Revisiting Pathlib (PDF)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

At—At, Batch—Execute Commands at a Later Time
at—at, batch—execute commands at a later time at [–csm] [–f script] [–qqueue] time [date] [+ increment] at –l [ job...] at –r job... batch at and batch read commands from standard input to be executed at a later time. at allows you to specify when the commands should be executed, while jobs queued with batch will execute when system load level permits. Executes commands read from stdin or a file at some later time. Unless redirected, the output is mailed to the user. Example A.1 1 at 6:30am Dec 12 < program 2 at noon tomorrow < program 3 at 1945 pm August 9 < program 4 at now + 3 hours < program 5 at 8:30am Jan 4 < program 6 at -r 83883555320.a EXPLANATION 1. At 6:30 in the morning on December 12th, start the job. 2. At noon tomorrow start the job. 3. At 7:45 in the evening on August 9th, start the job. 4. In three hours start the job. 5. At 8:30 in the morning of January 4th, start the job. 6. Removes previously scheduled job 83883555320.a. awk—pattern scanning and processing language awk [ –fprogram–file ] [ –Fc ] [ prog ] [ parameters ] [ filename...] awk scans each input filename for lines that match any of a set of patterns specified in prog. Example A.2 1 awk '{print $1, $2}' file 2 awk '/John/{print $3, $4}' file 3 awk -F: '{print $3}' /etc/passwd 4 date | awk '{print $6}' EXPLANATION 1. Prints the first two fields of file where fields are separated by whitespace. 2. Prints fields 3 and 4 if the pattern John is found. -

Unix Introduction
Unix introduction Mikhail Dozmorov Summer 2018 Mikhail Dozmorov Unix introduction Summer 2018 1 / 37 What is Unix Unix is a family of operating systems and environments that exploits the power of linguistic abstractions to perform tasks Unix is not an acronym; it is a pun on “Multics”. Multics was a large multi-user operating system that was being developed at Bell Labs shortly before Unix was created in the early ’70s. Brian Kernighan is credited with the name. All computational genomics is done in Unix http://www.read.seas.harvard.edu/~kohler/class/aosref/ritchie84evolution.pdfMikhail Dozmorov Unix introduction Summer 2018 2 / 37 History of Unix Initial file system, command interpreter (shell), and process management started by Ken Thompson File system and further development from Dennis Ritchie, as well as Doug McIlroy and Joe Ossanna Vast array of simple, dependable tools that each do one simple task Ken Thompson (sitting) and Dennis Ritchie working together at a PDP-11 Mikhail Dozmorov Unix introduction Summer 2018 3 / 37 Philosophy of Unix Vast array of simple, dependable tools Each do one simple task, and do it really well By combining these tools, one can conduct rather sophisticated analyses The Linux help philosophy: “RTFM” (Read the Fine Manual) Mikhail Dozmorov Unix introduction Summer 2018 4 / 37 Know your Unix Unix users spend a lot of time at the command line In Unix, a word is worth a thousand mouse clicks Mikhail Dozmorov Unix introduction Summer 2018 5 / 37 Unix systems Three common types of laptop/desktop operating systems: Windows, Mac, Linux. Mac and Linux are both Unix-like! What that means for us: Unix-like operating systems are equipped with “shells”" that provide a command line user interface. -

