Interpreting and Unifying Outlier Scores
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A Review on Outlier/Anomaly Detection in Time Series Data
A review on outlier/anomaly detection in time series data ANE BLÁZQUEZ-GARCÍA and ANGEL CONDE, Ikerlan Technology Research Centre, Basque Research and Technology Alliance (BRTA), Spain USUE MORI, Intelligent Systems Group (ISG), Department of Computer Science and Artificial Intelligence, University of the Basque Country (UPV/EHU), Spain JOSE A. LOZANO, Intelligent Systems Group (ISG), Department of Computer Science and Artificial Intelligence, University of the Basque Country (UPV/EHU), Spain and Basque Center for Applied Mathematics (BCAM), Spain Recent advances in technology have brought major breakthroughs in data collection, enabling a large amount of data to be gathered over time and thus generating time series. Mining this data has become an important task for researchers and practitioners in the past few years, including the detection of outliers or anomalies that may represent errors or events of interest. This review aims to provide a structured and comprehensive state-of-the-art on outlier detection techniques in the context of time series. To this end, a taxonomy is presented based on the main aspects that characterize an outlier detection technique. Additional Key Words and Phrases: Outlier detection, anomaly detection, time series, data mining, taxonomy, software 1 INTRODUCTION Recent advances in technology allow us to collect a large amount of data over time in diverse research areas. Observations that have been recorded in an orderly fashion and which are correlated in time constitute a time series. Time series data mining aims to extract all meaningful knowledge from this data, and several mining tasks (e.g., classification, clustering, forecasting, and outlier detection) have been considered in the literature [Esling and Agon 2012; Fu 2011; Ratanamahatana et al. -
Outlier Identification.Pdf
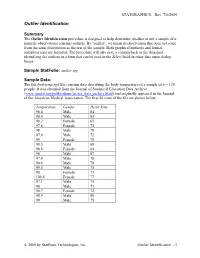
STATGRAPHICS – Rev. 7/6/2009 Outlier Identification Summary The Outlier Identification procedure is designed to help determine whether or not a sample of n numeric observations contains outliers. By “outlier”, we mean an observation that does not come from the same distribution as the rest of the sample. Both graphical methods and formal statistical tests are included. The procedure will also save a column back to the datasheet identifying the outliers in a form that can be used in the Select field on other data input dialog boxes. Sample StatFolio: outlier.sgp Sample Data: The file bodytemp.sgd file contains data describing the body temperature of a sample of n = 130 people. It was obtained from the Journal of Statistical Education Data Archive (www.amstat.org/publications/jse/jse_data_archive.html) and originally appeared in the Journal of the American Medical Association. The first 20 rows of the file are shown below. Temperature Gender Heart Rate 98.4 Male 84 98.4 Male 82 98.2 Female 65 97.8 Female 71 98 Male 78 97.9 Male 72 99 Female 79 98.5 Male 68 98.8 Female 64 98 Male 67 97.4 Male 78 98.8 Male 78 99.5 Male 75 98 Female 73 100.8 Female 77 97.1 Male 75 98 Male 71 98.7 Female 72 98.9 Male 80 99 Male 75 2009 by StatPoint Technologies, Inc. Outlier Identification - 1 STATGRAPHICS – Rev. 7/6/2009 Data Input The data to be analyzed consist of a single numeric column containing n = 2 or more observations. -

A Machine Learning Approach to Outlier Detection and Imputation of Missing Data1
Ninth IFC Conference on “Are post-crisis statistical initiatives completed?” Basel, 30-31 August 2018 A machine learning approach to outlier detection and imputation of missing data1 Nicola Benatti, European Central Bank 1 This paper was prepared for the meeting. The views expressed are those of the authors and do not necessarily reflect the views of the BIS, the IFC or the central banks and other institutions represented at the meeting. A machine learning approach to outlier detection and imputation of missing data Nicola Benatti In the era of ready-to-go analysis of high-dimensional datasets, data quality is essential for economists to guarantee robust results. Traditional techniques for outlier detection tend to exclude the tails of distributions and ignore the data generation processes of specific datasets. At the same time, multiple imputation of missing values is traditionally an iterative process based on linear estimations, implying the use of simplified data generation models. In this paper I propose the use of common machine learning algorithms (i.e. boosted trees, cross validation and cluster analysis) to determine the data generation models of a firm-level dataset in order to detect outliers and impute missing values. Keywords: machine learning, outlier detection, imputation, firm data JEL classification: C81, C55, C53, D22 Contents A machine learning approach to outlier detection and imputation of missing data ... 1 Introduction .............................................................................................................................................. -

