Promiscuous Cookies
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Product ID Product Type Product Description Notes Price (USD) Weight (KG) SKU 10534 Mobile-Phone Apple Iphone 4S 8GB White 226.8
Rm A1,10/F, Shun Luen Factory Building, 86 Tokwawan Road, Hong Kong TEL: +852 2325 1867 FAX: +852 23251689 Website: http://www.ac-electronic.com/ For products not in our pricelist, please contact our sales. 29/8/2015 Product Price Weight Product Type Product Description Notes SKU ID (USD) (KG) 10534 mobile-phone Apple iPhone 4S 8GB White 226.8 0.5 40599 10491 mobile-phone Apple iPhone 5s 16GB Black Slate 486.4 0.5 40557 10497 mobile-phone Apple iPhone 5s 16GB Gold 495.6 0.5 40563 10494 mobile-phone Apple iPhone 5s 16GB White Silver 487.7 0.5 40560 10498 mobile-phone Apple iPhone 5s 32GB Gold 536.3 0.5 40564 11941 mobile-phone Apple iPhone 6 128GB Gold 784.1 0.5 41970 11939 mobile-phone Apple iPhone 6 16GB Gold 622.8 0.5 41968 11936 mobile-phone Apple iPhone 6 16GB Silver 633.3 0.5 41965 11942 mobile-phone Apple iPhone 6 16GB Space Grey 618.9 0.5 41971 11940 mobile-phone Apple iPhone 6 64GB Gold 705.4 0.5 41969 11937 mobile-phone Apple iPhone 6 64GB Silver 706.7 0.5 41966 11943 mobile-phone Apple iPhone 6 64GB Space Grey 708 0.5 41972 11963 mobile-phone Apple iPhone 6 Plus 128GB Silver 917.9 1 41991 11955 mobile-phone Apple iPhone 6 Plus 16GB Gold 755.3 1 41983 11961 mobile-phone Apple iPhone 6 Plus 16GB Silver 731.6 1 41989 11958 mobile-phone Apple iPhone 6 Plus 16GB Space Grey 735.6 1 41986 11956 mobile-phone Apple iPhone 6 Plus 64GB Gold 843.1 1 41984 11962 mobile-phone Apple iPhone 6 Plus 64GB Silver 841.8 1 41990 11959 mobile-phone Apple iPhone 6 Plus 64GB Space Grey 840.5 1 41987 12733 mobile-phone ASUS ZenFone 2 ZE550ML Dual SIM -
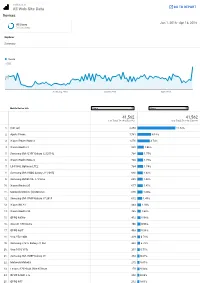
Web Site Data 41562 41562
auditguru.in All Web Site Data GO TO REPORT Devices Jan 1, 2018 - Apr 16, 2018 All Users 78.52% Users Explorer Summary Users 1,500 750 February 2018 March 2018 April 2018 Mobile Device Info Users Users 41,562 41,562 % of Total: 78.14% (53,186) % of Total: 78.14% (53,186) 1. (not set) 4,853 11.52% 2. Apple iPhone 1,761 4.18% 3. Xiaomi Redmi Note 4 1,576 3.74% 4. Xiaomi Redmi 4 825 1.96% 5. Samsung SM-J210F Galaxy J2 (2016) 736 1.75% 6. Xiaomi Redmi Note 3 736 1.75% 7. LG F160L Optimus LTE2 734 1.74% 8. Samsung SM-J200G Galaxy J2 (2015) 686 1.63% 9. Samsung SM-G610F J7 Prime 685 1.63% 10. Xiaomi Redmi 3S 677 1.61% 11. Motorola Moto G (4) Moto G4 676 1.60% 12. Samsung SM-J700F Galaxy J7 2015 612 1.45% 13. Xiaomi Mi A1 463 1.10% 14. Xiaomi Redmi 4A 435 1.03% 15. OPPO A37fw 412 0.98% 16. Acer A1-850 Iconia 406 0.96% 17. OPPO A37f 403 0.96% 18. Vivo Y53 1606 329 0.78% 19. Samsung J701F Galaxy J7 Nxt 328 0.78% 20. Vivo 1610 Y55s 315 0.75% 21. Samsung SM-J500F Galaxy J5 283 0.67% 22. Motorola MotoG3 272 0.65% 23. Lenovo A7020a48 Vibe K5 Note 270 0.64% 24. OPPO A1601 F1s 266 0.63% 25. OPPO A57 252 0.60% 26. Lenovo A6000 247 0.59% 27. Lenovo K33a42 Vibe K6 Power 245 0.58% 28. -

Factory Model Device Model
