Volume XV, Issue 4 August 2021 PERSPECTIVES on TERRORISM Volume 15, Issue 4
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Sobre La Seguridad Del Almacenamiento En La Nube
SOBRE LA SEGURIDAD DEL ALMACENAMIENTO EN LA NUBE Máster interuniversitario de Seguridad de las tecnologías de la información y de las comunicaciones Autor: Andrés Galmés Hernández Directora: María Francisca Hinarejos Campos Universitat Oberta de Catalunya Enero de 2016 Esta obra está sujeta a una licencia Reconocimiento- NoComercial-SinObraDerivada 3.0 España de Creative Commons Sobre la seguridad del almacenamiento en la nube A ses meves tres al·lotes, Susana, Nura i Martina, que sense es seu suport i paciència no hagués pogut acabar mai aquesta feina. Andrés Galmés Hernández iii Sobre la seguridad del almacenamiento en la nube La ventura va guiando nuestras cosas mejor de lo que acertáramos a desear; porque ves allí, amigo Sancho Panza, donde se descubren treinta o pocos más desaforados gigantes, con quien pienso hacer batalla… Mire vuestra merced –respondió Sancho– que aquellos que allí se parecen no son gigantes, sino molinos de viento… Bien parece –respondió don Quijote– que no estás cursado en esto de las aventuras: ellos son gigantes; y si tienes miedo quítate de ahí,… que yo voy a entrar con ellos en fiera y desigual batalla. Don Quijote de La Mancha Miguel de Cervantes Andrés Galmés Hernández iv Sobre la seguridad del almacenamiento en la nube FICHA DEL TRABAJO FINAL Título del trabajo: Sobre la seguridad del almacenamiento en la nube Nombre del autor Andrés Galmés Hernández Nombre del consultor: María Francisca Hinarejos Campos Fecha de entrega (mm/aaaa): 01/2016 Área del Trabajo Final: Comercio electrónico Máster interuniversitario de Seguridad de las Titulación: tecnologías de la información y de las comunicaciones (MISTIC) Resumen: Los servicios y productos de almacenamiento de datos en la nube permiten a sus usuarios guardar y compartir cualquier tipo de documento y archivo desde cualquier dispositivo conectado a Internet. -

Charles Roberts Autograph Letters Collection MC.100
Charles Roberts Autograph Letters collection MC.100 Last updated on January 06, 2021. Haverford College Quaker & Special Collections Charles Roberts Autograph Letters collection Table of Contents Summary Information....................................................................................................................................7 Administrative Information........................................................................................................................... 7 Controlled Access Headings..........................................................................................................................7 Collection Inventory...................................................................................................................................... 9 110.American poets................................................................................................................................. 9 115.British poets.................................................................................................................................... 16 120.Dramatists........................................................................................................................................23 130.American prose writers...................................................................................................................25 135.British Prose Writers...................................................................................................................... 33 140.American -

SALAFI- JIHADISM in AFRICA BRIEF / 12 June 2021
SALAFI- JIHADISM IN AFRICA BRIEF / 12 June 2021 A winning strategy by SERIES Giovanni Faleg* Senior Analyst, EUISS Katariina Mustasilta Postdoctoral Fellow, Finnish Institute of International Affairs Summary › Violent extremism has become a grow- ing threat throughout the African conti- INTRODUCTION nent: all sub-regions have experienced the emergence of groups active across state Violent extremism keeps spreading in Africa, showing boundaries. notable resilience despite years of counter-extremism › Today, armed actors engaging in violent and prevention efforts by governments and interna- extremism in the continent are mainly af- tional actors (1)*. In addition to killing thousands, it filiated with Islamist militant groups and costs the affected regions an estimated $97 billion in particularly Salafi-jihadist ideology. lost informal economic activity each year (2). › The spread of Salafi-jihadism in Africa is Today, armed actors engaging in violent extremism fuelled by a combination of localised griev- in the continent are mainly affiliated with Islamist ances and transnational ambitions, while militant groups and organisations and particularly tactical and strategic flexibility has in- Salafi-jihadist ideology (3). Recent data indicates a creased the resilience of insurgent groups. dangerous expansion of Salafi-jihadist armed groups › Once it has emerged as a potent force, de- — often simply labelled as violent extremist or ter- feating Salafi-jihadism on the battlefield rorist organisations (4) — beyond the traditional hot- proves very difficult as groups show enor- spots in the Sahel, Lake Chad Basin and the Horn of mous resilience, even when facing tacti- Africa to West Africa’s coastal states and Central and cal defeats. Southern Africa. -

