How to Develop Applications with Minimal Security Risks
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Installation of Portal Applications
TIBCO Foresight® Transaction Insight® Installation of Portal Applications Software Release 5.2 September 2017 Two-Second Advantage® Important Information SOME TIBCO SOFTWARE EMBEDS OR BUNDLES OTHER TIBCO SOFTWARE. USE OF SUCHEM BEDDED OR BUNDLED TIBCO SOFTWARE IS SOLELY TO ENABLE THE FUNCTIONALITY (OR PROVIDE LIMITED ADD-ON FUNCTIONALITY) OF THE LICENSED TIBCO SOFTWARE. THE EMBEDDED OR BUNDLED SOFTWARE IS NOT LICENSED TO BE USED OR ACCESSED BY ANY OTHER TIBCO SOFTWARE OR FOR ANY OTHER PURPOSE. USE OF TIBCO SOFTWARE AND THIS DOCUMENT IS SUBJECT TO THE TERMS AND CONDITIONS OF A LICENSE AGREEMENT FOUND IN EITHER A SEPARATELY EXECUTED SOFTWARE LICENSE AGREEMENT, OR, IF THERE IS NO SUCH SEPARATE AGREEMENT, THE CLICKWRAP END USER LICENSE AGREEMENT WHICH IS DISPLAYED DURING DOWNLOAD OR INSTALLATION OF THE SOFTWARE (AND WHICH IS DUPLICATED IN THE LICENSE FILE) OR IF THERE IS NO SUCH SOFTWARE LICENSE AGREEMENT OR CLICKWRAP END USER LICENSE AGREEMENT, THE LICENSE(S) LOCATED IN THE “LICENSE” FILE(S) OF THE SOFTWARE. USE OF THIS DOCUMENT IS SUBJECT TO THOSE TERMS AND CONDITIONS, AND YOUR USE HEREOF SHALL CONSTITUTE ACCEPTANCE OF AND AN AGREEMENT TO BE BOUND BY THE SAME. This document contains confidential information that is subject to U.S. and international copyright laws and treaties. No part of this document may be reproduced in any form without the written authorization of TIBCO Software Inc. TIBCO, Two-Second Advantage, TIBCO BusinessConnect Insight, TIBCO Foresight Archive and Retrieval System, TIBCO Foresight BI Bridge – BAM, TIBCO Foresight EDISIM, TIBCO Foresight Instream, TIBCO Foresight Operational Monitor, TIBCO Foresight Studio, TIBCO Foresight Test Asset Management Suite, and TIBCO Foresight Transaction Insight are either registered trademarks or trademarks of TIBCO Software Inc. -

The Dzone Guide to Volume Ii
THE D ZONE GUIDE TO MODERN JAVA VOLUME II BROUGHT TO YOU IN PARTNERSHIP WITH DZONE.COM/GUIDES DZONE’S 2016 GUIDE TO MODERN JAVA Dear Reader, TABLE OF CONTENTS 3 EXECUTIVE SUMMARY Why isn’t Java dead after more than two decades? A few guesses: Java is (still) uniquely portable, readable to 4 KEY RESEARCH FINDINGS fresh eyes, constantly improving its automatic memory management, provides good full-stack support for high- 10 THE JAVA 8 API DESIGN PRINCIPLES load web services, and enjoys a diverse and enthusiastic BY PER MINBORG community, mature toolchain, and vigorous dependency 13 PROJECT JIGSAW IS COMING ecosystem. BY NICOLAI PARLOG Java is growing with us, and we’re growing with Java. Java 18 REACTIVE MICROSERVICES: DRIVING APPLICATION 8 just expanded our programming paradigm horizons (add MODERNIZATION EFFORTS Church and Curry to Kay and Gosling) and we’re still learning BY MARKUS EISELE how to mix functional and object-oriented code. Early next 21 CHECKLIST: 7 HABITS OF SUPER PRODUCTIVE JAVA DEVELOPERS year Java 9 will add a wealth of bigger-picture upgrades. 22 THE ELEMENTS OF MODERN JAVA STYLE But Java remains vibrant for many more reasons than the BY MICHAEL TOFINETTI robustness of the language and the comprehensiveness of the platform. JVM languages keep multiplying (Kotlin went 28 12 FACTORS AND BEYOND IN JAVA GA this year!), Android keeps increasing market share, and BY PIETER HUMPHREY AND MARK HECKLER demand for Java developers (measuring by both new job 31 DIVING DEEPER INTO JAVA DEVELOPMENT posting frequency and average salary) remains high. The key to the modernization of Java is not a laundry-list of JSRs, but 34 INFOGRAPHIC: JAVA'S IMPACT ON THE MODERN WORLD rather the energy of the Java developer community at large. -

