2020, Fresh from the Oven!
NON-FUNGIBLE TOKENS YEARLY REPORT 2020 FREE EDITION MARKET RESEARCH. TRENDS DECRYPTION. PROJECT REVIEW. EVERYTHING YOU NEED TO KNOW ABOUT THE NFT ECOSYSTEM FOREWORDS The NFT Yearly Report 2020, fresh from the oven! The purpose of this report is to provide an overarching and detailed view of the Non-Fungible Token ecosystem during 2020. The exponential growth within the sector has been particularly impressive, especially given that the Crypto bear market was in full force during most of the early stages of development. There is little doubt that the loyal and tight knit groups who initially evolved around various NFT blockchain projects have since seen the contents of their wallets dramatically increase in value as the ecosystem evolved and NFT projects began to attract more and more outside and mainstream interest. This report is not meant for Non-Fungible experts but to help everyone in or outside the Non- Fungible Tokens ecosystem to better understand what is going on. What is the potential? Why should you care about NFT? 2020 has been an unprecedented year for most of the world's population, with many challenges to face, from a global pandemic and lockdown to political upheavals, riots and not to mention catastrophic natural disasters… we’ve had it all! In stark contrast and perhaps partially due to such turbulent global events, interest and investment in virtual economies and digital assets has boomed, more than ever seen before. Within the Non-Fungible Token ecosystem individual sectors have seen success, Art, Gaming and Digital Assets have all gained remarkable traction during 2020 with this once niche and experimental industry maturing into a force to be reckoned with. -

Pay Toll with Coins: Looking Back on Fbar Penalties and Prosecutions to Inform the Future of Cryptocurrency Taxation
PAY TOLL WITH COINS: LOOKING BACK ON FBAR PENALTIES AND PROSECUTIONS TO INFORM THE FUTURE OF CRYPTOCURRENCY TAXATION Caroline T. Parnass* Cryptocurrencies are gaining a foothold in the global economy, and the government wants its cut. However, few people are reporting cryptocurrency transactions on their tax returns. How will the IRS solve its cryptocurrency noncompliance problem? Its response so far bears many similarities to the government’s campaign to increase Reports of Foreign Bank and Financial Accounts (FBARs). FBAR noncompliance penalties are notoriously harsh, and the government has pursued them vigorously. This Note explores the connections and differences between cryptocurrency reporting and foreign bank account reporting in an effort to predict the future regime of cryptocurrency tax compliance. * J.D. Candidate, 2021, University of Georgia School of Law; M.S., 2018, Georgia State University; B.A., 2013, Wellesley College. Thanks to Professor Camilla E. Watson for her help developing this Note. Dedicated to Nadia Tscherny, Ph.D. 359 360 GEORGIA LAW REVIEW [Vol. 55:359 TABLE OF CONTENTS I. INTRODUCTION .................................................................... 361 II. WHAT IS CRYPTOCURRENCY? ............................................. 365 III. THE IRS’S RESPONSE TO CRYPTOCURRENCY ................... 369 A. ADMINISTRATIVE ACTS ............................................. 369 B. LEGAL ACTION .......................................................... 372 IV. FOREIGN BANK ACCOUNT REPORTING ............................ -

IRS Issues Additional Cryptocurrency Guidance Addressing Hard Forks, Soft Forks, and Airdrops
WWW.ALSTON.COM International Tax ADVISORY n NOVEMBER 15, 2019 Is the IRS HODLing* Out on Us? IRS Issues Additional Cryptocurrency Guidance Addressing Hard Forks, Soft Forks, and Airdrops The cryptocurrency landscape has changed considerably since the mysterious introduction of bitcoin in 2008. Today, the magic Internet money can be used to order pizza, pay employees, day trade, and serve as collateral for loans. The IRS has been notably slow to react. It has issued very limited guidance so far on how it intends to treat cryptocurrency transactions, but even in the absence of such guidance, it has recently begun ramping up its cryptocurrency transaction enforcement efforts. In 2014, the IRS issuedNotice 2014-21, confirming its view that “convertible virtual currencies” are treated as property and thus subject to general tax principles that apply to transactions in property (and not to certain special rules that apply to transactions in currencies). In 2018, the IRS included noncompliance with tax laws relating to the use of cryptocurrencies as one of its new compliance campaigns. (See prior coverage here.) The IRS recently issued new guidance in Rev. Rul. 2019-24 and an updated set of frequently asked questions addressing the tax treatment of cryptocurrencies that undergo a hard fork and the treatment of a subsequent airdrop. Background Cryptocurrencies use distributed ledger, or “blockchain,” technology to verify and secure transactions between users. Each transaction is recorded in a block of transactions, which are linked to all prior and subsequent blocks on the blockchain. A blockchain runs on a specific protocol that dictates its rules. -