Factory Model Device Model Acer A1-713 acer_aprilia Acer A1-811 mango Acer A1-830 ducati Acer A3-A10 G1EA3 Acer A3-A10 mtk6589_e_lca Acer A3-A10 zara Acer A3-A20 acer_harley Acer A3-A20FHD acer_harleyfhd Acer Acer E320-orange C6 Acer Aspire A3 V7 Acer AT390 T2 Acer B1-723 oban Acer B1-730 EverFancy D40 Acer B1-730 vespatn Acer CloudMobile S500 a9 Acer DA220HQL lenovo72_we_jb3 Acer DA222HQL N451 Acer DA222HQLA A66 Acer DA222HQLA Flare S3 Power Acer DA226HQ tianyu72_w_hz_kk Acer E330 C7 Acer E330 GT-N7105T Acer E330 STUDIO XL Acer E350 C8n Acer E350 wiko Acer G100W maya Acer G1-715 A510s Acer G1-715 e1808_v75_hjy1_5640_maxwest Acer Icona One 7 vespa Acer Iconia One 7 AT1G* Acer Iconia One 7 G1-725 Acer Iconia One 7 m72_emmc_s6_pcb22_1024_8g1g_fuyin Acer Iconia One 7 vespa2 Acer Iconia One 8 vespa8 Acer Iconia Tab 7 acer_apriliahd Acer Iconia Tab 8 ducati2fhd Acer Iconia Tab 8 ducati2hd Acer Iconia Tab 8 ducati2hd3g Acer Iconia Tab 8 Modelo II - Professor Acer Iconia Tab A100 (VanGogh) vangogh Acer Iconia Tab A200 s7503 Acer Iconia Tab A200 SM-N9006 Acer Iconia Tab A501 ELUGA_Mark Acer Iconia Tab A501 picasso Acer Iconia Tab A510 myPhone Acer Iconia Tab A510 picasso_m Acer Iconia Tab A510 ZUUM_M50 Acer Iconia Tab A701 picasso_mf Acer Iconia Tab A701 Revo_HD2 Acer Iconia TalkTab 7 acer_a1_724 Acer Iconia TalkTab 7 AG CHROME ULTRA Acer Liquid a1 Acer Liquid C1 I1 Acer Liquid C1 l3365 Acer Liquid E1 C10 Acer Liquid E2 C11 Acer Liquid E3 acer_e3 Acer Liquid E3 acer_e3n Acer Liquid E3 LS900 Acer Liquid E3 Quasar Acer Liquid E600 e600 Acer Liquid -
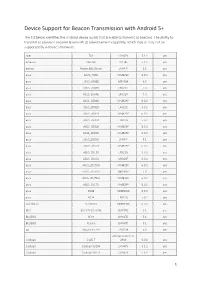
Device Support for Beacon Transmission with Android 5+
Device Support for Beacon Transmission with Android 5+ The list below identifies the Android device builds that are able to transmit as beacons. The ability to transmit as a beacon requires Bluetooth LE advertisement capability, which may or may not be supported by a device’s firmware. Acer T01 LMY47V 5.1.1 yes Amazon KFFOWI LVY48F 5.1.1 yes archos Archos 80d Xenon LMY47I 5.1 yes asus ASUS_T00N MMB29P 6.0.1 yes asus ASUS_X008D MRA58K 6.0 yes asus ASUS_Z008D LRX21V 5.0 yes asus ASUS_Z00AD LRX21V 5.0 yes asus ASUS_Z00AD MMB29P 6.0.1 yes asus ASUS_Z00ED LRX22G 5.0.2 yes asus ASUS_Z00ED MMB29P 6.0.1 yes asus ASUS_Z00LD LRX22G 5.0.2 yes asus ASUS_Z00LD MMB29P 6.0.1 yes asus ASUS_Z00UD MMB29P 6.0.1 yes asus ASUS_Z00VD LMY47I 5.1 yes asus ASUS_Z010D MMB29P 6.0.1 yes asus ASUS_Z011D LRX22G 5.0.2 yes asus ASUS_Z016D MXB48T 6.0.1 yes asus ASUS_Z017DA MMB29P 6.0.1 yes asus ASUS_Z017DA NRD90M 7.0 yes asus ASUS_Z017DB MMB29P 6.0.1 yes asus ASUS_Z017D MMB29P 6.0.1 yes asus P008 MMB29M 6.0.1 yes asus P024 LRX22G 5.0.2 yes blackberry STV100-3 MMB29M 6.0.1 yes BLU BLU STUDIO ONE LMY47D 5.1 yes BLUBOO XFire LMY47D 5.1 yes BLUBOO Xtouch LMY47D 5.1 yes bq Aquaris E5 HD LRX21M 5.0 yes ZBXCNCU5801712 Coolpad C106-7 291S 6.0.1 yes Coolpad Coolpad 3320A LMY47V 5.1.1 yes Coolpad Coolpad 3622A LMY47V 5.1.1 yes 1 CQ CQ-BOX 2.1.0-d158f31 5.1.1 yes CQ CQ-BOX 2.1.0-f9c6a47 5.1.1 yes DANY TECHNOLOGIES HK LTD Genius Talk T460 LMY47I 5.1 yes DOOGEE F5 LMY47D 5.1 yes DOOGEE X5 LMY47I 5.1 yes DOOGEE X5max MRA58K 6.0 yes elephone Elephone P7000 LRX21M 5.0 yes Elephone P8000 -
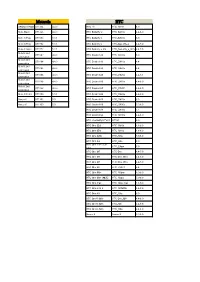
Motorola HTC DROIDTURBO XT1254 4.4.3 HTC 10 HTC M10h 6.0
