On Line Trace Synchronization for Large Scale Distributed Systems
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

'DIY' Digital Preservation for Audio Identify · Appraise · Organise · Preserve · Access Plan + Housekeeping
'DIY' Digital Preservation for Audio Identify · Appraise · Organise · Preserve · Access Plan + housekeeping Part 1 (10:00am-10:50am) Part 2 (11:00am-11:45am) 10:00am-10:10am Intros and housekeeping 10:50am-11:00am [10-minute comfort break] 10:10am-10:30am Digital Preservation for audio 11:00am-11:15am Organise (Migrate) What material do you care 11:15am-11:45am Store, Maintain, Access about and hope to keep?_ Discussion & Questions 10:30am-10:50am Locate, Appraise, Identify What kind of files are you working with?_ Feel free to Using Zoom swap to ‘Grid View’ when slides are not in use, to gage ‘the room’. Please use the chat Please keep function to your mic on ask questions ‘mute’ when while slides not speaking. are in use. Who are we? • Bridging the Digital Gap traineeship scheme • UK National Archives (National Lottery Heritage Fund) • bringing ‘digital’ skills into the archives sector Why are we doing these workshops? • agitate the cultural record to reflect lived experience • embrace tools that support historical self-determination among non- specialists • raise awareness, share skills, share knowledge What is digital preservation? • digital material is vulnerable in different ways to analog material • digital preservation = “a series of managed activities undertaken to ensure continued access to digital materials for as long as necessary.” Audio practices and technological dependency Image credit: Tarje Sælen Lavik Image credit: Don Shall Image credit: Mk2010 Image credit: Stahlkocher Image credit: JuneAugust Digital preservation and ‘born-digital’ audio Bitstream File(s) Digital Content Rendered Content • codecs (e.g. LPCM) • formats and containers (e.g. -

Amateur Computer Group of New Jersey NEWS Volume 39, Number 01 January 2014
Amateur Computer Group of New Jersey NEWS Volume 39, Number 01 January 2014 Main Meeting/Election Report ACGNJ Meetings Brenda Bell, ACGNJ For the very latest news on ACGNJ meetings, please On December 6, 2013, we held our Annual Business visit the ACGNJ Website (www.acgnj.org). Meeting, with 8 persons attending. Having reached a Board of Directors Meeting: December 31, 7:00 PM quorum, the meeting was called to order at 9:09 PM. MOVED to Friday, January 3, 7:00 PM. Mike Redlich presented a President's Report. (Due to the New Year's Holiday) Malthi Masurekar presented a Treasurer's Report. Board of Directors Meeting: Friday, Jan 3, 7:00 PM Several topics were raised for discussion, including Mike Redlich (president (at) acgnj.org) membership issues and outreach to other clubs. Main Meeting: Friday, January 3. 8:00 PM Election results. Without discussion, and with no Mike Redlich (president (at) acgnj.org) additional candidates being nominated for our two Lunics (Linux/UNIX): Monday, January 6, 8:00 PM still open Director positions, John Raff moved that Andreas Meyer (lunics (at) acgnj.org) the Secretary cast one vote for the pat slate. The Investing: Thursday, January 9, 8:00 PM motion was seconded and carried. Jim Cooper (jim (at) thecoopers.org). President: Michael Redlich NJ Gamers: Friday, January 10, 6:00 PM Vice-President: Wendy Bell Gregg McCarthy (greggmajestic (at) gmail.com) Secretary: Brenda Bell Treasurer: Malthi Masurekar Layman’s Forum: Monday, January 13, 8:00 PM Directors (Two year term, through end of 2015): Matt Skoda (som359 (at) gmail.com) Gregg McCarthy Java: Tuesday, January 14, 7:30 PM John Raff Mike Redlich (mike (at) redlich.net) Frank Warren Window Pains: Friday, January 17, 7:00 PM Directors (From last year, through end of 2014): !!!WARNING!!! This meeting will NOT be held in Bob Hawes our usual location. -

