Java SE 8 - Moving Java Forward
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Interactive Applications for Digital TV Using Internet Legacy – a Successful Case Study
Interactive Applications for Digital TV Using Internet Legacy – A Successful Case Study Márcio Gurjão Mesquita, Osvaldo de Souza B. The Big Players Abstract—This paper describes the development of an interactive application for Digital TV. The architectural Today there are three main Digital TV standards in the decisions, drawbacks, solutions, advantages and disadvantages world. DVB is the European standard, ATSC is the of Interactive Digital TV development are discussed. The American one and ISDB is the Japanese standard. Each one application, an e-mail client and its server, are presented and has its own characteristics, advantages and disadvantages. the main considerations about its development are shown, The European standard offers good options for interactive especially a protocol developed for communication between Internet systems and Digital TV systems. applications, the Japanese is very good on mobile applications and the American is strong on high quality Index Terms—Protocols, Digital TV, Electronic mail, image. Interactive TV C. The Brazilian Digital Television Effort Television is one of the main communication media in I. INTRODUCTION Brazil. More than 90% of Brazilian homes have a TV set, EVEOLOPING software applications has always been a most of which receive only analog signals [1]-[2]. The TV D hard task. When new paradigms appear, new plays an important role as a communication medium difficulties come along and software designers must deal integrator in a country of continental size and huge social with it in order to succeed and, maybe, establish new design differences as Brazil, taking information, news and and programming paradigms. This paper describes the entertainment to the whole country. -

A Java Security Scanner for Eclipse
Colby College Digital Commons @ Colby Honors Theses Student Research 2005 JeSS – a Java Security Scanner for Eclipse Russell Spitler Colby College Follow this and additional works at: https://digitalcommons.colby.edu/honorstheses Part of the Databases and Information Systems Commons, Other Computer Engineering Commons, Programming Languages and Compilers Commons, and the Systems Architecture Commons Colby College theses are protected by copyright. They may be viewed or downloaded from this site for the purposes of research and scholarship. Reproduction or distribution for commercial purposes is prohibited without written permission of the author. Recommended Citation Spitler, Russell, "JeSS – a Java Security Scanner for Eclipse" (2005). Honors Theses. Paper 567. https://digitalcommons.colby.edu/honorstheses/567 This Honors Thesis (Open Access) is brought to you for free and open access by the Student Research at Digital Commons @ Colby. It has been accepted for inclusion in Honors Theses by an authorized administrator of Digital Commons @ Colby. JeSS – a Java Security Scanner for Eclipse Russell Spitler Senior Honors Thesis Spring 2005 Colby College Department of Computer Science Advisor: Dale Skrien Contents Chapter 1 Introduction 1 Chapter 2 Secure Coding and Java Security 2.1 – Secure Coding 3 2.2 – Java Security 7 Chapter 3 Java Security Holes 3.1 – Don’t depend on initialization 13 3.2 – Make everything final 14 3.3 – Make your code unserializable and undeserializable 16 3.4 – Make your class non-Cloneable 19 3.5 – Don’t rely on -

Proceedings of the 2Nd Annual Digital TV Applications Software Environment
NISTIR 6740 Proceedings of the 2nd Annual Digital TV Applications Software Environment (DASE) Symposium 2001: End-to-End Data Services, Interoperability & Applications Edited by: Alan Mink Robert Snelick Information Technology Laboratory June 2001 National Institute of Standards and Technology Technology Administration, U.S. Deportment of Commerce U.S. Department of Commerce Donald L Evans, Secretary National Institute of Standards and Technology Karen H. Brown, Acting Director Table of Contents Foreword ..................................................................................…………………………………………… vi Symposium Committee ................................................................................................................................ vii Opening Remarks Welcome to NIST Alan Mink A TSC Introduction Marker Richer, Executive Director. Advanced Television Systems Committee (ATSC) 1st Day Keynote Gloria Tristani, Commissioner, Federal Communications Commission (FCC) ATP at NIST Marc Stanley, Acting Director, Advanced Technology Program (ATP) 2nd Day Keynote Christopher Atienza. Associate Director of Technology, Public Broadcasting System (PBS) Session 1: DASE Components DASE Overview, Architecture & Common Content Types...............................................................1 Glenn Adams (ATSC T3/SI7 Acting Chair), XFSI, Inc DASE Declarative Applications & Environment .............................................................................31 Glenn Adams (ATSC T3/SI7 Acting Chair), XFSI, Inc DASE API Object Model -

