Final Report2.Pdf
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
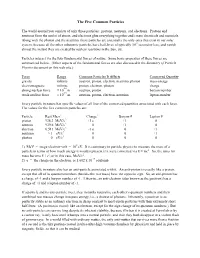
The Five Common Particles
The Five Common Particles The world around you consists of only three particles: protons, neutrons, and electrons. Protons and neutrons form the nuclei of atoms, and electrons glue everything together and create chemicals and materials. Along with the photon and the neutrino, these particles are essentially the only ones that exist in our solar system, because all the other subatomic particles have half-lives of typically 10-9 second or less, and vanish almost the instant they are created by nuclear reactions in the Sun, etc. Particles interact via the four fundamental forces of nature. Some basic properties of these forces are summarized below. (Other aspects of the fundamental forces are also discussed in the Summary of Particle Physics document on this web site.) Force Range Common Particles It Affects Conserved Quantity gravity infinite neutron, proton, electron, neutrino, photon mass-energy electromagnetic infinite proton, electron, photon charge -14 strong nuclear force ≈ 10 m neutron, proton baryon number -15 weak nuclear force ≈ 10 m neutron, proton, electron, neutrino lepton number Every particle in nature has specific values of all four of the conserved quantities associated with each force. The values for the five common particles are: Particle Rest Mass1 Charge2 Baryon # Lepton # proton 938.3 MeV/c2 +1 e +1 0 neutron 939.6 MeV/c2 0 +1 0 electron 0.511 MeV/c2 -1 e 0 +1 neutrino ≈ 1 eV/c2 0 0 +1 photon 0 eV/c2 0 0 0 1) MeV = mega-electron-volt = 106 eV. It is customary in particle physics to measure the mass of a particle in terms of how much energy it would represent if it were converted via E = mc2. -

The Particle World
The Particle World ² What is our Universe made of? This talk: ² Where does it come from? ² particles as we understand them now ² Why does it behave the way it does? (the Standard Model) Particle physics tries to answer these ² prepare you for the exercise questions. Later: future of particle physics. JMF Southampton Masterclass 22–23 Mar 2004 1/26 Beginning of the 20th century: atoms have a nucleus and a surrounding cloud of electrons. The electrons are responsible for almost all behaviour of matter: ² emission of light ² electricity and magnetism ² electronics ² chemistry ² mechanical properties . technology. JMF Southampton Masterclass 22–23 Mar 2004 2/26 Nucleus at the centre of the atom: tiny Subsequently, particle physicists have yet contains almost all the mass of the discovered four more types of quark, two atom. Yet, it’s composite, made up of more pairs of heavier copies of the up protons and neutrons (or nucleons). and down: Open up a nucleon . it contains ² c or charm quark, charge +2=3 quarks. ² s or strange quark, charge ¡1=3 Normal matter can be understood with ² t or top quark, charge +2=3 just two types of quark. ² b or bottom quark, charge ¡1=3 ² + u or up quark, charge 2=3 Existed only in the early stages of the ² ¡ d or down quark, charge 1=3 universe and nowadays created in high energy physics experiments. JMF Southampton Masterclass 22–23 Mar 2004 3/26 But this is not all. The electron has a friend the electron-neutrino, ºe. Needed to ensure energy and momentum are conserved in ¯-decay: ¡ n ! p + e + º¯e Neutrino: no electric charge, (almost) no mass, hardly interacts at all. -

