Sharing Experiments and Their Provenance
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
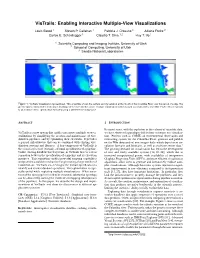
Vistrails: Enabling Interactive Multiple-View Visualizations
VisTrails: Enabling Interactive Multiple-View Visualizations Louis Bavoil 1 Steven P. Callahan 1 Patricia J. Crossno 3 Juliana Freire 2 Carlos E. Scheidegger 1 Claudio´ T. Silva 1,2 Huy T. Vo 1 1 Scientific Computing and Imaging Institute, University of Utah 2 School of Computing, University of Utah 3 Sandia National Laboratories Figure 1: VisTrails Visualization Spreadsheet. This ensemble shows the surface salinity variation at the mouth of the Columbia River over the period of a day. The green regions represent the fresh-water discharge of the river into the ocean. A single vistrail specification is used to construct this ensemble. Each cell corresponds to an instance of this specification executed using a different timestamp value. ABSTRACT 1 INTRODUCTION In recent years, with the explosion in the volume of scientific data, VisTrails is a new system that enables interactive multiple-view vi- we have observed a paradigm shift in how scientists use visualiza- sualizations by simplifying the creation and maintenance of visu- tion. Projects such as CORIE, an environmental observation and alization pipelines, and by optimizing their execution. It provides forecasting system for the Columbia River, generate and publish a general infrastructure that can be combined with existing visu- on the Web thousands of new images daily which depict river cir- alization systems and libraries. A key component of VisTrails is culation forecasts and hindcasts, as well as real-time sensor data.1 the visualization trail (vistrail), a formal specification of a pipeline. The growing demand for visualization has led to the development Unlike existing dataflow-based systems, in VisTrails there is a clear of new and freely available systems [14, 20, 24], which due to separation between the specification of a pipeline and its execution increased computational power, wide availability of inexpensive instances. -

Vistrails Documentation Release 1.7.0
VisTrails Documentation Release 1.7.0 University of Utah December 05, 2011 CONTENTS I Preliminary Pages1 1 Preface 3 1.1 Acknowledgements...........................................3 II An Introduction to VisTrails5 2 What Is VisTrails? 7 2.1 Important Features............................................7 2.2 Obtaining the software..........................................8 3 Getting Started 9 3.1 Installation................................................9 3.2 Quick Start................................................ 11 3.3 Manipulating VisTrails Files....................................... 11 3.4 VisTrails Basics............................................. 14 3.5 VisTrails Interaction........................................... 14 III Learning VisTrails By Example 17 4 Creating and Modifying Workflows 19 4.1 Working with Modules.......................................... 19 4.2 Adding and Deleting Modules...................................... 19 4.3 Connecting Modules........................................... 21 4.4 Changing Module Parameters...................................... 21 4.5 Changing Module Labels........................................ 23 4.6 Configuring Module Ports........................................ 23 4.7 Grouping Modules............................................ 24 4.8 Basic Modules.............................................. 24 5 Interacting with the Version Tree 29 5.1 Version Tree View............................................ 29 5.2 Adding and Deleting Tags........................................ 33 5.3 -

Using Vistrails and Provenance for Teaching Scientific Visualization
DOI: 10.1111/j.1467-8659.2010.01830.x COMPUTER GRAPHICS forum Volume 30 (2011), number 1 pp. 75–84 Using VisTrails and Provenance for Teaching Scientific Visualization Claudio´ T. Silva, Erik Anderson, Emanuele Santos and Juliana Freire Scientific Computing and Imaging Institute, University of Utah, USA Abstract Over the last 20 years, visualization courses have been developed and offered at universities around the world. Many of these courses use established visualization libraries and tools (e.g. VTK, ParaView, AVS, VisIt) as a way to provide students a hands-on experience, allowing them to prototype and explore different visualization techniques. In this paper, we describe our experiences using VisTrails as a platform to teach scientific visualization. VisTrails is an open-source system that was designed to support exploratory computational tasks such as visualization and data analysis. Unlike previous scientific workflow and visualization systems, VisTrails provides a comprehensive provenance management infrastructure. We discuss how different features of the system, and in particular, the provenance information have changed the dynamics of the Scientific Visualization course we offer at the University of Utah. We also describe our initial attempts at using the provenance information to better assess our teaching techniques and student performance. Keywords: provenance, scientific visualization, education ACM CCS: K.3 [Computer and Education]: General. 1. Introduction tant to contrast the two fields. In the more traditional com- puter graphics, used to make movies or games, the goal is to As the volume of digital data explodes, the ability to visual- produce visually engaging (beautiful) imagery that ‘appears ize these data has become increasingly important. -