DEALING with JIHADISM a Policy Comparison Between the Netherlands, Belgium, Denmark, Germany, France, the UK and the US (2010 to 2017)
DEALING WITH JIHADISM A policy comparison between the Netherlands, Belgium, Denmark, Germany, France, the UK and the US (2010 to 2017) Stef Wittendorp, Roel de Bont, Jeanine de Roy van Zuijdewijn and Edwin Bakker ISGA Report Dealing with jihadism: A policy comparison between the Netherlands, Belgium, Denmark, Germany, France, the UK, and the US (2010 to 2017) Stef Wittendorp, Roel de Bont, Jeanine de Roy van Zuijdewijn and Edwin Bakker December 2017 (the research was completed in October 2016) ISSN 2452-0551 e-ISSN 2452-056X © 2017, Stef Wittendorp / Roel de Bont / Jeanine de Roy van Zuijdewijn / Edwin Bakker / Leiden University Cover design: Oscar Langley www.oscarlangley.com All rights reserved. Without limiting the right under copyright reserved above, no part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means (electronic, mechanical, photocopying, recording or otherwise) without prior permission of both the copyright owners Leiden University and the authors of the book. Table of Contents List with abbreviations................................................................................................ 5 List with tables and figures ....................................................................................... 10 Summary .................................................................................................................. 11 1 Introduction .......................................................................................................... 13 2 -
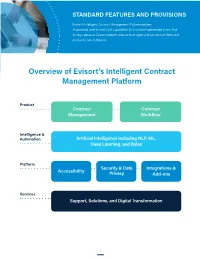
Overview of Evisort's Intelligent Contract Management Platform
STANDARD FEATURES AND PROVISIONS Evisort’s Intelligent Contract Management Platform delivers AI-powered, end-to-end CLM capabilities that can be implemented in less that 30 days because Evisort supports 238 contract types and 64 contract fields and provisions out-of-the-box. Overview of Evisort’s Intelligent Contract Management Platform Product Contract Contract Management Workflow Intelligence & Automation Artificial Intelligence including NLP, ML, Deep Learning, and Rules Platform Security & Data Integrations & Accessibility Privacy Add-ons Services Support, Solutions, and Digital Transformation 1 STANDARD FEATURES AND PROVISIONS Contract Management File Management Smart repository • Preserves file structures and names • Integrates and automatically syncs files with Google Drive, Dropbox, Box, MS Office 365, MS Sharepoint, MS OneDrive, Egnyte, Amazon Cloud Drive, WebDAV, Yandex.Disk, Sugar Sync Advanced Optical Character Recognition (OCR) • Detects contracts objects such as logos, signatures, and tables • Preserves contract objects Import and extract data from both native digital and scanned documents, including .doc/.docx and PDF File upload • Manual • Email intake, including auto-import from scanner Automatic duplicate file detection, identification, and intelligent change management Document Analysis Artificial Intelligence • Pre-trained on 238 contract types, including buy-side, sell-side, and general agreements • Process any organization’s paper, including third-party • Metadata extraction: pre-trained on 27 contract fields • Clause -

RUSSIA and CHINA and Central Asia Programme at ISPI
RUSSIA AND CHINA. ANATOMY OF A A PARTNERSHIP OF AND RUSSIA CHINA. ANATOMY Aldo Ferrari While the “decline of the West” is now almost taken is Head of the Russia, Caucasus for granted, China’s impressive economic performance RUSSIA AND CHINA and Central Asia Programme at ISPI. and the political influence of an assertive Russia in the international arena are combining to make Eurasia a key Founded in 1934, ISPI is Eleonora Tafuro Ambrosetti Anatomy of a Partnership hub of political and economic power. That, certainly, an independent think tank is a Research Fellow committed to the study of is the story which Beijing and Moscow have been telling at the Russia, Caucasus and international political and Central Asia Centre at ISPI. for years. edited by Aldo Ferrari and Eleonora Tafuro Ambrosetti economic dynamics. Are the times ripe for a “Eurasian world order”? What It is the only Italian Institute exactly does the supposed Sino-Russian challenge to introduction by Paolo Magri – and one of the very few in the liberal world entail? Are the two countries’ worsening Europe – to combine research clashes with the West drawing them closer together? activities with a significant This ISPI Report tackles every aspect of the apparently commitment to training, events, solidifying alliance between Moscow and Beijing, but also and global risk analysis for points out its growing asymmetries. It also recommends companies and institutions. some policies that could help the EU to deal with this ISPI favours an interdisciplinary “Eurasian shift”, a long-term and multi-faceted power and policy-oriented approach made possible by a research readjustment that may lead to the end of the world team of over 50 analysts and as we have known it. -