Configuring UNIX-Specific Settings: Creating Symbolic Links : Snap
Configuring UNIX-specific settings: Creating symbolic links Snap Creator Framework NetApp September 23, 2021 This PDF was generated from https://docs.netapp.com/us-en/snap-creator- framework/installation/task_creating_symbolic_links_for_domino_plug_in_on_linux_and_solaris_hosts.ht ml on September 23, 2021. Always check docs.netapp.com for the latest. Table of Contents Configuring UNIX-specific settings: Creating symbolic links . 1 Creating symbolic links for the Domino plug-in on Linux and Solaris hosts. 1 Creating symbolic links for the Domino plug-in on AIX hosts. 2 Configuring UNIX-specific settings: Creating symbolic links If you are going to install the Snap Creator Agent on a UNIX operating system (AIX, Linux, and Solaris), for the IBM Domino plug-in to work properly, three symbolic links (symlinks) must be created to link to Domino’s shared object files. Installation procedures vary slightly depending on the operating system. Refer to the appropriate procedure for your operating system. Domino does not support the HP-UX operating system. Creating symbolic links for the Domino plug-in on Linux and Solaris hosts You need to perform this procedure if you want to create symbolic links for the Domino plug-in on Linux and Solaris hosts. You should not copy and paste commands directly from this document; errors (such as incorrectly transferred characters caused by line breaks and hard returns) might result. Copy and paste the commands into a text editor, verify the commands, and then enter them in the CLI console. The paths provided in the following steps refer to the 32-bit systems; 64-bit systems must create simlinks to /usr/lib64 instead of /usr/lib. -

CS101 Lecture 9
How do you copy/move/rename/remove files? How do you create a directory ? What is redirection and piping? Readings: See CCSO’s Unix pages and 9-2 cp option file1 file2 First Version cp file1 file2 file3 … dirname Second Version This is one version of the cp command. file2 is created and the contents of file1 are copied into file2. If file2 already exits, it This version copies the files file1, file2, file3,… into the directory will be replaced with a new one. dirname. where option is -i Protects you from overwriting an existing file by asking you for a yes or no before it copies a file with an existing name. -r Can be used to copy directories and all their contents into a new directory 9-3 9-4 cs101 jsmith cs101 jsmith pwd data data mp1 pwd mp1 {FILES: mp1_data.m, mp1.m } {FILES: mp1_data.m, mp1.m } Copy the file named mp1_data.m from the cs101/data Copy the file named mp1_data.m from the cs101/data directory into the pwd. directory into the mp1 directory. > cp ~cs101/data/mp1_data.m . > cp ~cs101/data/mp1_data.m mp1 The (.) dot means “here”, that is, your pwd. 9-5 The (.) dot means “here”, that is, your pwd. 9-6 Example: To create a new directory named “temp” and to copy mv option file1 file2 First Version the contents of an existing directory named mp1 into temp, This is one version of the mv command. file1 is renamed file2. where option is -i Protects you from overwriting an existing file by asking you > cp -r mp1 temp for a yes or no before it copies a file with an existing name. -

The Different Unix Contexts
The different Unix contexts • User-level • Kernel “top half” - System call, page fault handler, kernel-only process, etc. • Software interrupt • Device interrupt • Timer interrupt (hardclock) • Context switch code Transitions between contexts • User ! top half: syscall, page fault • User/top half ! device/timer interrupt: hardware • Top half ! user/context switch: return • Top half ! context switch: sleep • Context switch ! user/top half Top/bottom half synchronization • Top half kernel procedures can mask interrupts int x = splhigh (); /* ... */ splx (x); • splhigh disables all interrupts, but also splnet, splbio, splsoftnet, . • Masking interrupts in hardware can be expensive - Optimistic implementation – set mask flag on splhigh, check interrupted flag on splx Kernel Synchronization • Need to relinquish CPU when waiting for events - Disk read, network packet arrival, pipe write, signal, etc. • int tsleep(void *ident, int priority, ...); - Switches to another process - ident is arbitrary pointer—e.g., buffer address - priority is priority at which to run when woken up - PCATCH, if ORed into priority, means wake up on signal - Returns 0 if awakened, or ERESTART/EINTR on signal • int wakeup(void *ident); - Awakens all processes sleeping on ident - Restores SPL a time they went to sleep (so fine to sleep at splhigh) Process scheduling • Goal: High throughput - Minimize context switches to avoid wasting CPU, TLB misses, cache misses, even page faults. • Goal: Low latency - People typing at editors want fast response - Network services can be latency-bound, not CPU-bound • BSD time quantum: 1=10 sec (since ∼1980) - Empirically longest tolerable latency - Computers now faster, but job queues also shorter Scheduling algorithms • Round-robin • Priority scheduling • Shortest process next (if you can estimate it) • Fair-Share Schedule (try to be fair at level of users, not processes) Multilevel feeedback queues (BSD) • Every runnable proc. -

