COMPARATIVE ANALYSIS of IPHONE IMAGE DATA ACROSS VARIOUS TRANSFER METHODS by JOHN OZ NELSON B.P.S., Berklee College of Music, 20
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

How Do I Get Started with Aperture?
1 How Do I Get Started with Aperture? COPYRIGHTED MATERIAL 004_9781118274293-ch01.indd4_9781118274293-ch01.indd 2 99/18/12/18/12 112:002:00 PPMM 1 2345678910 Aperture is like iPhoto on steroids in some ways; but in other ways, it’s a com- pletely different beast. Unlike iPhoto, it’s designed to be an incredibly flexi- ble image, video, and audio file asset management tool that you can integrate into your existing workflow. However, this flexibility means that Aperture has more jargon, settings, and buttons than iPhoto. This chapter helps demystify Aperture’s jargon and shows you key fundamentals you need to know when using Aperture. Understanding Why Aperture Is a Key Part of Your Workflow . 4 Working with Aperture’s File Structure . 6 A Brief Tour of Aperture’s Interface . 13 Basic Customization Options . 26 004_9781118274293-ch01.indd4_9781118274293-ch01.indd 3 99/18/12/18/12 112:002:00 PPMM Aperture 3 Portable Genius Understanding Why Aperture Is a Key Part of Your Workflow Most photographers agree that the time you spend behind the lens shooting is the best part of being a photographer, and all the other stuff (processing an image, categorizing it, trying to sell it, or using it to promote business) is really just annoying. While digital photography enables you to be more creative as a photographer, from being able to see right away whether you got the shot to being able to experiment as much as you want with the only cost being hard drive space, the “other stuff” arguably gets more frustrating because now you have to manage digital files instead of physical film and learn to use multiple programs to develop and output your images. -
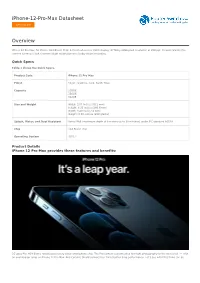
Iphone-12-Pro-Max Datasheet Overview
iPhone-12-Pro-Max Datasheet Get a Quote Overview iPhone 12 Pro Max, 5G Phone. A14 Bionic Chip; 6.7-inch all-screen OLED display; 2778-by-1284-pixel resolution at 458 ppi; Ceramic Shield; Pro camera system; LiDAR Scanner; Night mode portraits; Dolby Vision recording. Quick Specs Table 1 shows the Quick Specs. Product Code iPhone 12 Pro Max Finish Silver, Graphite, Gold, Pacific Blue Capacity 128GB 256GB 512GB Size and Weight Width: 3.07 inches (78.1 mm) Height: 6.33 inches (160.8 mm) Depth: 0.29 inch (7.4 mm) Weight: 8.03 ounces (228 grams) Splash, Water, and Dust Resistant Rated IP68 (maximum depth of 6 meters up to 30 minutes) under IEC standard 60529 Chip A14 Bionic chip Operating System iOS 14 Product Details iPhone 12 Pro Max provides these features and benefits: 5G goes Pro. A14 Bionic rockets past every other smartphone chip. The Pro camera system takes low-light photography to the next level — with an even bigger jump on iPhone 12 Pro Max. And Ceramic Shield delivers four times better drop performance. Let’s see what this thing can do. 5G transforms iPhone with accelerated wireless speeds and better performance on congested networks.5 Now you can download huge files on the go or stream high-quality HDR movies. Without. All. The. Lag. iPhone also has the most 5G bands of any smartphone so you get 5G in more places. And all that speed opens up amazing possibilities for the future of apps. A14 Bionic The only thing even close was our last chip. -

