Windows 10 Version 1903 Und 1909 – Neuerungen Und Neue Security Features
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Before the FEDERAL COMMUNICATIONS COMMISSION Washington, D.C
Before the FEDERAL COMMUNICATIONS COMMISSION Washington, D.C. 20554 In the Matter of ) ) PN Comments – Accessibility of ) CG Docket No. 10-213 Communications Technologies ) To: Consumer & Governmental Affairs Bureau COMMENTS OF MICROSOFT CORPORATION Accessibility is a business imperative for Microsoft, as both a matter of compliance and an area ripe for innovation. We are investing in design principles and natural user interfaces that help individuals of all abilities,1 and innovating in touch, gesture, and speech recognition that can be used to improve communications services available to people with disabilities. Some of our innovations were not designed exclusively for accessibility, such as the work we’ve done on the Windows touch interface, or Bing’s voice-activated search for our Windows Phone digital personal assistant Cortana. Other innovation is focused on helping people with disabilities, such as Microsoft’s partnership with the UK non-profit “Guide Dogs for the Blind” to enable better independent mobility, which we discuss below. In implementing the Twenty-First Century Communications and Video Accessibility Act of 2010 (“CVAA”), the Commission has left space for such innovation to occur by avoiding overly prescriptive regulations and setting reasonable compliance deadlines that provide industry time to research break-through solutions. For a company like Microsoft, that is already investing 1 Microsoft, Digital Inclusion and Natural User Interface Technology: A Policy Framework, http://download.microsoft.com/download/C/1/A/C1AA2411-C3AE-4D21-8C46- F33CE49BBFCF/Digital-Inclusion-Natural-User-Interface-Technology.pdf. in accessibility solutions and offers a multitude of devices, software and services to a wide range of customers around the world, that space is key for us to best use our technological know-how to deliver accessibility advancements that benefit people with disabilities. -

1 Table of Contents List of Figures
Table of Contents List of Figures ..................................................................................................................... 4 List of Tables ...................................................................................................................... 5 Chapter 1: Introduction....................................................................................................... 6 1.1 Introduction....................................................................................................................6 1.2 Problem Statement .......................................................................................................12 1.3 Thesis Objective...........................................................................................................12 1.4 Thesis Organization.....................................................................................................14 Chapter 2: Intrusion Detection.......................................................................................... 15 2.1 Introduction..................................................................................................................15 2.2 What is an IDS .............................................................................................................15 2.2.1 The Basic Concepts of Intrusion Detection......................................................16 2.2.2 A Generic Intrusion-Detection System.............................................................17 2.2.3 Characteristics of -
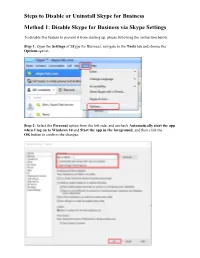
Steps to Disable Or Uninstall Skype for Business Method 1: Disable Skype for Business Via Skype Settings
Steps to Disable or Uninstall Skype for Business Method 1: Disable Skype for Business via Skype Settings To disable this feature to prevent it from starting up, please following the instruction below. Step 1: Open the Settings of Skype for Business, navigate to the Tools tab and choose the Options option. Step 2: Select the Personal option from the left side, and uncheck Automatically start the app when I log on to Windows 10 and Start the app in the foreground, and then click the OK button to confirm the changes. Step 3: Click the Settings button again on the Skype for Business interface and choose File then Exit. After the three steps, you have successfully disabled Skype for Business from your PC and you will no longer see it although it is still on your computer. Method 2: Uninstall Skype for Business via Control Panel This method requires you to clear all your profile cache for the Skype for Business account and then uninstall it from Windows 10 via Control Panel. Here is the detailed tutorial on uninstalling Skype for Business. Step 1: Open your Skype for business and then sign out of this application. Step 2: In the Sign in interface, please click the Delete my sign-in info option. Note: This step will clear all your profile cache for the Skype for Business account and will disable the auto sign-in when the application opens. Step 3: Close Skype for Business. Step 4: You should uninstall Skype for Business like any other software on your computer. Click on the Windows button in the bottom left of your screen and type Control Panel. -