Mac Keyboard Shortcuts Cut, Copy, Paste, and Other Common Shortcuts
Mac keyboard shortcuts By pressing a combination of keys, you can do things that normally need a mouse, trackpad, or other input device. To use a keyboard shortcut, hold down one or more modifier keys while pressing the last key of the shortcut. For example, to use the shortcut Command-C (copy), hold down Command, press C, then release both keys. Mac menus and keyboards often use symbols for certain keys, including the modifier keys: Command ⌘ Option ⌥ Caps Lock ⇪ Shift ⇧ Control ⌃ Fn If you're using a keyboard made for Windows PCs, use the Alt key instead of Option, and the Windows logo key instead of Command. Some Mac keyboards and shortcuts use special keys in the top row, which include icons for volume, display brightness, and other functions. Press the icon key to perform that function, or combine it with the Fn key to use it as an F1, F2, F3, or other standard function key. To learn more shortcuts, check the menus of the app you're using. Every app can have its own shortcuts, and shortcuts that work in one app may not work in another. Cut, copy, paste, and other common shortcuts Shortcut Description Command-X Cut: Remove the selected item and copy it to the Clipboard. Command-C Copy the selected item to the Clipboard. This also works for files in the Finder. Command-V Paste the contents of the Clipboard into the current document or app. This also works for files in the Finder. Command-Z Undo the previous command. You can then press Command-Shift-Z to Redo, reversing the undo command. -
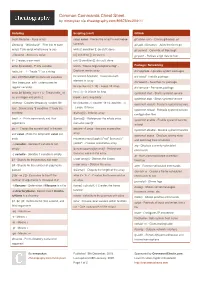
Common Commands Cheat Sheet by Mmorykan Via Cheatography.Com/89673/Cs/20411
Common Commands Cheat Sheet by mmorykan via cheatography.com/89673/cs/20411/ Scripting Scripting (cont) GitHub bash filename - Runs script sleep value - Forces the script to wait value git clone <url > - Clones gitkeeper url Shebang - "# !bi n/b ash " - First line of bash seconds git add <fil ena me> - Adds the file to git script. Tells script what binary to use while [[ condition ]]; do stuff; done git commit - Commits all files to git ./file name - Also runs script if [[ condition ]]; do stuff; fi git push - Pushes all git files to host # - Creates a comment until [[ condition ]]; do stuff; done echo ${varia ble} - Prints variable words=" h ouse dogs telephone dog" - Package / Networking hello_int = 1 - Treats "1 " as a string Declares words array dnf upgrade - Updates system packages Use UPPERC ASE for constant variables for word in ${words} - traverses each dnf install - Installs package element in array Use lowerc ase _wi th_ und ers cores for dnf search - Searches for package for counter in {1..10} - Loops 10 times regular variables dnf remove - Removes package for ((;;)) - Is infinite for loop echo $(( ${hello _int} + 1 )) - Treats hello_int systemctl start - Starts systemd service as an integer and prints 2 break - exits loop body systemctl stop - Stops systemd service mktemp - Creates temporary random file for ((count er=1; counter -le 10; counter ++)) systemctl restart - Restarts systemd service test - Denoted by "[[ condition ]]" tests the - Loops 10 times systemctl reload - Reloads systemd service condition -