Lepton Flavor and Number Conservation, and Physics Beyond the Standard Model
Lepton Flavor and Number Conservation, and Physics Beyond the Standard Model Andr´ede Gouv^ea1 and Petr Vogel2 1 Department of Physics and Astronomy, Northwestern University, Evanston, Illinois, 60208, USA 2 Kellogg Radiation Laboratory, Caltech, Pasadena, California, 91125, USA April 1, 2013 Abstract The physics responsible for neutrino masses and lepton mixing remains unknown. More ex- perimental data are needed to constrain and guide possible generalizations of the standard model of particle physics, and reveal the mechanism behind nonzero neutrino masses. Here, the physics associated with searches for the violation of lepton-flavor conservation in charged-lepton processes and the violation of lepton-number conservation in nuclear physics processes is summarized. In the first part, several aspects of charged-lepton flavor violation are discussed, especially its sensitivity to new particles and interactions beyond the standard model of particle physics. The discussion concentrates mostly on rare processes involving muons and electrons. In the second part, the sta- tus of the conservation of total lepton number is discussed. The discussion here concentrates on current and future probes of this apparent law of Nature via searches for neutrinoless double beta decay, which is also the most sensitive probe of the potential Majorana nature of neutrinos. arXiv:1303.4097v2 [hep-ph] 29 Mar 2013 1 1 Introduction In the absence of interactions that lead to nonzero neutrino masses, the Standard Model Lagrangian is invariant under global U(1)e × U(1)µ × U(1)τ rotations of the lepton fields. In other words, if neutrinos are massless, individual lepton-flavor numbers { electron-number, muon-number, and tau-number { are expected to be conserved. -

The Masses of the First Family of Fermions and of the Higgs Boson Are Equal to Integer Powers of 2 Nathalie Olivi-Tran
The masses of the first family of fermions and of the Higgs boson are equal to integer powers of 2 Nathalie Olivi-Tran To cite this version: Nathalie Olivi-Tran. The masses of the first family of fermions and of the Higgs boson are equal to integer powers of 2. QCD14, S.Narison, Jun 2014, MONTPELLIER, France. pp.272-275, 10.1016/j.nuclphysbps.2015.01.057. hal-01186623 HAL Id: hal-01186623 https://hal.archives-ouvertes.fr/hal-01186623 Submitted on 27 Aug 2015 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. See discussions, stats, and author profiles for this publication at: http://www.researchgate.net/publication/273127325 The masses of the first family of fermions and of the Higgs boson are equal to integer powers of 2 ARTICLE · JANUARY 2015 DOI: 10.1016/j.nuclphysbps.2015.01.057 1 AUTHOR: Nathalie Olivi-Tran Université de Montpellier 77 PUBLICATIONS 174 CITATIONS SEE PROFILE Available from: Nathalie Olivi-Tran Retrieved on: 27 August 2015 The masses of the first family of fermions and of the Higgs boson are equal to integer powers of 2 a, Nathalie Olivi-Tran ∗ aLaboratoire Charles Coulomb, UMR CNRS 5221, cc. -

Introduction to Subatomic- Particle Spectrometers∗
IIT-CAPP-15/2 Introduction to Subatomic- Particle Spectrometers∗ Daniel M. Kaplan Illinois Institute of Technology Chicago, IL 60616 Charles E. Lane Drexel University Philadelphia, PA 19104 Kenneth S. Nelsony University of Virginia Charlottesville, VA 22901 Abstract An introductory review, suitable for the beginning student of high-energy physics or professionals from other fields who may desire familiarity with subatomic-particle detection techniques. Subatomic-particle fundamentals and the basics of particle in- teractions with matter are summarized, after which we review particle detectors. We conclude with three examples that illustrate the variety of subatomic-particle spectrom- eters and exemplify the combined use of several detection techniques to characterize interaction events more-or-less completely. arXiv:physics/9805026v3 [physics.ins-det] 17 Jul 2015 ∗To appear in the Wiley Encyclopedia of Electrical and Electronics Engineering. yNow at Johns Hopkins University Applied Physics Laboratory, Laurel, MD 20723. 1 Contents 1 Introduction 5 2 Overview of Subatomic Particles 5 2.1 Leptons, Hadrons, Gauge and Higgs Bosons . 5 2.2 Neutrinos . 6 2.3 Quarks . 8 3 Overview of Particle Detection 9 3.1 Position Measurement: Hodoscopes and Telescopes . 9 3.2 Momentum and Energy Measurement . 9 3.2.1 Magnetic Spectrometry . 9 3.2.2 Calorimeters . 10 3.3 Particle Identification . 10 3.3.1 Calorimetric Electron (and Photon) Identification . 10 3.3.2 Muon Identification . 11 3.3.3 Time of Flight and Ionization . 11 3.3.4 Cherenkov Detectors . 11 3.3.5 Transition-Radiation Detectors . 12 3.4 Neutrino Detection . 12 3.4.1 Reactor Neutrinos . 12 3.4.2 Detection of High Energy Neutrinos . -