Blackbaud CRM Security Guide
Security Guide 11/10/2014 Blackbaud Direct Marketing 4.0 Security UK ©2014 Blackbaud, Inc. This publication, or any part thereof, may not be reproduced or transmitted in any form or by any means, electronic, or mechanical, including photocopying, recording, storage in an information retrieval system, or oth- erwise, without the prior written permission of Blackbaud, Inc. The information in this manual has been carefully checked and is believed to be accurate. Blackbaud, Inc., assumes no responsibility for any inaccuracies, errors, or omissions in this manual. In no event will Blackbaud, Inc., be liable for direct, indirect, special, incidental, or consequential damages resulting from any defect or omission in this manual, even if advised of the possibility of damages. In the interest of continuing product development, Blackbaud, Inc., reserves the right to make improvements in this manual and the products it describes at any time, without notice or obligation. All Blackbaud product names appearing herein are trademarks or registered trademarks of Blackbaud, Inc. All other products and company names mentioned herein are trademarks of their respective holder. Security-2014 Contents CONTENTS I SECURITY 1 Fundamentals of Security 1 APPLICATION USERS 3 Search for Users 3 Application User Records 4 Add an Application User 4 Edit Users 5 Delete Users 6 Grant/Revoke Users Administrator Rights 6 Run the Program as a Selected User 6 Organisational Unit Record 7 Application Users Page 8 Manage System Roles of an Application User 8 Add System Roles -
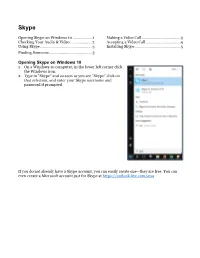
Opening Skype on Windows 10
Skype Opening Skype on Windows 10 ................... 1 Making a Video Call ..................................... 3 Checking Your Audio & Video .................... 2 Accepting a Video Call .................................4 Using Skype ................................................. 3 Installing Skype ........................................... 5 Finding Someone ........................................ 3 Opening Skype on Windows 10 1. On a Windows 10 computer, in the lower left corner click the Windows icon. 2. Type in “Skype” and as soon as you see “Skype” click on that selection, and enter your Skype username and password if prompted. If you do not already have a Skype account, you can easily create one—they are free. You can even create a Microsoft account just for Skype at https://outlook.live.com/owa Checking Your Audio & Video 1. Open Skype. 2. In the left pane, in the top right corner, click on the ellipse (…). 3. Your Settings open. 4. In the left pane, select Audio & Video. 5. In the Camera section your live picture should appear. If it does not, see if there is an option above your picture, and try selecting a different web camera. 6. Scroll down until you see the Audio section. Test your microphone and speakers and adjust the volume as needed. 7. Close the dialog box by clicking the X in the top left corner. Using Skype Once you open Skype, you will select someone to call from the left pane. You have some important options there: Search, Chats, Contacts The first couple times you use Skype you may need to search for your friends and family. You can search by name or email address associated with their Skype account. -