Securities and Tax Law Effects of Token Airdrops
Advisory | Blockchain May 2018 Securities and Tax Law Effects of Token Airdrops This GT Advisory examines token airdrops in blockchain technology development and finance.1 The term “airdrop” means a project founder’s distribution of tokens or cryptocurrencies without monetary payment from the token recipient in an evolving cryptocurrency lexicon. The practice of token airdrop distributions increased in late 2017 and early 2018 in the midst of closer regulatory scrutiny of initial coin offerings (ICOs) in the United States and worldwide. However, the practice of airdropping tokens to avoid “sales” of tokens while promoting a project is itself under close regulator watch, based on a fundamental tenet of the federal securities laws prohibiting engaging in a transaction indirectly, which would not be allowed directly. It is recommended for token issuers to not engage in any form of airdrop distribution in the absence of advice from experienced securities law practitioners. Airdrop Activity in ICOs and Marketing Campaigns Token airdrops or “free crypto” distributions are occurring in conjunction with ICOs and emergent blockchain technology project marketing campaigns. Generally, airdrops take place when a new blockchain project distributes free tokens to existing holders of certain cryptocurrency (also known as the base token in the context of airdrops), such as bitcoin and Ethereum, although not limited to these cryptocurrencies. Airdrops are in some instances utilized as a pre-ICO marketing strategy for an upcoming project designed to build brand recognition, attract users, and provide benefits to the blockchain project and user network. An airdrop can either be announced or unannounced prior to the distribution. -

I See a Future Where Crypto, Nfts, and Blockchain Will Be the Norm, Rather Than the Exception."
1 “NFTs could act as a catalyst, to help society create the perfect balance between creativity and rationality.” @andreabonac_art (Bison Trails, 2020) 2 Prerelease DRAFT v0.971 Celebrities talk NFTs 5 Basic Tech Concepts 9 What is Fungible and Non-Fungible? 9 Fungible 9 Non-Fungible (NF) 10 What is a Digital Wallet 19 NFT Listing Marketplaces: Should you create your own? 26 Global Marketplace 26 Your Own Marketplace 26 NFT Platform Features 27 What can we do with NFTs? 31 Industries that may be Disrupted by NFTs 67 Art 67 Photography 68 Music 68 Events 68 Sports Memorabilia 69 Redemption Coupons 69 Create an NFT 70 Create your own Marketplace 72 Whitelabel Marketplace Examples 77 Podcasts 77 Fan Clubs 80 Sport Events 82 Consensus Event 83 Music 84 Quick Start to create your own NFT Marketplace 85 Making money from NFTs 87 NFT Energy Consumption 89 NFT Dictionary 90 NFT.NYC Speakers 103 NFT.NYC Partners 113 3 Intentionally Blank 4 Celebrities talk NFTs In early 2021 NFTs gain mainstream traction among prominent artists, public figures, and celebrities. Snoop Dogg “I am excited about it, ya dig?” @SnoopDogg Snoop Dogge Coins NFT Rob Gronkowski "When I was a kid my brothers and I collected every single trading card out there...It's great to be that first athlete to get on NFTs." @RobGronkowski Career Highlight NFT 5 Lindsay Lohan "It's only a matter of time till everyone in Hollywood and beyond gets involved" and also "I see a future where crypto, NFTs, and blockchain will be the norm, rather than the exception." Lindsay Lohan, Actress @lindsaylohan Lightning NFT Paris Hilton “NFTs have literally taken over my entire mind and soul.” @ParisHilton “I’m obsessed. -

