Fundamentals of UNIX®: Solaris™ and Linux™ Supplement
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Fundamentals of UNIX Lab 5.4.6 – Listing Directory Information (Estimated Time: 30 Min.)
Fundamentals of UNIX Lab 5.4.6 – Listing Directory Information (Estimated time: 30 min.) Objectives: • Learn to display directory and file information • Use the ls (list files) command with various options • Display hidden files • Display files and file types • Examine and interpret the results of a long file listing • List individual directories • List directories recursively Background: In this lab, the student will use the ls command, which is used to display the contents of a directory. This command will display a listing of all files and directories within the current directory or specified directory or directories. If no pathname is given as an argument, ls will display the contents of the current directory. The ls command will list any subdirectories and files that are in the current working directory if a pathname is specified. The ls command will also default to a wide listing and display only file and directory names. There are many options that can be used with the ls command, which makes this command one of the more flexible and useful UNIX commands. Command Format: ls [-option(s)] [pathname[s]] Tools / Preparation: a) Before starting this lab, the student should review Chapter 5, Section 4 – Listing Directory Contents b) The student will need the following: 1. A login user ID, for example user2, and a password assigned by their instructor. 2. A computer running the UNIX operating system with CDE. 3. Networked computers in classroom. Notes: 1 - 5 Fundamentals UNIX 2.0—-Lab 5.4.6 Copyright 2002, Cisco Systems, Inc. Use the diagram of the sample Class File system directory tree to assist with this lab. -

Copy on Write Based File Systems Performance Analysis and Implementation
Copy On Write Based File Systems Performance Analysis And Implementation Sakis Kasampalis Kongens Lyngby 2010 IMM-MSC-2010-63 Technical University of Denmark Department Of Informatics Building 321, DK-2800 Kongens Lyngby, Denmark Phone +45 45253351, Fax +45 45882673 [email protected] www.imm.dtu.dk Abstract In this work I am focusing on Copy On Write based file systems. Copy On Write is used on modern file systems for providing (1) metadata and data consistency using transactional semantics, (2) cheap and instant backups using snapshots and clones. This thesis is divided into two main parts. The first part focuses on the design and performance of Copy On Write based file systems. Recent efforts aiming at creating a Copy On Write based file system are ZFS, Btrfs, ext3cow, Hammer, and LLFS. My work focuses only on ZFS and Btrfs, since they support the most advanced features. The main goals of ZFS and Btrfs are to offer a scalable, fault tolerant, and easy to administrate file system. I evaluate the performance and scalability of ZFS and Btrfs. The evaluation includes studying their design and testing their performance and scalability against a set of recommended file system benchmarks. Most computers are already based on multi-core and multiple processor architec- tures. Because of that, the need for using concurrent programming models has increased. Transactions can be very helpful for supporting concurrent program- ming models, which ensure that system updates are consistent. Unfortunately, the majority of operating systems and file systems either do not support trans- actions at all, or they simply do not expose them to the users. -
Administering Unidata on UNIX Platforms
C:\Program Files\Adobe\FrameMaker8\UniData 7.2\7.2rebranded\ADMINUNIX\ADMINUNIXTITLE.fm March 5, 2010 1:34 pm Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta UniData Administering UniData on UNIX Platforms UDT-720-ADMU-1 C:\Program Files\Adobe\FrameMaker8\UniData 7.2\7.2rebranded\ADMINUNIX\ADMINUNIXTITLE.fm March 5, 2010 1:34 pm Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Notices Edition Publication date: July, 2008 Book number: UDT-720-ADMU-1 Product version: UniData 7.2 Copyright © Rocket Software, Inc. 1988-2010. All Rights Reserved. Trademarks The following trademarks appear in this publication: Trademark Trademark Owner Rocket Software™ Rocket Software, Inc. Dynamic Connect® Rocket Software, Inc. RedBack® Rocket Software, Inc. SystemBuilder™ Rocket Software, Inc. UniData® Rocket Software, Inc. UniVerse™ Rocket Software, Inc. U2™ Rocket Software, Inc. U2.NET™ Rocket Software, Inc. U2 Web Development Environment™ Rocket Software, Inc. wIntegrate® Rocket Software, Inc. Microsoft® .NET Microsoft Corporation Microsoft® Office Excel®, Outlook®, Word Microsoft Corporation Windows® Microsoft Corporation Windows® 7 Microsoft Corporation Windows Vista® Microsoft Corporation Java™ and all Java-based trademarks and logos Sun Microsystems, Inc. UNIX® X/Open Company Limited ii SB/XA Getting Started The above trademarks are property of the specified companies in the United States, other countries, or both. All other products or services mentioned in this document may be covered by the trademarks, service marks, or product names as designated by the companies who own or market them. License agreement This software and the associated documentation are proprietary and confidential to Rocket Software, Inc., are furnished under license, and may be used and copied only in accordance with the terms of such license and with the inclusion of the copyright notice. -

