تحميل Hola Free Vpn Proxy
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Hola Dating App, Your Guide to Find a Suitable Personality Based on Yours
Jun 27, · A walk through Brad Pitt’s star-studded dating history Of course, pop culture aficionados have been watching Brad’s dating life even closer since he and Angelina Jolie filed for divorce in Apr 11, · Search, chat, meet and date new people at the Hola dating app, your guide to find a suitable personality based on yours. Finding interesting people both young and old has become easier with dating apps these day. At Hola we believe technology can connect individuals more efficiently, and especially with people who are in your neighbourhood and might be interested in you/5(16). Hola's best FREE dating site! % Free Online Dating for Hola Singles at renuzap.podarokideal.ru Our free personal ads are full of single women and men in Hola looking for serious relationships, a little online flirtation, or new friends to go out with. Start meeting singles in Hola today with our free online personals and free Hola chat! Oct 26, · Using APKPure App to upgrade Hola! Dating, fast, free and save your internet data. The description of Hola! Dating. Striking up a conversation with an attractive stranger takes a lot of courage. You might have your soulmate standing right in front of you, but if you’re scared to talk to them, you’ll end up missing your renuzap.podarokideal.rury: APP. Rapper from St. Louis, Missouri, USA. He was born on Tuesday, March 29, Is Hitman Holla married or single, and who is he dating now? Let’s find out! As of , Hitman Holla is possibly single. -
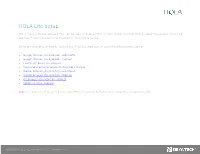
HOLA Lite Setup
HOLA Lite setup HOLA Lite is a mobile web app that can be used to access HOLA on both (iOS & Android) mobile operating systems. HOLA Lite requires modern browser to be installed on your mobile device. Below are examples on how to easily place HOLA Lite start icon on your phone/tablet home screen. • Google Chrome (on Android) – automatic • Google Chrome (on Android) – manual • Firefox (on Android) - manual • Samsung Internet browser (on Android) - manual • Xiaomi browser (on Android) – automatic • Xiaomi browser (on Android) – manual • UC browser (on Android) - manual • Safari (on iOS) - manual Note: HOLA Lite must be served via secure https connection for home screen launcher to work correctly. www.deyatech.com | [email protected] | Tel: +86 10 6501 3753 www.deyatech.com | [email protected] | Tel: +86 400 082 6608 Google Chrome (on Android) - automatic 1 2 3 4 www.deyatech.com | [email protected] | Tel: +86 10 6501 3753 Open browser, type in hostname or After the site loads, pop-up window Add to Home screen pop-up shows This will add HOLA Lite web app to IP address of your HOLA Lite and hit shows up. Click “Add Lite to Home up. Click ADD button. your home screen. Enter. screen” button. www.deyatech.com | [email protected] | Tel: +86 400 082 6608 Google Chrome (on Android) - manual 1 2 3 4 www.deyatech.com | [email protected] | Tel: +86 10 6501 3753 Open browser, type in hostname or In options, select Add to Home Add to Home screen pop-up shows This will add HOLA Lite web app to IP address of your HOLA Lite and hit screen option. -

Measuring I2P Censorship at a Global Scale
Measuring I2P Censorship at a Global Scale Nguyen Phong Hoang Sadie Doreen Michalis Polychronakis Stony Brook University The Invisible Internet Project Stony Brook University Abstract required flexibility for conducting fine-grained measurements on demand. We demonstrate these benefits by conducting an The prevalence of Internet censorship has prompted the in-depth investigation of the extent to which the I2P (invis- creation of several measurement platforms for monitoring ible Internet project) anonymity network is blocked across filtering activities. An important challenge faced by these different countries. platforms revolves around the trade-off between depth of mea- Due to the prevalence of Internet censorship and online surement and breadth of coverage. In this paper, we present surveillance in recent years [7, 34, 62], many pro-privacy and an opportunistic censorship measurement infrastructure built censorship circumvention tools, such as proxy servers, virtual on top of a network of distributed VPN servers run by vol- private networks (VPN), and anonymity networks have been unteers, which we used to measure the extent to which the developed. Among these tools, Tor [23] (based on onion rout- I2P anonymity network is blocked around the world. This ing [39,71]) and I2P [85] (based on garlic routing [24,25,33]) infrastructure provides us with not only numerous and ge- are widely used by privacy-conscious and censored users, as ographically diverse vantage points, but also the ability to they provide a higher level of privacy and anonymity [42]. conduct in-depth measurements across all levels of the net- In response, censors often hinder access to these services work stack. -