Address Clustering Heuristics for Ethereum
Address clustering heuristics for Ethereum Friedhelm Victor[0000−0001−8329−3133] Technical University of Berlin, Straße des 17. Juni 135, 10623 Berlin, Germany [email protected] Abstract. For many years, address clustering for the identification of entities has been the basis for a variety of graph-based investigations of the Bitcoin blockchain and its derivatives. Especially in the field of fraud detection it has proven to be useful. With the popularization and increasing use of alternative blockchains, the question arises how to rec- ognize entities in these new systems. Currently, there are no heuristics that can directly be applied to Ethereum's account balance model. This drawback also applies to other smart contract platforms like EOS or NEO, for which previous transaction network analyses have been lim- ited to address graphs. In this paper, we show how addresses can be clustered in Ethereum, yielding entities that are likely in control of mul- tiple addresses. We propose heuristics that exploit patterns related to deposit addresses, multiple participation in airdrops and token autho- rization mechanisms. We quantify the applicability of each individual heuristic over the first 4 years of the Ethereum blockchain and illustrate identified entities in a sample token network. Our results show that we can cluster 17.9% of all active externally owned account addresses, indi- cating that there are more than 340,000 entities that are likely in control of multiple addresses. Comparing the heuristics, we conclude that the deposit address heuristic is currently the most effective approach. Keywords: Blockchain · Accounts · Ethereum · Network Analysis. 1 Introduction Since the introduction and popularization of Bitcoin [22] in 2009, blockchain and cryptocurrency analysis has gained a foothold in science as well as in business. -

Dapp Ecosystem Report|August 2020
DappRadar Dapp Ecosystem Report | August 2020 Dapp Ecosystem Report|August 2020 Total transaction volume surpassed $24 Billion as high Ethereum GAS prices failed to halt DeFi’s momentum. Our August 2020 overview of the dapp ecosystem covers a total of seven blockchains. Not only the three main dapp blockchains – Ethereum, TRON, and EOS are included, but also Steem, Hive, ThunderCore, and WAX. Within this review, we are going to analyze daily active wallets, total value locked, transaction volumes, and native protocols token price changes. Table of Contents ● Key Takeaways 2 ● Ethereum 3 - 6 ● TRON 7 - 9 ● EOS 10 - 12 ● The best of the rest 13 - 14 ● Conclusions 14 Key takeaways ● High Ethereum gas prices have not affected the DeFi ecosystem yet. $24 billion in transaction volume generated in August. More than $7 billion total value locked at the end of August. ● Ethereum transaction volumes account for 94% of total transaction volumes in August. The protocol increased its share by 2%. ● TRON showed positive development in all metrics. Daily active wallets and transaction volumes reached their best results in 2020. ● EOS spiked in all metrics. DeFi and DEX dapps were behind the sustained growth. ● Other protocols such as Hive and WAX increased steadily, ThunderCore exploded and reached 25,000 active wallets daily. 2 Ethereum Ethereum is still facing contradictory results. High Ethereum gas prices decreased the number of active wallets drastically in almost all categories. On the other hand, DeFi and DEX dapps witnessed different activity trends. Although a transaction currently costs more than $50 at the time of writing, it hasn’t slowed down DeFi enthusiasts. -

CLE Materials New York Track | Saturday January 11, 2020
Fordham Law | CLE BRIDGE THE GAP Satisfy a full year of CLE credits in one weekend CLE Materials New York Track | Saturday January 11, 2020 Fordham Law School Skadden Conference Center Costantino Room (Second Floor) 150 W 62nd Street New York, NY 10023 NEW YORK DAY 1 – Saturday January 11, 2020 Table of Contents 1. Speaker Biographies (view in document) 2. CLE Materials Panel 1: Legal Writing Supplemental Materials. Ramos, Leah; Cheng-de Castro, Supplemental Material. Estate Planning Questionnaire Pei Pei. Fordham Law School’s 2020 Bridge the Gap Legal Template. (View in document) Writing Panel Presentation Detailed Slides. (View in document) Bergen County Surrogate’s Court. Intestacy Information. (View in document) Lebovits, Gerald. New York State Bar Journal 80-DC N.Y. St. B.J. 64. Plain English: Eschew Legalese. Justia 108 N.J.L.J 501. Attorney’s Including Person Gain in (View in document) Client’s Will. (View in document) Panel 2: Criminal Justice Legal Ethics Opinion 1515: Attorney Drafting Instrument Which Names Self Either As Personal Representative or Kossover, Andrew. NYSACDL-2020 Reform Article. Trustee or Which Directs Such Other Designee to Employ Finally! True Criminal Justice Reform. (View in document) Attorney as Fiduciary Administrator. (View in document) Panel 3: Employment Law NJ Inheritance Tax Guide 2019. (View in document) Blocker, Tanya; Johnson, Natalya G.; Yim, Mihcael. New Jersey Division of Taxation. A Guide to Being an Fordham Bridge the Gap 2020 Labor & Employment Executor. (View in document) Update – Sexual Harrassment, Reasonable Accommodations, Pay Equity, Medical Marijuana, Will Form 1 Simple with Trusts Last Will and Testament.