Motorola HTC DROIDTURBO XT1254 4.4.3 HTC 10 HTC_M10h 6.0 Moto Maxx XT1225 4.4.3 HTC Butterfly 2 HTC_B810x 4.4-6.0 Moto X Play XT1563 5.1.1 HTC Butterfly 3 HTC_B830x 6.0 Moto X Play XT1562 5.1.1 HTC Butterfly s HTC_Butterfly_s 4.4-5.0 Moto X Style XT1572 5.1.1 HTC Butterfly s 4G HTC_Butterfly_s_901s 4.4-5.0 MotoX 2nd XT1097 4.4.3 HTC Desire 530 HTC_D530x 6.0 generation MotoX 2nd XT1094 4.4.3 HTC Desire 610 HTC_D610x 4.4 generation MotoX 2nd XT1093 4.4.3 HTC Desire 620 HTC_D620x 4.4 generation MotoX 2nd XT1095 4.4.3 HTC Desire 626 HTC_D626x 4.4-5.1 generation MotoX 2nd XT1096 4.4.3 HTC Desire 816 HTC_D816x 4.4-6.0 generation MotoX 2nd XT1092 4.4.3 HTC Desire 820 HTC_D820f 4.4-6.0 generation Moto X Force XT1580 5.1.1 HTC Desire 820 HTC_D820u 4.4-6.0 Nexus 6 XT1103 5.0 HTC Desire 825 HTC_D825x 6.0 Nexus 6 XT1100 5.0 HTC Desire 826 HTC_D826x 5.0-6.0 HTC Desire 830 HTC_D830x 5.1 HTC Desire Eye HTC_M910x 4.4-6.0 HTC J butterfly HTV31 HTV31 6.0 HTC One (E8) HTC_M8Sx 4.4-6.0 HTC One (E8) HTC_M8Sy 4.4-6.0 HTC One (M9) HTC_M9u 5.0-6.0 HTC One A9 HTC_A9u 6.0 HTC One E9+ Dual HTC_E9pw 5.0 SIM HTC One M7 HTC One 4.4-5.0 HTC One M7 HTC One 801e 4.4-5.0 HTC One M7 HTC One 801s 4.4-5.0 HTC One M7 HTC_PN071 4.4 HTC One M9+ HTC_M9pw 5.0-6.0 HTC One M9+ (極光) HTC_M9px 5.0-6.0 HTC One max HTC_One_max 4.4-5.0 HTC One mini 2 HTC_M8MINx 4.4-6.0 HTC One X9 HTC_X9u 6.0 HTC One® (M8) HTC One_M8 4.4-6.0 HTC One® (M8) HTC_M8 4.4-6.0 HTC One® (M8) HTC_M8x 4.4-6.0 Nexus 9 Nexus 9 5.0-6.0 HUAWEI LG HUAWEI GRA- P8 6.0 AKA LG-H788n 4.4 L09 P8 Lite HUAWEI ALE-L21 5.0 F90 -

HTC Desire 626 2 Inhalte Inhalte
Handbuch HTC Desire 626 2 Inhalte Inhalte Features, an denen Sie Spaß haben werden Personalisierung 9 Bildaufnahme 10 Ton 11 Auspacken HTC Desire 626 12 nano SIM-Karte 13 Speicherkarte 14 Laden des Akkus 16 Ein- und Ausschalten 16 Benötigen Sie eine Kurzanleitung zur Verwendung Ihres Telefons? 17 Telefoneinrichtung und Übertragung Erstmalige Einrichtung des HTC Desire 626 18 Wiederherstellung Ihrer Sicherung von Ihrem Cloudspeicher 19 Inhalte von einem Android Telefon übertragen 20 Möglichkeiten zur Übertragung von Inhalten von einem iPhone 21 Übertragung von iPhone Inhalten via iCloud 21 Andere Möglichkeiten, um Kontakte und andere Inhalte abzurufen 22 Fotos, Videos und Musik zwischen dem Telefon und einem Computer übertragen 22 Verwendung von Kurzeinstellungen 23 Kennenlernen der Einstellungen 24 Telefon-Software aktualisieren 24 Apps von Google Play abrufen 27 Apps aus dem Web herunterladen 28 Deinstallieren einer App 28 Die erste Woche mit dem neuen Telefon Grundlagen 29 HTC Sense Startseite Widget 39 Displaysperre 42 Benachrichtigungen 45 Arbeiten mit Text 47 HTC Hilfe 51 Persönliche Einrichtung Themes 52 Mehr Möglichkeiten zur Personalisierung 55 HTC BlinkFeed Was ist HTC BlinkFeed? 63 3 Inhalte HTC BlinkFeed aktivieren oder deaktivieren 64 Restaurantempfehlungen 64 Möglichkeiten zum Hinzufügen von Inhalten zu HTC BlinkFeed 65 Den Höhepunkte Feed anpassen 66 Artikel für später speichern 67 In Ihren sozialen Netzwerken posten 67 Inhalte aus HTC BlinkFeed entfernen 67 Kamera Kamera-Grundlagen 68 Selfies und Personenaufnahmen 72 Panoramaaufnahmen -

HTC Desire 626 User Guide
