Microservices Best Practices for Java
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Working with Unreliable Observers Using Reactive Extensions
Master thesis WORKING WITH UNRELIABLE OBSERVERS USING REACTIVE EXTENSIONS November 10, 2016 Dorus Peelen (s4167821) Computing science Radboud University [email protected] — Supervisors: Radboud University: Rinus Plasmeijer Aia Software: Jeroen ter Hofstede Contents 1 Introduction 5 1.1 Overview of thesis . .7 2 Background 8 2.1 Aia Software . .8 2.2 Current situation . .8 2.3 The use case . .9 2.3.1 Technical details . 10 2.3.2 Potential problems . 11 2.4 Problem description . 11 2.5 Desired Properties of the new system . 11 3 Overview of Rx 13 3.1 Basic Ideas of Rx . 13 3.2 Observer and Observable . 15 3.3 Hot vs Cold observables . 15 3.4 Marble diagrams . 16 3.5 Transformations on Event Streams . 16 3.6 Schedulers . 16 3.7 Control process in Rx . 17 3.8 Interactive vs reactive . 18 3.9 Push-back and backpressure . 18 3.10 Operators with unbounded Queue . 19 3.11 Explanation and example of different operators in Rx . 19 3.11.1 Select .................................. 19 3.11.2 SelectMany ............................... 20 3.11.3 Where .................................. 20 3.11.4 Delay .................................. 20 3.11.5 Merge and Concat ........................... 21 3.11.6 Buffer and Window ........................... 21 3.11.7 GroupBy ................................. 21 3.11.8 Amb .................................... 21 3.11.9 Debounce, Sample and Throttle ................... 22 3.11.10 ObserveOn ................................ 22 3.12 Related work . 22 3.12.1 TPL . 23 3.12.2 iTasks . 23 4 The experiment 25 4.1 Important properties . 25 4.2 Test architecture . 26 4.2.1 Design . 26 2 4.2.2 Concepts . -
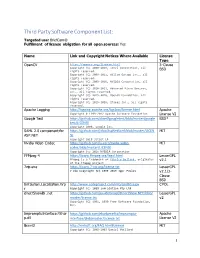
Third Party Software Component List: Targeted Use: Briefcam® Fulfillment of License Obligation for All Open Sources: Yes
Third Party Software Component List: Targeted use: BriefCam® Fulfillment of license obligation for all open sources: Yes Name Link and Copyright Notices Where Available License Type OpenCV https://opencv.org/license.html 3-Clause Copyright (C) 2000-2019, Intel Corporation, all BSD rights reserved. Copyright (C) 2009-2011, Willow Garage Inc., all rights reserved. Copyright (C) 2009-2016, NVIDIA Corporation, all rights reserved. Copyright (C) 2010-2013, Advanced Micro Devices, Inc., all rights reserved. Copyright (C) 2015-2016, OpenCV Foundation, all rights reserved. Copyright (C) 2015-2016, Itseez Inc., all rights reserved. Apache Logging http://logging.apache.org/log4cxx/license.html Apache Copyright © 1999-2012 Apache Software Foundation License V2 Google Test https://github.com/abseil/googletest/blob/master/google BSD* test/LICENSE Copyright 2008, Google Inc. SAML 2.0 component for https://github.com/jitbit/AspNetSaml/blob/master/LICEN MIT ASP.NET SE Copyright 2018 Jitbit LP Nvidia Video Codec https://github.com/lu-zero/nvidia-video- MIT codec/blob/master/LICENSE Copyright (c) 2016 NVIDIA Corporation FFMpeg 4 https://www.ffmpeg.org/legal.html LesserGPL FFmpeg is a trademark of Fabrice Bellard, originator v2.1 of the FFmpeg project 7zip.exe https://www.7-zip.org/license.txt LesserGPL 7-Zip Copyright (C) 1999-2019 Igor Pavlov v2.1/3- Clause BSD Infralution.Localization.Wp http://www.codeproject.com/info/cpol10.aspx CPOL f Copyright (C) 2018 Infralution Pty Ltd directShowlib .net https://github.com/pauldotknopf/DirectShow.NET/blob/ LesserGPL -