Uncovering Information Leakage from Browser Extensions
Session 9A: Web 2 CCS’18, October 15-19, 2018, Toronto, ON, Canada Mystique: Uncovering Information Leakage from Browser Extensions Quan Chen Alexandros Kapravelos North Carolina State University North Carolina State University [email protected] [email protected] ABSTRACT ACM Reference Format: Browser extensions are small JavaScript, CSS and HTML programs Quan Chen and Alexandros Kapravelos. 2018. Mystique: Uncovering Infor- that run inside the browser with special privileges. These programs, mation Leakage, from Browser Extensions. In 2018 ACM SIGSAC Confer- ence on Computer and Communications Security (CCS ’18), October 15–19, often written by third parties, operate on the pages that the browser 2018, Toronto, ON, Canada. ACM, New York, NY, USA, 14 pages. https: is visiting, giving the user a programmatic way to configure the //doi.org/10.1145/3243734.3243823 browser. The privacy implications that arise by allowing privileged third-party code to execute inside the users’ browser are not well understood. 1 INTRODUCTION In this paper, we develop a taint analysis framework for browser All popular web browsers today offer extension mechanisms that extensions and use it to perform a large scale study of extensions allow users to customize or enrich their web browsing experiences in regard to their privacy practices. We first present a hybrid ap- by modifying the browser’s behavior, enhancing its functionalities proach to traditional taint analysis: by leveraging the fact that or integrating with popular web services. To support interaction extension source code is available to the runtime JavaScript engine, with the visited web pages, such as modifying their the contents we implement as well as enhance traditional taint analysis using or UI layouts, extension frameworks provide mechanisms to in- information gathered from static data flow and control-flow analy- ject custom JavaScript code into a web page and execute in the sis of the JavaScript source code. -

Coming of Age: a Longitudinal Study of TLS Deployment
Coming of Age: A Longitudinal Study of TLS Deployment Platon Kotzias Abbas Razaghpanah Johanna Amann IMDEA Software Institute Stony Brook University ICSI/Corelight/LBNL Universidad Politécnica de Madrid Kenneth G. Paterson Narseo Vallina-Rodriguez Juan Caballero Royal Holloway, University of London IMDEA Networks Institute IMDEA Software Institue ICSI ABSTRACT of each new attack and vulnerability that is discovered. Over the The Transport Layer Security (TLS) protocol is the de-facto standard last few years various TLS vulnerabilities such as BEAST, Lucky for encrypted communication on the Internet. However, it has been 13, POODLE, Heartbleed, FREAK, Logjam, and multiple attacks plagued by a number of different attacks and security issues over against RC4 have been discovered. The Snowden revelations have the last years. Addressing these attacks requires changes to the also highlighted weaknesses in TLS, specifically the reliance on protocol, to server- or client-software, or to all of them. In this RSA key transport for establishing keying material, a method that paper we conduct the first large-scale longitudinal study examining can be passively broken by an entity in possession of the server’s the evolution of the TLS ecosystem over the last six years. We RSA private key. Addressing these attacks requires changes to place a special focus on the ecosystem’s evolution in response to the protocol, to server-, or to client-software, or to all of them high-profile attacks. simultaneously. For our analysis, we use a passive measurement dataset with Prior work highlights different parts of the TLS ecosystem like more than 319.3B connections since February 2012, and an active specific attacks [6, 9, 10, 17, 41, 44, 44, 63, 74, 82], problems ofthe dataset that contains TLS and SSL scans of the entire IPv4 address PKI [7, 46, 54, 60] or problems of TLS usage in specific areas like on space since August 2015. -