Effects of Outliers with an Outlier
• The mean is a good measure to use to describe data that are close in value. • The median more accurately describes data Effects of Outliers with an outlier. • The mode is a good measure to use when you have categorical data; for example, if each student records his or her favorite color, the color (a category) listed most often is the mode of the data. In the data set below, the value 12 is much less than Additional Example 2: Exploring the Effects of the other values in the set. An extreme value such as Outliers on Measures of Central Tendency this is called an outlier. The data shows Sara’s scores for the last 5 35, 38, 27, 12, 30, 41, 31, 35 math tests: 88, 90, 55, 94, and 89. Identify the outlier in the data set. Then determine how the outlier affects the mean, median, and x mode of the data. x x xx x x x 10 12 14 16 18 20 22 24 26 28 30 32 34 36 38 40 42 55, 88, 89, 90, 94 outlier 55 1 Additional Example 2 Continued Additional Example 2 Continued With the Outlier Without the Outlier 55, 88, 89, 90, 94 55, 88, 89, 90, 94 outlier 55 mean: median: mode: mean: median: mode: 55+88+89+90+94 = 416 55, 88, 89, 90, 94 88+89+90+94 = 361 88, 89,+ 90, 94 416 5 = 83.2 361 4 = 90.25 2 = 89.5 The mean is 83.2. The median is 89. There is no mode. -

Outlier Detection in Graphs: a Study on the Impact of Multiple Graph Models
Computer Science and Information Systems 16(2):565–595 https://doi.org/10.2298/CSIS181001010C Outlier Detection in Graphs: A Study on the Impact of Multiple Graph Models Guilherme Oliveira Campos1;2, Edre´ Moreira1, Wagner Meira Jr.1, and Arthur Zimek2 1 Federal University of Minas Gerais Belo Horizonte, Minas Gerais, Brazil fgocampos,edre,[email protected] 2 University of Southern Denmark Odense, Denmark [email protected] Abstract. Several previous works proposed techniques to detect outliers in graph data. Usually, some complex dataset is modeled as a graph and a technique for de- tecting outliers in graphs is applied. The impact of the graph model on the outlier detection capabilities of any method has been ignored. Here we assess the impact of the graph model on the outlier detection performance and the gains that may be achieved by using multiple graph models and combining the results obtained by these models. We show that assessing the similarity between graphs may be a guid- ance to determine effective combinations, as less similar graphs are complementary with respect to outlier information they provide and lead to better outlier detection. Keywords: outlier detection, multiple graph models, ensemble. 1. Introduction Outlier detection is a challenging problem, since the concept of outlier is problem-de- pendent and it is hard to capture the relevant dimensions in a single metric. The inherent subjectivity related to this task just intensifies its degree of difficulty. The increasing com- plexity of the datasets as well as the fact that we are deriving new datasets through the integration of existing ones is creating even more complex datasets. -

How Significant Is a Boxplot Outlier?
Journal of Statistics Education, Volume 19, Number 2(2011) How Significant Is A Boxplot Outlier? Robert Dawson Saint Mary’s University Journal of Statistics Education Volume 19, Number 2(2011), www.amstat.org/publications/jse/v19n2/dawson.pdf Copyright © 2011 by Robert Dawson all rights reserved. This text may be freely shared among individuals, but it may not be republished in any medium without express written consent from the author and advance notification of the editor. Key Words: Boxplot; Outlier; Significance; Spreadsheet; Simulation. Abstract It is common to consider Tukey’s schematic (“full”) boxplot as an informal test for the existence of outliers. While the procedure is useful, it should be used with caution, as at least 30% of samples from a normally-distributed population of any size will be flagged as containing an outlier, while for small samples (N<10) even extreme outliers indicate little. This fact is most easily seen using a simulation, which ideally students should perform for themselves. The majority of students who learn about boxplots are not familiar with the tools (such as R) that upper-level students might use for such a simulation. This article shows how, with appropriate guidance, a class can use a spreadsheet such as Excel to explore this issue. 1. Introduction Exploratory data analysis suddenly got a lot cooler on February 4, 2009, when a boxplot was featured in Randall Munroe's popular Webcomic xkcd. 1 Journal of Statistics Education, Volume 19, Number 2(2011) Figure 1 “Boyfriend” (Feb. 4 2009, http://xkcd.com/539/) Used by permission of Randall Munroe But is Megan justified in claiming “statistical significance”? We shall explore this intriguing question using Microsoft Excel. -

