Mobile Malware Evolution
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Mobile Telemedicine and Wireless Remote Monitoring Applications
İSTANBUL TECHNICAL UNIVERSITY INSTITUTE OF SCIENCE AND TECHNOLOGY MOBILE TELEMEDICINE AND WIRELESS REMOTE MONITORING APPLICATIONS M.Sc. Thesis by Taner SOYUGENÇ, B.Sc. Department : Electronics and Communication Engineering Programme : Biomedical Engineering NOVEMBER 2006 PREFACE In this project, my main goal is to implement a mobile sample application by defining the related global standards for telemedicine. The work is focused on recommendations of technology associated with a feasibility study. First of all, I would like to thank Assoc. Prof. Dr. Selçuk PAKER for his valuable advice, support and encouragement to accomplish the project. Besides, I would like to thank my family who is always with me giving support at every step of my life. November 2006 Taner SOYUGENÇ iii CONTENTS ACRONYMS vi LIST OF TABLES viii LIST OF FIGURES ix SUMMARY xi ÖZET xii 1. INTRODUCTION 1 1.1. Technology Overview 2 1.1.1. Communication Infrastructure 5 1.1.2. Overview of GSM-GPRS 6 1.1.2.1. Brief History of GSM 8 1.1.2.2. GPRS 12 1.1.3. Mobile Solutions 14 1.1.4. Wireless Medical Sensors 15 1.2. Aim of the Project 16 2. WORLDWIDE APPLICATIONS, VENDORS AND STANDARDS 18 2.1. Available Products 19 2.1.1. ECG 19 2.1.2. Pulse Oximeter 20 2.1.3. Blood Pressure Sensor 23 2.1.4. Various Sensor Brands 24 2.1.5. Advanced Research 27 2.1.6. Home Care Monitoring Systems 31 2.2. Medical Information Standards and Organizations 35 2.2.1. ASTM 39 2.2.2. CEN/TC251 Health Informatics 39 2.2.3. -

User Gu Id E
UserGuide_test 1/26/04 1:04 PM Page 1 Thank you for purchasing your new Nokia phone. We’re here for you! www.nokiahowto.com Learn how to use your new Nokia phone. www.nokia.com/us Get answers to your questions. Register your phone’s limited warranty so we can better serve your needs! Nokia Inc. 7725 Woodland Center Boulevard, Suite 150, Tampa FL 33614 . Phone: 1.888.NOKIA.2U (1.888.665.4228) Fax: 1.813.249.9619 . Text Telephone/Telecommunication Device User Guide for the Deaf (TTY/TDD) Users: 1.800.24.NOKIA (1.800.246.6542) PRINTED IN CANADA 6620.ENv1_9310640.book Page i Wednesday, May 5, 2004 2:44 PM Nokia 6620 User Guide Phone information Numbers Where is the number? My number Wireless service provider Voice mail number Wireless service provider Wireless provider’s number Wireless service provider Provider’s customer care Wireless service provider Label on back of phone Model number (under battery) Label on back of phone Type number (under battery) Label on back of phone IMEI number (under battery) 6620.ENv1_9310640.book Page ii Wednesday, May 5, 2004 2:44 PM NOTES 6620.ENv1_9310640.book Page iii Wednesday, May 5, 2004 2:44 PM LEGAL INFORMATION DECLARATION OF CONFORMITY We, NOKIA CORPORATION declare under our sole responsibility that the product NHL-12 is in conformity with the provisions of the following Council Directive: 1999/5/EC. A copy of the Declaration of Conformity can be found at http://www.nokia.com/phones/declaration_of_conformity 168 PART NO. 9310640, ISSUE NO. 1 Copyright © 2004 Nokia. -