Tackling the Provenance Challenge One Layer at a Time
CONCURRENCY AND COMPUTATION: PRACTICE AND EXPERIENCE Concurrency Computat.: Pract. Exper. 2007; V:1–11 Prepared using cpeauth.cls [Version: 2002/09/19 v2.02] Tackling the Provenance Challenge One Layer at a Time Carlos Scheidegger1, David Koop2, Emanuele Santos1, Huy Vo1, Steven Callahan1, Juliana Freire2, Cl´audio Silva1 1 Scientific Computing and Imaging Institute, University of Utah 2 School of Computing, University of Utah SUMMARY VisTrails is a new workflow and provenance management system that provides support for scientific data exploration and visualization. Whereas workflows have been traditionally used to automate repetitive tasks, for applications that are exploratory in nature, change is the norm. VisTrails uses a new change-based provenance mechanism which was designed to handle rapidly-evolving workflows. It uniformly and automatically captures provenance information for data products and for the evolution of the workflows used to generate these products. In this paper, we describe how the VisTrails provenance data is organized in layers and present a first approach for querying this data that we developed to tackle the Provenance Challenge queries. key words: visualization, provenance, workflow evolution 1. Introduction Workflows are emerging as a paradigm for representing and managing complex computations. Workflows capture elaborate processes in a structured way and provide the provenance information necessary for result reproducibility, publication, and sharing among collaborators. Because of the formalism they provide and the automation they support, workflows have the potential to accelerate and transform the information analysis process [6]. Workflows are rapidly replacing primitive shell scripts as evidenced by the release of Apple’s Mac OS X Automator [1] and Microsoft’s Workflow Foundation [12]. -

Reproducibility Using Vistrails
1 Reproducibility Using VisTrails Juliana Freire Polytechnic Institute of NYU David Koop Polytechnic Institute of NYU Fernando Seabra Chirigati Polytechnic Institute of NYU Cl´audio T. Silva Polytechnic Institute of NYU CONTENTS 1.1 Introduction ...................................................... 1 1.2 Reproducibility, Workflows, and Provenance .................... 3 1.2.1 The Anatomy of a Reproducible Experiment ........... 3 1.2.2 Describing Computations as Workflows ................. 4 1.2.3 Provenance in Workflow Systems ....................... 6 1.2.4 Workflows and Reproducibility .......................... 7 1.3 The VisTrails System ............................................ 7 1.4 Reproducing and Publishing Results with VisTrails ............ 9 1.4.1 Reproducibility Support ................................. 10 1.4.2 Publishing Results ....................................... 14 1.4.3 Publishing Interactive Results on the Web .............. 14 1.5 Challenges and Opportunities ................................... 16 1.6 Related Work .................................................... 16 1.7 Conclusion ........................................................ 17 Acknowledgments ................................................... 17 1.1 Introduction Science has long placed an emphasis on revisiting and reusing past results: re- producibility is a core component of the scientific process. Testing and extend- 1 2 Implementing Reproducible Computational Research ing published results are standard activities that lead to practical progress: -

Vistrails Documentation Release 2.0.3
VisTrails Documentation Release 2.0.3 NYU Poly March 31, 2014 CONTENTS I User’s Guide1 1 Preliminary Pages 3 1.1 Preface..................................................3 2 An Introduction to VisTrails 5 2.1 What Is VisTrails?............................................5 2.2 Getting Started..............................................6 3 Learning VisTrails By Example 15 3.1 Creating and Modifying Workflows................................... 15 3.2 Groups and Subworkflows........................................ 23 3.3 Interacting with the Version Tree.................................... 27 3.4 Merging Two Version Trees....................................... 32 3.5 Querying the Version Tree........................................ 32 3.6 Spreadsheet................................................ 38 3.7 Using Analogies to Update Workflows................................. 44 3.8 Parameter Exploration.......................................... 50 3.9 Provenance Browser........................................... 57 3.10 Mashups................................................. 59 3.11 Module Descriptions and Examples................................... 61 4 Intermediate Concepts and VisTrails Packages 71 4.1 Control Flow in VisTrails........................................ 71 4.2 The Control Flow Assistant....................................... 81 4.3 Connecting to a Database........................................ 86 4.4 Example: Web Services......................................... 90 4.5 Persistence in VisTrails........................................ -