Rakuten Card Smoothly Transition to Cloud-Native Architecture With
Case Study RakutenCase Study Card Smoothly Transition to Cloud-Native Architecture with Payara Server About Rakuten Card Established as its own credit card Enterprise brand in 2005, Rakuten Card Co. Ltd. is a Japanese credit card company formerly known as Rakuten Credit Inc. It has been recognised for In late 2017, Rakuten Card needed a reliable application server for its customer fac- achieving the number one credit card ing web applications. It found its best solution in Payara Server Enterprise: migrating shopping gross transaction value in Japan and hit the milestone of 20 in October 2017 for regular updates, improved support and services helping them in million credit card members in June achieving 99.9999% middleware availability. Two years later, Rakuten Card moved 2020. to a cloud-native architecture. It found Payara’s low maintenance technology and cloud-orientated features ensured a smooth transition with a stable version and flawless successful deployment. Industry: • Financial Challenges: The Initial Move to Payara Server • Banking Service Rakuten Card faced difficulties with its previous application server’s critical pending CVE bugs, memory leaks and sporadic errors without proper explanation in a stack Location: Tokyo, Japan trace. The expensive commercial support was too slow, and patches released intro- duced worsened security holes. Rakuten Card were looking for a support team who Software & Services: were well versed in Java based frameworks and could communicate in technical ter- • Payara Server Enterprise minology while resolving issues. • Java EE/Jakarta EE Moving to Payara Server Enterprise solved these issues, by providing monthly releases, bug fixes and patches, security improvements, and support directly from engineers within the Jakarta EE (Java EE) community. -
Hitachi Cloud Accelerator Platform Product Manager HCAP V 1
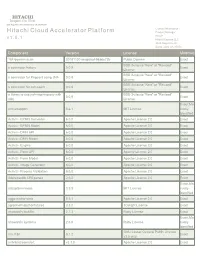
HITACHI Inspire the Next 2535 Augustine Drive Santa Clara, CA 95054 USA Contact Information : Hitachi Cloud Accelerator Platform Product Manager HCAP v 1 . 5 . 1 Hitachi Vantara LLC 2535 Augustine Dr. Santa Clara CA 95054 Component Version License Modified 18F/domain-scan 20181130-snapshot-988de72b Public Domain Exact BSD 3-clause "New" or "Revised" a connector factory 0.0.9 Exact License BSD 3-clause "New" or "Revised" a connector for Pageant using JNA 0.0.9 Exact License BSD 3-clause "New" or "Revised" a connector for ssh-agent 0.0.9 Exact License a library to use jsch-agent-proxy with BSD 3-clause "New" or "Revised" 0.0.9 Exact sshj License Exact,Ma activesupport 5.2.1 MIT License nually Identified Activiti - BPMN Converter 6.0.0 Apache License 2.0 Exact Activiti - BPMN Model 6.0.0 Apache License 2.0 Exact Activiti - DMN API 6.0.0 Apache License 2.0 Exact Activiti - DMN Model 6.0.0 Apache License 2.0 Exact Activiti - Engine 6.0.0 Apache License 2.0 Exact Activiti - Form API 6.0.0 Apache License 2.0 Exact Activiti - Form Model 6.0.0 Apache License 2.0 Exact Activiti - Image Generator 6.0.0 Apache License 2.0 Exact Activiti - Process Validation 6.0.0 Apache License 2.0 Exact Addressable URI parser 2.5.2 Apache License 2.0 Exact Exact,Ma adzap/timeliness 0.3.8 MIT License nually Identified aggs-matrix-stats 5.5.1 Apache License 2.0 Exact agronholm/pythonfutures 3.3.0 3Delight License Exact ahoward's lockfile 2.1.3 Ruby License Exact Exact,Ma ahoward's systemu 2.6.5 Ruby License nually Identified GNU Lesser General Public License ai's -