Powershell Integration with Vmware View 5.0
PowerShell Integration with VMware® View™ 5.0 TECHNICAL WHITE PAPER PowerShell Integration with VMware View 5.0 Table of Contents Introduction . 3 VMware View. 3 Windows PowerShell . 3 Architecture . 4 Cmdlet dll. 4 Communication with Broker . 4 VMware View PowerCLI Integration . 5 VMware View PowerCLI Prerequisites . 5 Using VMware View PowerCLI . 5 VMware View PowerCLI cmdlets . 6 vSphere PowerCLI Integration . 7 Examples of VMware View PowerCLI and VMware vSphere PowerCLI Integration . 7 Passing VMs from Get-VM to VMware View PowerCLI cmdlets . 7 Registering a vCenter Server . .. 7 Using Other VMware vSphere Objects . 7 Advanced Usage . 7 Integrating VMware View PowerCLI into Your Own Scripts . 8 Scheduling PowerShell Scripts . 8 Workflow with VMware View PowerCLI and VMware vSphere PowerCLI . 9 Sample Scripts . 10 Add or Remove Datastores in Automatic Pools . 10 Add or Remove Virtual Machines . 11 Inventory Path Manipulation . 15 Poll Pool Usage . 16 Basic Troubleshooting . 18 About the Authors . 18 TECHNICAL WHITE PAPER / 2 PowerShell Integration with VMware View 5.0 Introduction VMware View VMware® View™ is a best-in-class enterprise desktop virtualization platform. VMware View separates the personal desktop environment from the physical system by moving desktops to a datacenter, where users can access them using a client-server computing model. VMware View delivers a rich set of features required for any enterprise deployment by providing a robust platform for hosting virtual desktops from VMware vSphere™. Windows PowerShell Windows PowerShell is Microsoft’s command line shell and scripting language. PowerShell is built on the Microsoft .NET Framework and helps in system administration. By providing full access to COM (Component Object Model) and WMI (Windows Management Instrumentation), PowerShell enables administrators to perform administrative tasks on both local and remote Windows systems. -

Backup and Restore Cisco Prime Collaboration Provisioning
Backup and Restore Cisco Prime Collaboration Provisioning This section explains the following: • Perform Backup and Restore, page 1 • Back Up the Single-Machine Provisioning Database, page 2 • Restore the Single-Machine Provisioning Database, page 3 • Schedule Backup Using the Provisioning User Interface, page 5 Perform Backup and Restore Cisco Prime Collaboration Provisioning allows you to backup your data and restore it. You can schedule periodic backups using the Provisioning UI (Schedule Backup Using the Provisioning User Interface, on page 5). There are two backup and restore scenarios; select the set of procedures that matches your scenario: • Backup and restore on a single machine, with the same installation or a new installation. For this scenario, see Schedule Backup Using the Provisioning User Interface, on page 5. Note When backing up files, you should place the files on a different file server. Also, you should burn the backup data onto a CD. Cisco Prime Collaboration Provisioning allows you to back up system data and restore it on a different system in the event of total system failure. To restore the backup from another system, the following prerequisites must be met: • Ensure that the server to which data is restored has the same MAC address as that of the system that was backed up (the IP address and the hostname can be different). • If you are unable to assign the MAC address of the original system (the one that was backed up) to another system, contact the Engineering Team for information on a new license file (for a new MAC address). Cisco Prime Collaboration Provisioning Install and Upgrade Guide, 12.3 1 Backup and Restore Cisco Prime Collaboration Provisioning Back Up the Single-Machine Provisioning Database • The procedure to backup and restore data on a different system is the same as the procedure to backup and restore data on the same system. -

Where Do You Want to Go Today? Escalating
Where Do You Want to Go Today? ∗ Escalating Privileges by Pathname Manipulation Suresh Chari Shai Halevi Wietse Venema IBM T.J. Watson Research Center, Hawthorne, New York, USA Abstract 1. Introduction We analyze filename-based privilege escalation attacks, In this work we take another look at the problem of where an attacker creates filesystem links, thereby “trick- privilege escalation via manipulation of filesystem names. ing” a victim program into opening unintended files. Historically, attention has focused on attacks against priv- We develop primitives for a POSIX environment, provid- ileged processes that open files in directories that are ing assurance that files in “safe directories” (such as writable by an attacker. One classical example is email /etc/passwd) cannot be opened by looking up a file by delivery in the UNIX environment (e.g., [9]). Here, an “unsafe pathname” (such as a pathname that resolves the mail-delivery directory (e.g., /var/mail) is often through a symbolic link in a world-writable directory). In group or world writable. An adversarial user may use today's UNIX systems, solutions to this problem are typ- its write permission to create a hard link or symlink at ically built into (some) applications and use application- /var/mail/root that resolves to /etc/passwd. A specific knowledge about (un)safety of certain directories. simple-minded mail-delivery program that appends mail to In contrast, we seek solutions that can be implemented in the file /var/mail/root can have disastrous implica- the filesystem itself (or a library on top of it), thus providing tions for system security. -