Making Computations and Publications Reproducible with Vistrails
R EPRODUCIBLE R E S E A R C H F O R S C I E N T I F I C C OMPUTING Making Computations and Publications Reproducible with VisTrails The VisTrails system supports the creation of reproducible experiments. VisTrails integrates data acquisition, derivation, analysis, and visualization as executable components throughout the scientific exploration process, and through systematic provenance capture, it makes it easier to generate and share reproducible results. Using VisTrails, authors can link results to their provenance, reviewers can assess the experiment’s validity, and readers can repeat and utilize the computations. mportant scientific results give insight and www.vpf.ethz.ch/services/researchethics/Broschure. lead to practical progress. The ability to pdf), funding agencies, conferences (www. test these results is crucial for science to be sigmod2011.org/calls_papers_sigmod_research_ self-correcting, and the ability to reuse and repeatability.shtml), and journals (www. Iextend the results enables science to move for- signalprocessingsociety.org/publications/periodicals/ ward. In natural science, long tradition requires tsp) have started to encourage (or require) authors that results be reproducible, and in math, results to include reproducible results in their publications. must be accompanied by formal, verifiable proofs. However, a major barrier to the wider adoption However, the same standard hasn’t been applied of reproducibility is the fact that it’s hard for au- for the results of computational experiments. thors to derive a compendium that encapsulates Most computational experiments are specified all the components (for example, the data, code, only informally in papers, where experimental parameter settings, and environment) needed to results are briefly described in figure captions, reproduce a result; and even when a compendium and the code that produced the results is seldom is available, it’s often hard for reviewers to verify available. -

Managing Rapidly-Evolving Scientific Workflows
Managing Rapidly-Evolving Scientific Workflows Juliana Freire Claudio T. Silva http://www.sci.utah.edu/~vgc/vistrails/ University of Utah Joint work with: Steven P. Callahan, Emanuele Santos, Carlos E. Scheidegger and Huy T. Vo Our Motivation: CORIE Environmental observation and forecasting system (EOFS) –Combine real-time sensor measurements with advanced computer models to describe complex, and dynamic environmental systems – focus on the Columbia River Initially: goal was to develop 3D visualizations Look at visualization from an information management perspective IPAW 2006 Juliana Freire 2 Data Exploration through Visualization Hard to make sense out of large volumes of raw data, e.g., sensor feeds, simulations, MRI scans Insightful visualizations help analyze and validate various hypothesis But creating a visualization is a complex, iterative process Perception & Data Visualization Image Knowledge Cognition Specification Exploration Data Visualization User J. van Wijk, IEEE Vis 2005 IPAW 2006 Juliana Freire 3 Visualization Systems: State of the Art Interactive creation and manipulation of visualizations Systems: SCIRun, ParaView/VTK Visual programming for creating visualization pipelines—dataflows of visualization operations Hard to create and compare a large number of visualizations Limitations: – No separation between the specification of a dataflow and its instances – Destructive updates—no provenance tracking mechanism – Users need to manage data and metadata The generation and maintenance of visualizations is a major -

Vistrails User's Guide
User's Guide Version 1.0 September 28, 2007 ii This is the preface. Contents 1 What Is VisTrails? 1 2 Getting Started 3 2.1 Installation . .3 2.2 Quick Start . .3 2.3 Manipulating VisTrails Files . .5 2.4 VisTrails Basics . .5 2.5 VisTrails Interaction . .6 3 Creating and Modifying Workflows 7 3.1 Working with Modules . .7 3.2 Adding and Deleting Modules . .7 3.3 Connecting Modules . .8 3.4 Changing Module Parameters . .9 3.5 Configuring Module Ports . 10 3.6 Basic Modules . 10 4 Interacting with the Version Tree 12 4.1 Version Tree View . 12 4.2 Adding and Deleting Tags . 13 4.3 Adding Version Annotations . 14 4.4 Navigating Versions . 14 4.5 Comparing Versions . 14 5 The Spreadsheet 16 5.1 The Spreadsheet Layout . 16 5.2 Using the Spreadsheet . 17 5.2.1 Interactive Mode . 17 5.2.2 Editing Mode . 18 5.3 Saving a Spreadsheet . 19 5.4 Creating a Customized Cell Widget . 20 iii iv CONTENTS 6 Querying the Version Tree 21 6.1 Query By Example . 21 6.2 Textual Queries . 22 6.3 Query Results . 24 7 Parameter Exploration 25 7.1 Creating a Parameter Exploration . 25 7.2 Spreadsheet Integration . 28 7.3 Examples . 28 7.3.1 Isosurfaces . 29 7.3.2 Resampling . 29 7.3.3 Animation . 30 8 Using Bookmarks 33 9 Connecting to a Database 34 9.1 Setup . 34 9.1.1 Setting up the database . 34 9.1.2 Setting up VisTrails . 35 9.2 Opening from a database . -

