A Forensic Analysis of Security Events on System Z, Without the Use Of
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Parker Review
Ethnic Diversity Enriching Business Leadership An update report from The Parker Review Sir John Parker The Parker Review Committee 5 February 2020 Principal Sponsor Members of the Steering Committee Chair: Sir John Parker GBE, FREng Co-Chair: David Tyler Contents Members: Dr Doyin Atewologun Sanjay Bhandari Helen Mahy CBE Foreword by Sir John Parker 2 Sir Kenneth Olisa OBE Foreword by the Secretary of State 6 Trevor Phillips OBE Message from EY 8 Tom Shropshire Vision and Mission Statement 10 Yvonne Thompson CBE Professor Susan Vinnicombe CBE Current Profile of FTSE 350 Boards 14 Matthew Percival FRC/Cranfield Research on Ethnic Diversity Reporting 36 Arun Batra OBE Parker Review Recommendations 58 Bilal Raja Kirstie Wright Company Success Stories 62 Closing Word from Sir Jon Thompson 65 Observers Biographies 66 Sanu de Lima, Itiola Durojaiye, Katie Leinweber Appendix — The Directors’ Resource Toolkit 72 Department for Business, Energy & Industrial Strategy Thanks to our contributors during the year and to this report Oliver Cover Alex Diggins Neil Golborne Orla Pettigrew Sonam Patel Zaheer Ahmad MBE Rachel Sadka Simon Feeke Key advisors and contributors to this report: Simon Manterfield Dr Manjari Prashar Dr Fatima Tresh Latika Shah ® At the heart of our success lies the performance 2. Recognising the changes and growing talent of our many great companies, many of them listed pool of ethnically diverse candidates in our in the FTSE 100 and FTSE 250. There is no doubt home and overseas markets which will influence that one reason we have been able to punch recruitment patterns for years to come above our weight as a medium-sized country is the talent and inventiveness of our business leaders Whilst we have made great strides in bringing and our skilled people. -
Solucom No. 5 Among IT Consulting Firms in France
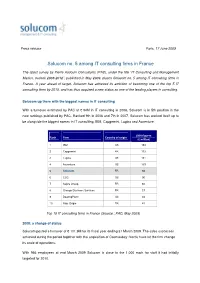
Press release Paris, 17 June 2009 Solucom no. 5 among IT consulting firms in France The latest survey by Pierre Audouin Consultants (PAC), under the title “IT Consulting and Management Market, outlook 2008-2012”, published in May 2009, places Solucom no. 5 among IT consulting firms in France. A year ahead of target, Solucom has achieved its ambition of becoming one of the top 5 IT consulting firms by 2010, and has thus acquired a new status as one of the leading players in consulting. Solucom up there with the biggest names in IT consulting With a turnover estimated by PAC at € 94M in IT consulting in 2008, Solucom is in 5th position in the new rankings published by PAC. Ranked 9th in 2006 and 7th in 2007, Solucom has worked itself up to be alongside the biggest names in IT consulting, IBM, Capgemini, Logica and Accenture. 2008 figures Rank Firm Country of origin (€ million) 1 IBM US 194 2 Capgemini FR 173 3 Logica UK 151 4 Accenture US 139 5 Solucom FR 94 6 CSC US 90 7 Sopra Group FR 66 8 Orange Business Services FR 57 9 BearingPoint US 44 10 Atos Origin FR 41 Top 10 IT consulting firms in France (Source : PAC, May 2009) 2008: a change of status Solucom posted a turnover of € 101.9M for its fiscal year ending 31 March 2009. The sales successes achieved during the period together with the acquisition of Cosmosbay~Vectis have let the firm change its scale of operations. With 966 employees at end March 2009 Solucom is close to the 1,000 mark for staff it had initially targeted for 2010. -