User Guide ® hTC Desire 626 @ 2 Contents Contents Features you'll enjoy Android 6.0 Marshmallow 14 Sound 16 Personalization 16 Software and app updates 18 Unboxing HTC Desire 626 19 nano SIM card 20 Inserting a nano SIM card 21 Removing a nano SIM card 23 Storage card 24 Charging the battery 26 Switching the power on or off 27 Want some quick guidance on your phone? 28 Phone setup and transfer Setting up HTC Desire 626 for the first time 29 Restoring from your previous HTC phone 30 Transferring content from an Android phone 31 Contents 3 Ways of transferring content from an iPhone 32 Transferring iPhone content through iCloud 32 Other ways of getting contacts and other content 33 Transferring photos, videos, and music between your phone and computer 34 Using Quick Settings 35 Getting to know your settings 36 Updating your phone's software 37 Getting apps from Google Play 40 Downloading apps from the web 42 Uninstalling an app 43 Your first week with your new phone Basics 44 HTC Sense Home widget 58 Lock screen 62 Notifications 66 Working with text 68 HTC Help 75 Personalizing Themes 76 More ways to personalize 81 4 Contents HTC BlinkFeed What is HTC BlinkFeed? 93 Turning HTC BlinkFeed on or off 94 Restaurant recommendations 95 Ways of adding content on HTC BlinkFeed 96 Customizing the Highlights feed 99 Posting to your social networks 99 Removing content from HTC BlinkFeed 100 Camera Camera basics 101 Selfies and people shots 108 Panoramic shots 111 Other camera features 112 Camera settings 113 Gallery Viewing photos and videos in Gallery -

Terraillon Wellness Coach Supported Devices
Terraillon Wellness Coach Supported Devices Warning This document lists the smartphones compatible with the download of the Wellness Coach app from the App Store (Apple) and Play Store (Android). Some models have been tested by Terraillon to check the compatibility and smooth operation of the Wellness Coach app. However, many models have not been tested. Therefore, Terraillon doesn't ensure the proper functioning of the Wellness Coach application on these models. If your smartphone model does not appear in the list, thank you to send an email to [email protected] giving us the model of your smartphone so that we can activate if the application store allows it. BRAND MODEL NAME MANUFACTURER MODEL NAME OS REQUIRED ACER Liquid Z530 acer_T02 Android 4.3+ ACER Liquid Jade S acer_S56 Android 4.3+ ACER Liquid E700 acer_e39 Android 4.3+ ACER Liquid Z630 acer_t03 Android 4.3+ ACER Liquid Z320 T012 Android 4.3+ ARCHOS 45 Helium 4G a45he Android 4.3+ ARCHOS 50 Helium 4G a50he Android 4.3+ ARCHOS Archos 45b Helium ac45bhe Android 4.3+ ARCHOS ARCHOS 50c Helium ac50che Android 4.3+ APPLE iPhone 4S iOS8+ APPLE iPhone 5 iOS8+ APPLE iPhone 5C iOS8+ APPLE iPhone 5S iOS8+ APPLE iPhone 6 iOS8+ APPLE iPhone 6 Plus iOS8+ APPLE iPhone 6S iOS8+ APPLE iPhone 6S Plus iOS8+ APPLE iPad Mini 1 iOS8+ APPLE iPad Mini 2 iOS8+ 1 / 48 www.terraillon.com Terraillon Wellness Coach Supported Devices BRAND MODEL NAME MANUFACTURER MODEL NAME OS REQUIRED APPLE iPad Mini 3 iOS8+ APPLE iPad Mini 4 iOS8+ APPLE iPad 3 iOS8+ APPLE iPad 4 iOS8+ APPLE iPad Air iOS8+ -

Electronic 3D Models Catalogue (On July 26, 2019)