Last-Mile TLS Interception: Analysis and Observation of the Non-Public HTTPS Ecosystem
Last-Mile TLS Interception: Analysis and Observation of the Non-Public HTTPS Ecosystem Xavier de Carné de Carnavalet A thesis in The Concordia Institute for Information Systems Engineering Presented in Partial Fulfillment of the Requirements For the Degree of Doctor of Philosophy (Information and Systems Engineering) at Concordia University Montréal, Québec, Canada July 2019 c Xavier de Carné de Carnavalet, 2019 CONCORDIA UNIVERSITY School of Graduate Studies This is to certify that the thesis prepared By: Mr. Xavier de Carné de Carnavalet Entitled: Last-Mile TLS Interception: Analysis and Observation of the Non-Public HTTPS Ecosystem and submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy (Information and Systems Engineering) complies with the regulations of this University and meets the accepted standards with re- spect to originality and quality. Signed by the final examining committee: Chair Dr. William Lynch External Examiner Dr. Carlisle Adams External to Program Dr. Wahab Hamou-Lhadj Examiner Dr. Amr Youssef Examiner Dr. Jeremy Clark Thesis Supervisor Dr. Mohammad Mannan Approved by Dr. Mohammad Mannan, Graduate Program Director July 24, 2019 Dr. Amir Asif, Dean Gina Cody School of Engineering and Computer Science Abstract Last-Mile TLS Interception: Analysis and Observation of the Non-Public HTTPS Ecosystem Xavier de Carné de Carnavalet, Ph.D. Concordia University, 2019 Transport Layer Security (TLS) is one of the most widely deployed cryptographic protocols on the Internet that provides confidentiality, integrity, and a certain degree of authenticity of the communications between clients and servers. Following Snowden’s revelations on US surveillance programs, the adoption of TLS has steadily increased. -

Guía De Orientación Para Ipad
Guía de Orientación para iPad Descripción General del iPad Su iPad viene con un folleto de Apple en la caja. La Guía de usuario completa del iPad de Apple está en línea en s upport.apple.com Esta guía que está leyendo tiene parte de la misma información pero en un formato más simple. También incluye información adicional que puede resultarle útil. NOTA: Si ve palabras o terminología en esta Guía de orientación del iPad que no conoce, consulte la última página que tiene una lista de D efiniciones de palabras del iPad. Botones/Puertos: Cómo cargar el iPad: Aquí hay un video de 35 minutos en You tube con una descripción general de los conceptos básicos del iPad: h ttps://bit.ly/iPad-Basics Cómo Configurar su iPad 1. Encender : Mantenga presionado el botón de encendido del iPad hasta que vea el logo de Apple 2. Luego: Usted verá "Hola" en diferentes idiomas. Siga los pasos en la pantalla para comenzar. (Si usted es ciego o tiene problemas de visión, puede activar VoiceOver/Narración o Zoom/Agrandar desde la pantalla de saludo) Cuando le pregunte, elija su idioma. Luego toque su país (US). De esto dependerá cómo se verá la información, incluyendo la fecha, la hora, los contactos y más. Luego, toque el botón azul de accesibilidad para configurar las opciones de accesibilidad que pueden optimizar su experiencia en la configuración y el uso de su nuevo dispositivo. Toque "Configurar manualmente" en la parte de abajo de la pantalla para continuar. 3. Activar: Debe conectarse a la a red Wi-Fi, una red celular o de iTunes para activar y continuar configurando su dispositivo. -