Drivers for Windows NVIDIA Display Properties Desktop User’S Guide
nViewGuide_.book Page 1 Wednesday, May 14, 2003 11:29 PM Drivers for Windows NVIDIA Display Properties Desktop User’s Guide Driver Version: Release 40 4th Edition NVIDIA Corporation May 2003 nViewGuide_.book Page 2 Wednesday, May 14, 2003 11:29 PM NVIDIA Display Properties User’s Guide Published by NVIDIA Corporation 2701 San Tomas Expressway Santa Clara, CA 95050 Copyright © 2003 NVIDIA Corporation. All rights reserved. This software may not, in whole or in part, be copied through any means, mechanical, electromechanical, or otherwise, without the express permission of NVIDIA Corporation. Information furnished is believed to be accurate and reliable. However, NVIDIA assumes no responsibility for the consequences of use of such information nor for any infringement of patents or other rights of third parties, which may result from its use. No License is granted by implication or otherwise under any patent or patent rights of NVIDIA Corporation. Specifications mentioned in the software are subject to change without notice. NVIDIA Corporation products are not authorized for use as critical components in life support devices or systems without express written approval of NVIDIA Corporation. NVIDIA, the NVIDIA logo, Accuview Antialiasing, Detonator, Digital Vibrance Control, GeForce, nForce, nView, NVKeystone, PowerMizer, Quadro, RIVA, TNT, TNT2, TwinView, and Vanta are registered trademarks or trademarks of NVIDIA Corporation in the United States and/or other countries. Intel and Pentium are registered trademarks of Intel. DirectX, Microsoft, Microsoft Internet Explorer logo, Outlook, PowerPoint, Windows, Windows logo, Windows NT, and/or other Microsoft products referenced in this guide are either registered trademarks or trademarks of Microsoft Corporation in the U.S. -
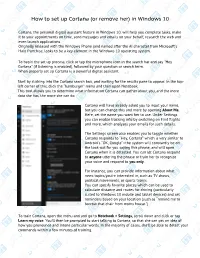
How to Set up Cortana (Or Remove Her) in Windows 10
How to set up Cortana (or remove her) in Windows 10 Cortana, the personal digital assistant feature in Windows 10, will help you complete tasks, make it to your appointments on time, send messages and emails on your behalf, research the web and even launch applications. Orignally released with the Windows Phone (and named after the AI character from Microsoft's Halo franchise, looks to be a key element in the Windows 10 operating system. To begin the set up process, click or tap the microphone icon in the search bar and say "Hey Cortana" (if listening is enabled), followed by your question or search term. When properly set up Cortana is a powerful digital assistant. Start by clicking into the Cortana search box, and waiting for the results pane to appear. In the top- left corner of this, click the “hamburger” menu and then open Notebook. This tool allows you to determine what information Cortana can gather about you, and the more data she has, the more she can do. Cortana will have already asked you to input your name, but you can change this and more by opening About Me. Here, set the name you want her to use. Under Settings you can enable tracking info by switching on Find flights and more, which analyses your emails for such details. The Settings screen also enables you to toggle whether Cortana responds to “Hey, Cortana” which is very similar to Android’s “OK, Google“–the system will constantly be on the look-out for you saying this phrase, and will open Cortana when it is detected. -

Guide to Hardening Windows 10 Technical Guide
NOVEMBER 2020 Guide to Hardening Windows 10 For Administrators, Developers and Office Workers TABLE OF CONTENTS Introduction .......................................................................................................................... 4 Prerequisites ............................................................................................................................ 4 User roles ................................................................................................................................. 4 EFI (BIOS) Configuration ...................................................................................................... 5 To be enabled: ......................................................................................................................... 5 To be disabled: ......................................................................................................................... 5 Windows Defender Firewall .................................................................................................. 6 Enable logging of dropped packets ............................................................................................. 6 Disable enforcement of local rules and disable notifications .......................................................... 7 Block outbound connections by default ....................................................................................... 8 Secure potentially vulnerable protocols ...................................................................................... -

Implementing Remote Credential Guard and Remote Admin Mode on Domain-Joined Windows 10 Clients
INF258x: Implementing Remote Credential Guard and Remote Admin mode on Domain-joined Windows 10 Clients Estimated Time: 30 minutes You have a domain-joined Windows 10 client computer. You plan to take advantage of the Remote Desktop Credential Guard and Restrict Admin mode to protect credentials during Remote Desktop sessions between Windows 10 client and Windows Server 2016 computers. Objectives After completing this lab, students will be able to: • Implement Remote Credential Guard. • Implement the Restricted Admin mode. • Verify functionality of Remote Credential Guard and the Restricted Admin mode. Lab environment The lab consists of the following computers: • LON-DC1 – a Windows Server 2016 domain controller in the adatum.com single-domain forest. • LON-SVR1 – a Windows Server 2016 domain member server • LON-CL1 – a Windows 10 Pro or Enterprise version 1607 (or newer) domain member computer with Remote Server Administration Tools for Windows 10 All computers have Windows PowerShell Remoting enabled and have Internet connectivity Remote Desktop connections protected with Credential Guard have the following characteristics: • Require Windows 10 version 1607 (or newer) or Windows Server 2016 • Enforce of Kerberos authentication (NTLM is not allowed). • Require that both computers (a Remote Desktop client and a Remote Desktop host) are members of the same Active Directory domain or trusted Active Directory domains (Kerberos is enforced) • Support connecting with non-Administrative credentials (as a member of the Remote Desktop Users group) -