System Calls System Calls
System calls We will investigate several issues related to system calls. Read chapter 12 of the book Linux system call categories file management process management error handling note that these categories are loosely defined and much is behind included, e.g. communication. Why? 1 System calls File management system call hierarchy you may not see some topics as part of “file management”, e.g., sockets 2 System calls Process management system call hierarchy 3 System calls Error handling hierarchy 4 Error Handling Anything can fail! System calls are no exception Try to read a file that does not exist! Error number: errno every process contains a global variable errno errno is set to 0 when process is created when error occurs errno is set to a specific code associated with the error cause trying to open file that does not exist sets errno to 2 5 Error Handling error constants are defined in errno.h here are the first few of errno.h on OS X 10.6.4 #define EPERM 1 /* Operation not permitted */ #define ENOENT 2 /* No such file or directory */ #define ESRCH 3 /* No such process */ #define EINTR 4 /* Interrupted system call */ #define EIO 5 /* Input/output error */ #define ENXIO 6 /* Device not configured */ #define E2BIG 7 /* Argument list too long */ #define ENOEXEC 8 /* Exec format error */ #define EBADF 9 /* Bad file descriptor */ #define ECHILD 10 /* No child processes */ #define EDEADLK 11 /* Resource deadlock avoided */ 6 Error Handling common mistake for displaying errno from Linux errno man page: 7 Error Handling Description of the perror () system call. -

Lecture 1: Introduction to UNIX
The Operating System Course Overview Getting Started Lecture 1: Introduction to UNIX CS2042 - UNIX Tools September 29, 2008 Lecture 1: UNIX Intro The Operating System Description and History Course Overview UNIX Flavors Getting Started Advantages and Disadvantages Lecture Outline 1 The Operating System Description and History UNIX Flavors Advantages and Disadvantages 2 Course Overview Class Specifics 3 Getting Started Login Information Lecture 1: UNIX Intro The Operating System Description and History Course Overview UNIX Flavors Getting Started Advantages and Disadvantages What is UNIX? One of the first widely-used operating systems Basis for many modern OSes Helped set the standard for multi-tasking, multi-user systems Strictly a teaching tool (in its original form) Lecture 1: UNIX Intro The Operating System Description and History Course Overview UNIX Flavors Getting Started Advantages and Disadvantages A Brief History of UNIX Origins The first version of UNIX was created in 1969 by a group of guys working for AT&T's Bell Labs. It was one of the first big projects written in the emerging C language. It gained popularity throughout the '70s and '80s, although non-AT&T versions eventually took the lion's share of the market. Predates Microsoft's DOS by 12 years! Lecture 1: UNIX Intro The Operating System Description and History Course Overview UNIX Flavors Getting Started Advantages and Disadvantages Lecture Outline 1 The Operating System Description and History UNIX Flavors Advantages and Disadvantages 2 Course Overview Class Specifics 3 -

The Strange Birth and Long Life of Unix - IEEE Spectrum Page 1 of 6
The Strange Birth and Long Life of Unix - IEEE Spectrum Page 1 of 6 COMPUTING / SOFTWARE FEATURE The Strange Birth and Long Life of Unix The classic operating system turns 40, and its progeny abound By WARREN TOOMEY / DECEMBER 2011 They say that when one door closes on you, another opens. People generally offer this bit of wisdom just to lend some solace after a misfortune. But sometimes it's actually true. It certainly was for Ken Thompson and the late Dennis Ritchie, two of the greats of 20th-century information technology, when they created the Unix operating system, now considered one of the most inspiring and influential pieces of software ever written. A door had slammed shut for Thompson and Ritchie in March of 1969, when their employer, the American Telephone & Telegraph Co., withdrew from a collaborative project with the Photo: Alcatel-Lucent Massachusetts Institute of KEY FIGURES: Ken Thompson [seated] types as Dennis Ritchie looks on in 1972, shortly Technology and General Electric after they and their Bell Labs colleagues invented Unix. to create an interactive time- sharing system called Multics, which stood for "Multiplexed Information and Computing Service." Time-sharing, a technique that lets multiple people use a single computer simultaneously, had been invented only a decade earlier. Multics was to combine time-sharing with other technological advances of the era, allowing users to phone a computer from remote terminals and then read e -mail, edit documents, run calculations, and so forth. It was to be a great leap forward from the way computers were mostly being used, with people tediously preparing and submitting batch jobs on punch cards to be run one by one. -

