The Peril of Fragmentation: Security Hazards in Android Device Driver Customizations
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Response Data 910 14
Count of Type Desc. Total [40 (DUMMY) DISPLAY PHONES] 1 [BLACKBERRY] 2 [CHARGER] 1 [COVERS] 1 [FLIPTOP PHONE] 1 [HC1] 1 [HDCI M8 MOBILE PHONE] 1 [HUAWEI] 1 [I PHONE 4] 2 [I PHONE 5] 2 [I PHONE 5C] 1 [I PHONE 5S] 1 [I PHONE] 1 [IPHONE 5 WHITE IN COLOUR] 1 [IPHONE 5S] 1 [IPHONE 6] 1 [IPHONE CHARGER] 2 [IPHONE CHARGERS] 1 [IPHONE PHONE CHARGER] 1 [IPHONE] 2 [MOBILE PHONE AND CHARGED] 1 [MOBILE PHONE BATTERY] 1 [MOBILE PHONE CASE] 1 [MOBILE PHONE FOR SENIOR] 1 [MOBILE PHONE] 16 [MOBILE TELEPHONE - UNKNOWN DETAILS] 1 [MOBILE TELEPHONE] 4 [MOTOROLA] 1 [NOKIA LUMINA 530 MOBILE PHONE] 1 [NOKIA MOBILE] 1 [PHONE CHARGER] 1 [PHONE SIM CARD] 1 [SAMSUNG GALAXY S3 MINI] 1 [SAMSUNG] 1 [SIM CARD] 2 [SMART PHONE] 1 [SONY XPERIA Z1] 1 [SONY XPERIA Z2] 1 [TABLET] 1 [TELEPHONE CABLE] 1 [TESCO MOBILE PHONE] 1 [TESCO] 1 [UNKNOWN MAKE OF MOBILE PHONE] 1 [WORKS AND PERSONAL] 1 1PHONE 4S 1 3 [3 SIM CARD] 1 3G 1 4 [I PHONE] 1 4S 1 ACCESSORIES [CHARGER AND PHONE COVER] 1 ACER 2 ACER LIQUID 1 ACER LIQUID 3 1 ACER LIQUID 4Z [MOBILE TELEPHONE] 1 ACER LIQUID E 1 ACER LIQUID E2 1 ACER LIQUID E3 1 ACTEL [MOBILE PHONE] 1 ALCATEL 6 ALCATEL [MOBILE PHONE] 3 ALCATEL ITOUCH [ALCATEL ITOUCH] 1 ALCATEL ONE 232 1 ALCATEL ONE TOUCH 6 ALCATEL ONE TOUCH [TRIBE 30GB] 1 ALCATEL ONE TOUCH TRIBE 3040 1 ALCATELL 1 ANDROID [TABLET] 1 APHONE 5 1 APLE IPHONE 5C 1 APLLE I PHONE 5S 2 APLLE IPHONE 4 1 APPL I PHONE 4 1 APPLE 11 APPLE [I PHONE] 1 APPLE [IPHONE] 1 APPLE [MOBILE PHONE CHARGER] 1 APPLE 1 PHONE 4 1 APPLE 1 PHONE 5 1 APPLE 1 PHONE 5 [I PHONE] 1 APPLE 3GS [3GS] 1 APPLE 4 3 APPLE 4 -

Electronic 3D Models Catalogue (On July 26, 2019)
Electronic 3D models Catalogue (on July 26, 2019) Acer 001 Acer Iconia Tab A510 002 Acer Liquid Z5 003 Acer Liquid S2 Red 004 Acer Liquid S2 Black 005 Acer Iconia Tab A3 White 006 Acer Iconia Tab A1-810 White 007 Acer Iconia W4 008 Acer Liquid E3 Black 009 Acer Liquid E3 Silver 010 Acer Iconia B1-720 Iron Gray 011 Acer Iconia B1-720 Red 012 Acer Iconia B1-720 White 013 Acer Liquid Z3 Rock Black 014 Acer Liquid Z3 Classic White 015 Acer Iconia One 7 B1-730 Black 016 Acer Iconia One 7 B1-730 Red 017 Acer Iconia One 7 B1-730 Yellow 018 Acer Iconia One 7 B1-730 Green 019 Acer Iconia One 7 B1-730 Pink 020 Acer Iconia One 7 B1-730 Orange 021 Acer Iconia One 7 B1-730 Purple 022 Acer Iconia One 7 B1-730 White 023 Acer Iconia One 7 B1-730 Blue 024 Acer Iconia One 7 B1-730 Cyan 025 Acer Aspire Switch 10 026 Acer Iconia Tab A1-810 Red 027 Acer Iconia Tab A1-810 Black 028 Acer Iconia A1-830 White 029 Acer Liquid Z4 White 030 Acer Liquid Z4 Black 031 Acer Liquid Z200 Essential White 032 Acer Liquid Z200 Titanium Black 033 Acer Liquid Z200 Fragrant Pink 034 Acer Liquid Z200 Sky Blue 035 Acer Liquid Z200 Sunshine Yellow 036 Acer Liquid Jade Black 037 Acer Liquid Jade Green 038 Acer Liquid Jade White 039 Acer Liquid Z500 Sandy Silver 040 Acer Liquid Z500 Aquamarine Green 041 Acer Liquid Z500 Titanium Black 042 Acer Iconia Tab 7 (A1-713) 043 Acer Iconia Tab 7 (A1-713HD) 044 Acer Liquid E700 Burgundy Red 045 Acer Liquid E700 Titan Black 046 Acer Iconia Tab 8 047 Acer Liquid X1 Graphite Black 048 Acer Liquid X1 Wine Red 049 Acer Iconia Tab 8 W 050 Acer -