Empirical Study on the Usage of Graph Query Languages in Open Source Java Projects
Empirical Study on the Usage of Graph Query Languages in Open Source Java Projects Philipp Seifer Johannes Härtel Martin Leinberger University of Koblenz-Landau University of Koblenz-Landau University of Koblenz-Landau Software Languages Team Software Languages Team Institute WeST Koblenz, Germany Koblenz, Germany Koblenz, Germany [email protected] [email protected] [email protected] Ralf Lämmel Steffen Staab University of Koblenz-Landau University of Koblenz-Landau Software Languages Team Koblenz, Germany Koblenz, Germany University of Southampton [email protected] Southampton, United Kingdom [email protected] Abstract including project and domain specific ones. Common applica- Graph data models are interesting in various domains, in tion domains are management systems and data visualization part because of the intuitiveness and flexibility they offer tools. compared to relational models. Specialized query languages, CCS Concepts • General and reference → Empirical such as Cypher for property graphs or SPARQL for RDF, studies; • Information systems → Query languages; • facilitate their use. In this paper, we present an empirical Software and its engineering → Software libraries and study on the usage of graph-based query languages in open- repositories. source Java projects on GitHub. We investigate the usage of SPARQL, Cypher, Gremlin and GraphQL in terms of popular- Keywords Empirical Study, GitHub, Graphs, Query Lan- ity and their development over time. We select repositories guages, SPARQL, Cypher, Gremlin, GraphQL based on dependencies related to these technologies and ACM Reference Format: employ various popularity and source-code based filters and Philipp Seifer, Johannes Härtel, Martin Leinberger, Ralf Lämmel, ranking features for a targeted selection of projects. -

An Opinionated Guide to Technology Frontiers
TECHNOLOGY RADAR An opinionated guide to technology frontiers Volume 24 #TWTechRadar thoughtworks.com/radar The Technology Advisory Board (TAB) is a group of 20 senior technologists at Thoughtworks. The TAB meets twice a year face-to-face and biweekly by phone. Its primary role is to be an advisory group for Thoughtworks CTO, Contributors Rebecca Parsons. The Technology Radar is prepared by the The TAB acts as a broad body that can look at topics that affect technology and technologists at Thoughtworks. With the ongoing global pandemic, we Thoughtworks Technology Advisory Board once again created this volume of the Technology Radar via a virtual event. Rebecca Martin Fowler Bharani Birgitta Brandon Camilla Cassie Parsons (CTO) (Chief Scientist) Subramaniam Böckeler Byars Crispim Shum Erik Evan Fausto Hao Ian James Lakshminarasimhan Dörnenburg Bottcher de la Torre Xu Cartwright Lewis Sudarshan Mike Neal Perla Rachel Scott Shangqi Zhamak Mason Ford Villarreal Laycock Shaw Liu Dehghani TECHNOLOGY RADAR | 2 © Thoughtworks, Inc. All Rights Reserved. About the Radar Thoughtworkers are passionate about technology. We build it, research it, test it, open source it, write about it and constantly aim to improve it — for everyone. Our mission is to champion software excellence and revolutionize IT. We create and share the Thoughtworks Technology Radar in support of that mission. The Thoughtworks Technology Advisory Board, a group of senior technology leaders at Thoughtworks, creates the Radar. They meet regularly to discuss the global technology strategy for Thoughtworks and the technology trends that significantly impact our industry. The Radar captures the output of the Technology Advisory Board’s discussions in a format that provides value to a wide range of stakeholders, from developers to CTOs. -

