Opendocument Format the Standard for Office Documents
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Microsoft Office Open XML Formats New File Formats for “Office 12”
The Microsoft Office Open XML Formats New File Formats for “Office 12” White Paper Published: June 2005 For the latest information, please see http://www.microsoft.com/office/wave12 Contents Introduction ...............................................................................................................................1 From .doc to .docx: a brief history of the Office file formats.................................................1 Benefits of the Microsoft Office Open XML Formats ................................................................2 Integration with Business Data .............................................................................................2 Openness and Transparency ...............................................................................................4 Robustness...........................................................................................................................7 Description of the Microsoft Office Open XML Format .............................................................9 Document Parts....................................................................................................................9 Microsoft Office Open XML Format specifications ...............................................................9 Compatibility with new file formats........................................................................................9 For more information ..............................................................................................................10 -

Why ODF?” - the Importance of Opendocument Format for Governments
“Why ODF?” - The Importance of OpenDocument Format for Governments Documents are the life blood of modern governments and their citizens. Governments use documents to capture knowledge, store critical information, coordinate activities, measure results, and communicate across departments and with businesses and citizens. Increasingly documents are moving from paper to electronic form. To adapt to ever-changing technology and business processes, governments need assurance that they can access, retrieve and use critical records, now and in the future. OpenDocument Format (ODF) addresses these issues by standardizing file formats to give governments true control over their documents. Governments using applications that support ODF gain increased efficiencies, more flexibility and greater technology choice, leading to enhanced capability to communicate with and serve the public. ODF is the ISO Approved International Open Standard for File Formats ODF is the only open standard for office applications, and it is completely vendor neutral. Developed through a transparent, multi-vendor/multi-stakeholder process at OASIS (Organization for the Advancement of Structured Information Standards), it is an open, XML- based document file format for displaying, storing and editing office documents, such as spreadsheets, charts, and presentations. It is available for implementation and use free from any licensing, royalty payments, or other restrictions. In May 2006, it was approved unanimously as an International Organization for Standardization (ISO) and International Electrotechnical Commission (IEC) standard. Governments and Businesses are Embracing ODF The promotion and usage of ODF is growing rapidly, demonstrating the global need for control and choice in document applications. For example, many enlightened governments across the globe are making policy decisions to move to ODF. -

MPEG-21 Overview
MPEG-21 Overview Xin Wang Dept. Computer Science, University of Southern California Workshop on New Multimedia Technologies and Applications, Xi’An, China October 31, 2009 Agenda ● What is MPEG-21 ● MPEG-21 Standards ● Benefits ● An Example Page 2 Workshop on New Multimedia Technologies and Applications, Oct. 2009, Xin Wang MPEG Standards ● MPEG develops standards for digital representation of audio and visual information ● So far ● MPEG-1: low resolution video/stereo audio ● E.g., Video CD (VCD) and Personal music use (MP3) ● MPEG-2: digital television/multichannel audio ● E.g., Digital recording (DVD) ● MPEG-4: generic video and audio coding ● E.g., MP4, AVC (H.24) ● MPEG-7 : visual, audio and multimedia descriptors MPEG-21: multimedia framework ● MPEG-A: multimedia application format ● MPEG-B, -C, -D: systems, video and audio standards ● MPEG-M: Multimedia Extensible Middleware ● ● MPEG-V: virtual worlds MPEG-U: UI ● (29116): Supplemental Media Technologies ● ● (Much) more to come … Page 3 Workshop on New Multimedia Technologies and Applications, Oct. 2009, Xin Wang What is MPEG-21? ● An open framework for multimedia delivery and consumption ● History: conceived in 1999, first few parts ready early 2002, most parts done by now, some amendment and profiling works ongoing ● Purpose: enable all-electronic creation, trade, delivery, and consumption of digital multimedia content ● Goals: ● “Transparent” usage ● Interoperable systems ● Provides normative methods for: ● Content identification and description Rights management and protection ● Adaptation of content ● Processing on and for the various elements of the content ● ● Evaluation methods for determining the appropriateness of possible persistent association of information ● etc. Page 4 Workshop on New Multimedia Technologies and Applications, Oct. -