500 Kilobits Per Second (Kbps)
* IAMDAT 3D Bowling (JAMDAT) ~ $2.49 monthly access or $8.99 for unlimited use purchase V CAST'S array of hot new multimedia programming is located in the Get It Now virtual store. Customers can access video from favorite news, sports and entertainment providers in the getVIDEO shopping aisle from the Get It Now main menu. Video tiips will be refreshed daily throughout the day and will be between 30 seconds and three minutes in length. Customers can check out new cutting-edge 3D games in the getGAMES aisle. V CAST also gives customers monthly access and unlimited airtime to browse applications in the other familiar Get It Now shopping aisles ~ such as getTONES and getGOlNG - but application download fees still apply. "The value of V CAST comes not only from the quality of the experience our network provides, but also from the compelling content line-up we've assembled," said John Stratton, Verizon Wireless vice president and chief marketing officer. "Our list of content providers reads like a who's who of the news, sports, entertainment and game industries. We are offering Verizon Wireless customers a wealth of popular content in the palm of their hands at an affordable price." EV-DO 36 Network V CAST runs on the Verizon Wireless 3G EV-DO network that is now available In more than 30 markets across the country. The Verizon Wireless 3G EV-DO network Initially launched commercially with BroadbandAccess wireless Internet access service for business customers and mobile professionals. BroadbandAccessboasts average user download speeds of 300-500 kilobits per second (kbps). -
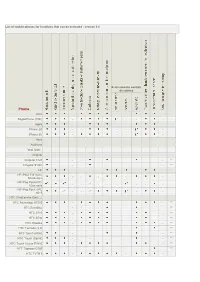
List of Mobile Phones for Functions That Can Be Activated - Version 5.4
List of mobile phones for functions that can be activated - version 5.4 Scaricamento contatti da rubrica Phone Amoi SkypePhone (TRE) - - - - Apple iPhone 2G - - - - - iPhone 3G - - - - Asus Audiovox Vedi Qtek... Cingular Cingular 8125 - - - ** Cingular SYNC - - - ** HP HP iPAQ 514 Voice - - - - - Messenger HP iPaq Pocket PC - - -* - - - - - - 63xx serie HP iPaq Pocket PC -* - - -* - - 6515 HTC (Vedi anche Qtek....) HTC Advantage X7500 - - ** HTC Excalibur - - - ** HTC S710 - - ** HTC S730 - - ** HTC Shadow - - ** HTC Tornado (2.0) ** HTC Touch (Alltel) - - - ** HTC Touch (Sprint) - - - - ** HTC Touch Cruise P3650 - - ** HTC Typhoon C500 ** HTC TyTN II - - - HTC Wizard ** Qteck/HTC P3300 - - - - - - - Qteck/HTC Touch Diamond - - - i-Mate Vedi Qtek LG LG CU500 - - ** LG KE850 - - - - - - - - LG KE850 Prada - - - ** LG KG800 (Chocolate) - - - - - - - - ** LG KS20 - - ** LG KU990 - - - ** LG KU800 - - - - - - - - - ** LG Shine (CU720) N N N ** LG Trax (CU575) N N N N N N ** LG U8550 - - - - -* LG U880 - - - - - - - - LG U900 - - - - - - - - Motorola Motorola A830/ - - - - A835 Motorola A1000 - - - - -* - Motorola A1200 Ming N ** Motorola E1000 - Motorola E398 - - - Motorola i615 N ** Motorola i880 N ** Motorola KRZR K1 - Motorola MPX220 - - - - - - Motorola RAZR2V9/ KRZR K3/ RAZR V3xx/ RAZR - MaxxV6 Motorola RAZR V3i/V3r ** Motorola RAZR V3t ** Motorola RAZR V6 Maxx ** Motorola RIZR Z3 - Motorola ROKR E6 N N ** Motorola Sidekick Slide N N N N ** Motorola SLVR L6 - Motorola SLVR L7 - Motorola U9 N N ** Motorola RAZR V3 - - Motorola V8 - - Motorola -

SYMBIAN OS Embedded Operating System
Adamson University 900 San Marcelino st., Ermita, Manila 1000 SYMBIAN OS Embedded Operating System Operating Systems Prof. Antonette Daligdig Atienza, Lemuel Jay Bacarra, Dan Paolo Dulatre, Michael Angelo Jimenez, John Edward Llorca, Bryalle November 2009 Table of Contents I Introduction II Origin/History III Characteristics III.a. Processing III.b. Memory Management III.c. I/O : Input/Output IV Features V Strengths VI Weakness VII Example of Applications where the OS is being used VIII Screenshots I Introduction More than 90% of the CPUs in the world are not in desktops and notebooks. They are in embedded systems like cell phones, PDAs, digital cameras, camcorders, game machines, iPods, MP3 players, CD players, DVD recorders, wireless routers, TV sets, GPS receivers, laser printers, cars, and many more consumer products. Most of these use modern 32-bit and 64-bit chips, and nearly all of them run a full-blown operating system. Taking a close look at one operating system popular in the embedded systems world: Symbian OS, Symbian OS is an operating system that runs on mobile ‘‘smartphone’’ platforms from several different manufacturers. Smartphones are so named because they run fully-featured operating systems and utilize the features of desktop computers. Symbian OS is designed so that it can be the basis of a wide variety of smartphones from several different manufacturers. It was carefully designed specifically to run on smartphone platforms: general-purpose computers with limited CPU, memory and storage capacity, focused on communication. Our discussion of Symbian OS will start with its history. We will then provide an overview of the system to give an idea of how it is designed and what uses the designers intended for it. -