Troubleshooting : Virtual Desktop Service
Troubleshooting Virtual Desktop Service NetApp September 23, 2021 This PDF was generated from https://docs.netapp.com/us-en/virtual-desktop- service/Troubleshooting.reviewing_vds_logs.html on September 23, 2021. Always check docs.netapp.com for the latest. Table of Contents Troubleshooting . 1 Troubleshooting Failed VDS Actions . 1 Internet Connection Quality Troubleshooting . 6 Enable Desktop Wallpaper for User Sessions . 9 Troubleshooting Printing Issues . 11 Azure vCPU Core Quota . 12 Unlocking User Accounts . 15 Troubleshooting Virtual Machine Performance . 17 DNS Forwards for Azure ADDS & SSO via O365 identity . 28 Troubleshooting Application Issues . 34 Troubleshooting Troubleshooting Failed VDS Actions Overview Much of the logging that happens in VDS is not exposed in the web UI due to the sheer volume of it. More detailed logs are found on the end point. These logs are described below. In VDS v5.4+, the logs are found in the following folder path: C:\programdata\cloudworkspace In previous version of VDS, they can reside in the following paths: C:\Program Files\CloudWorkspace\ C:\Program Files\CloudJumper\ C:\Program Files\IndependenceIT\ File type also varies by VDS version, log files are either .txt or .log files found in sub-folders of the above outlined path. Automation logs CW VM Automation Service log CwVmAutomationService.log The CW VM Automation service is a Windows Service that is responsible for the management of all Virtual Machines in the deployment. As a Windows Service it is always running in a deployment, but has two main modes of operation: Scheduled Task Mode and Event Mode. Scheduled Task Mode consists of activities that are performed on the VMs as part of a schedule, including collection sizing and performance data, rebooting VMs, checking on state (on or off) vs rule sets generated by the Workload Schedule and Live Scaling features. -

Listener Feedback Q&A
Transcript of Episode #100 Listener Feedback Q&A #21 Description: Steve and Leo discuss questions asked by listeners of their previous episodes. They tie up loose ends, explore a wide range of topics that are too small to fill their own episode, clarify any confusion from previous installments, and present real world "application notes" for any of the security technologies and issues they have previously discussed. High quality (64 kbps) mp3 audio file URL: http://media.GRC.com/sn/SN-100.mp3 Quarter size (16 kbps) mp3 audio file URL: http://media.GRC.com/sn/sn-100-lq.mp3 INTRO: Netcasts you love, from people you trust. This is TWiT. Leo Laporte: Bandwidth for Security Now! is provided by AOL Radio at AOL.com/podcasting. This is Security Now! with Steve Gibson, Episode 100 for July 12, 2007: Your questions, Steve’s answers. It’s time for Security Now!, our 100th episode. We need streamers. We need - we’re actually recording this on the 4th of July. You’d think there’d be some fireworks. But no. Nothing. Steve Gibson: No. Leo: Unlike some of the other shows, we’re just going to go along about our business. But congratulations, Steve. My deepest thanks for allowing us to carry this on the TWiT network. It is absolutely, after TWiT, the flagship podcast, it’s the one everybody talks about. Steve: Well, I’ve been really, really happy that we did it, Leo. I wouldn’t be doing it were it not for you because, you know, you make me get up.. -

Download File Management and Processing Tools
File Management and Processing Tools Published January 2018 CONTACT US Division of Library, Archives and Museum Collections | [email protected] File Management and Processing Tools Contents Introduction ................................................................................................................................................................................... 3 Bulk operations ............................................................................................................................................................................. 3 Duplicate file finding and deduplication ......................................................................................................................................... 4 Disk space analysis....................................................................................................................................................................... 4 Image viewer ................................................................................................................................................................................. 5 Integrity checking .......................................................................................................................................................................... 5 Last Updated January 2018 2 Introduction This guidance document provides a list of software tools that can assist in electronic file management and processing. This document is intended for records managers at state agencies, -