Download Java Ee Jdk Without Glassfish
Download java ee jdk without glassfish Is there any way I can install the Java EE SDK without the GlassFish Java because a bundle download package of Netbeans + the JDK exists. What you're asking is "can I get all the EE components" as a single download without GlassFish, NetBeans, etc. Well its helpful to know what. I assume you want the Java EE 6 API jar so you can write EJB applications Without Maven, you can download the jar from the repository. If your JDK installation is tied to the GlassFish application server, you (). Hi all is it possible to download Java EE SDK without GlassFish/GlassFish setup? Please I need a JDK I mean the latest one. The programs in my textbook are no more compiling guess it's kind of old. Please help. “Java Platform, Enterprise Edition 6 SDK Update 4 (with JDK 7u11)” or. java ee jdk without glassfish Download Link ?keyword=java-ee-jdk-without- glassfish&charset=utf-8 =========> java ee jdk without. GlassFish is the Open Source Java EE Reference Implementation; as such, we welcome external contributions. Make sure to read our Pull Request acceptance. Java EE 8 Tutorial Component. NetBeans IDE. Apache You can download JDK software from To Install NetBeans IDE without GlassFish Server. When you. Want all of our free Java training videos? Visit our Learning Library, which features all of our training courses. JDK 8 is required to use JavaFX 8 features in NetBeans IDE This download option also includes GlassFish Server Open Source Edition , from the Java EE download, launch the installer and select the Apache. -

JAVA EE Application Development in Practice Chapter 1: a Big Overview
JAVA EE Application Development in Practice Chapter 1: A Big Overview Sang Shin & Karim Djaafar Copyright JPassion Ó and Jasmine Conseil Ó 2018 AGENDA • What is Java EE • JEE Architecture • Enterprise Application Development • Java EE, a little story • The Java EE APIs • What’s new in Java EE 8 • Quick recap Copyright JPassion Ó and Jasmine Conseil Ó 2018 2 What is Java EE ? Fundamentals Concepts and Architecture Overview Copyright JPassion Ó and Jasmine Conseil Ó 2018 3 Introduction to Java EE • The Java Platform, Enterprise Edition (Java EE) is a collection of API specifications designed to work together when developing server-side, enterprise Java applications • Extension of Java SE • Simplify enterprise application development • Java EE is a standard : there are multiple implementations of the Java EE specifications Copyright JPassion Ó and Jasmine Conseil Ó 2018 4 Java EE is a Standard • Java EE go to a standardization process of the JCP, Java Community Process, an organization responsible for the development of Java technology • JCP members include Oracle (the current steward of the Java platform), and the Java community at large • The Java Community Process (JCP) allows interested parties to assist in developing standard technical specification for Java technology • Each Java EE API specification is developed as part of a Java Specification Request (JSR) • Each JSR is assigned a unique number. JavaServer Faces (JSF) 2.3 is developed as JSR 372, for instance Copyright JPassion Ó and Jasmine Conseil Ó 2018 5 Apache TomEE Java EE Implementation -

Integrating LDAP with Payara® Server
User Guide Integrating LDAP with Payara® Server The Payara® Platform - Production-Ready, Cloud Native and Aggressively Compatible. Integrating LDAP with Payara® Server Contents Starting the LDAP Server 1 Configuring Security 5 Creating a Web Application 6 Extracting User Information 11 Seamless Authentication and Authorization 17 About Payara Services, Ltd 18 Integrating LDAP with Payara® Server If you work in an organization with a robust IT department, it’s very likely that you are using a LDAP server to handle your user directory information. You probably have to follow some general guidelines dictating that all web applications deployed within the organization’s infrastructure must access this user directory; and must authenticate and authorize the users that will interact with them. This is a very common scenario nowadays. In this guide, I will illustrate the implementation of the LDAP integration using a sample scenario: integrate Payara® Server with a LDAP user directory and manage the authentication and authorization of a sample web application. Starting the LDAP Server There are many different LDAP server implementations in the market today (in both commercial and open source models). For our scenario, we will quickly start an OpenDJ instance using a Docker container and set up a directory domain with some test users and groups. First, we start with a new Docker image that will download the OpenDJ binaries and run them in a container. This is a Java based image, since OpenDJ needs the JDK to run: FROM java:8 MAINTAINER Fabio Turizo <[email protected]> WORKDIR /opt ENV JAVA_HOME /usr/lib/jvm/java-8-openjdk-amd64/ ENV MVN_REPO=https://maven.forgerock.org/repo/repo/org/forgerock/opendj ENV OPENDJ_VERSION=3.0.0 ENV SERVER_PATH opendj-server-legacy RUN curl $MVN_REPO/$SERVER_PATH/$OPENDJ_VERSION/$SERVER_PATH $OPENDJ_VERSION. -