FIFI-LS Highlights Robert Minchin FIFI-LS Highlights
FIFI-LS Highlights Robert Minchin FIFI-LS Highlights • Nice face-on galaxies where [CII] traces star formation [CII] traces star formation in M51 Pineda et al. 2018 [CII] in NGC 6946 Bigiel et al. 2020 [CII] particularly important as H2 & SFR tracer in inter-arm regions FIFI-LS Highlights • Nice face-on galaxies where [CII] traces star formation • Galaxies where [CII] doesn’t trace star formation [CII] from shocks & turbulence in NGC 4258 • [CII] seen along X-ray/radio ‘arms’ of NGC 4258, associated with past or present jet activity • [CII] excited by shocks and turbulence associated with the jet impacting the disk • NOT star formation Appleton et al. 2018 Excess [CII] in HE 1353-1917 1011 HE 1353-1917 1% MUSE RGB Images: 0.1 % • HE 1353-1917 1010 iband[OIII] Hα 0.02 % has a large 109 excess in HE 0433-1028 L[CII]/LFIR 8 10 excess 1σ 10 × 2σ /L 3C 326 3σ HE 1029-1831 • AGN ionization [CII] 7 10 HE 1108-2813 L cone intercepts HE 2211-3903 106 the cold SOFIA AGN Hosts galactic disk AGN Hosts High z 105 LINERs [Brisbin+15] Normal Galaxies LIRGs ULIRGs [Decarli+18] 104 108 109 1010 1011 1012 1013 1014 L /L Smirnova-Pinchukova et al. 2019 FIR Shock-excited [CII] in NGC 2445 [CII] in the ring of NGC 2445 is enhanced compared to PAHs, showing a shock excitement origin rather than star formation Fadda & Appleton, 2020, AAS Meeting 235 FIFI-LS Highlights • Nice face-on galaxies where [CII] traces star formation • Galaxies where [CII] doesn’t trace star formation • Galaxies with gas away from the plane Extraplanar [CII] in edge-on galaxies • Edge-on galaxies NGC 891 & NGC 5907 observed by Reach et al. -

Praat Scripting Tutorial
Praat Scripting Tutorial Eleanor Chodroff Newcastle University July 2019 Praat Acoustic analysis program Best known for its ability to: Visualize, label, and segment audio files Perform spectral and temporal analyses Synthesize and manipulate speech Praat Scripting Praat: not only a program, but also a language Why do I want to know Praat the language? AUTOMATE ALL THE THINGS Praat Scripting Why can’t I just modify others’ scripts? Honestly: power, flexibility, control Insert: all the gifs of ‘you can do it’ and ‘you got this’ and thumbs up Praat Scripting Goals ~*~Script first for yourself, then for others~*~ • Write Praat scripts quickly, effectively, and “from scratch” • Learn syntax and structure of the language • Handle various input/output combinations Tutorial Overview 1) Praat: Big Picture 2) Getting started 3) Basic syntax 4) Script types + Practice • Wav files • Measurements • TextGrids • Other? Praat: Big Picture 1) Similar to other languages you may (or may not) have used before • String and numeric variables • For-loops, if else statements, while loops • Regular expression matching • Interpreted language (not compiled) Praat: Big Picture 2) Almost everything is a mouse click! i.e., Praat is a GUI scripting language GUI = Graphical User Interface, i.e., the Objects window If you ever get lost while writing a Praat script, click through the steps using the GUI Getting Started Open a Praat script From the toolbar, select Praat à New Praat script Save immediately! Save frequently! Script Goals and Input/Output • Consider what