Freeware Software Tools
FIVE POWERFUL PROGRAMS FOR EVERY REAL ESTATE APPRAISER The right tools are critical to keeping an appraisal business up and running efficiently. Here are five programs that deliver significant functionality to an appraiser’s daily practice. These programs can secure and shrink files, clean your OS to keep your system running efficiently, and save you from horrible mistakes when files are accidentally deleted. They can also manage password access to your OS and programs, and provide you with a sophisticated real- time backup of all of your important programs and data. Any one of these five programs are a problem solver on a multitude of levels, and together they help to fill your tool box with the five solutions that will help keep your computer up and running efficiently every day. ZIP ARCHIVER ZIP Archiver is a powerful and modern archival program that allows users to easily compress and open files from any archive. Users can use cloud technologies to conveniently create copies of important files, quickly send reports to their clients, or share data with colleagues. Figure 1: Zip Archiver CCLEANER CCleaner may be the most popular system maintenance tool ever. Is your computer running slow? As it gets older it collects unused files and settings which take up hard drive space making it slower and slower. CCleaner cleans up these files and remedies this problem in seconds. Advertisers and websites track your behavior online with cookies that are placed on your computer. CCleaner erases your browser search history and cookies so any Internet browsing you do stays confidential and your identity remains anonymous. -

A Windows XP Diagnostic Guide Step 1
home.comcast.net 20/11/2010 12:26 Diagnose XP Diagnose XP - Step 1 - Malware A Windows XP Removal Diagnostic Guide Malware Infection which includes Viruses, Worms, Trojans, Spyware, Adware and Rootkits can cause or mimic just about any system problem. These in- clude: Application Errors, Lock-ups (freezing), The following Free guide will help you Blue Screen Stop Errors (BSOD) and Random troubleshoot the most common causes of sys- Reboots. tem problems. Diagnosing System problems can be very complicated and time consuming. There Malware Removal Guide - Malware is short are no simple solutions. Windows XP systems should for «Malicious Software». It is a general never Lock-up (freeze), display Blue Screen Stop term that refers to any software or program Errors or Randomly Reboot. These are all warning code designed to infiltrate or damage a computer signs something is wrong or misconfigured with system without the owner’s informed consent. This your system. Unless you are a highly trained, expe- includes Viruses, Worms, Trojans, Spyware, Adware rienced PC Technician do not skip any of the fol- and Rootkits. This 3 step guide will show you how lowing steps. to remove these infections and protect yourself from future infections for free using free software. Notes - Overclocking can cause almost any system problem. It is strongly recommended to only run FACT: 89% of consumer PCs are infected with your system at the correct frequencies. Troubles- spyware hooting any problem on an Overclocked system is feedback a complete waste of time. Set the system back to its ^ TOP default frequencies before you begin troubleshoo- ting. -