The Strange Birth and Long Life of Unix - IEEE Spectrum
The Strange Birth and Long Life of Unix - IEEE Spectrum http://spectrum.ieee.org/computing/software/the-strange-birth-and-long-li... COMPUTING / SOFTWARE FEATURE The Strange Birth and Long Life of Unix The classic operating system turns 40, and its progeny abound By WARREN TOOMEY / DECEMBER 2011 They say that when one door closes on you, another opens. People generally offer this bit of wisdom just to lend some solace after a misfortune. But sometimes it's actually true. It certainly was for Ken Thompson and the late Dennis Ritchie, two of the greats of 20th-century information technology, when they created the Unix operating system, now considered one of the most inspiring and influential pieces of software ever written. A door had slammed shut for Thompson and Ritchie in March of 1969, when their employer, the American Telephone & Telegraph Co., withdrew from a collaborative project with the Photo: Alcatel-Lucent Massachusetts Institute of KEY FIGURES: Ken Thompson [seated] types as Dennis Ritchie looks on in 1972, shortly Technology and General Electric after they and their Bell Labs colleagues invented Unix. to create an interactive time-sharing system called Multics, which stood for "Multiplexed Information and Computing Service." Time-sharing, a technique that lets multiple people use a single computer simultaneously, had been invented only a decade earlier. Multics was to combine time-sharing with other technological advances of the era, allowing users to phone a computer from remote terminals and then read e-mail, edit documents, run calculations, and so forth. It was to be a great leap forward from the way computers were mostly being used, with people tediously preparing and submitting batch jobs on punch cards to be run one by one. -

Introduction to UNIX What Is UNIX? Why UNIX? Brief History of UNIX Early UNIX History UNIX Variants
What is UNIX? A modern computer operating system Introduction to UNIX Operating system: “a program that acts as an intermediary between a user of the computer and the computer hardware” CS 2204 Software that manages your computer’s resources (files, programs, disks, network, …) Class meeting 1 e.g. Windows, MacOS Modern: features for stability, flexibility, multiple users and programs, configurability, etc. *Notes by Doug Bowman and other members of the CS faculty at Virginia Tech. Copyright 2001-2003. (C) Doug Bowman, Virginia Tech, 2001- 2 Why UNIX? Brief history of UNIX Used in many scientific and industrial settings Ken Thompson & Dennis Richie Huge number of free and well-written originally developed the earliest software programs versions of UNIX at Bell Labs for Open-source OS internal use in 1970s Internet servers and services run on UNIX Borrowed best ideas from other Oss Largely hardware-independent Meant for programmers and computer Based on standards experts Meant to run on “mini computers” (C) Doug Bowman, Virginia Tech, 2001- 3 (C) Doug Bowman, Virginia Tech, 2001- 4 Early UNIX History UNIX variants Thompson also rewrote the operating system Two main threads of development: in high level language of his own design Berkeley software distribution (BSD) which he called B. Unix System Laboratories System V Sun: SunOS, Solaris The B language lacked many features and Ritchie decided to design a successor to B GNU: Linux (many flavors) which he called C. SGI: Irix They then rewrote UNIX in the C FreeBSD programming language to aid in portability. Hewlett-Packard: HP-UX Apple: OS X (Darwin) … (C) Doug Bowman, Virginia Tech, 2001- 5 (C) Doug Bowman, Virginia Tech, 2001- 6 1 Layers in the UNIX System UNIX Structure User Interface The kernel is the core of the UNIX Library Interface Users system, controlling the system Standard Utility Programs hardware and performing various low- (shell, editors, compilers, etc.) System Interface calls User Mode level functions. -