Lecture 14 Testing for Kurtosis
9/8/2016 CHE384, From Data to Decisions: Measurement, Kurtosis Uncertainty, Analysis, and Modeling • For any distribution, the kurtosis (sometimes Lecture 14 called the excess kurtosis) is defined as Testing for Kurtosis 3 (old notation = ) • For a unimodal, symmetric distribution, Chris A. Mack – a positive kurtosis means “heavy tails” and a more Adjunct Associate Professor peaked center compared to a normal distribution – a negative kurtosis means “light tails” and a more spread center compared to a normal distribution http://www.lithoguru.com/scientist/statistics/ © Chris Mack, 2016Data to Decisions 1 © Chris Mack, 2016Data to Decisions 2 Kurtosis Examples One Impact of Excess Kurtosis • For the Student’s t • For a normal distribution, the sample distribution, the variance will have an expected value of s2, excess kurtosis is and a variance of 6 2 4 1 for DF > 4 ( for DF ≤ 4 the kurtosis is infinite) • For a distribution with excess kurtosis • For a uniform 2 1 1 distribution, 1 2 © Chris Mack, 2016Data to Decisions 3 © Chris Mack, 2016Data to Decisions 4 Sample Kurtosis Sample Kurtosis • For a sample of size n, the sample kurtosis is • An unbiased estimator of the sample excess 1 kurtosis is ∑ ̅ 1 3 3 1 6 1 2 3 ∑ ̅ Standard Error: • For large n, the sampling distribution of 1 24 2 1 approaches Normal with mean 0 and variance 2 1 of 24/n 3 5 • For small samples, this estimator is biased D. N. Joanes and C. A. Gill, “Comparing Measures of Sample Skewness and Kurtosis”, The Statistician, 47(1),183–189 (1998). -

Comparison of Data Mining Methods on Different Applications: Clustering and Classification Methods
Inf. Sci. Lett. 4, No. 2, 61-66 (2015) 61 Information Sciences Letters An International Journal http://dx.doi.org/10.12785/isl/040202 Comparison of Data Mining Methods on Different Applications: Clustering and Classification Methods Richard Merrell∗ and David Diaz Department of Computer Engineering, Yerevan University, Yerevan, Armenia. Received: 12 Jan. 2015, Revised: 21 Apr. 2015, Accepted: 24 Apr. 2015 Published online: 1 May 2015 Abstract: Cluster analysis or clustering is the task of grouping a set of objects in such a way that objects in the same group (called a cluster) are more similar (in some sense or another) to each other than to those in other groups (clusters). It is a main task of exploratory data mining, and a common technique for statistical data analysis, used in many fields, including machine learning, pattern recognition, image analysis, information retrieval, and bioinformatics. In this review we study different type if clustering methods. Keywords: Clustering, Data Mining, Ensemble, Big data. 1 Introduction connected by an edge can be considered as a prototypical form of cluster. Relaxations of the complete connectivity According to Vladimir Estivill-Castro, the notion of a requirement (a fraction of the edges can be missing) are ”cluster” cannot be precisely defined, which is one of the known as quasi-cliques. A ”clustering” is essentially a set reasons why there are so many clustering algorithms [1,2, of such clusters, usually containing all objects in the data 3,4]. There is a common denominator: a group of data set. Additionally, it may specify the relationship of the objects. -

A SYSTEMATIC REVIEW of OUTLIERS DETECTION TECHNIQUES in MEDICAL DATA Preliminary Study
A SYSTEMATIC REVIEW OF OUTLIERS DETECTION TECHNIQUES IN MEDICAL DATA Preliminary Study Juliano Gaspar1,2, Emanuel Catumbela1,2, Bernardo Marques1,2 and Alberto Freitas1,2 1Department of Biostatistics and Medical Informatics, Faculty of Medicine, University of Porto, Porto, Portugal 2CINTESIS - Center for Research in Health Technologies and Information Systems University of Porto, Porto, Portugal Keywords: Outliers detection, Data mining, Medical data. Abstract: Background: Patient medical records contain many entries relating to patient conditions, treatments and lab results. Generally involve multiple types of data and produces a large amount of information. These databases can provide important information for clinical decision and to support the management of the hospital. Medical databases have some specificities not often found in others non-medical databases. In this context, outlier detection techniques can be used to detect abnormal patterns in health records (for instance, problems in data quality) and this contributing to better data and better knowledge in the process of decision making. Aim: This systematic review intention to provide a better comprehension about the techniques used to detect outliers in healthcare data, for creates automatisms for those methods in the order to facilitate the access to information with quality in healthcare. Methods: The literature was systematically reviewed to identify articles mentioning outlier detection techniques or anomalies in medical data. Four distinct bibliographic databases were searched: Medline, ISI, IEEE and EBSCO. Results: From 4071 distinct papers selected, 80 were included after applying inclusion and exclusion criteria. According to the medical specialty 32% of the techniques are intended for oncology and 37% of them using patient data. -