Neutrino Opacity I. Neutrino-Lepton Scattering*
PHYSICAL REVIEW VOLUME 136, NUMBER 4B 23 NOVEMBER 1964 Neutrino Opacity I. Neutrino-Lepton Scattering* JOHN N. BAHCALL California Institute of Technology, Pasadena, California (Received 24 June 1964) The contribution of neutrino-lepton scattering to the total neutrino opacity of matter is investigated; it is found that, contrary to previous beliefs, neutrino scattering dominates the neutrino opacity for many astro physically important conditions. The rates for neutrino-electron scattering and antineutrino-electron scatter ing are given for a variety of conditions, including both degenerate and nondegenerate gases; the rates for some related reactions are also presented. Formulas are given for the mean scattering angle and the mean energy loss in neutrino and antineutrino scattering. Applications are made to the following problems: (a) the detection of solar neutrinos; (b) the escape of neutrinos from stars; (c) neutrino scattering in cosmology; and (d) energy deposition in supernova explosions. I. INTRODUCTION only been discussed for the special situation of electrons 13 14 XPERIMENTS1·2 designed to detect solar neu initially at rest. · E trinos will soon provide crucial tests of the theory In this paper, we investigate the contribution of of stellar energy generation. Other neutrino experiments neutrino-lepton scattering to the total neutrino opacity have been suggested as a test3 of a possible mechanism of matter and show, contrary to previous beliefs, that for producing the high-energy electrons that are inferred neutrino-lepton scattering dominates the neutrino to exist in strong radio sources and as a means4 for opacity for many astrophysically important conditions. studying the high-energy neutrinos emitted in the decay Here, neutrino opacity is defined, analogously to photon of cosmic-ray secondaries. -

Tritium Beta Decay and the Search for Neutrino Mass
ritium Beta Decay and the Search for Neutrino Mass Tritium Beta Decay and the Search for Neutrino Mass eutrinos have been around, that the decay also produced a second neutrino mass. A short lifetime literally, since the beginning unseen particle, now called the means atoms decay more rapidly, Nof time. In the sweltering electron neutrino. The neutrino would making more data available. moments following the Big Bang, share the energy released in the decay A wonderful accident of nature, tri- neutrinos were among the first particles with the daughter atom and the tium (a hydrogen atom with two extra Tritium Beta Decay and the Search to emerge from the primordial sea. electron. The electrons would emerge neutrons) is a perfect source by both A minute later, the universe had cooled with a spectrum of energies. of these measures: it has a reasonably for Neutrino Mass enough for protons and neutrons In 1934, Enrico Fermi pointed out short lifetime (12.4 years) and releases to bind together and form atomic that, if the neutrino had mass, it would only 18.6 kilo-electron-volts (keV) Thomas J. Bowles and R. G. Hamish Robertson as told to David Kestenbaum nuclei. Ten or twenty billion years subtly distort the tail of this spectrum. as it decays into helium-3. later—today—the universe still teems When an atom undergoes beta decay, it Additionally, its molecular structure with these ancient neutrinos, which produces a specific amount of available is simple enough that the energy outnumber protons and neutrons by energy that is carried away by the spectrum of the decay electrons can roughly a billion to one. -