Software Architecture: Past, Present, Future
Software Architecture: Past, Present, Future Wilhelm Hasselbring 1 Introduction For large, complex software systems, the design of the overall system structure (the software architecture) is an essential challenge. The architecture of a software system defines that system in terms of components and connections among those components [55, 58]. It is not the design of that system which is more detailed. The architecture shows the correspondence between the requirements and the constructed system, thereby providing some rationale for the design decisions. This level of design has been addressed in a number of ways including informal diagrams and descriptive terms, module interconnection languages, and frameworks for systems that serve the needs of specific application domains. An architecture embodies decisions about quality properties. It represents the earliest opportunity for evaluating those decisions. Furthermore, reusability of components and services depends on how strongly coupled they are with other components in the system architecture. Performance, for instance, depends largely upon the complexity of the required coordination, in particular when the components are distributed via some network. The architecture is usually the first artifact to be examined when a programmer (particularly a maintenance programmer) unfamiliar with the system begins to work on it. Software architecture is often the first design artifact that represents decisions on how requirements of all types are to be achieved. As the manifestation of early design decisions, it represents design decisions that are hardest to change and hence most deserving of careful consideration. W. Hasselbring () Kiel University, Kiel, Germany e-mail: [email protected] © The Author(s) 2018 169 V. -

Reference Guide
Apache Syncope - Reference Guide Version 2.1.9 Table of Contents 1. Introduction. 2 1.1. Identity Technologies. 2 1.1.1. Identity Stores . 2 1.1.2. Provisioning Engines . 4 1.1.3. Access Managers . 5 1.1.4. The Complete Picture . 5 2. Architecture. 7 2.1. Core . 7 2.1.1. REST . 7 2.1.2. Logic . 8 2.1.3. Provisioning . 8 2.1.4. Workflow. 9 2.1.5. Persistence . 9 2.1.6. Security . 9 2.2. Admin UI. 10 2.2.1. Accessibility . 10 2.3. End-user UI. 12 2.3.1. Password Reset . 12 2.3.2. Accessibility . 13 2.4. CLI . 15 2.5. Third Party Applications. 15 2.5.1. Eclipse IDE Plugin . 15 2.5.2. Netbeans IDE Plugin. 15 3. Concepts . 16 3.1. Users, Groups and Any Objects . 16 3.2. Type Management . 17 3.2.1. Schema . 17 Plain . 17 Derived . 18 Virtual . 18 3.2.2. AnyTypeClass . 19 3.2.3. AnyType . 19 3.2.4. RelationshipType . 21 3.2.5. Type Extensions . 22 3.3. External Resources. 23 3.3.1. Connector Bundles . 24 3.3.2. Connector Instance details . 24 3.3.3. External Resource details . 25 3.3.4. Mapping . 26 3.3.5. Linked Accounts . 29 3.4. Realms . 29 3.4.1. Realm Provisioning . 30 3.4.2. LogicActions . 31 3.5. Entitlements. 31 3.6. Privileges . 31 3.7. Roles. 31 3.7.1. Delegated Administration . 32 3.8. Provisioning. 33 3.8.1. Overview. 33 3.8.2. -