GDPR Assessment Evidence of Compliance
33 GDPR Assessment Evidence of Compliance Prepared for: CONFIDENTIALITY NOTE: The information contained in this report document My Client Company is for the exclusive use of the organisation specified above and may contain confidential, privileged and non-disclosable information. If the recipient of this Prepared by: report is not the organisation or addressee, such recipient is strictly prohibited from reading, photocopying, distributing or otherwise using this report or its YourIT Company contents in any way. Scan Date: 1/18/2018 1/18/2018 Evidence of Compliance GDPR ASSESSMENT Table of Contents 1 - APPLICABLE LAW 2 - DATA PROTECTION OFFICER 3 - REPRESENTATIVE OF CONTROLLER OR PROCESSORS NOT ESTABLISHED IN THE UNION 4 - PRINCIPLES RELATING TO PROCESSING OF PERSONAL DATA 5 - PERSONAL DATA 5.1 - AUTOMATED SCAN FOR PERSONAL DATA 6 - CHILD CONSENT 7 - SPECIAL CATEGORIES OF PERSONAL DATA 8 - PRIVACY POLICY REVIEW 9 - PROCESSOR OR SUB-PROCESSOR 10 - IMPLEMENTATION OF CONTROLS FROM ISO 27001 11 - INFORMATION SECURITY POLICIES 12 - ORGANISATION OF INFORMATION SECURITY 13 - USER ACCESS MANAGEMENT 13.1 - TERMINATED USERS 13.2 - INACTIVE USERS 13.3 - SECURITY GROUPS 13.4 - GENERIC ACCOUNTS 13.5 - PASSWORD MANAGEMENT 14 - PHYSICAL AND ENVIRONMENTAL SECURITY 14.1 - SCREEN LOCK SETTINGS 15 - OPERATIONS SECURITY 15.1 - APPLICATION LIST 15.2 - OUTBOUND WEB FILTERING 15.3 - ENDPOINT SECURITY 15.4 - CORPORATE BACKUP 15.5 - ENDPOINT BACKUP 15.6 - LOGGING AND MONITORING 15.7 - CLOCK SYNCHRONIZATION 15.8 - TECHNICAL VULNERABILITY MANAGEMENT 16 - COMMUNICATION SECURITY Page 2 of 80 Evidence of Compliance GDPR ASSESSMENT 16.1 - NETWORK CONTROLS 16.2 - SEGREGATION IN NETWORKS 17 - SYSTEM ACQUISITION 17.1 - EXTERNAL APPLICATION SECURITY Page 3 of 80 Evidence of Compliance GDPR ASSESSMENT 1 - APPLICABLE LAW ISO 27001 (18.1.1): Identification of applicable legislation and contractual requirements We have identified the following laws, regulations and standards as being applicable to our business. -
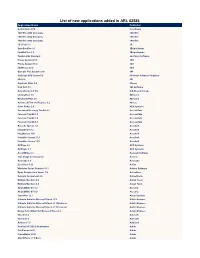
List of New Applications Added in ARL #2586
List of new applications added in ARL #2586 Application Name Publisher NetCmdlets 2016 /n software 1099 Pro 2009 Corporate 1099 Pro 1099 Pro 2020 Enterprise 1099 Pro 1099 Pro 2008 Corporate 1099 Pro 1E Client 5.1 1E SyncBackPro 9.1 2BrightSparks FindOnClick 2.5 2BrightSparks TaxAct 2002 Standard 2nd Story Software Phone System 15.5 3CX Phone System 16.0 3CX 3CXPhone 16.3 3CX Grouper Plus System 2021 3M CoDeSys OPC Server 3.1 3S-Smart Software Solutions 4D 15.0 4D Duplicate Killer 3.4 4Team Disk Drill 4.1 508 Software NotesHolder 2.3 Pro A!K Research Labs LibraryView 1.0 AB Sciex MetabolitePilot 2.0 AB Sciex Advanced Find and Replace 5.2 Abacre Color Picker 2.0 ACA Systems Password Recovery Toolkit 8.2 AccessData Forensic Toolkit 6.0 AccessData Forensic Toolkit 7.0 AccessData Forensic Toolkit 6.3 AccessData Barcode Xpress 7.0 AccuSoft ImageGear 17.2 AccuSoft ImagXpress 13.6 AccuSoft PrizmDoc Server 13.1 AccuSoft PrizmDoc Server 12.3 AccuSoft ACDSee 2.2 ACD Systems ACDSync 1.1 ACD Systems Ace Utilities 6.3 Acelogix Software True Image for Crucial 23. Acronis Acrosync 1.6 Acrosync Zen Client 5.10 Actian Windows Forms Controls 16.1 Actipro Software Opus Composition Server 7.0 ActiveDocs Network Component 4.6 ActiveXperts Multiple Monitors 8.3 Actual Tools Multiple Monitors 8.8 Actual Tools ACUCOBOL-GT 5.2 Acucorp ACUCOBOL-GT 8.0 Acucorp TransMac 12.1 Acute Systems Ultimate Suite for Microsoft Excel 13.2 Add-in Express Ultimate Suite for Microsoft Excel 21.1 Business Add-in Express Ultimate Suite for Microsoft Excel 21.1 Personal Add-in Express -