IDC Marketscape Names Accenture a Digital Strategy Leader | Accenture
IDC MarketScape IDC MarketScape: Worldwide Digital Strategy Consulting Services 2021 Vendor Assessment Douglas Hayward IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape Worldwide Digital Strategy Consulting Services Vendor Assessment Source: IDC, 2021 June 2021, IDC #US46766521 Please see the Appendix for detailed methodology, market definition, and scoring criteria. IDC OPINION This study represents the vendor assessment model called IDC MarketScape. This research is a quantitative and qualitative assessment of the characteristics that explain a vendor's current and future success in the digital strategy consulting services marketplace. This study assesses the capabilities and business strategies of 13 prominent digital strategy consulting services vendors. This evaluation is based on a comprehensive framework and a set of parameters expected to be most conducive to success in providing digital strategy consultancy. A significant component of this evaluation is the inclusion of digital strategy consulting buyers' perception of both the key characteristics and the capabilities of these providers. This client input was provided primarily from the vendors' clients, supplemented with a worldwide survey. Key findings include: . Consultancies are getting the basics right. Reference clients that IDC spoke with were impressed by the quality of the people from the leading digital strategy consultancies. On average, reference clients gave consultancies highest scores for people quality, action orientation, and client-specific insight. This indicates that digital strategy consultancies are getting the basics right — they are recruiting smart and empathetic people and are training and developing them well, they are getting to know their clients inside out, and they are producing very useful advice as a result. Clients want to be challenged more than ever by their digital strategy consultants. -

Integrated Virtual Ethernet Adapter Technical Overview and Introduction
Front cover Integrated Virtual Ethernet Adapter Technical Overview and Introduction Unique and flexible up to 10 Gbps Ethernet industry standard virtualizable network solution Hardware accelerated for improved throughput Configurable connections between LPARs and the physical network without the Virtual I/O Server Laurent Agarini Giuliano Anselmi ibm.com/redbooks Redpaper International Technical Support Organization Integrated Virtual Ethernet Adapter Technical Overview and Introduction October 2007 REDP-4340-00 Note: Before using this information and the product it supports, read the information in “Notices” on page v. First Edition (October 2007) This edition applies to IBM AIX Version 6, Release 1, the IBM System p 570, 560, 550, and 520, and the Hardware Management Console Version 7. © Copyright International Business Machines Corporation 2007. All rights reserved. Note to U.S. Government Users Restricted Rights -- Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Notices . .v Trademarks . vi Preface . vii The team that wrote this paper . vii Become a published author . viii Comments welcome. viii Chapter 1. Integrated Virtual Ethernet adapter overview . 1 1.1 Introduction . 2 1.2 Advanced hardware features . 3 1.3 Virtualization features . 3 1.3.1 Virtualized logical ports . 3 1.3.2 Physical ports and system integration. 4 1.4 System p virtualization review. 7 1.4.1 Virtualization features and options . 7 1.5 IVE and Virtual I/O Server positioning. 9 Chapter 2. Integrated Virtual Ethernet architecture. 11 2.1 Architecture introduction . 12 2.2 Logical and physical components . 13 2.2.1 IVE logical component introduction. 13 2.2.2 IVE and physical, logical, and port groups . -

Capgemini U.S./ Worldwide | Systems Integrator
Launch Partner Solutions Atos Origin France/ Worldwide | Systems Integrator PARTNERS ARE TALKING Solution Summary ―Being an early adopter of Microsoft innovations will complement the company culture of Atos Origin. Wave • Based on the robust, scalable, and flexible platform that 2010 server-related technologies will improve the includes Microsoft® SharePoint® 2010, Office 2010, and Exchange Server 2010, Atos Origin will develop several productivity and collaboration efforts of our employees in solutions and standard services including Solvency II in their day-to-day work.‖ Motion, Procure to Pay in Motion, and AO Scientific - Francois Gruau, Senior Vice President, Community. Atos Origin's SharePoint portal development Business Development & Innovation, Atos Origin service enables companies to optimally access, manage, and utilize information whilst enabling new ways of communication, connection, and collaboration. • Solvency II in Motion is a project management infrastructure that helps insurance companies to better execute project coordination, document management, About the partner collaboration, and risk management. Procure to Pay in Motion assists purchasing departments through automation Atos Origin is a leading international information and collaborative functionality. The Scientific Community is technology (IT) services company, providing hi-tech the best 50 scientific people from within the organization. They are ―creators of change, making sure that whenever our transactional services, consulting, systems integration, clients choose us, they always get the best solution and managed operations to deliver business outcomes available.‖ globally. Atos Origin, Atos Worldline, and Atos Consulting employ 50,000 people. Atos Origin is the Worldwide Information Technology Partner for the Atos Origin Favorites Olympic Games and has a client base of international Business Connectivity Services | Visio® Services | Advanced companies across all sectors. -