Recommended Methods for Outlier Detection and Calculations Of
Recommended Methods for Outlier Detection and Calculations of Tolerance Intervals and Percentiles – Application to RMP data for Mercury-, PCBs-, and PAH-contaminated Sediments Final Report May 27th, 2011 Prepared for: Regional Monitoring Program for Water Quality in San Francisco Bay, Oakland CA Prepared by: Dr. Don L. Stevens, Jr. Principal Statistician Stevens Environmental Statistics, LLC 6200 W. Starr Road Wasilla, AK 99654 Introduction This report presents results of a review of existing methods for outlier detection and for calculation of percentiles and tolerance intervals. Based on the review, a simple method of outlier detection that could be applied annually as new data becomes available is recommended along with a recommendation for a method for calculating tolerance intervals for population percentiles. The recommended methods are applied to RMP probability data collected in the San Francisco Estuary from 2002 through 2009 for Hg, PCB, and PAH concentrations. Outlier detection There is a long history in statistics of attempts to identify outliers, which are in some sense data points that are unusually high or low . Barnett and Lewis (1994) define an outlier in a set of data as “an observation (or subset of observations) which appears to be inconsistent with the remainder of that set of data. This captures the intuitive notion, but does not provide a constructive pathway. Hawkins (1980) defined outliers as data points which are generated by a different distribution than the bulk observations. Hawkins definition suggests something like using a mixture distribution to separate the data into one or more distributions, or, if outliers are few relative to the number of data points, to fit the “bulk” distribution with a robust/resistant estimation procedure, and then determine which points do not conform to the bulk distribution. -

Identify the Outlier in the Data Set. Determine How the Outlier Affects the Mean, Median, and Mode of the Data
11-5 Appropriate Measures 1. The number of minutes spent studying are: 60, 70, 45, 60, 80, 35, and 45. Find the measure of center that best represents the data. Justify your selection and then find the measure of center. ANSWER: The mean best represents the data. There are no extreme values. mean: 56.4 minutes median: 2. The table shows monthly rainfall in inches for five months. Identify the outlier in the data set. Determine how the outlier affects the mean, median, and mode of the data. Then tell which measure of center best describes the data with and without the outlier. Round to the nearest hundredth. Justify your selection. ANSWER: outlier: 2.43 in.; without the outlier: mean: 7.36 in., median: 7.19 in., mode: none; with the outlier: mean: 6.54 in., median: 6.83 in., mode: none; The mean rainfall best describes the data without the outlier. The median rainfall best describes the data with the outlier. 3. The table shows the average depth of several lakes. a. Identify the outlier in the data set. b. Determine how the outlier affects the mean, median, mode, and range eSolutionsof theManual data.- Powered by Cognero Page 1 c. Tell which measure of central tendency best describes the data with and without the outlier. ANSWER: a. 1,148 b. With the outlier, the mean is 216.83 ft, the median is 33.5 ft, there is no mode, and the range is 1,138. Without the outlier, the mean is 30.6 ft, the median is 24 ft, there is no mode, and the range is 52. -

Topics in Biostatistics: Part II
Basic Statistics for Virology Sarah J. Ratcliffe, Ph.D. Center for Clinical Epidemiology and Biostatistics U. Penn School of Medicine Email: [email protected] September 2011 CCEB Outline Summarizing the Data Hypothesis testing Example Interpreting results Resources CCEB Summarizing the Data Two basic aspects of data Centrality Variability Different measures for each Optimal measure depends on type of data being described CCEB Centrality Mean Sum of observed values divided by number of observations Most common measure of centrality Most informative when data follow normal distribution (bell-shaped curve) Median “middle” value: half of all observed values are smaller, half are larger Best centrality measure when data are skewed Mode Most frequently observed value CCEB Mean can Mislead Group 1 data: 1,1,1,2,3,3,5,8,20 Mean: 4.9 Median: 3 Mode: 1 Group 2 data: 1,1,1,2,3,3,5,8,10 Mean: 3.8 Median: 3 Mode: 1 When data sets are small, a single extreme observation will have great influence on mean, little or no influence on median In such cases, median is usually a more informative measure of centrality CCEB CCEB CCEB Variability Most commonly used measure to describe variability is standard deviation (SD) SD is a function of the squared differences of each observation from the mean If the mean is influenced by a single extreme observation, the SD will overstate the actual variability CCEB Variability SD describes variability in original data SE = SD / √n describes variability in the mean. Confidence intervals for the mean use SE e.g. Mean ± t* SE Confidence interval for predicted observation uses SD.