Metasys Server Installation and Upgrade Instructions Code No
Metasys Server Installation and Upgrade Instructions Code No. LIT-12012162 Software Release 10.0 Issued April 15, 2019 Welcome.....................................................................................................................................3 Getting Started...........................................................................................................................3 Summary of Changes.........................................................................................................................4 Prerequisite Software Checklist for Installation and Upgrade.......................................................4 Recommended OS and SQL Server Combinations.........................................................................7 Upgrade Pre-Work Checklist..............................................................................................................8 Metasys Server Installation.....................................................................................................10 Installing Unified Metasys Server on Desktop Computer.............................................................10 Installing Unified Metasys Server on Server Computer................................................................12 Installing Unified Metasys Server and SCT on Desktop Computer.............................................14 Installing Unified Metasys Server and SCT on Server Computer................................................17 Installing a Split Metasys Server and SCT.....................................................................................20 -

Lesson 14: Creating and Managing Active Directory Users and Computers
Lesson 14: Creating and Managing Active Directory Users and Computers MOAC 70-410: Installing and Configuring Windows Server 2012 Overview • Exam Objective 5.2: Create and Manage Active Directory Users and Computers • Creating User Objects • Creating Computer Objects • Managing Active Directory Objects © 2013 John Wiley & Sons, Inc. 2 Creating User Objects Lesson 14: Creating and Managing Active Directory Users and Computers © 2013 John Wiley & Sons, Inc. 3 Creating User Objects • The user account is the primary method for authentication on a network. • Usernames and passwords are validated at log on by comparing entered information to the information stored in the AD DS database. © 2013 John Wiley & Sons, Inc. 4 Types of Users • Local users: These accounts can only access resources on the local computer and are stored in the local Security Account Manager (SAM) database on the computer where they reside. • Domain users: These accounts can access AD DS or network-based resources, such as shared folders and printers. o Account information for these users is stored in the AD DS database and replicated to all domain controllers within the same domain. © 2013 John Wiley & Sons, Inc. 5 Built-In User Accounts Administrator and Guest • On a member server or standalone server: The built-in local Administrator account has full control of all files as well as complete management permissions for the local computer. • On a domain controller: The built-in Administrator account created in Active Directory has full control of the domain in which it was created. The Administrator account cannot be deleted, but it can be renamed. © 2013 John Wiley & Sons, Inc. -

Caverns Measureless to Man: Interdisciplinary Planetary Science & Technology Analog Research Underwater Laser Scanner Survey (Quintana Roo, Mexico)
Caverns Measureless to Man: Interdisciplinary Planetary Science & Technology Analog Research Underwater Laser Scanner Survey (Quintana Roo, Mexico) by Stephen Alexander Daire A Thesis Presented to the Faculty of the USC Graduate School University of Southern California In Partial Fulfillment of the Requirements for the Degree Master of Science (Geographic Information Science and Technology) May 2019 Copyright © 2019 by Stephen Daire “History is just a 25,000-year dash from the trees to the starship; and while it’s going on its wild and woolly but it’s only like that, and then you’re in the starship.” – Terence McKenna. Table of Contents List of Figures ................................................................................................................................ iv List of Tables ................................................................................................................................. xi Acknowledgements ....................................................................................................................... xii List of Abbreviations ................................................................................................................... xiii Abstract ........................................................................................................................................ xvi Chapter 1 Planetary Sciences, Cave Survey, & Human Evolution................................................. 1 1.1. Topic & Area of Interest: Exploration & Survey ....................................................................12