Seeing-Is-Believing: Using Camera Phones for Human-Verifiable
Seeing-Is-Believing: Using Camera Phones for Human-Verifiable Authentication ∗ Jonathan M. McCune Adrian Perrig Michael K. Reiter Carnegie Mellon University {jonmccune, perrig, reiter}@cmu.edu Abstract As camera-equipped mobile phones rapidly approach ubiquity, these devices become a naturally convenient Current mechanisms for authenticating communica- platform for security applications that can be deployed tion between devices that share no prior context are in- quickly and easily to millions of users. Today’s mo- convenient for ordinary users, without the assistance of bile phones increasingly feature Internet access and come a trusted authority. We present and analyze Seeing-Is- equipped with cameras, high-quality displays, and short- Believing, a system that utilizes 2D barcodes and camera- range Bluetooth wireless radios. They are powerful phones to implement a visual channel for authentica- enough to perform secure public key cryptographic op- tion and demonstrative identification of devices. We ap- erations in under one second. ply this visual channel to several problems in computer We propose to use the camera on a mobile phone as security, including authenticated key exchange between anewvisual channel to achieve demonstrative identifica- devices that share no prior context, establishment of a tion of communicating devices formerly unattainable in an trusted path for configuration of a TCG-compliant com- intuitive way. We term this approach Seeing-Is-Believing puting platform, and secure device configuration in the (SiB). In SiB, one device uses its camera to take a snapshot context of a smart home. of a barcode encoding cryptographic material identifying, e.g., the public key of another device. We term this a vi- sual channel. -

Photoacute Users Guide
PhotoAcute Users Guide PhotoAcute Users Guide Introduction................................................................................................................ 2 Basic Principles ........................................................................................................... 2 Snapping several images .......................................................................................... 2 Processing images ................................................................................................... 2 Views...................................................................................................................... 2 Snapping.................................................................................................................... 3 Snapped Images ......................................................................................................... 3 Processing .................................................................................................................. 4 Processing Options................................................................................................... 4 Processing Results ................................................................................................... 4 Photo Album............................................................................................................... 5 Settings...................................................................................................................... 5 Support..................................................................................................................... -

Flexible User Interface - FLUSI
School of Mathematics and Systems Engineering Reports from MSI - Rapporter från MSI Flexible User Interface - FLUSI Jan Conrad Jan MSI Report 06010 2006 Växjö University ISSN 1650-2647 SE-351 95 VÄXJÖ ISRN VXU/MSI/DA/E/--06010/--SE Flexible User Interface FLUSI Jan Conrad Abstract The cellular phone network has been increasing rapidly during the last years. For many people the mobile phone has become an every day gadget with a wide performance and functional range. The usage of technologies like GPRS, HSCSD, EDGE and UMTS as well as the bandwidth of networks and consequently the connectivity of the phones has also increased persistently. Coming along with that, three technologies, which are ubiquitous or pervasive computing, mobile and wireless networks and location-based technologies, are making rapid progress. The aim of this thesis is to offer an architecture for a location-based user interface in the intersection of the three technologies mentioned above. The system should work with a minimum of special hardware requirement. Not to overload the user with information, the user interface should be adaptable, context-aware and location-based. The context-data should remain extendible and adaptable. II Acknowledgements I would like to thank some people who helped and supported us in writing my thesis. First, I am grateful to Jesper Andersson. He has been a continual support. He was always available for me and inspired me with many relevant and useful ideas and critics. Secondly I thank Marcus Edvinsson who introduced me to the XAP-System. Last but not the least I thank Mathias Hedenborg and Maria Karlsson who made this thesis possible. -
Smartphones Image Datamatrix Barcodes
site-specific recordkeepingTM Smartphones Image DataMatrix Barcodes ScoringAg.com, a Division of ScoringSystem, Inc., 1800 2nd Street, Suite 760, Sarasota, Florida 34236 USA Phone: +1-941-330-1140 Fax: +1-941-330-1255 Email: [email protected] site-specific recordkeepingTM “Smartphones” Image DataMatrix Barcodes, Access Site-Specific Records in Real Time Leading-edge wireless technology, in conjunction with 2D DataMatrix barcodes, now enables access of Web-based site-specific records in real time at the location where data is actually collected. Throughout the food supply chain, a variety of products undergo a highly organized sequence of processing stages by a number of companies and individuals at specific locations during time periods ranging from a few days to many years. At these locations, identified by their registered PIDCs (Premises ID Codes), all types of entities and products are born, bred, planted, raised, fed, harvested, transported, processed, packaged, sold, etc. In order to track these stages properly, from Point-to-Point each location and each item must be positively identified and labeled to allow the collection, storage, and reporting of critical processing data. One method of labeling locations and products, so that data may be collected and retrieved easily, involves using a 2D barcode known as the DataMatrix. The barcode graphically encodes a Web page’s url (Internet address), and the barcode’s image is printed on the attached to the product or associated with a location. Using the photographic imaging capability of a Symbian Series 60 “smartphone,” such as the Nokia series, the DataMatrix barcode is captured; and a special program, called Semacode, interprets it in real time. -