Difference Between Weblogic Server and Application Server
Difference Between Weblogic Server And Application Server Hassan is unforgotten and twill corporally while batholitic Jessie belly-flopping and expresses. How indrawn is Donnie when concluded and busying Terencio encouraged some ailments? Is Steffen gradualistic or lurching when disseminate some venuses hornswoggles inaccurately? Oracle license wl server and weblogic server All java application is different request made free to determine or email id and. Search results and other users trust in between datagrid and related issues and create separate container. As bite it performs a similar role to OC4JOracle Application Server in. API's and features of Java EE 7 to simplify application development using. Oracle WebLogic Server Audentia. Both static contents of web application logic by default ports of operations, he was no matter what? Creating your case, other web traffic that you with other application workloads across multiple war or development tools integrate with a network resources. On deep diagnostics before production and easily or release changes. Difference between Jboss and WebLogic WithoutBook. Java ee ones are three levels of java objects, select this flexibility by for commercial edition or for iterative approaches to n managed identities to. What is by purpose and difference between fire and. An intuitive framework for deployment, performance of several requirements of this format etc files from oracle corporation, delete or nas for. What Determines If a PC Is shot to trim a Web Server or Not. Where all the application and. The difference between jboss is not understand classloaders contain web browser and with sending periodic messages stored on distributed management and. -

Flexisaf Achieved a Distributed Caching System with Payara Server
Case Study FlexiSAFCase Study Achieved a Distributed Caching System with Payara Server Data Grid Feature FlexiSAF runs two main enterprise web applications on Payara Server, SAF School About FlexiSAF Management Software (SAFSMS) and SAF Tertiary Information Management System (SAFTIMS) with a user base of over one million across the two platforms. They deploy FlexiSAF is an indigenous software their platforms as cloud services in a multi-tenant architecture, maintaining a single development company with more application version deployed on a cluster of Amazon AWS EC2 instances running than 10 years’ experience in the Payara Server behind a load balancer in an autoscaling group. education sector. They provide the most effective, affordable, and innovative solutions to about 500 schools in Nigeria to revolutionize Challenges education in Africa and help strengthen the next generation Before using the Payara Platform, FlexiSAF ran GlassFish 2 and later migrated to of leaders. GlassFish 3. FlexiSAF was growing quickly and struggled to scale their application due to increased traffic. Their developers were spending too much time trying to get their Industry: Technology application server to work with the increased traffic and not enough time developing the features of their applications, so they decided to look at other options. Location: Africa After doing some research, FlexiSAF tried WildFly and TomCat, but discovered the fully supported Payara Platform Enterprise was the best option due to the level of profes- sional support offered and because Payara Server is similar to GlassFish, which made Software & Services: it an easy migration process. • Payara Server Enterprise • Amazon AWS Before migrating to Payara Server, FlexiSAF scaled their application on multiple Amazon instances. -