X86 Disassembly Exploring the Relationship Between C, X86 Assembly, and Machine Code
x86 Disassembly Exploring the relationship between C, x86 Assembly, and Machine Code PDF generated using the open source mwlib toolkit. See http://code.pediapress.com/ for more information. PDF generated at: Sat, 07 Sep 2013 05:04:59 UTC Contents Articles Wikibooks:Collections Preface 1 X86 Disassembly/Cover 3 X86 Disassembly/Introduction 3 Tools 5 X86 Disassembly/Assemblers and Compilers 5 X86 Disassembly/Disassemblers and Decompilers 10 X86 Disassembly/Disassembly Examples 18 X86 Disassembly/Analysis Tools 19 Platforms 28 X86 Disassembly/Microsoft Windows 28 X86 Disassembly/Windows Executable Files 33 X86 Disassembly/Linux 48 X86 Disassembly/Linux Executable Files 50 Code Patterns 51 X86 Disassembly/The Stack 51 X86 Disassembly/Functions and Stack Frames 53 X86 Disassembly/Functions and Stack Frame Examples 57 X86 Disassembly/Calling Conventions 58 X86 Disassembly/Calling Convention Examples 64 X86 Disassembly/Branches 74 X86 Disassembly/Branch Examples 83 X86 Disassembly/Loops 87 X86 Disassembly/Loop Examples 92 Data Patterns 95 X86 Disassembly/Variables 95 X86 Disassembly/Variable Examples 101 X86 Disassembly/Data Structures 103 X86 Disassembly/Objects and Classes 108 X86 Disassembly/Floating Point Numbers 112 X86 Disassembly/Floating Point Examples 119 Difficulties 121 X86 Disassembly/Code Optimization 121 X86 Disassembly/Optimization Examples 124 X86 Disassembly/Code Obfuscation 132 X86 Disassembly/Debugger Detectors 137 Resources and Licensing 139 X86 Disassembly/Resources 139 X86 Disassembly/Licensing 141 X86 Disassembly/Manual of Style 141 References Article Sources and Contributors 142 Image Sources, Licenses and Contributors 143 Article Licenses License 144 Wikibooks:Collections Preface 1 Wikibooks:Collections Preface This book was created by volunteers at Wikibooks (http:/ / en. -
Change Or Remove Your Payment Information from Your Itunes Store
Change or remove your payment information from your iTunes ... http://support.apple.com/kb/HT1918 Change or remove your payment information from Languages English Helpful? Yes No your iTunes Store account (Apple ID) On your iPhone, iPad, or iPod touch, you can change the payment information for your Apple ID from the Account Information page. On your Mac or PC, you can change your payment information from the iTunes Store. When you change your credit card number or billing address through the iTunes Store, you also update that information in iCloud, the Apple Online Store, iPhoto, and Aperture. Change your payment information on an iPhone, iPad, or iPod touch 1. Tap Settings on the Home screen. 2. Tap iTunes & App Store. 3. Tap your Apple ID. (You may need to sign in with your Apple ID.) 4. Tap View Apple ID. 5. Tap Payment Information. 6. Change your information and tap Done. After you change your payment information, the iTunes Store places an authorization hold on your credit card. Change your payment information on a Mac or PC 1. Click to open your account in iTunes (you may need to sign in with your Apple ID), or follow these steps: a. Open iTunes and click iTunes Store. 1 of 3 8/29/14, 12:37 PM Change or remove your payment information from your iTunes ... http://support.apple.com/kb/HT1918 b. Click Sign In and enter your Apple ID. c. Click your Apple ID and select Account. 2. From the Account Information page, click Edit to the right of Payment Type. -

Does That Look Right?
Gregory Helmstetter Digital Preservation Final Project December 15, 2017 Does That Look Right? Playback Software in Digital Preservation With the ubiquity of digital files persisting throughout every aspect of modern life, from cell phone videos to time-based art to video preservation and archiving, one major question is often asked when playing back a digital file: Does that look right? This is an important question for several reasons. First, this is often the first question conservators, preservationists, or archivists ask when playing back video on any platform, whether it be in digital playback software or on analog machines. Second, as of the writing of this paper, I am frankly still questioning whether or not particular digital videos look the way they were intended to look and still questioning how software plays a role in the presentation of videos. And third, the results of this paper and the informal case study I conducted specifically to test playback software may generate more questions that conservators, et al, should ask when playing back digital files. This paper, therefore, will survey a number of playback software tools that archives rely on in quality control processes (particularly as they pertain to large-scale digital preservation workflows); it will consider the critical role that software plays when displaying digital content for preservation and quality control processes and how software is integrated into these workflows; and it will outline and address issues one might encounter when playing digital video files on different software. The Case Study First it will be beneficial to discuss from where this idea originated. -