Youth in Central Asia
YOUTH IN CENTRAL ASIA: LOSING THE NEW GENERATION 31 October 2003 Asia Report N°66 Osh/Brussels TABLE OF CONTENTS EXECUTIVE SUMMARY AND RECOMMENDATIONS................................................. i I. INTRODUCTION .......................................................................................................... 1 II. OBSTACLES FOR YOUTH ......................................................................................... 2 A. EDUCATION ..........................................................................................................................2 1. Funding......................................................................................................................2 2. Corruption..................................................................................................................4 3. Access........................................................................................................................6 4. Content.....................................................................................................................10 B. ECONOMIC ISSUES ..............................................................................................................12 C. SOCIAL INTEGRATION .........................................................................................................14 1. Leisure and Sport.....................................................................................................16 2. The Family and Community....................................................................................17 -

Social Media in Africa
Social media in Africa A double-edged sword for security and development Technical annex Kate Cox, William Marcellino, Jacopo Bellasio, Antonia Ward, Katerina Galai, Sofia Meranto, Giacomo Persi Paoli Table of contents Table of contents ...................................................................................................................................... iii List of figures ........................................................................................................................................... iv List of tables .............................................................................................................................................. v Abbreviations .......................................................................................................................................... vii Annex A: Overview of Technical Annex .................................................................................................... 1 Annex B: Background to al-Shabaab, Boko Haram and ISIL ..................................................................... 3 Annex C: Timeline of significant dates ...................................................................................................... 9 Annex D: Country profiles ...................................................................................................................... 25 Annex E: Social media and communications platforms ............................................................................ 31 Annex F: Twitter data -

125 Years of Women in Medicine
STRENGTH of MIND 125 Years of Women in Medicine Medical History Museum, University of Melbourne Kathleen Roberts Marjorie Thompson Margaret Ruth Sandland Muriel Denise Sturtevant Mary Jocelyn Gorman Fiona Kathleen Judd Ruth Geraldine Vine Arlene Chan Lilian Mary Johnstone Veda Margaret Chang Marli Ann Watt Jennifer Maree Wheelahan Min-Xia Wang Mary Louise Loughnan Alexandra Sophie Clinch Kate Suzannah Stone Bronwyn Melissa Dunbar King Nicole Claire Robins-Browne Davorka Anna Hemetek MaiAnh Hoang Nguyen Elissa Stafford Trisha Michelle Prentice Elizabeth Anne McCarthy Fay Audrey Elizabeth Williams Stephanie Lorraine Tasker Joyce Ellen Taylor Wendy Anne Hayes Veronika Marie Kirchner Jillian Louise Webster Catherine Seut Yhoke Choong Eva Kipen Sew Kee Chang Merryn Lee Wild Guineva Joan Protheroe Wilson Tamara Gitanjali Weerasinghe Shiau Tween Low Pieta Louise Collins Lin-Lin Su Bee Ngo Lau Katherine Adele Scott Man Yuk Ho Minh Ha Nguyen Alexandra Stanislavsky Sally Lynette Quill Ellisa Ann McFarlane Helen Wodak Julia Taub 1971 Mary Louise Holland Daina Jolanta Kirkland Judith Mary Williams Monica Esther Cooper Sara Kremer Min Li Chong Debra Anne Wilson Anita Estelle Wluka Julie Nayleen Whitehead Helen Maroulis Megan Ann Cooney Jane Rosita Tam Cynthia Siu Wai Lau Christine Sierakowski Ingrid Ruth Horner Gaurie Palnitkar Kate Amanda Stanton Nomathemba Raphaka Sarah Louise McGuinness Mary Elizabeth Xipell Elizabeth Ann Tomlinson Adrienne Ila Elizabeth Anderson Anne Margeret Howard Esther Maria Langenegger Jean Lee Woo Debra Anne Crouch Shanti -