Electronic 3D models Catalogue (on July 26, 2019) Acer 001 Acer Iconia Tab A510 002 Acer Liquid Z5 003 Acer Liquid S2 Red 004 Acer Liquid S2 Black 005 Acer Iconia Tab A3 White 006 Acer Iconia Tab A1-810 White 007 Acer Iconia W4 008 Acer Liquid E3 Black 009 Acer Liquid E3 Silver 010 Acer Iconia B1-720 Iron Gray 011 Acer Iconia B1-720 Red 012 Acer Iconia B1-720 White 013 Acer Liquid Z3 Rock Black 014 Acer Liquid Z3 Classic White 015 Acer Iconia One 7 B1-730 Black 016 Acer Iconia One 7 B1-730 Red 017 Acer Iconia One 7 B1-730 Yellow 018 Acer Iconia One 7 B1-730 Green 019 Acer Iconia One 7 B1-730 Pink 020 Acer Iconia One 7 B1-730 Orange 021 Acer Iconia One 7 B1-730 Purple 022 Acer Iconia One 7 B1-730 White 023 Acer Iconia One 7 B1-730 Blue 024 Acer Iconia One 7 B1-730 Cyan 025 Acer Aspire Switch 10 026 Acer Iconia Tab A1-810 Red 027 Acer Iconia Tab A1-810 Black 028 Acer Iconia A1-830 White 029 Acer Liquid Z4 White 030 Acer Liquid Z4 Black 031 Acer Liquid Z200 Essential White 032 Acer Liquid Z200 Titanium Black 033 Acer Liquid Z200 Fragrant Pink 034 Acer Liquid Z200 Sky Blue 035 Acer Liquid Z200 Sunshine Yellow 036 Acer Liquid Jade Black 037 Acer Liquid Jade Green 038 Acer Liquid Jade White 039 Acer Liquid Z500 Sandy Silver 040 Acer Liquid Z500 Aquamarine Green 041 Acer Liquid Z500 Titanium Black 042 Acer Iconia Tab 7 (A1-713) 043 Acer Iconia Tab 7 (A1-713HD) 044 Acer Liquid E700 Burgundy Red 045 Acer Liquid E700 Titan Black 046 Acer Iconia Tab 8 047 Acer Liquid X1 Graphite Black 048 Acer Liquid X1 Wine Red 049 Acer Iconia Tab 8 W 050 Acer -

Htc Desireusb Drivers Download HTC DESIRE 610 ADB 64-BITS DRIVER
htc desireusb drivers download HTC DESIRE 610 ADB 64-BITS DRIVER. Install ADB mini with Fastboot tools to get all needed tools and rest of adb drivers that are required. Download the latest and original HTC USB Drivers to connect any HTC Smartphone and Tablets to the Windows Computer quickly. In this article, you will find out the HTC USB Drivers? Mode, Another great thing about it using the computer? To Fix Unrooted HTC Desire 610. We recommend you boot the HTC Desire 610 device up in that custom recovery before you start using your device normally, so you do not wipe the custom recovery. One is for Flashing the Stock Firmware and another is for normal connecting the device to the computer. How to Root And Install Official TWRP Recovery For HTC. On this page, we have managed to share the official usb driver for HTC Desire 610 Device. We have shared 2 USB drivers for your HTC Android device on this page. Before performing any of these steps make sure you back up your Android device completely. Don t worry about it, we are here to give you the latest officially released drivers for your HTC Desire 610 smartphone or tablet and check for the USB driver for your device? Run the following commands via adb shell or a terminal emulator app, su. However, due to some of our carrier customers concerns, certain models with specific restrictions may not be able to be unlocked. Install HTC drivers to get communication with HTC Desire 610. HTC Desire 610 USB Drivers, front camera 1. -

Welcome to Twit.Tv! If You've Stumbled Upon This Page and Are Wondering What It's All About, Read On