Parental Privacy Disclosure 1114 EN.Pages
Apple ID For Students Parent Privacy Disclosure !English | Español Protecting children is an important priority for everyone at Apple, especially in the context of education. We believe in transparency and giving parents the information they need to determine what is best for their child and their child's education. We will not knowingly collect, use or disclose personal information from students without parental consent or share such personal information with third parties for their marketing purposes. As a parent or guardian, you want the best learning environment for your student. Your student's school has provided them with an Apple device so they can have access to a customized learning experience, one that makes learning relevant and allows for creativity, collaboration, and critical thinking. We work hard to offer students and schools access to a wide array of educational resources in conjunction with controls for parents that are intuitive and customizable. By creating an Apple ID for your child you enable them to fully utilize their Apple device, access the great educational content available in the App Store, iBooks Store, and iTunes U, share the materials they create, and have their own personalized Apple ID experience using all of the services and content available to an Apple ID account holder. PLEASE NOTE: THIS DISCLOSURE DOES NOT APPLY TO THE DATA COLLECTION PRACTICES OF ANY THIRD PARTY APPS. PRIOR TO PURCHASE OR DOWNLOAD, YOU SHOULD REVIEW THE TERMS, POLICIES, AND PRACTICES OF SUCH THIRD PARTY APPS TO UNDERSTAND WHAT DATA THEY MAY COLLECT FROM YOUR STUDENT AND HOW SUCH DATA MAY BE USED. -

Resume (Here Here)
Michael A. Crane : User Experience : User Interaction (312) 909-1570! [email protected] ! www.realuses.com OBJECTIVE I am currently seeking a position within an organization or design firm in User Experience / User Interaction (UI/UX) and/or Interaction Design (IxD). I am a masters candidate in Human-Computer Interaction, and would like to continue focusing on producing creative interfaces based on user-centered design prin- ciples. My ultimate goal is to work, collaborate & learn from creative, driven people. My motivation is fueled by working on creating better interfaces & experience's for the user; focusing on making experiences using the web, application's & technology easier for the user. Ultimately, I would like to work with software or web design firms, communicating application design principles & strategies for ongoing development. In my work, I have always tried to simplify communication barriers, fo- cusing on bridging the gap between end-users, designers & developers. SPECIALTIES User experience, user interaction, website layout & design, schematics, wire-framing, prototyping, information architecture. LANGUAGES (X)HTML | CSS | JavaScript | jQuery | ActionScript 3 | Markdown EDUCATION DePaul University, Chicago, IL !2009 - Present MS Candidate | Human-Computer Interaction Illinois Institute of Technology, Chicago, IL !2004-2007 MS | Personnel & Human Resource Development Northwestern University, Chicago, IL !2006 Executive Certificate | Managing Product Design & Development University of Colorado at Boulder, Boulder, CO !1999-2003 BS | Psychology WORK EXPERIENCE UI/UX Designer | SpiderOak, San Francisco, CA!Oct 2011 - Present • Mobile application design • Designed version 2 of SpiderOak's iOS application for the iPhone & iPad (in development) • Designed version 2 of SpiderOak’s Android application (in development queue) • Website design • Designed the admin management console web app interface to control user’s file sharing portals (Share- Rooms) for SpiderOak’s enterprise product. -