Circular Economy and Standardization
G7 WORKSHOP, 20-21 MARCH 2019 TOOLS MAKING VALUE CHAINS MORE CIRCULAR AND RESOURCE EFFICIENT STANDARDIZATION STANDARDIZATION A FRAMEWORK FOR PROGRESS FOR ALL Olivier Peyrat ISO Board member Past ISO VP Finance AFNOR CEO SUCCESS STORIES OF STANDARDIZATION LIFE CYCLE ASSESSMENT 100 million mobile phones Forgotten in cupboards and drawers in France* € 124 million in gold lost due for failing to recycle 27,000 tons printed circuit boards in France in 2012* 3 YEARS average interval for replacing for mobile phones in Europe* ISO 14040 : Life Cycle Assessment the purpose of LCA is to identify ways of reducing environmental impact at each ones of these stages. It is important to decision-makers in the industry: • preservation of resources • energy choices • production modes Tool for implementing the Paris Agreement, LCA reveals that 70% of environmental impact is determined at the raw material stage. * Rapport n°850 du Sénat, 27 septembre 2016 Référence document Page 2 INTERNATIONAL ORGANIZATIONS International standards: volontary implementation International UIT ISO IEC level National level National standardization body (AFNOR, BSI, DIN, SAC, ANSI…) European ETSI CEN CENELEC level European standards: mandatory implementation Référence document Page 3 STANDARDIZATION STRATEGY ON CIRCULAR ECONOMY Climate change Resources New principles New paradigms Standards: Compilations of good practices New business models circular economy in standardization documents Page 4 STANDARDIZATION STRATEGY ON CIRCULAR ECONOMY What are the expected benefits of standards -
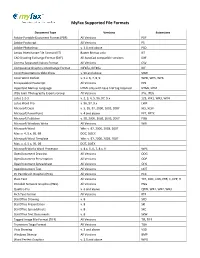
Supported File Types
MyFax Supported File Formats Document Type Versions Extensions Adobe Portable Document Format (PDF) All Versions PDF Adobe Postscript All Versions PS Adobe Photoshop v. 3.0 and above PSD Amiga Interchange File Format (IFF) Raster Bitmap only IFF CAD Drawing Exchange Format (DXF) All AutoCad compatible versions DXF Comma Separated Values Format All Versions CSV Compuserve Graphics Interchange Format GIF87a, GIF89a GIF Corel Presentations Slide Show v. 96 and above SHW Corel Word Perfect v. 5.x. 6, 7, 8, 9 WPD, WP5, WP6 Encapsulated Postscript All Versions EPS Hypertext Markup Language HTML only with base href tag required HTML, HTM JPEG Joint Photography Experts Group All Versions JPG, JPEG Lotus 1-2-3 v. 2, 3, 4, 5, 96, 97, 9.x 123, WK1, WK3, WK4 Lotus Word Pro v. 96, 97, 9.x LWP Microsoft Excel v. 5, 95, 97, 2000, 2003, 2007 XLS, XLSX Microsoft PowerPoint v. 4 and above PPT, PPTX Microsoft Publisher v. 98, 2000, 2002, 2003, 2007 PUB Microsoft Windows Write All Versions WRI Microsoft Word Win: v. 97, 2000, 2003, 2007 Mac: v. 4, 5.x, 95, 98 DOC, DOCX Microsoft Word Template Win: v. 97, 2000, 2003, 2007 Mac: v. 4, 5.x, 95, 98 DOT, DOTX Microsoft Works Word Processor v. 4.x, 5, 6, 7, 8.x, 9 WPS OpenDocument Drawing All Versions ODG OpenDocument Presentation All Versions ODP OpenDocument Spreadsheet All Versions ODS OpenDocument Text All Versions ODT PC Paintbrush Graphics (PCX) All Versions PCX Plain Text All Versions TXT, DOC, LOG, ERR, C, CPP, H Portable Network Graphics (PNG) All Versions PNG Quattro Pro v. -

How to Use the IBM CMIS Authentication Methods Contents
How to use the IBM CMIS authentication methods This tech note describes how to use the authentication methods supported with IBM CMIS. Contents Introduction .............................................................................................................................................. 1 Before You Start ........................................................................................................................................ 2 Using HTTP Basic Authentication .............................................................................................................. 2 Basic Authentication with Authorization Header ................................................................................. 2 Basic Authentication with an LTPA Token sent via an HTTP Cookie Header ........................................ 3 Using WS-Security Authentication ............................................................................................................ 4 LTPA Token sent via a SOAP Header ..................................................................................................... 4 Username Token sent via SOAP Header ............................................................................................... 5 Introduction There are two authentication methods supported with IBM CMIS: • HTTP Basic Authentication This option uses an HTTP header that contains an encoded username and password to authenticate clients. • WS-Security Authentication This option uses a WS-Security SOAP header to authenticate clients. -