Neutrino Vs Antineutrino Lepton Number Splitting
Introduction to Elementary Particle Physics. Note 18 Page 1 of 5 Neutrino vs antineutrino Neutrino is a neutral particle—a legitimate question: are neutrino and anti-neutrino the same particle? Compare: photon is its own antiparticle, π0 is its own antiparticle, neutron and antineutron are different particles. Dirac neutrino : If the answer is different , neutrino is to be called Dirac neutrino Majorana neutrino : If the answer is the same , neutrino is to be called Majorana neutrino 1959 Davis and Harmer conducted an experiment to see whether there is a reaction ν + n → p + e - could occur. The reaction and technique they used, ν + 37 Cl e- + 37 Ar, was proposed by B. Pontecorvo in 1946. The result was negative 1… Lepton number However, this was not unexpected: 1953 Konopinski and Mahmoud introduced a notion of lepton number L that must be conserved in reactions : • electron, muon, neutrino have L = +1 • anti-electron, anti-muon, anti-neutrino have L = –1 This new ad hoc law would explain many facts: • decay of neutron with anti-neutrino is OK: n → p e -ν L=0 → L = 1 + (–1) = 0 • pion decays with single neutrino or anti-neutrino is OK π → µ-ν L=0 → L = 1 + (–1) = 0 • but no pion decays into a muon and photon π- → µ- γ, which would require: L= 0 → L = 1 + 0 = 1 • no decays of muon with one neutrino µ- → e - ν, which would require: L= 1 → L = 1 ± 1 = 0 or 2 • no processes searched for by Davis and Harmer, which would require: L= (–1)+0 → L = 0 + 1 = 1 But why there are no decays µµµ →→→ e γγγ ? 2 Splitting lepton numbers 1959 Bruno Pontecorvo -

Arxiv:1210.3065V1
Neutrino. History of a unique particle S. M. Bilenky Joint Institute for Nuclear Research, Dubna, R-141980, Russia TRIUMF 4004 Wesbrook Mall, Vancouver BC, V6T 2A3 Canada Abstract Neutrinos are the only fundamental fermions which have no elec- tric charges. Because of that neutrinos have no direct electromagnetic interaction and at relatively small energies they can take part only 0 in weak processes with virtual W ± and Z bosons (like β-decay of nuclei, inverse β processν ¯ + p e+n, etc.). Neutrino masses are e → many orders of magnitude smaller than masses of charged leptons and quarks. These two circumstances make neutrinos unique, special par- ticles. The history of the neutrino is very interesting, exciting and instructive. We try here to follow the main stages of the neutrino his- tory starting from the Pauli proposal and finishing with the discovery and study of neutrino oscillations. 1 The idea of neutrino. Pauli Introduction The history of the neutrino started with the famous Pauli letter. The exper- imental data ”forced” Pauli to assume the existence of a new particle which later was called neutrino. The hypothesis of the neutrino allowed Fermi to build the first theory of the β-decay which he considered as a process of a quantum transition of a neutron into a proton with the creation of an electron-(anti)neutrino pair. During many years this was the only experi- arXiv:1210.3065v1 [hep-ph] 10 Oct 2012 mentally studied process in which the neutrino takes part. The main efforts were devoted at that time to the search for a Hamiltonian of the interaction which governs the decay. -

Neutrino-Electron Scattering: General Constraints on Z 0 and Dark Photon Models
Neutrino-Electron Scattering: General Constraints on Z 0 and Dark Photon Models Manfred Lindner,a Farinaldo S. Queiroz,b Werner Rodejohann,a Xun-Jie Xua aMax-Planck-Institut für Kernphysik, Saupfercheckweg 1, 69117 Heidelberg, Germany bInternational Institute of Physics, Federal University of Rio Grande do Norte, Campus Univer- sitário, Lagoa Nova, Natal-RN 59078-970, Brazil E-mail: [email protected], [email protected], [email protected], [email protected] Abstract. We study the framework of U(1)X models with kinetic mixing and/or mass mixing terms. We give general and exact analytic formulas and derive limits on a variety of U(1)X models that induce new physics contributions to neutrino-electron scattering, taking into account interference between the new physics and Standard Model contributions. Data from TEXONO, CHARM-II and GEMMA are analyzed and shown to be complementary to each other to provide the most restrictive bounds on masses of the new vector bosons. In particular, we demonstrate the validity of our results to dark photon-like as well as light Z0 models. arXiv:1803.00060v1 [hep-ph] 28 Feb 2018 Contents 1 Introduction 1 2 General U(1)X Models2 3 Neutrino-Electron Scattering in U(1)X Models7 4 Data Fitting 10 5 Bounds 13 6 Conclusion 16 A Gauge Boson Mass Generation 16 B Cross Sections of Neutrino-Electron Scattering 18 C Partial Cross Section 23 1 Introduction The Standard Model provides an elegant and successful explanation to the electroweak and strong interactions in nature [1]. -