Tracking Known Security Vulnerabilities in Third-Party Components
Tracking known security vulnerabilities in third-party components Master’s Thesis Mircea Cadariu Tracking known security vulnerabilities in third-party components THESIS submitted in partial fulfillment of the requirements for the degree of MASTER OF SCIENCE in COMPUTER SCIENCE by Mircea Cadariu born in Brasov, Romania Software Engineering Research Group Software Improvement Group Department of Software Technology Rembrandt Tower, 15th floor Faculty EEMCS, Delft University of Technology Amstelplein 1 - 1096HA Delft, the Netherlands Amsterdam, the Netherlands www.ewi.tudelft.nl www.sig.eu c 2014 Mircea Cadariu. All rights reserved. Tracking known security vulnerabilities in third-party components Author: Mircea Cadariu Student id: 4252373 Email: [email protected] Abstract Known security vulnerabilities are introduced in software systems as a result of de- pending on third-party components. These documented software weaknesses are hiding in plain sight and represent the lowest hanging fruit for attackers. Despite the risk they introduce for software systems, it has been shown that developers consistently download vulnerable components from public repositories. We show that these downloads indeed find their way in many industrial and open-source software systems. In order to improve the status quo, we introduce the Vulnerability Alert Service, a tool-based process to track known vulnerabilities in software projects throughout the development process. Its usefulness has been empirically validated in the context of the external software product quality monitoring service offered by the Software Improvement Group, a software consultancy company based in Amsterdam, the Netherlands. Thesis Committee: Chair: Prof. Dr. A. van Deursen, Faculty EEMCS, TU Delft University supervisor: Prof. Dr. A. -
Unravel Data Systems Version 4.5
UNRAVEL DATA SYSTEMS VERSION 4.5 Component name Component version name License names jQuery 1.8.2 MIT License Apache Tomcat 5.5.23 Apache License 2.0 Tachyon Project POM 0.8.2 Apache License 2.0 Apache Directory LDAP API Model 1.0.0-M20 Apache License 2.0 apache/incubator-heron 0.16.5.1 Apache License 2.0 Maven Plugin API 3.0.4 Apache License 2.0 ApacheDS Authentication Interceptor 2.0.0-M15 Apache License 2.0 Apache Directory LDAP API Extras ACI 1.0.0-M20 Apache License 2.0 Apache HttpComponents Core 4.3.3 Apache License 2.0 Spark Project Tags 2.0.0-preview Apache License 2.0 Curator Testing 3.3.0 Apache License 2.0 Apache HttpComponents Core 4.4.5 Apache License 2.0 Apache Commons Daemon 1.0.15 Apache License 2.0 classworlds 2.4 Apache License 2.0 abego TreeLayout Core 1.0.1 BSD 3-clause "New" or "Revised" License jackson-core 2.8.6 Apache License 2.0 Lucene Join 6.6.1 Apache License 2.0 Apache Commons CLI 1.3-cloudera-pre-r1439998 Apache License 2.0 hive-apache 0.5 Apache License 2.0 scala-parser-combinators 1.0.4 BSD 3-clause "New" or "Revised" License com.springsource.javax.xml.bind 2.1.7 Common Development and Distribution License 1.0 SnakeYAML 1.15 Apache License 2.0 JUnit 4.12 Common Public License 1.0 ApacheDS Protocol Kerberos 2.0.0-M12 Apache License 2.0 Apache Groovy 2.4.6 Apache License 2.0 JGraphT - Core 1.2.0 (GNU Lesser General Public License v2.1 or later AND Eclipse Public License 1.0) chill-java 0.5.0 Apache License 2.0 Apache Commons Logging 1.2 Apache License 2.0 OpenCensus 0.12.3 Apache License 2.0 ApacheDS Protocol -

Return of Organization Exempt from Income
OMB No. 1545-0047 Return of Organization Exempt From Income Tax Form 990 Under section 501(c), 527, or 4947(a)(1) of the Internal Revenue Code (except black lung benefit trust or private foundation) Open to Public Department of the Treasury Internal Revenue Service The organization may have to use a copy of this return to satisfy state reporting requirements. Inspection A For the 2011 calendar year, or tax year beginning 5/1/2011 , and ending 4/30/2012 B Check if applicable: C Name of organization The Apache Software Foundation D Employer identification number Address change Doing Business As 47-0825376 Name change Number and street (or P.O. box if mail is not delivered to street address) Room/suite E Telephone number Initial return 1901 Munsey Drive (909) 374-9776 Terminated City or town, state or country, and ZIP + 4 Amended return Forest Hill MD 21050-2747 G Gross receipts $ 554,439 Application pending F Name and address of principal officer: H(a) Is this a group return for affiliates? Yes X No Jim Jagielski 1901 Munsey Drive, Forest Hill, MD 21050-2747 H(b) Are all affiliates included? Yes No I Tax-exempt status: X 501(c)(3) 501(c) ( ) (insert no.) 4947(a)(1) or 527 If "No," attach a list. (see instructions) J Website: http://www.apache.org/ H(c) Group exemption number K Form of organization: X Corporation Trust Association Other L Year of formation: 1999 M State of legal domicile: MD Part I Summary 1 Briefly describe the organization's mission or most significant activities: to provide open source software to the public that we sponsor free of charge 2 Check this box if the organization discontinued its operations or disposed of more than 25% of its net assets. -