Background Information History, Licensing, and File Formats Copyright This Document Is Copyright © 2008 by Its Contributors As Listed in the Section Titled Authors
Getting Started Guide Appendix B Background Information History, licensing, and file formats Copyright This document is Copyright © 2008 by its contributors as listed in the section titled Authors. You may distribute it and/or modify it under the terms of either the GNU General Public License, version 3 or later, or the Creative Commons Attribution License, version 3.0 or later. All trademarks within this guide belong to their legitimate owners. Authors Jean Hollis Weber Feedback Please direct any comments or suggestions about this document to: [email protected] Acknowledgments This Appendix includes material written by Richard Barnes and others for Chapter 1 of Getting Started with OpenOffice.org 2.x. Publication date and software version Published 13 October 2008. Based on OpenOffice.org 3.0. You can download an editable version of this document from http://oooauthors.org/en/authors/userguide3/published/ Contents Introduction...........................................................................................4 A short history of OpenOffice.org..........................................................4 The OpenOffice.org community.............................................................4 How is OpenOffice.org licensed?...........................................................5 What is “open source”?..........................................................................5 What is OpenDocument?........................................................................6 File formats OOo can open.....................................................................6 -

Quadtree Based JBIG Compression
Quadtree Based JBIG Compression B. Fowler R. Arps A. El Gamal D. Yang ISL, Stanford University, Stanford, CA 94305-4055 ffowler,arps,abbas,[email protected] Abstract A JBIG compliant, quadtree based, lossless image compression algorithm is describ ed. In terms of the numb er of arithmetic co ding op erations required to co de an image, this algorithm is signi cantly faster than previous JBIG algorithm variations. Based on this criterion, our algorithm achieves an average sp eed increase of more than 9 times with only a 5 decrease in compression when tested on the eight CCITT bi-level test images and compared against the basic non-progressive JBIG algorithm. The fastest JBIG variation that we know of, using \PRES" resolution reduction and progressive buildup, achieved an average sp eed increase of less than 6 times with a 7 decrease in compression, under the same conditions. 1 Intro duction In facsimile applications it is desirable to integrate a bilevel image sensor with loss- less compression on the same chip. Suchintegration would lower p ower consumption, improve reliability, and reduce system cost. To reap these b ene ts, however, the se- lection of the compression algorithm must takeinto consideration the implementation tradeo s intro duced byintegration. On the one hand, integration enhances the p os- sibility of parallelism which, if prop erly exploited, can sp eed up compression. On the other hand, the compression circuitry cannot b e to o complex b ecause of limitations on the available chip area. Moreover, most of the chip area on a bilevel image sensor must b e o ccupied by photo detectors, leaving only the edges for digital logic. -

National and International Standardization of Radiation Dosimetry
National and International Standardization of Radiation Dosimetry PROCEEDINGS OF A SYMPOSIUM ATLANTA 5 -9 DECEMBER 1977 V tTj? INTERNATIONAL ATOMIC ENERGY AGENCY, VIENNA, 1978 >*___¿I? NATIONAL AND INTERNATIONAL STANDARDIZATION OF RADIATION DOSIMETRY VOL.II The following States are Members of the International Atomic Energy Agency: AFGHANISTAN HOLY SEE PHILIPPINES ALBANIA HUNGARY POLAND ALGERIA ICELAND PORTUGAL ARGENTINA INDIA QATAR AUSTRALIA INDONESIA ROMANIA AUSTRIA IRAN SAUDI ARABIA BANGLADESH IRAQ SENEGAL BELGIUM IRELAND SIERRA LEONE BOLIVIA ISRAEL SINGAPORE BRAZIL ITALY SOUTH AFRICA BULGARIA IVORY COAST SPAIN BURMA JAMAICA SRI LANKA BYELORUSSIAN SOVIET JAPAN SUDAN SOCIALIST REPUBLIC JORDAN SWEDEN CANADA KENYA SWITZERLAND CHILE KOREA, REPUBLIC OF SYRIAN ARAB REPUBLIC COLOMBIA KUWAIT THAILAND COSTA RICA LEBANON TUNISIA CUBA LIBERIA TURKEY CYPRUS LIBYAN ARAB JAMAHIRIYA UGANDA CZECHOSLOVAKIA LIECHTENSTEIN UKRAINIAN SOVIET SOCIALIST DEMOCRATIC KAMPUCHEA LUXEMBOURG REPUBLIC DEMOCRATIC PEOPLE’S MADAGASCAR UNION OF SOVIET SOCIALIST REPUBLIC OF KOREA MALAYSIA REPUBLICS DENMARK MALI UNITED ARAB EMIRATES DOMINICAN REPUBLIC MAURITIUS UNITED KINGDOM OF GREAT ECUADOR MEXICO BRITAIN AND NORTHERN EGYPT MONACO IRELAND EL SALVADOR MONGOLIA UNITED REPUBLIC OF ETHIOPIA MOROCCO CAMEROON FINLAND NETHERLANDS UNITED REPUBLIC OF FRANCE NEW ZEALAND TANZANIA GABON NICARAGUA UNITED STATES OF AMERICA GERMAN DEMOCRATIC REPUBLIC NIGER URUGUAY GERMANY, FEDERAL REPUBLIC OF NIGERIA VENEZUELA GHANA NORWAY VIET NAM GREECE PAKISTAN YUGOSLAVIA GUATEMALA PANAMA ZAIRE HAITI PARAGUAY ZAMBIA PERU The Agency’s Statute was approved on 23 October 1956 by the Conference on the Statute of the IAEA held at United Nations Headquarters, New York; it entered into force on 29 July 1957. The Headquarters of the Agency are situated in Vienna. Its principal objective is “ to accelerate and enlarge the contribution of atomic energy to peace, health and prosperity throughout the world” . -