Eu-19-Zhang-New-Exploit-Technique
New Exploit Technique In Java Deserialization Attack • Yang Zhang • Yongtao Wang Keyi Li “在此键⼊引⽂。• ” • Kunzhe Chai –Johnny Appleseed New Exploit Technique In Java Deserialization Attack Back2Zero Team BCM Social Corp. BCM Social Group Who are we? Yang Zhang(Lucas) • Founder of Back2Zero Team & Leader of Security Research Department in BCM Social Corp. • Focus on Application Security, Cloud Security, Penetration Testing. • Spoke at various security conferences such as CanSecWest, POC, ZeroNights. Keyi Li(Kevin) • Master degree majoring in Cyber Security at Syracuse University. • Co-founder of Back2Zero team and core member of n0tr00t security team. • Internationally renowned security conference speaker. –Johnny Appleseed Who are we? Yongtao Wang • Co-founder of PegasusTeam and Leader of Red Team in BCM Social Corp. • Specializes in penetration testing and wireless security. • Blackhat, Codeblue, POC, Kcon, etc. Conference speaker. Kunzhe Chai(Anthony) • Founder of PegasusTeam and Chief Information Security Officer in BCM Social Corp. • Author of the well-known security tool MDK4. • Maker of China's first Wireless Security Defense Product Standard and he also is the world's first inventor of Fake Base Stations defense technology–Johnny Appleseed Agenda • Introduction to Java Deserialization • Well-Known Defense Solutions • Critical vulnerabilities in Java • URLConnection • JDBC • New exploit for Java Deserialization • Takeaways 2015: Chris Frohoff and Gabriel Lawrence presented their research into Java object deserialization vulnerabilities ultimately resulting in what can be readily described as the biggest wave of RCE bugs in Java history. Introduction to Java Deserialization Java Deserialization Serialization • The process of converting a Java object into stream of bytes. Databases Deserialization Serialization • A reverse process of creating a Java object from stream of bytes. -

Apache Harmony Project Tim Ellison Geir Magnusson Jr
The Apache Harmony Project Tim Ellison Geir Magnusson Jr. Apache Harmony Project http://harmony.apache.org TS-7820 2007 JavaOneSM Conference | Session TS-7820 | Goal of This Talk In the next 45 minutes you will... Learn about the motivations, current status, and future plans of the Apache Harmony project 2007 JavaOneSM Conference | Session TS-7820 | 2 Agenda Project History Development Model Modularity VM Interface How Are We Doing? Relevance in the Age of OpenJDK Summary 2007 JavaOneSM Conference | Session TS-7820 | 3 Agenda Project History Development Model Modularity VM Interface How Are We Doing? Relevance in the Age of OpenJDK Summary 2007 JavaOneSM Conference | Session TS-7820 | 4 Apache Harmony In the Beginning May 2005—founded in the Apache Incubator Primary Goals 1. Compatible, independent implementation of Java™ Platform, Standard Edition (Java SE platform) under the Apache License 2. Community-developed, modular architecture allowing sharing and independent innovation 3. Protect IP rights of ecosystem 2007 JavaOneSM Conference | Session TS-7820 | 5 Apache Harmony Early history: 2005 Broad community discussion • Technical issues • Legal and IP issues • Project governance issues Goal: Consolidation and Consensus 2007 JavaOneSM Conference | Session TS-7820 | 6 Early History Early history: 2005/2006 Initial Code Contributions • Three Virtual machines ● JCHEVM, BootVM, DRLVM • Class Libraries ● Core classes, VM interface, test cases ● Security, beans, regex, Swing, AWT ● RMI and math 2007 JavaOneSM Conference | Session TS-7820 | -

Java Security, 2Nd Edition
Table of Contents Preface..................................................................................................................................................................1 Who Should Read This Book?.................................................................................................................1 Versions Used in This Book....................................................................................................................2 Conventions Used in This Book..............................................................................................................2 Organization of This Book.......................................................................................................................3 What's New in This Edition.....................................................................................................................5 How to Contact Us...................................................................................................................................5 Acknowledgments....................................................................................................................................6 Feedback for the Author..........................................................................................................................6 Chapter 1. Java Application Security...............................................................................................................7 1.1 What Is Security?...............................................................................................................................7 -