Huh? Welcome to TWiT.tv! If you've stumbled upon this page and are wondering what it's all about, read on. The TWiT.tv Story It all started in 1998 with a small cable network called ZDTV, a channel dedicated to covering computers, the Internet, and personal technology. The people behind this site all worked on that network as hosts, reporters, or producers. In 2004, ZDTV, then called TechTV, was sold and dismantled. Former TechTV hosts, Leo Laporte, Patrick Norton, Kevin Rose, and John C. Dvorak, and producers Robert Heron, David Prager, and Roger Chang went on to other jobs, but we stayed in touch, with each other, and with fans of the late TechTV. Those fans told us again and again how important TechTV had been in their lives, and how much they missed the channel. We missed working with each other, too. On a rainy evening in January, 2005 a few of of us got together for dinner after spending the day covering MacWorld Expo in San Francisco. Leo, who was working as a radio host, happened to have a microphone and recorder. He turned it on and recorded 20 minutes of idle chatter about the Expo and the tech world in general. He posted that recording on his web site. Within a few days tens of thousands of people had downloaded the recording. TechTV fans began clamoring for more. A few months later,TWiT was born. We originally called the show The Revenge of The Screen Savers because that was the name of the defunct TV show many of us had worked on, but the cable channel that had bought TechTV complained, so we changed the name to this WEEK in TECH, or TWiT, for short. -

Podcast Industry Audience Rankings July 2016
PODCAST INDUSTRY AUDIENCE RANKINGS JULY 2016 2 INTRODUCTION With the growing popularity of podcasts, more and more brands and agencies are exploring the medium in search of opportunities that make the most sense for their brands. And publishers are making important content decisions about ways to expand or better serve their audiences across multiple shows. What is the most accurate measure of podcast audience size? An obvious place for advertisers to begin exploring podcast advertising is with understanding the relative audience sizes of podcast publishers and of podcasts individually. Podtrac has provided the leading measurement service for podcasts since 2005. In 2016, Podtrac introduced “Monthly Unique Audience” for the podcast industry. It's the same metric used for planning other types of digital media, and for the first time it's available for podcasts from Podtrac. Monthly Unique Audience from Podtrac is available: ● By podcast publisher across all of the podcast shows and episodes they produce ● By show for all of the podcast episodes they produce ● By global and U.S. audience counts “Monthly Unique Audience” is an important metric in digital media because it enables advertisers and publishers to consider monthly audience reach in addition to potential impressions served. And as with other media, the monthly unique audience metrics from Podtrac are consistent across publishers and shows whether the episodes post daily, twice a week, weekly, etc. Which podcasts are audiences listening to most? Podtrac produces a monthly Ranking Report showing the top publishers in the industry by US audience. Podtrac is in a unique position to produce this report, because of its podcast measurement technology and its 10+ years of measurement relationships with substantially all of the top publishers in the industry.