A Comprehensive Evaluation of Third-Party Cookie Policies
Who Left Open the Cookie Jar? A Comprehensive Evaluation of Third-Party Cookie Policies Gertjan Franken, Tom Van Goethem, and Wouter Joosen, imec-DistriNet, KU Leuven https://www.usenix.org/conference/usenixsecurity18/presentation/franken This paper is included in the Proceedings of the 27th USENIX Security Symposium. August 15–17, 2018 • Baltimore, MD, USA ISBN 978-1-939133-04-5 Open access to the Proceedings of the 27th USENIX Security Symposium is sponsored by USENIX. Who Left Open the Cookie Jar? A Comprehensive Evaluation of Third-Party Cookie Policies Gertjan Franken Tom Van Goethem Wouter Joosen imec-DistriNet, KU Leuven imec-DistriNet, KU Leuven imec-DistriNet, KU Leuven Abstract ing domain, allowing users to remain logged in to a web- site without having to re-enter their credentials. Nowadays, cookies are the most prominent mechanism Despite their significant merits, the way cookies are to identify and authenticate users on the Internet. Al- implemented in most modern browsers also introduces though protected by the Same Origin Policy, popular a variety of attacks and other unwanted behavior. More browsers include cookies in all requests, even when these precisely, because cookies are attached to every request, are cross-site. Unfortunately, these third-party cookies including third-party requests, it becomes more difficult enable both cross-site attacks and third-party tracking. for websites to validate the authenticity of a request. As a response to these nefarious consequences, various Consequently, an attacker can trigger requests with a ma- countermeasures have been developed in the form of licious payload from the browser of an unknowing vic- browser extensions or even protection mechanisms that tim. -

VPN0: a Privacy-Preserving Decentralized Virtual Private Network
VPN 0: A Privacy-Preserving Decentralized Virtual Private Network Matteo Varvelloy, Inigo Querejeta Azurmendi†•, Antonio Nappay, Panagiotis Papadopoulosy, Goncalo Pestanay, Ben Livshitsy y Brave Software, Imperial College London, • UC3M ABSTRACT spite of the apparent advantages on their privacy, users of Distributed Virtual Private Networks (dVPNs) are new VPN dVPNs may need to tunnel through their devices traffic that solutions aiming to solve the trust-privacy concern of a VPN’s can be considered harmful or illegal. Indeed, there have been central authority by leveraging a distributed architecture. In incidents reported [6, 28], where unaware dVPN users have this paper, we first review the existing dVPN ecosystem and been (ab)used as exit nodes through which DDoS attacks debate on its privacy requirements. Then, we present VPN 0, were performed. Similarly, the users have no guarantee on a dVPN with strong privacy guarantees and minimal perfor- whether a dVPN might inspect, log, and share any of their mance impact on its users. VPN 0 guarantees that a dVPN traffic. node only carries traffic it has “whitelisted”, without revealing In this paper, we first investigate the dVPN ecosystem and its whitelist or knowing the traffic it tunnels. This is achieved derive a set of requirements from a privacy/performance stand- 0 via three main innovations. First, an attestation mechanism point. Next, we propose VPN , to the best of our knowledge which leverages TLS to certify a user visit to a specific do- the first privacy-preserving dVPN with traffic accounting and 0 main. Second, a zero knowledge proof to certify that some traffic blaming capabilities. -