Java(8$ Andrew$Binstock,$Editor$In$Chief,$Dr.Dobbs$
Java$Update$and$Roadmap$ November(2014( Tomas$Nilsson$ Senior$Principal$Product$Manager$ Java$SE$ Copyright$©$2014,$Oracle$and/or$its$affiliates.$All$rights$reserved.$$|$ Safe$Harbor$Statement$ The$following$is$intended$to$outline$our$general$product$direcNon.$It$is$intended$for$ informaNon$purposes$only,$and$may$not$be$incorporated$into$any$contract.$It$is$not$a$ commitment$to$deliver$any$material,$code,$or$funcNonality,$and$should$not$be$relied$upon$ in$making$purchasing$decisions.$The$development,$release,$and$Nming$of$any$features$or$ funcNonality$described$for$Oracle’s$products$remains$at$the$sole$discreNon$of$Oracle.$ Copyright$©$2014,$Oracle$and/or$its$affiliates.$All$rights$reserved.$$|$ Agenda$ 1( Oracle$and$Java$ 2( Java$SE$8$Overview$ 3( Java$SE$9$and$Beyond$ Copyright$©$2014,$Oracle$and/or$its$affiliates.$All$rights$reserved.$$|$ 1( Oracle$and$Java$ 2( Java$SE$8$Overview$ 3( Roadmap$ Copyright$©$2014,$Oracle$and/or$its$affiliates.$All$rights$reserved.$$|$ Oracle$and$Java$ • Oracle$has$used$Java$since$the$beginning$of$Nme$(eg$1990s)$ • Acquired$JAVA$(Sun$Microsystems)$in$2010,$including$Java$IP,$trademarks$ • Embraced$OpenJDK,$open$community,$open$JCP$ – Welcomed$IBM,$Apple,$SAP,$ARM,$AMD,$Intel,$Twi\er,$Goldman$Sachs,$Microso^$and$many$others$ – Made$OpenJDK$official$Java$SE$reference$implementaNon$ – Ongoing$move$towards$open$development,$governance,$transparency$ • JDK$development:$Oracle$and$community$ – Oracle$focus$on$modernizaNon,$security,$big$Ncket$R&D$and$commercial$value$to$Oracle$ – Community$contributes$based$on$interest$and$ability,$examples:$ -

Evaluating the Flexibility of the Java Sandbox
Evaluating the Flexibility of the Java Sandbox Zack Coker, Michael Maass, Tianyuan Ding, Claire Le Goues, and Joshua Sunshine Carnegie Mellon University {zfc,mmaass}@cs.cmu.edu, [email protected], {clegoues,sunshine}@cs.cmu.edu ABSTRACT should protect both the host application and machine from The ubiquitously-installed Java Runtime Environment (JRE) malicious behavior. In practice, these security mechanisms provides a complex, flexible set of mechanisms that support are problematically buggy such that Java malware is often the execution of untrusted code inside a secure sandbox. able to alter the sandbox's settings [4] to override security However, many recent exploits have successfully escaped the mechanisms. Such exploits take advantage of defects in either sandbox, allowing attackers to infect numerous Java hosts. the JRE itself or the application's sandbox configuration to We hypothesize that the Java security model affords devel- disable the security manager, the component of the sandbox opers more flexibility than they need or use in practice, and responsible for enforcing the security policy [5, 6, 7, 8]. thus its complexity compromises security without improving In this paper, we investigate this disconnect between theory practical functionality. We describe an empirical study of the and practice. We hypothesize that it results primarily from ways benign open-source Java applications use and interact unnecessary complexity and flexibility in the design and with the Java security manager. We found that developers engineering of Java's security mechanisms. For example, regularly misunderstand or misuse Java security mechanisms, applications are allowed to change the security manager at that benign programs do not use all of the vast flexibility runtime, whereas static-only configuration of the manager afforded by the Java security model, and that there are clear would be more secure. -

Semi-Automated Mobile TV Service Generation
> IEEE Transactions on Broadcasting < 1 Semi-automated Mobile TV Service Generation Dr Moxian Liu, Member, IEEE, Dr Emmanuel Tsekleves, Member, IEEE, and Prof. John P. Cosmas, Senior Member, IEEE environments from both hardware and software perspectives. The development results on the hardware environment and Abstract—Mobile Digital TV (MDTV), the hybrid of Digital lower layer protocols are promising with reliable solutions Television (DTV) and mobile devices (such as mobile phones), has (broadcast networks such as DVB-H and mobile convergence introduced a new way for people to watch DTV and has brought networks such as 3G) being formed. However the new opportunities for development in the DTV industry. implementation of higher layer components is running Nowadays, the development of the next generation MDTV service relatively behind with several fundamental technologies has progressed in terms of both hardware layers and software, (specifications, protocols, middleware and software) still being with interactive services/applications becoming one of the future MDTV service trends. However, current MDTV interactive under development. services still lack in terms of attracting the consumers and the The vast majority of current commercial MDTV service service creation and implementation process relies too much on applications include free-to-air, Pay Television (PayTV) and commercial solutions, resulting in most parts of the process being Video-on-Demand (VoD) services. When contrasted with the proprietary. In addition, this has increased the technical demands various service types of conventional DTV, MDTV services for developers as well as has increased substantially the cost of are still unidirectional, offering basic services that lack in producing and maintaining MDTV services. -