An Experimental Study on Microservices Based Edge Computing Platforms Qian Qu, Ronghua Xu, Seyed Yahya Nikouei, Yu Chen Dept
1 An Experimental Study on Microservices based Edge Computing Platforms Qian Qu, Ronghua Xu, Seyed Yahya Nikouei, Yu Chen Dept. of Electrical & Computer Engineering, Binghamton University, SUNY, Binghamton, NY 13902, USA fqqu2, rxu22, snikoue1, [email protected] Abstract—The rapid technological advances in the Internet of development and easy deployment among multiple service Things (IoT) allows the blueprint of Smart Cities to become providers. feasible by integrating heterogeneous cloud/fog/edge computing Because of many attractive features, such as good scalabil- paradigms to collaboratively provide variant smart services in our cities and communities. Thanks to attractive features like fine ity, fine granularity, loose coupling, continuous development, granularity and loose coupling, the microservices architecture and low maintenance cost, the microservices architecture has has been proposed to provide scalable and extensible services in emerged and gained a lot of interests both in industry and large scale distributed IoT systems. Recent studies have evaluated academic community [17], [21]. Compared to traditional SOAs and analyzed the performance interference between microser- in which the system is a monolithic unit, the microservices vices based on scenarios on the cloud computing environment. However, they are not holistic for IoT applications given the architecture divides an monolithic application into multiple restriction of the edge device like computation consumption and atomic microservices that run independently on distributed network capacity. This paper investigates multiple microservice computing platforms. Each microservice performs one specific deployment policies on edge computing platform. The microser- sub-task or service, which requires less computation resource vices are developed as docker containers, and comprehensive ex- and reduces the communication overhead. -

Towards an Integrated Graph Algebra for Graph Pattern Matching with Gremlin
Towards an Integrated Graph Algebra for Graph Pattern Matching with Gremlin Harsh Thakkar1, S¨orenAuer1;2, Maria-Esther Vidal2 1 Smart Data Analytics Lab (SDA), University of Bonn, Germany 2 TIB & Leibniz University of Hannover, Germany [email protected], [email protected] Abstract. Graph data management (also called NoSQL) has revealed beneficial characteristics in terms of flexibility and scalability by differ- ently balancing between query expressivity and schema flexibility. This peculiar advantage has resulted into an unforeseen race of developing new task-specific graph systems, query languages and data models, such as property graphs, key-value, wide column, resource description framework (RDF), etc. Present-day graph query languages are focused towards flex- ible graph pattern matching (aka sub-graph matching), whereas graph computing frameworks aim towards providing fast parallel (distributed) execution of instructions. The consequence of this rapid growth in the variety of graph-based data management systems has resulted in a lack of standardization. Gremlin, a graph traversal language, and machine provide a common platform for supporting any graph computing sys- tem (such as an OLTP graph database or OLAP graph processors). In this extended report, we present a formalization of graph pattern match- ing for Gremlin queries. We also study, discuss and consolidate various existing graph algebra operators into an integrated graph algebra. Keywords: Graph Pattern Matching, Graph Traversal, Gremlin, Graph Alge- bra 1 Introduction Upon observing the evolution of information technology, we can observe a trend arXiv:1908.06265v2 [cs.DB] 7 Sep 2019 from data models and knowledge representation techniques being tightly bound to the capabilities of the underlying hardware towards more intuitive and natural methods resembling human-style information processing. -

Licensing Information User Manual
Oracle® Database Express Edition Licensing Information User Manual 18c E89902-02 February 2020 Oracle Database Express Edition Licensing Information User Manual, 18c E89902-02 Copyright © 2005, 2020, Oracle and/or its affiliates. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, then the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs (including any operating system, integrated software, any programs embedded, installed or activated on delivered hardware, and modifications of such programs) and Oracle computer documentation or other Oracle data delivered to or accessed by U.S. Government end users are "commercial computer software" or “commercial computer software documentation” pursuant to the applicable Federal