Filesystems HOWTO Filesystems HOWTO Table of Contents Filesystems HOWTO
Filesystems HOWTO Filesystems HOWTO Table of Contents Filesystems HOWTO..........................................................................................................................................1 Martin Hinner < [email protected]>, http://martin.hinner.info............................................................1 1. Introduction..........................................................................................................................................1 2. Volumes...............................................................................................................................................1 3. DOS FAT 12/16/32, VFAT.................................................................................................................2 4. High Performance FileSystem (HPFS)................................................................................................2 5. New Technology FileSystem (NTFS).................................................................................................2 6. Extended filesystems (Ext, Ext2, Ext3)...............................................................................................2 7. Macintosh Hierarchical Filesystem − HFS..........................................................................................3 8. ISO 9660 − CD−ROM filesystem.......................................................................................................3 9. Other filesystems.................................................................................................................................3 -
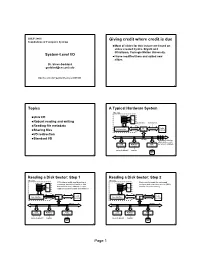
System-Level I/O I Have Modified Them and Added New Slides
JDEP 284H Giving credit where credit is due Foundations of Computer Systems Most of slides for this lecture are based on slides created by Drs. Bryant and O’Hallaron, Carnegie Mellon University. System-Level I/O I have modified them and added new slides. Dr. Steve Goddard [email protected] http://cse.unl.edu/~goddard/Courses/JDEP284 2 Topics A Typical Hardware System CPU chip register file Unix I/O ALU Robust reading and writing system bus memory bus Reading file metadata I/O main bus interface Sharing files bridge memory I/O redirection Standard I/O I/O bus Expansion slots for other devices such USB graphics disk as network adapters. controller adapter controller mouse keyboard monitor disk 3 4 Reading a Disk Sector: Step 1 Reading a Disk Sector: Step 2 CPU chip CPU chip CPU initiates a disk read by writing a Disk controller reads the sector and register file command, logical block number, and register file performs a direct memory access (DMA) destination memory address to a port transfer into main memory. ALU ALU (address) associated with disk controller. main main bus interface bus interface memory memory I/O bus I/O bus USB graphics disk USB graphics disk controller adapter controller controller adapter controller mouse keyboard monitor mouse keyboard monitor disk disk 5 6 Page 1 Reading a Disk Sector: Step 3 Unix Files CPU chip When the DMA transfer completes, the register file disk controller notifies the CPU with an A Unix file is a sequence of m bytes: interrupt (i.e., asserts a special “interrupt” B , B , ... -

A Brief History of Unix
A Brief History of Unix Tom Ryder [email protected] https://sanctum.geek.nz/ I Love Unix ∴ I Love Linux ● When I started using Linux, I was impressed because of the ethics behind it. ● I loved the idea that an operating system could be both free to customise, and free of charge. – Being a cash-strapped student helped a lot, too. ● As my experience grew, I came to appreciate the design behind it. ● And the design is UNIX. ● Linux isn’t a perfect Unix, but it has all the really important bits. What do we actually mean? ● We’re referring to the Unix family of operating systems. – Unix from Bell Labs (Research Unix) – GNU/Linux – Berkeley Software Distribution (BSD) Unix – Mac OS X – Minix (Intel loves it) – ...and many more Warning signs: 1/2 If your operating system shows many of the following symptoms, it may be a Unix: – Multi-user, multi-tasking – Hierarchical filesystem, with a single root – Devices represented as files – Streams of text everywhere as a user interface – “Formatless” files ● Data is just data: streams of bytes saved in sequence ● There isn’t a “text file” attribute, for example Warning signs: 2/2 – Bourne-style shell with a “pipe”: ● $ program1 | program2 – “Shebangs” specifying file interpreters: ● #!/bin/sh – C programming language baked in everywhere – Classic programs: sh(1), awk(1), grep(1), sed(1) – Users with beards, long hair, glasses, and very strong opinions... Nobody saw it coming! “The number of Unix installations has grown to 10, with more expected.” — Ken Thompson and Dennis Ritchie (1972) ● Unix in some flavour is in servers, desktops, embedded software (including Intel’s management engine), mobile phones, network equipment, single-board computers.. -

History of Unix.Pdf
History of Unix In order to define UNIX, it helps to look at its history. In 1969, Ken Thompson, Dennis Ritchie and others started work on what was to become UNIX on a "little-used PDP-7 in a corner" at AT&T Bell Labs. For ten years, the development of UNIX proceeded at AT&T in numbered versions. V4 (1974) was re-written in C -- a major milestone for the operating system's portability among different systems. V6 (1975) was the first to become available outside Bell Labs -- it became the basis of the first version of UNIX developed at the University of California Berkeley. Bell Labs continued work on UNIX into the 1980s, culminating in the release of System V (as in "five," not the letter) in 1983 and System V, Release 4 (abbreviated SVR4) in 1989. Meanwhile, programmers at the University of California hacked mightily on the source code AT&T had released, leading to many a master thesis. The Berkeley Standard Distribution (BSD) became a second major variant of "UNIX." It was widely deployed in both university and corporate computing environments starting with the release of BSD 4.2 in 1984. Some of its features were incorporated into SVR4. As the 1990s opened, AT&T's source code licensing had created a flourishing market for hundreds of UNIX variants by different manufacturers. AT&T sold its UNIX business to Novell in 1993, and Novell sold it to the Santa Cruz Operation two years later. In the meantime, the UNIX trademark had been passed to the X/Open consortium, which eventually merged to form The Open Group.1 While the stewardship of UNIX was passing from entity to entity, several long- running development efforts started bearing fruit.