6.4.0 Release Notes
Red Hat JBoss Enterprise Application Platform 6.4 6.4.0 Release Notes For Use with Red Hat JBoss Enterprise Application Platform 6 Last Updated: 2017-12-12 Red Hat JBoss Enterprise Application Platform 6.4 6.4.0 Release Notes For Use with Red Hat JBoss Enterprise Application Platform 6 Legal Notice Copyright © 2017 Red Hat, Inc.. This document is licensed by Red Hat under the Creative Commons Attribution-ShareAlike 3.0 Unported License. If you distribute this document, or a modified version of it, you must provide attribution to Red Hat, Inc. and provide a link to the original. If the document is modified, all Red Hat trademarks must be removed. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. Node.js ® is an official trademark of Joyent. Red Hat Software Collections is not formally related to or endorsed by the official Joyent Node.js open source or commercial project. -
Downloads and Documentation Are 12 Implementation Details
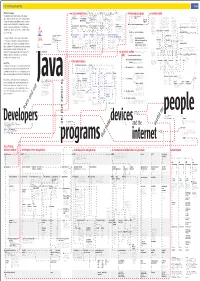
Java™ Technology Concept Map SM 2 Sun works with companies become members of the JCP by signing JSPA has a is which What is Java Technology? onthe represented are supports the development of ... Java 0 within the context of the Java Community Process, Java Community Process The Java Specification Participation Programming language Java object model that is an that by is organized defines This diagram is a model of Java™ technology. The diagram begins with members join the JCP by signing the provides ... documentation 42 may function as ... developers 23 Agreement is a one-year renewable is defined by the ... Java Language Specification 43 logo owns the ... Java trademark 1 support the development of ... Java 0 agreement that allows signatories to is used to write ... programs 24 make(s) ... SDKs 29 make ... SDKs 29 Class libraries are An application programming interface is the Particular to Java, Abstract classes permit child explains Java technology by placing it in the context of related Java forums often discuss Java in Java developer become members of the JCP. is used to write ... class libraries 10 organized collections written or understood specification of how a interfaces are source code classes to inherit a defined method makes versions of a ... JVM 18 make versions of a ... JVM 18 Companies include Alternatively, developers can sign the syntax and 4 of prebuilt classes piece of software interacts with the outside files that define a set of or to create groups of related communities provides certify Java applications using IBM, Motorola, more limited Individual Expert The Java language has roots in C, Objective C, and functions used to world. -

Entrevista Promoções Agenda De Eventos
ENTREVISTA Bjjarne Stroustrup, o criador do C++ PROMOÇÕES AGENDA DE http://reviista.espiiriitolliivre.org | #024 | MarÇo 2011 EVENTOS Linguagens de ProgramaÇÃo Grampos Digitais PÁg 21 TV pela Internet no Ubuntu PÁg 70 SumÁrio e PaginaÇÃo no LibreOffice PÁg 57 Navegando em pequenos dispositivos PÁg 74 Teste de IntrusÃo com Software Livre PÁg 65 Linux AcessÍvel PÁg 88 Alterando endereÇos MAC PÁg 69 Mulheres e TI: Seja tambÉm uma delas PÁg 90 COM LICENÇA Revista EspÍrito Livre | Março 2011 | http://revista.espiritolivre.org |02 EDITORIAL / EXPEDIENTE EXPEDIENTE Diretor Geral Programando sua vida... JoÃo Fernando Costa Júnior Neste mês de março, a Revista EspÍrito Livre fala de um assunto que para muitos É um bicho de 7 cabeças: Linguagens de ProgramaÇÃo. Seja você Editor desenvolvedor ou nÃo, programar É um ato diÁrio. Nossos familiares se JoÃo Fernando Costa Júnior programam para seus afazeres, seu filho se programa para passar no vestibular, você se programa para cumprir as suas obrigaÇÕes. Programarse É RevisÃo um ato cotidiano, e nÃo exclusivo dos desenvolvedores de programas. EntÃo AÉcio Pires, Alessandro Ferreira Leite, porque inÚmeras pessoas materializam na programaÇÃo os "seus piores Alexandre A. Borba, Carlos Alberto V. pesadelos? Será algo realmente complexo? Será fÁcil atÉ demais? A quem Loyola Júnior, Daniel Bessa, Eduardo Charquero, Felipe Buarque de Queiroz, diga e atÉ ignore tais dificuldades encontradas por várias pessoas nesse ramo Fernando Mercês, Larissa Ventorim da computaÇÃo, que sempre carece de mãodeobra qualificada para o Costa, Murilo Machado, OtÁvio mercado. Alunos de diversos cursos de computaÇÃo encontram nesta parte da Gonçalves de Santana, Rodolfo M.