GEO Awards 2009.Pdf
Chief Executive Founding Corporate Sponsors Michael Bendorf, GEO Charles Schwab Board of Directors Morgan Stanley CHAIR: Carine M. Schneider, Global Shares Smith Barney VICE-CHAIR: Janet Cooper, Linklaters Compensation Phil Ainsley, Equiniti Venture Group John Bagdonas, Independent Computershare Juan Bonilla, Cuatrecasas Deutsche Bank June Anne Burke, Baker & McKenzie Alex Brown Lindsey Doud, RBC cees E*TRADE FINANCIAL Jay Foley, Morgan Stanley Smith Barney Global Reward Judith Greaves, Pinsent Masons Plan Group Véronique Japp, BNP Paribas Securities Services HBOS Employee Desiree Klein-Wagner, Allianz Equity Solutions Nancy Mesereau, Fidelity Stock Plan Services Hewitt Bacon Steve Morey, Proctor & Gamble & Woodrow Brian Ruff, Eli Lilly & Company Linklaters Mary Samsa, Seyfarth Shaw LLP Merrill Lynch Barbara Seta, UBS AG Pinsent Masons Sean Trotman, Deloitte PricewaterhouseCoopers James Wulforst, E*TRADE Financial Prudential Financial Corporate Services, Incorporated UBS Financial Advisory Council Services, Inc. CHAIR: Steve Morey, Proctor & Gamble Watson Wyatt Worldwide Karen Beyer, General Electric Provider Council Kelley Garrett, Microsoft Corp. Wendy Jennings, Riverbed Technology, Inc. CHAIR: Jewon Wee, ISP Advisors Yvonne Prang, McDonald’s Deutschland Inc. CO-CHAIR: Paul Stoddart, Brian Ruff, Eli Lilly & Company HBOS Employee Equity Bernice Toy, Cisco Systems, Inc. Solutions Nigel Turner, BP Debbie Veys, Vodafone Group Plc Dominique Welcomme, Vivendi 1442 E. Lincoln Ave. #487 Orange, CA 92865 US TEL +1 714-630-2908 • FAX +1 253-423-8390 • WEB www.globalequity.org ost Innovative M &CreativeD esign TheGEO war AJ� udges The 00 2 9 war ACategories� The 2 009 A war� Categories A�out �he GEO A war�s Welcome �o �heGEO 2009 war s Dear GEO Members, A � The 2009 GEO Awards celebrate outstanding performance in the international employee share plan commu- nity by honoring the impressive achievements of ten companies from around the world. -

CDP Supply Chain 2011
CARBON DISCLOSURE PROJECT CDP Supply Chain 2011 Frances Way Head of Supply Chain [email protected] UK Office +44 (0)20 7415 7095 US Office +1 212 378 2085 2010 CDP SuPPly Chain MeMberS CDP Supply Chain 2011 Accenture Hynix Semiconductor CDP Supply Chain enables businesses to successfully implement supplier engagement strategies around greenhouse gas emissions and risk management in a Acer Inc. IBM changing climate. ASUSTeK Computer Imperial Tobacco Group Banco Bradesco Johnson & Johnson The Carbon Disclosure Project (CDP) is the recognized leader in carbon reporting Bank of America Johnson Controls and has assembled the largest global database of corporate emissions and climate Barclays Juniper Networks change information. Using the same standardized reporting platform, CDP Supply Chain provides world-class data collection so that members can calculate their Baxter International KAO Corporation supply chain emissions and better manage risk. Other benefits include best practice Kellogg Company Becker Underwood sharing and unique cross-sector networking opportunities. Biogen Idec Kimberly-Clark Corporation BT Group L’O r e a l Cadbury Logica Chicony Power Technology Merck & Co. Colgate-Palmolive Company Millipore Coloplast Molson Coors “Logica has been reporting via the CDP since 2006 and ConAgra Foods National Australia Bank in 2009 achieved a leading position in our sector in CO2 Danone National Grid emission reduction and strategy. We use it to drive Dell* Nestle reporting across our organization and as a result have Diebold PepsiCo* saved £10M in our UK organization alone. By supporting EADS* Philips Electronics our suppliers to report via the CDP we want to help them Elopak Reckitt Benckiser to make similar energy, carbon and cost savings. -