Extensible Access Control Markup Language (XACML) Version 1.0
1 2 eXtensible Access Control Markup Language 3 (XACML) Version 2.0 4 OASIS Standard, 1 Feb 2005 5 Document Identifier: oasis-access_control-xacml-2.0-core-spec-os 6 Location: http://docs.oasis-open.org/xacml/2.0/access_control-xacml-2.0-core-spec-os.pdf 7 Editor: 8 Tim Moses, Entrust Inc. ([email protected]) 9 Abstract: 10 This specification defines version 2.0 of the extensible access-control markup language. 11 Status: 12 This version of the specification is an approved OASIS Standard within the OASIS Access 13 Control TC. 14 Access Control TC members should send comments on this specification to the 15 [email protected] list. Others may use the following link and complete the 16 comment form: http://oasis-open.org/committees/comments/form.php?wg_abbrev=xacml. 17 For information on whether any patents have been disclosed that may be essential to 18 implementing this specification, and any offers of patent licensing terms, please refer to the 19 Intellectual Property Rights section of the Access Control TC web page (http://www.oasis- 20 open.org/committees/tc_home.php?wg_abbrev=xacml). 21 For any errata page for this specification, please refer to the Access Control TC web page 22 (http://www.oasis-open.org/committees/tc_home.php?wg_abbrev=xacml). 23 The non-normative errata page for this specification is located at 24 www.oasis-open.org/committees/access-control. 25 Copyright © OASIS Open 2004-2005 All Rights Reserved. access_control-xacml-2.0-core-spec-os 1 February 2005 Copyright © OASIS Open 2004. -

Server Administration Manual Release Latest
Nextcloud Server Administration Manual Release latest The Nextcloud developers Oct 01, 2021 CONTENTS 1 Introduction 1 1.1 Videos and blogs.............................................1 1.2 Target audience..............................................1 2 Release notes 3 3 Maintenance and release schedule5 3.1 Major releases..............................................5 3.2 Maintenance releases...........................................5 3.3 Older versions..............................................6 4 Installation and server configuration7 4.1 System requirements...........................................7 4.2 Deployment recommendations......................................9 4.3 Installation on Linux...........................................9 4.4 Installation wizard............................................ 17 4.5 Installing from command line...................................... 21 4.6 Supported apps.............................................. 22 4.7 SELinux configuration.......................................... 24 4.8 NGINX configuration.......................................... 27 4.9 Hardening and security guidance.................................... 36 4.10 Server tuning............................................... 40 4.11 Example installation on Ubuntu 20.04 LTS............................... 42 4.12 Example installation on CentOS 8.................................... 44 4.13 Example installation on OpenBSD.................................... 48 5 Nextcloud configuration 53 5.1 Warnings on admin page........................................ -

SAML Profiles
EUROPEAN COMMISSION DIRECTORATE-GENERAL FOR HEALTH AND FOOD SAFETY General Affairs Information systems eHealth DSI Patient Summary and ePrescription SAML Profiles DOCUMENT VERSION 2.0.0 DATE 28/03/2017 STATUS Release Candidate Disclaimer "Release Candidate" versions are provided for evaluation/approval purposes only. Minor updates that benefit the document maturity are expected towards the "Production Release". Responsibility for the information and views set out in this document lies entirely with the authors. Reproduction is authorised provided the source is acknowledged. COVER AND CONTROL PAGE OF DOCUMENT Document old name: epSOS Architecture and Design EED DESIGN – epSOS SAML Profiles Document name: SAML Profile Distribution level*: PU Status: Release Candidate Author(s): eHealth DSI provider Organization: * Distribution level: PU = Public, PP = Restricted to other programme participants, RE = Restricted to a group specified by the consortium, CO = Confidential, only for members of the consortium. ABSTRACT This normative binding specifies the mapping of the eHealth DSI HP identity and treatment context claims onto the SAML 2.0. CHANGE HISTORY Version Date Status Changes From Review V 1.1 17/12/2013 Publish Fraunhofer FOKUS V2.0.0 28/03/2017 Remove all eHealth DSI provider references to epSOS and requirements TABLE OF CONTENTS 1 Introduction............................................................................................................................... 4 1.1 eHealth DSI Identity and Context Claims...........................................................................