Flare-‐On 4: Challenge 10 Solution – Shell.Php
Flare-On 4: Challenge 10 Solution – shell.php Challenge Author: Dominik Weber (@Invalid_handle) Summary Modelled after a real-world web shell, this crypto level is a PHP page containing an encrypted HTML stage2 with 3 encrypted JavaScripts. The HTTP POST variable flag is the key. This level is intended to be a two-stage password attack. The first stage gets the MD5 of the password and decrypt stage2, then the second stage derives the flag with a known-plaintext attack. Description: Figure 1 depicts the essential contents of shell.php <?php $o__o_ = base64_decode('<Base64 block omitted>'); $o_o = isset($_POST['o_o']) ? $_POST['o_o'] : ""; $o_o = md5($o_o) . substr(MD5(strrev($o_o)), 0, strlen($o_o)); for ($o___o = 0; $o___o < 2268; $o___o++) { $o__o_[$o___o] = chr((ord($o__o_[$o___o]) ^ ord($o_o[$o___o])) % 256); $o_o .= $o__o_[$o___o]; } if (MD5($o__o_) == '43a141570e0c926e0e3673216a4dd73d') { if (isset($_POST['o_o'])) @setcookie('o_o', $_POST['o_o']); $o___o = create_function('', $o__o_); unset($o_o, $o__o_); $o___o(); } else { echo '<form method="post" action="shell.php"><input type="text" name="o_o" value=" "/><input type="submit" value=">"/></form>'; } ?> Figure 1: Contents of shell.php The HTTP post variable, o_o is the flag for the level. This string is then hashed with MD5 and the textual hash is the first 16 bytes of a decryption XOR key. The remainder of the key bytes is the MD5 of the reverse string array, truncated to password length size. The resulting XOR key is password length dependent and consists of characters 0-9 and a-f. This key decrypts the Base64 blob into a PHP function that gets executed. Looking at the code, we can see that the resulting plain text of this FireEye, Inc., 1440 McCarthy Blvd., Milpitas, CA 95035 | +1 408.321.6300 | +1 877.FIREEYE (347.3393) | [email protected] | www.FireEye.com 1 function has 2268 bytes. -

Pocket-Size Camera with HD Video. at Only 0.7 Inch Thick, This Compact Camera Packs a Punch with 12.1 Megapixels and HD Movie Capabilities
Shop Online | Find a Store | 1-800-MY-APPLE See all Mac computers Organize photos using Faces Pocket-size camera with HD video. At only 0.7 inch thick, this compact camera packs a punch with 12.1 megapixels and HD movie capabilities. And those aren't the only smart features. It also has face detection and blink detection technology. Canon PowerShot SD780 IS Organize photos using Places Buy now Shop all digital cameras Map your memories with automatic geotagging. This SD memory card adds geographic location data to each photo. It's perfect for use with iPhoto '09, which lets you organize photos by places. The card also wirelessly transfers photos and videos to your computer and the web. Eye-Fi Explore 4GB Wireless Memory Card Buy now Shop all storage media Create and share a slideshow You can take video tutorials Explore photos using Faces and everywhere you go. Download and sync them to Places. your iPhone and iPod from The newest version of iPhoto, iTunes for free. part of the iLife '09 suite, Browse now introduces amazing new features like Faces, which lets you organize photos by the people in them, and Places, which lets you browse photos by location. iLife '09 Upgrade now Reduce the infamous red-eye effect by taking a photo without flash. Try shooting with the flash on and then with it off and see which photo you like best. You can always get the red out later with the Red-Eye tool in iPhoto. Watch the tutorial Simply choose an Enhance and organize Apple-designed template in photos like a pro. -

Mediastorm's Compression Workflow: from Output to Web-Ready H.264
MediaStorm’s Compression Workflow: From Output to web-ready H.264 by Eric Maierson Created February 28, 2012 Updated March 6, 2013 Version 1.1 Rationale This document details MediaStorm’s best practices for encoding a single H.264 file for playback on the web, iPad, and iPhone (4 and above). Note that H.264 files created with Compressor will not work on Kindle Fire HD or Android devices. We will use Apple’s Compressor to encode with the following settings: Video Codec: H.264 (mp4) Dimensions: 1280 x 720 pixels Data Rate: 1800 - 2400 kbits/sec Encoding: Multi-pass Note that your video Data Rate will vary, as detailed later, depending on how much motion your project contains. Audio Format: AAC Channels: Stereo Rate: 48.00 KHz Bit Rate: 160 kbps http://mediastorm.com Encoding with Apple’s Compressor To begin, open Compressor. Note that Compressor used to be packaged with the Final Cut Studio. With the release of FCP X, Compressor is now sold as a separate application for $49.99 from the App Store. In Compressor's Settings window (command-3), click the plus button on the right side. Choose QuickTime movie. A new custom setting will appear in your window named Untitled QuickTime Movie. http://mediastorm.com INSPECTOR Double click it to open the settings in the Inspector window. In the Name field, rename the setting. In determining your naming convention, you should make sure to include the descriptors H.264 as well as AAC audio and the 1800kbits data rate. Also include the file dimensions. -