Istorie Unix/Linux
1. Introducere & Instalare 1.1 Istorie Unix/Linux Istorie Unix/Linux Anii 60 Bell Laboratories (divizie de cercetare a AT&T) formeaza un consortiu impreuna cu MIT (Massachusetts Institute of Technology) si General Electric pentru a dezvolta un sistem de operare interactiv, multiuser si multi-tasking numit Multics (Multiplexed Information and Computing Service) care sa ruleze pe Mainframe-uri GE-645. Proiectul nu a avut succesul scontat, iar Bell Labs se retrage. Un programator pe nume Ken Thompson nu renunta si continua dezvoltarea proiectului impreuna cu un alt programator pe nume Dennies Ritchie. 1970 Noul proiect este numit Unics (Uniplexed Information and Computing Service). Numele este atribuit de Brian Kernighan, iar mai tarziu este schimbat in UNIX. Sistemul de operare este scris in limbaj de asamblare. 1973 Unix este rescris in C pentru a putea fi portabil (sa ruleze si pe alte masini). Acest lucru a dus la o dezvoltare accelerata. AT&T distribuie noul sistem universitatilor, marilor firme dar si guvernului USA. 1973-1979 Unix-ul este in continuare dezvoltat in cadrul Universitatii Berkeley din California. Printre imbunatatiri sunt shell-ul C, editorul VI precum si alte utilitare necesare. Tot aici este adaugat suportul pentru lucrul in retea. 1980-1983 AT&T lanseaza prima versiune comerciala de UNIX fara a introduce modificarile aduse de Berkeley. 1982 Un programator din cadrul proiectului BSD (Berkeley Software Distribution - Berkeley Unix) impreuna cu cativa colegi de la Stanford University creaza firma SUN - Stanford University Network. Prima lansare de Unix are loc in 1983 si se numeste SunOS. Printre altele sunt introduse NFS (Network File System) care devine un standard. -

CGI 2018 Annual Report
FISCAL 2018 RESULTS Contents 1 Management’s Discussion and Analysis 63 Management’s and Auditors’ Reports 68 Consolidated Financial Statements 128 Shareholder Information FISCAL 2018 RESULTS Management’s Discussion and Analysis November 7, 2018 Basis of Presentation This Management’s Discussion and Analysis of the Financial Position and Results of Operations (MD&A) is the responsibility of management and has been reviewed and approved by the Board of Directors. This MD&A has been prepared in accordance with the requirements of the Canadian Securities Administrators. The Board of Directors is ultimately responsible for reviewing and approving the MD&A. The Board of Directors carries out this responsibility mainly through its Audit and Risk Management Committee, which is appointed by the Board of Directors and is comprised entirely of independent and financially literate directors. Throughout this document, CGI Group Inc. is referred to as “CGI”, “we”, “our” or “Company”. This MD&A provides information management believes is relevant to an assessment and understanding of the consolidated results of operations and financial condition of the Company. This document should be read in conjunction with the audited consolidated financial statements and the notes thereto for the years ended September 30, 2018 and 2017. CGI’s accounting policies are in accordance with International Financial Reporting Standards (IFRS) as issued by the International Accounting Standards Board (IASB). All dollar amounts are in Canadian dollars unless otherwise noted. Materiality of Disclosures This MD&A includes information we believe is material to investors. We consider something to be material if it results in, or would reasonably be expected to result in, a significant change in the market price or value of our shares, or if it is likely that a reasonable investor would consider the information to be important in making an investment decision. -