Introduction to the Vistrails System
Draft – do not distribute without permission. Introduction to the VisTrails system Steven P. Callahan Juliana Freire Emanuele Santos Carlos E. Scheidegger Cláudio T. Silva Wayne Tyler Huy T. Vo Scientific Computing and Imaging Institute School of Computing University of Utah [email protected] Summary This document is a short introduction and tutorial of the VisTrails prototype. This is not meant for widespread public use! We are making this early alpha release of VisTrails available to a select group of potential collaborators to give them a feel of the system and to get early feedback. You should expect broken or missing features and bugs in this release as well as major changes between this and future versions of VisTrails. Rationale and Goals of VisTrails Scientists are now faced with an incredible volume of data to analyze. To analyze and validate various hypotheses, it is necessary to create insightful visualizations of both the simulated processes and observed phenomena. Data exploration through visualization requires scientists to go through several steps. They need to select data sets and specify a series of operations to apply to the data to create appropriate visual representations before they can finally view and analyze the results. Often, insight comes from comparing multiple visualizations. Unfortunately, today this process is far from interactive and contains many error-prone and time-consuming tasks. Today, the generation and maintenance of visualization data products is a major bottleneck in the scientific process, hindering not only the ability to mine scientific data, but the actual use of scientific data. VisTrails extends existing dataflow-based visualization systems to streamline the creation, execution and sharing of complex visualizations. -

Vistrails Training Workflow
VisTrails Training Workflow VisTrails is an open-source scientific workflow and provenance management system that provides support for simulations, data exploration and visualization. Whereas workflows have been traditionally used to automate repetitive tasks, for applications that are exploratory in nature, such as simulations, data analysis and visualization, very little is repeated---change is the norm. As an engineer or scientist generates and evaluates hypotheses about data under study, a series of different, albeit related, workflows are created while a workflow is adjusted in an interactive process. VisTrails was designed to manage these rapidly-evolving workflows. A key distinguishing feature of VisTrails is a comprehensive provenance infrastructure that maintains detailed history information about the steps followed and data derived in the course of an exploratory task: VisTrails maintains provenance of data products, of the workflows that derive these products and their executions. This information is persisted as XML files or in a relational database, and it allows users to navigate workflow versions in an intuitive way, to undo changes but not lose any results, to visually compare different workflows and their results, and to examine the actions that led to a result. It also enables a series operations and user interfaces that simplify workflow design and use, including the ability to create and refine workflows by analogy and to query workflows by example. VisTrails supports the creation and execution of workflows. It allows the combination of loosely-coupled resources, specialized libraries, grid and Web services. The released version comes with support for several packages including, VTK, Image Magick, Web Services, and pylab. -

Workflows for Parameter Studies of Multi-Cell Modeling
Workflows for Parameter Studies of Multi-Cell Modeling Randy Heiland Maciek Swat Benjamin Zaitlen Open Systems Laboratory Biocomplexity Institute and Biocomplexity Institute and Indiana University Department of Physics Department of Physics Bloomington IN 47405, USA Indiana University Indiana University Bloomington IN 47405, USA Bloomington IN 47405, USA James Glazier Andrew Lumsdaine Biocomplexity Institute and Open Systems Laboratory Department of Physics Indiana University Indiana University Bloomington IN 47405, USA Bloomington IN 47405, USA Keywords: Scientific workflows, scripting languages, scripting language (www.python.org). CompuCell3D also cluster computing, visualization. uses Python as an interface to its underlying C++ code. Python is quite popular for developing interactive scientific Abstract applications [1]. Running simulations for multi-cell tissue models can involve numerous parameters and consume considerable 2. COMPUCELL3D computing resources. This paper presents an overview and CompuCell3D (www.compucell3d.org) is a multi-cell use case of two open source projects - CompuCell3D, a modeling framework [2]. It implements the Glazier- multi-cell modeling framework, and VisTrails, a workflow Graner-Hogeweg (GGH) model, also sometimes known as system for parameter exploration and data management. the cellular Potts model, and operates on a regular lattice (currently either square or hexagonal, in 2D and 3D). As a 1. INTRODUCTION general-purpose framework, CompuCell3D is capable of Mathematical modeling and computer simulations modeling a broad range of phenomena, e.g., continue to contribute to our understanding of a variety of ferromagnetism, foams, and biological cells [3][4]. One complex phenomena. In this paper we are interested in noteworthy feature of CompuCell3D is that its most processes involved in developmental biology.