Neutrino Masses-How to Add Them to the Standard Model
he Oscillating Neutrino The Oscillating Neutrino of spatial coordinates) has the property of interchanging the two states eR and eL. Neutrino Masses What about the neutrino? The right-handed neutrino has never been observed, How to add them to the Standard Model and it is not known whether that particle state and the left-handed antineutrino c exist. In the Standard Model, the field ne , which would create those states, is not Stuart Raby and Richard Slansky included. Instead, the neutrino is associated with only two types of ripples (particle states) and is defined by a single field ne: n annihilates a left-handed electron neutrino n or creates a right-handed he Standard Model includes a set of particles—the quarks and leptons e eL electron antineutrino n . —and their interactions. The quarks and leptons are spin-1/2 particles, or weR fermions. They fall into three families that differ only in the masses of the T The left-handed electron neutrino has fermion number N = +1, and the right- member particles. The origin of those masses is one of the greatest unsolved handed electron antineutrino has fermion number N = 21. This description of the mysteries of particle physics. The greatest success of the Standard Model is the neutrino is not invariant under the parity operation. Parity interchanges left-handed description of the forces of nature in terms of local symmetries. The three families and right-handed particles, but we just said that, in the Standard Model, the right- of quarks and leptons transform identically under these local symmetries, and thus handed neutrino does not exist. -

Neutrino Physics
0 Neutrino Physics Zhi-zhong Xing ★ Neutrino’s history & lepton families (IHEP, Beijing) ★ Dirac & Majorana neutrino masses ★ Lepton flavor mixing & CP violation ★ Neutrino oscillation phenomenology ★ Seesaw & leptogenesis mechanisms ★ Extreme corners in the neutrino sky Lecture A @ the 2nd Asia-Europe-Pacific School of HEP, 11/2014, Puri, India Neutrinos everywhere 1 SM Properties: charge = 0 spin = ½ mass = 0 Big Bang speed = c neutrinos Galaxy Human Supernova Sun Earth Reactor Accelerator Neutrinos: witness and participant 1 in the evolution of the Universe 3 2 < 1% Some open questions 3 . the absolute mass scale? . the mass hierarchy? . the flavor desert? . leptonic CP violation? . the Majorana nature? . How many species? . cosmic background? . supernova & stellar ’s? . UHE cosmic ’s? . warm dark matter? . matter-antimatter asymmetry… Lecture A1 ★ Neutrinos from new physics ★ Interactions and discoveries ★ Flavors / families of leptons Beta decays in 1930 5 2-body Energy crisis = New physics ? decays J. Chadwick 1914/C. Ellis 1920-1927 What to do? Two ways out? 6 . giving up sth . adding in sth Niels Bohr Wolfgang Pauli (1930) Pauli put forward this idea in a letter instead of a paper….. Solvay 1933 7 Pauli gave a talk on his neutrino proposal in this congress. Fermi’s theory 8 Enrico Fermi assumed a new force for I will be remembered decay by combining 3 new concepts: for this paper. ------ Fermi in Italian ★ Pauli’s idea: neutrinos Alps, Christmas 1933 ★ Dirac’s idea: creation of particles ★ Heisenberg’s idea: isospin symmetry Fermi’s paper 9 This is Fermi’s best theoretical work! ---- C.N. Yang Published first in this journal and later in Z.