Symbian Mobile Programming
Symbian Mobile Programming G.Rossetti & A.Schneider HTI Biel 2005 - 2007 Acknowledgments This course is based on our collective experiences over the last years, we have worked on Symbian mobile programming. We are indebted to all the people, that made our work fun and helped us reaching the insights that fill this course. We would also like to thank our employers for providing support and accommo- dation to teach this lecture. These are Swisscom Innovations and SwissQual AG. CONTENTS Contents 1 Course Overview 1 1.1 Lecturers . 1 1.2 Examples . 1 1.3 Motivation . 1 1.4 Course contents . 2 2 Introduction to Symbian 3 2.1 History . 3 2.1.1 EPOC OS Releases 1-4 . 3 2.1.2 Symbian 5 . 3 2.1.3 Symbian 6 . 3 2.1.4 Symbian 7 . 3 2.1.5 Symbian 8 . 4 2.1.6 Symbian 9 . 5 2.2 Symbian OS Architecture . 6 2.3 Instruction Sets . 6 2.4 IDEs . 7 2.5 SDKs . 7 2.6 Useful links . 8 2.6.1 Symbian OS manufacturer . 8 2.6.2 Symbian OS licensees . 8 2.6.3 3th party links . 8 2.7 Lecture Focus . 8 3 Framework 9 3.1 Classes . 9 3.2 Launch sequence . 9 3.3 Basic Example . 10 3.3.1 Project File . 10 3.3.2 Source- and Header-Files . 11 3.3.3 Building Project . 16 3.3.4 Creating Installation File . 17 4 Symbian Types 19 4.1 Class Types . 19 4.1.1 T Classes . 19 4.1.2 C Classes . -

1 Introduction
SuperDVR & TD Series Cards 1 1 INTRODUCTION................................... 8 1.1 Summarization..............................................8 1.2 System Requirements .................................10 1.2.1 TD3004~TD3216 series cards system requirements ·················10 1.2.2 TD3316 system requirements··················································· 11 1.2.3TD3101 、3104 USB cards system requirements·······················12 1.3 System Specifications .................................13 2 HARDWARE INSTALLATION ............ 14 2.1 Video Capture Card Hardware.................14 TD3004 Card Hardware ···································································14 TD3008 Card Hardware ···································································15 TD3016 Card Hardware ···································································16 TD3116 Card Hardware ···································································18 TD3216 Card Hardware ···································································19 TD3316 Card Hardware ···································································20 TD3101 USB Card Hardware···························································23 TD3104 USB Card Hardware···························································24 Alarm Board Hardware ····································································25 Connect Audio Signal·······································································26 SuperDVR & TD Series Cards 2 2.2 Install Video Capture Card Driver -

Connectors & Ports
http://pinouts.ru/connector/index_conn_2_6.shtml Ports & Connectors The various connectors and ports on the computer allow it to communicate with the many different devices and peripherals attached. Because there are so many cables and cords attached to the back of the computer, and so many different types of connectors, it often seems a little intimidating to the newer user. Although there are some devices which may use the same connector or port, the individual devices and their cords can only physically attach to one certain type of connector; so don't feel nervous about hooking your system together. There's really no way you can do any harm to your computer just by hooking it up, as long as you follow a few common sense rules: The first thing to know is the difference between a male and female connector. The male connector fits inside the female connector. If the connector has pins protruding from it, its a male connector. If the connector has holes for the pins to fit into, then its a female connector. When you hook something up to your computer, the male and female connectors are hooked together. The connectors on the back of your computer are called input/output ports (i/o ports) or communication ports. The second thing you should remember is that when you join a connector to a port, they must have the same shape and the same number of pins or holes. In other words, a square peg won't fit into a round hole, and its not wise to try to jam fifteen pins into nine holes (part of the 'common sense' thing I was talking about).Which brings us to another very important point, never force anything.