Myths and Realities: SSD Industry Trends and Perspectives and Tips
Flash back to reality – Myths and Realities SSD Industry trends perspectives and tips Presented by Greg Schulz, Founder & Sr. Advisory Analyst The Server and StorageIO Group (StorageIO) Author: Cloud and Virtual Data Storage Networking (CRC Press) [email protected] | StorageIOblog.com | Facebook.com/StorageIO | @storageio © Copyright 2014 ServerStorageIO and UnlimitedIO LLC All rights reserved. www.storageio.com 2 Introduction Who is Greg Schulz, contact and other information Has been IT Customer Has been Vendor Application systems development Storage, Network, SSD, Disk & Tape Systems programming/management Backup/BC/DR, RAID, Replication Performance and Capacity Planning NAS, SAN, LAN, MAN and WAN Data Protection/Backup/BC/DR Hardware, Software & Services Electric Power, Financial, Transportation Sales Engineering, Tech Marketing Industry Analyst/Advisor Author and Consultant Cloud, virtualization/VDI, servers, HW, SW, servers, software defined, services, archive, backup/BC/DR, Five Time performance/capacity planning Syndicated columnist & blogger Five time VMware vExpert StorageIOblog.com & StorageIO.TV StorageIO.com www.storageio.com/downloads Twitter @storageio | Facebook.com/storageio | Storageioblog.com | storageio.com/newsletter © Copyright 2014 ServerStorageIO and UnlimitedIO LLC All rights reserved. www.storageio.com 3 Industry Trends: SSD Walking the Talk My experiences with SSD, spanning a “few” decades ;) Launch customer for DEC ESE20 ram based SSD (late 80s, early 90s) AS a vendor sold various SSD solutions across various -

Access Denied: Error Message - Windows Update
Access Denied: Error Message - Windows Update Network policy settings prevent you from using Windows Update to download and install updates on your computer. If you believe you have received this message in error, please check with your system administrator. For Windows XP Pro: Start/Run/gpedit.msc. User Configuration/Administrative Templates/Windows Components/Windows Update. In the right pane, double click, Remove access to all Windows Update Features and set it to disabled. For Windows XP Home Edition: Start/Run/Regedit HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\WindowsUpda te Locate the value in the right pane called DisableWindowsUpdateAccess. Double click this entry and change the value to 0 (zero) or right click it and select Delete. If editing the Registry manually isn't to your liking click here for a small Visual Basic Script that will make the change for you. More information here: Why can't I download updates? WINUP-Err Msg: "Cannot Display Page" Accessibility Options Restore Accessibility Options to Default Settings (Line 135) http://www.kellys-korner-xp.com/xp_tweaks.htm Acdsee Acdsee.exe May Cause an Error Message Activation - Troubleshooting Blank Activate Windows Page in the WPA Wizard Service Pack 1 Changes to Product Activation Windows XP Prompts You to Re-activate After You Restore Your Computer Activation - Explained: Windows XP will typically remind you to activate the product (most users will have 30 days to activate XP after installation). To activate XP manually, you can use the Start menu shortcut in the System Tools Accessories folder. At the command prompt, type: oobe/msoobe /a or Start/All Programs/Accessories/System Tools/Activate Windows. -

Treesize Free - Introduction
Navigation: »No topics above this level« TreeSize Free - Introduction Every hard disk is too small if you just wait long enough. TreeSize Free tells you where precious space has gone to. It can be started from the context menu of a folder or drive and shows you the size of this folder, including its sub-folders. You can expand this folder in Explorer-like style and you will see the size of every sub-folder. Scanning is done in a thread, so you can already see results while TreeSize Free is working. The space, which is actually used by the file system can be displayed and the results can be printed in a report. Navigation: »No topics above this level« Installation Simply execute the installer and follow the instructions. TreeSize Free can be uninstalled through the Windows Control Panel. Supported operating systems are Windows Vista and later, including the 64Bit editions. Portable installation In addition to the normal installer, TreeSize Free is available as a ZIP file, which saves its settings locally and can e.g. be run from a portable medium such as an USB stick. Navigation: »No topics above this level« Tips & Annotations The following information is important. Provided are instructions and information which makes understanding of TreeSize and how to use it easier. The allocated space that Windows shows in the properties dialog of the drive may be larger than the allocated space reported by TreeSize Free. The Windows Explorer shows the space that is physically allocated on the drive while TreeSize Free shows the space that is occupied by all files under a certain path.