Quicktime File Format Specification Contents
QuickTime File Format Specification Contents Introduction to QuickTime File Format Specification 17 Organization of This Document 17 Licensing Information 18 Special Fonts 18 Updates to This Specification 18 For More Information 19 Overview of QTFF 20 Media Description 20 Atoms 20 Atom Layout 22 Atom Structure 22 QT Atoms and Atom Containers 24 QT Atom Containers 27 QuickTime Movie Files 30 The File Type Compatibility Atom 33 Free Space Atoms 35 Movie Data Atoms 35 Preview Atoms 35 Movie Atoms 37 Overview of Movie Atoms 38 The Movie Atom 40 The Movie Profile Atom 42 Movie Header Atoms 43 Color Table Atoms 46 User Data Atoms 47 Track Atoms 54 Track Profile Atom 57 Track Header Atoms 57 Track Exclude From Autoselection Atoms 61 Track Aperture Mode Dimension Atoms 61 Clipping Atoms 66 Clipping Region Atoms 67 2012-08-14 | © 2004, 2012 Apple Inc. All Rights Reserved. 2 Contents Track Matte Atoms 68 Compressed Matte Atoms 69 Edit Atoms 69 Edit List Atoms 70 Track Load Settings Atoms 71 Track Reference Atoms 73 Track Input Map Atoms 76 Media Atoms 79 Media Header Atoms 80 Extended Language Tag Atom 82 Handler Reference Atoms 84 Media Information Atoms 85 Video Media Information Atoms 86 Video Media Information Header Atoms 87 Sound Media Information Atoms 88 Sound Media Information Header Atoms 89 Base Media Information Atoms 89 Base Media Information Header Atoms 90 Base Media Info Atoms 91 Data Information Atoms 92 Data Reference Atoms 94 Sample Atoms 95 Sample Table Atoms 96 Sample Description Atoms 99 Time-to-Sample Atoms 101 Composition Offset Atom 103 Composition Shift Least Greatest Atom 105 Using Composition Offset and Composition Shift Least Greatest Atoms 106 Sync Sample Atoms 107 Partial Sync Sample Atom 108 Sample-to-Chunk Atoms 109 Sample Size Atoms 111 Chunk Offset Atoms 113 Sample Dependency Flags Atom 115 Using Sample Atoms 116 Compressed Movie Resources 117 Allowing QuickTime to Compress the Movie Resource 118 Structure of a Compressed Movie Resource 118 Reference Movies 119 2012-08-14 | © 2004, 2012 Apple Inc. -

Instruction Manual Instruction Manuals (PDF Files) and Software Can Be Downloaded from the Canon Web Site (P.4, 311)
Instruction Manual Instruction manuals (PDF files) and software can be downloaded from the Canon Web site (p.4, 311). www.canon.com/icpd E Introduction The EOS REBEL T100 or EOS 3000D is a digital single-lens reflex camera featuring a fine-detail CMOS sensor with approx. 18.0 effective megapixels, DIGIC 4+, high-precision and high-speed 9-point AF, approx. 3.0 shots/sec. continuous shooting, Live View shooting, Full High-Definition (Full HD) movie shooting, and Wi-Fi (wireless communication) function. Before Starting to Shoot, Be Sure to Read the Following To avoid botched pictures and accidents, first read the “Safety Instructions” (p.20-22) and “Handling Precautions” (p.23-25). Also, read this manual carefully to ensure that you use the camera correctly. Refer to This Manual while Using the Camera to Further Familiarize Yourself with the Camera While reading this manual, take a few test shots and see how they come out. You can then better understand the camera. Be sure to store this manual safely, too, so that you can refer to it again when necessary. Testing the Camera Before Use and Liability After shooting, play images back and check whether they have been properly recorded. If the camera or memory card is faulty and the images cannot be recorded or downloaded to a computer, Canon cannot be held liable for any loss or inconvenience caused. Copyrights Copyright laws in your country may prohibit the use of your recorded images or copyrighted music and images with music in the memory card for anything other than private enjoyment.