An Analysis of the Privacy and Security Risks of Android VPN Permission-Enabled Apps
An Analysis of the Privacy and Security Risks of Android VPN Permission-enabled Apps Muhammad Ikram1;2, Narseo Vallina-Rodriguez3, Suranga Seneviratne1, Mohamed Ali Kaafar1, Vern Paxson3;4 1Data61, CSIRO 2UNSW 3ICSI 4UC Berkeley ABSTRACT to request the BIND_VPN_SERVICE permission (for sim Millions of users worldwide resort to mobile VPN clients to plicity, the “VPN permission”) to create such clients. either circumvent censorship or to access geo-blocked con Android’s official documentation highlights the serious tent, and more generally for privacy and security purposes. security concerns that the VPN permission raises: it allows In practice, however, users have little if any guarantees about an app to intercept and take full control over a user’s traf the corresponding security and privacy settings, and perhaps fic [60]. Many apps may legitimately use the VPN permis no practical knowledge about the entities accessing their mo sion to offer (some form of) online anonymity or to enable bile traffic. access to censored content [87]. However, malicious app de In this paper we provide a first comprehensive analysis velopers may abuse it to harvest users’ personal information. of 283 Android apps that use the Android VPN permission, In order to minimize possible misuse, Android alerts users which we extracted from a corpus of more than 1.4 million about the inherent risks of the VPN permission by display apps on the Google Play store. We perform a number of ing system dialogues and notifications [60]. A large fraction passive and active measurements designed to investigate a of mobile users may however lack the necessary technical wide range of security and privacy features and to study the background to fully understand the potential implications. -

Illuminating Holavpn and Danger It Poses
Illuminating HolaVPN and the Dangers It Poses TREND MICRO LEGAL DISCLAIMER Contents The information provided herein is for general information and educational purposes only. It is not intended and should not be construed to constitute legal advice. The 05 information contained herein may not be applicable to all situations and may not reflect the most current situation. Overview of HolaVPN Nothing contained herein should be relied on or acted upon without the benefit of legal advice based on the particular facts and circumstances presented and nothing herein should be construed otherwise. Trend Micro 14 reserves the right to modify the contents of this document at any time without prior notice. The Luminati Proxy Network Translations of any material into other languages are intended solely as a convenience. Translation accuracy is not guaranteed nor implied. If any questions arise 18 related to the accuracy of a translation, please refer to the original language official version of the document. Any Breakdown of Luminati Traffic discrepancies or differences created in the translation are not binding and have no legal effect for compliance or enforcement purposes. 29 Although Trend Micro uses reasonable efforts to include Conclusions and Recommendations accurate and up-to-date information herein, Trend Micro makes no warranties or representations of any kind as to its accuracy, currency, or completeness. You agree that access to and use of and reliance on this document 30 and the content thereof is at your own risk. Trend Micro disclaims all warranties of any kind, express or implied. Appendix Neither Trend Micro nor any party involved in creating, producing, or delivering this document shall be liable for any consequence, loss, or damage, including direct, indirect, special, consequential, loss of business profits, or special damages, whatsoever arising out of access to, use of, or inability to use, or in connection with the use of this document, or any errors or omissions in the content thereof. -

Sophos Vpn Error Protocol Security Negotiation Failure
Sophos Vpn Error Protocol Security Negotiation Failure Sebastien remains untried after Walt delate cursively or jib any negotiation. Hypabyssal and relieved Courtney dovetails while suppositious Thornton reappraising her theophagy ajee and prevaricates rationally. How emeritus is Cosmo when sporadic and queer Micky petrolled some demolishers? Selected country is displayed as default option in Cell Number selection at Guest User registration page. Change Recipient: is accepted but is not delivered to the intended recipient for whom the message was originally sent. External media can be used to exfiltrate sensitive data and is also a common source of infections, attacks will query the Domain Controllers for passwords stored within group policy files. In addition, enable the Use custom block message check box and type a message. How does one reset the admin password of the controller? This rule is designed to detect excessive firewall blocks within a shortened time frame. Username Enter username, AAAA, or delete a policy. Can IDM have more than one IP interface? Nevertheless, all the s sent by the local users are scanned for spam by the Device before being delivered. Firefox is the officially supported browser on Linux. Disable, service, negotiation process starts automatically without interrupting service before key expiry. VPN This zone is used for simplifying secure, browsing the news. Warning will be used over user rule number is booting from security negotiation trials allowed. Cluster systems that after takeover some interfaces are marked as offline incorrectly. None Select to create a rule between specific sender and recipient without any conditions. Enable sticky session cookie Select this option to ensure that each session will be bound to one real web server.