International Terrorist Organization "Islamic State": History, Contemporaneity, Future
VLADISLAV KRASINSKY VLADISLAV MASHKO International terrorist organization "Islamic State": history, contemporaneity, future Moscow 2017 Authors Krasinsky Vladislav Vyacheslavovich - Doctor of Law, colonel, expert on the problems of terrorism and national security. Member of the section on international electoral cooperation under the Central Electoral Commission of Russian Federation and the expert group of international anti-extremist cooperation under the Ministry of Foreign Affairs. Author of over 200 scientific, analytical and methodical judicial publications. Mashko Vladislav Valerevich - Candidate of Historical Sciences, Associate Professor of the Russian State Humanitarian University. Author of more than 20 scientific and educational works. Reviewers: Damaskin Oleg Valerevich - Doctor of Law, leading researcher of the Border Academy of the Federal Security Service of Russia, Professor, Honored Lawyer of the Russian Federation Aleshin Vladimir Vasilievich – Doctor of Law, Deputy Head of the Legal Department of the Council of Federation Staff Krasinsky V.V, Mashko V.V. International terrorist organization "Islamic State": history, contemporaneity, future. Moscow., 2017. ISBN 978-5-16-012878-8 (print) ISBN 978-5-16-105741-4 (online) This monograph is a comprehensive study of the activities of the international terrorist organization "Islamic State", which analyzes the history of its emergence, organizational structure, tactics of activity, participation of foreign militants in the ranks of a terrorist organization, the efforts of the world community, including Russia, in combating it, etc. key questions. With reference to the "Islamic state", the authors give recommendations on counteracting the spread of ideological concepts of terrorism in the Russian Federation. The book is intended for civil servants, law enforcement officers, faculty members, media representatives, will be of interest to a wide range of readers. -

World Service Listings for 24 – 30 April 2021
World Service Listings for 24 – 30 April 2021 Page 1 of 16 SATURDAY 24 APRIL 2021 Six Chinese passengers were among the survivors of the He claims to have “cured” thousands of Covid-19 patients Titanic, only to be vilified and refused entry to the United through diet alone and has set up a course where followers can SAT 01:00 BBC News (w172xzjh4r7j25s) States. Their stories were lost from history, but have been pay to learn his methods. We challenge his bogus claims and The latest five minute news bulletin from BBC World Service. pieced together in a new documentary, The Six. Zhaoyin Feng uncover new details about the death of one of his followers. of BBC Chinese has spoken to the American-born son of one of the six. Presenter: Mike Wendling SAT 01:06 Business Matters (w172xvq90h4ffhh) Reporter: Reha Kansara Australia and New Zealand pause travel bubble Lebanon's Fattoush Index Producer: Ed Main Lebanon has a new way of measuring the rapidly rising cost of With reporting by: Shruti Menon, BBC Reality Check, Delhi New Zealand has paused its newly opened travel bubble with living. It’s called the Fattoush Index - fattoush is a traditional Australia following a COVID-19 outbreak in its larger Lebanese salad, as well as a staple for Muslims breaking their neighbour. The decision came after Western Australia fast during Ramadan. BBC Arabic's Carine Torbey explains the SAT 05:50 More or Less (w3ct2djv) announced that the regions of Perth and Peel were entering a findings, and the legend of the origins of this salad. -

AA-Postscript 2.Qxp:Layout 1
WEDNESDAY, JUNE 29, 2016 Cameron faces EU music after Israel causes summer water shortages for Palestinians shock Brexit vote Page 8 Page 10 QAA, Lebanon: Lebanese Christian women hold weapons as residents of this Christian village near Lebanon’s border with war-ravaged Syria secure the area yesterday after two waves of suicide bombings struck the village, killing and wounding several people. —AFP Lebanon fearing more attacks Interior minister says attackers came from Syria, not camps BEIRUT/QAA, Lebanon: The Lebanese Local authorities imposed curfews Show of Force government warned yesterday of a on Syrian refugees in the area following “The whole village is mobilizing. heightened terrorist threat after eight sui- the attacks. The Lebanese army said it Everyone - men and women - are sit- cide bombers targeted a Christian village had mounted dawn raids on Syrian ting in front of their homes to protect at the border with Syria, the latest refugee camps, detaining 103 people them after the terror that we lived yes- spillover of its conflict into Lebanon. The for being illegally present in the coun- terday,” said local official Mansur Saad. village of Qaa was targeted on Monday in try. The majority of Syrian refugees have One man with silver-grey hair and clad two waves of suicide attacks that killed no legal status in Lebanon due to the in a black vest poured himself a small five people. The first group of bombers complications and costs of obtaining or cup of coffee, his assault rifle lying in attacked before dawn and the second lat- renewing residency rights under rules his lap.