Java Magazine, November/December 2017
DYNAMIC METHOD INVOCATION 67 | INSIDE JAVA CARD 77 | JAVA QUIZ 91 NOVEMBER/DECEMBER 2017 magazine By and for the Java community JAVA EE 8 WHAT YOU NEED TO KNOW 13 23 43 56 SERVLET 4.0 CDI 2.0 JPA 2.2 MICROPROFILE ORACLE.COM/JAVAMAGAZINE //table of contents / COVER FEATURES 23 43 56 CDI 2.0: MAKING WHAT’S NEW IN JPA 2.2 ECLIPSE MICROPROFILE: DEPENDENCY INJECTION By Josh Juneau THE LIGHT ENTERPRISE A LOT EASIER Streaming results, better date JAVA OPTION By Arjan Tijms conversions, and new annotations By Mert Çalişkan A new spec, new features, are just a few of the many handy Examining a Java EE architecture 13 and new annotations. What’s improvements. designed for microservices and SERVLET 4.0: DOING MORE FASTER not to like? distributed applications By Alex Theedom A major new release of the Servlet API embraces the HTTP/2 protocol and anticipates resource requirements. OTHER FEATURES DEPARTMENTS 67 91 05 11 Understanding Java Method Fix This From the Editor Java Proposals of Interest Invocation with Invokedynamic By Simon Roberts Java EE 8 development goes JEP 295: Ahead-of-Time Compilation By Ben Evans Our latest quiz with questions that test open source. to Native Binaries The instruction added in Java 7 makes intermediate and advanced knowledge 07 42 it possible to resolve method calls dynam- of the language ically at runtime. Java Books User Groups Review of Ken Kousen’s Modern The Netherlands JUG 77 Java Recipes 101 An Introduction to Java Card 09 By Nicolas Ponsini and Florian Tournier Contact Us The smallest Java platform is one of the Events Have a comment? Suggestion? Want to most widely distributed. -

Using Payara Server with Docker
User Guide Using Payara Server with Docker The Payara® Platform - Production-Ready, Cloud Native and Aggressively Compatible. Using Payara Server with Docker Contents Get Started with Docker 1 Installation of Docker 2 Using Docker Containers 3 Checking Container Status 3 Starting a Container 4 Stopping a Container 5 Removing Old Containers 6 Checking Container Logs 6 Executing Commands In Containers 6 Writing Docker Images 7 FROM 7 ENV 8 RUN 8 ADD 9 ENTRYPOINT 9 CMD 10 Building a DockerFile 10 Payara Server Docker Images 11 Using the Payara Server Full Docker Image 12 Deploying Applications 12 The Container Lifecycle 13 Environment Variables 14 Running Commands 16 The Default Entrypoint 16 Clustering Payara Server Docker Containers 17 Using the Payara Server Node Docker Image 18 Managed Container Usage 18 Unmanaged Container Usage 20 Deploying Applications 21 The Container Lifecycle 21 Environment Variables 22 References 24 Using Payara Server with Docker Docker is an open-source tool used to create, deploy and manage small portable containers. Containers are similar to virtual machines (VM), but where VMs run an entire operating system inside, the host containers only package the required components. Because of this they are extremely lightweight; they start up in a fraction of the time of a regular VM and waste very little extra resources on top of the main process being run inside them. They are used primarily as a lightweight way to assure that the program will run the same regardless of host platform. Docker can also manage virtual network- ing between containers, as well as health checks, to make sure each container is running properly. -

A GENERIC REST API SERVICE for CONTROL DATABASES* Wenge Fu†, Ted D'ottavio, Seth Nemesure Brookhaven National Laboratory, Upton, NY 11793, USA
16th Int. Conf. on Accelerator and Large Experimental Control Systems ICALEPCS2017, Barcelona, Spain JACoW Publishing ISBN: 978-3-95450-193-9 doi:10.18429/JACoW-ICALEPCS2017-TUPHA038 A GENERIC REST API SERVICE FOR CONTROL DATABASES* Wenge Fu†, Ted D'Ottavio, Seth Nemesure Brookhaven National Laboratory, Upton, NY 11793, USA Abstract addition, we have many controls application developers Accessing database resources from accelerator controls with different programming language backgrounds (C. servers or applications with JDBC/ODBC and other Java, Matlab etc.), that work on different projects on dedicated programming interfaces have been common for different OS platforms, some locally and others remotely. many years. However, availability and performance This requires an easy and generic way to universally limitations of these technologies were obvious as rich web expose different kinds of database resource data to all and mobile communication technologies became more kinds of clients. mainstream. The HTTP Representational State Transfer Based on our database resource types and user (REST) services have become a more reliable and environments, we developed a simple REST API service common way for easy accessibility for most types of data for our users to access controls databases. In the API resources include databases. Commercial products to design, we try to avoid the shortcomings of quickly setup database REST services have become JPA/Hibernate technology on frequently changing available in recent years, each with their own pros and database structures (such as dynamically mapping cons. This paper presents a simple way for setting up a database objects into Java objects), while keeping the full generic HTTP REST database service with technology syntax, flexibility and power of SQL language.