EKERT, David Signed Statement
Health Payroll System Commission of Inquiry STATEMENT OF DAVID EKERT I, David William Ekert of a residential address known to the Commission of Inquiry state as follows: BACKGROUND 1. I am currently a Senior Consultant with a firm named Information Professionals and I have contracted to that business in this role since December 2005. 2. I am a Certified Practising Accountant and I have a degree in Accounting and I also hold the award of a Master of Business Administration. 3. Prior to commencing contract employment with Information Professionals I worked for Hudson Global Resources for a period of approximately two years. Prior to working for Hudson Global Resources I was employed by a firm called Anderson Contracting which was a business division of Andersen Consulting. On 1 January 2001, Andersen Contracting was renamed Diversiti and Andersen Consulting was renamed Accenture. I was employed by Andersen and Diversiti, which remained an Accenture business, from 1997 to 2003. In December 2005 I commenced some contracting work with the Queensland State Government at CorpTech . Work with CorpTech 4. I obtained the consultancy work with CorpTech through a person named Mark Nicholls. 5. Mark was the sole director of Information Professionals. He and I had previously known each other through different consultancy engagements. He had completed some consultancy work with Queensland Rail early in 2005 and we used to talk over coffee about further consultancy work we might be able to obtain with Government. Mark subsequently rang me in December 2005 and offered me a contract to complete some work for CorpTech as a strategist and planner. -

Logica Annual Review
LOGICA ANNUAL REVIEW 1989--- Talbot Leafafa Plant c1839 front saver: Man Ray L: Wotan 47713121 1924 back mm: chh Duyfvr Night 1988 Contents In the twenty years since its founding in 1969 Logica has made its mark on the computer software Introduction and systems industry. We have achieved a record of Review of the year growth, a worldwide spread ofoperations and a Staff reputation for quality that are impressive by any standards. We have also been involved in some of Business analysis UluPNrI the key developments in our field developments Research and development that have had a real impact on the advancement or the application of technology and sometimes on Management consultancy \O\l the world at large. Markets Finance 12 We feature some of these landmark projects in this Central and local years Annual Review alongside descriptions ofour government 14 recent work. Particularly noteworthy is the number Defence 16 ofearly clients with whom we continue to work Space 18 successfully today. Logica is proud to have won the Energy and utilities 20 loyalty and support of so many of the worlds major Manufacturing 22 organizations as its clients. Transport 24 Computing and electronics 26 The commitment and excellence ofLogicas staff Broadcasting and media 28 have also been essential ingredients in the Telecommunications and companys succ s. In the staffseetion ofthe review POS[ 30 we concentrate on the approach to career and management development that has enabled Logica Report and accounts to maintain over two decades both momentum for Company information 33 growth and a strong corporate culture, Report ofthe directors 34 Financial results As a focus for our twentieth birthday celebrations 0 Consolidated prot and this year Logica is sponsoring, The Art of loss account 36 Photography, a magnificent exhibition which 0 Consolidated balance opened at Londons Royal Academy ofArts in sheet 37 September 1989 after visiting, the US and Australia. -

CGI Annual Information Form
ANNUAL INFORMATION FORM For the fiscal year ended September 30, 2014 December 12, 2014 TABLE OF CONTENTS INCORPORATION AND DESCRIPTION OF CAPITAL STOCK .................................................................................. 1 Corporate Structure ..................................................................................................................................................................... 1 Capital Structure ........................................................................................................................................................................... 2 Stock Splits .......................................................................................................................................................... 2 Market for Securities, Trading Price and Volume ....................................................................................................................... 2 Normal Course Issuer Bid and Share Repurchases............................................................................................. 3 CORPORATE GOVERNANCE ..................................................................................................................................... 3 Board and Standing Committee Charters and Codes of Ethics ................................................................................................ 3 Audit Committee Information ......................................................................................................................................................