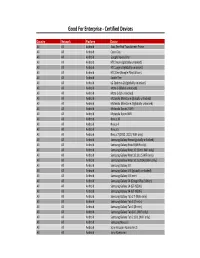
MMS Copy of Supported Devices
Good For Enterprise ‐ Certified Devices Country Network Platform Device All All Android Asus Eee Pad Transformer Prime All All Android Cisco Cius All All Android Google Nexus One All All Android HTC Desire (globally unlocked) All All Android HTC Legend (globally unlocked) All All Android HTC One (Google Play Edition) All All Android Kindle Fire All All Android LG Optimus 2X (globally unlocked) All All Android Moto G (Global unlocked) All All Android Moto G (US unlocked) All All Android Motorola Milestone (globally unlocked) All All Android Motorola Milestone 2 (globally unlocked) All All Android Motorola Xoom 2 WiFi All All Android Motorola Xoom WiFi All All Android Nexus 10 All All Android Nexus 4 All All Android Nexus 5 All All Android Nexus 7 (2012, 2013, WiFi only) All All Android Samsung Galaxy Nexus (globally unlocked) All All Android Samsung Galaxy Note 8 (WiFi only) All All Android Samsung Galaxy Note 10.1 (Intl. WiFi only) All All Android Samsung Galaxy Note 10.1 (U.S WiFi only) All All Android Samsung Galaxy Note 10.1 (2014) (WiFi only) All All Android Samsung Galaxy S II All All Android Samsung Galaxy S III (globally unlocked) All All Android Samsung Galaxy S III mini All All Android Samsung Galaxy S4 (Google Play Edition) All All Android Samsung Galaxy S4 (GT‐I9500) All All Android Samsung Galaxy S4 (GT‐I9505) All All Android Samsung Galaxy Tab 2 7 (WiFi only) All All Android Samsung Galaxy Tab 3 (7‐inch) All All Android Samsung Galaxy Tab 3 (8‐inch) All All Android Samsung Galaxy Tab 10.1 (WiFi only) All All Android Samsung -

Bedienungsanleitung Samsung Galaxy Ace 3
GT-S7275R Benutzerhandbuch www.samsung.com Über dieses Handbuch Dieses Gerät bietet Ihnen dank der hohen Standards und dem technologischen Know-how von Samsung mobile Kommunikationsmöglichkeiten und Unterhaltung höchster Qualität. Dieses Handbuch erklärt die Funktionen und Anwendungen des Geräts. • Lesen Sie dieses Handbuch vor der Verwendung des Geräts aufmerksam durch, um seine sichere und sachgemäße Verwendung zu gewährleisten. • Beschreibungen basieren auf den Standardeinstellungen des Geräts. • Bilder und Screenshots können vom Aussehen des tatsächlichen Produkts abweichen. • Der Inhalt unterscheidet sich möglicherweise vom Endprodukt oder von Software, die von Dienstanbietern oder Netzbetreibern bereitgestellt wird, und Samsung behält sich das Recht vor, Änderungen ohne vorherige Ankündigung vorzunehmen. Eine aktuelle Version dieses Handbuchs finden Sie auf der Samsung-Webseite www.samsung.com • Hochwertige Inhalte, bei denen für die Verarbeitung hohe CPU- und RAM-Leistungen erforderlich sind, wirken sich auf die Gesamtleistung des Geräts aus. Anwendungen, die mit diesen Inhalten zusammenhängen, funktionieren abhängig von den technischen Daten des Geräts und der Umgebung, in der es genutzt wird, möglicherweise nicht ordnungsgemäß. • Die verfügbaren Funktionen und zusätzlichen Dienste können sich je nach Gerät, Software und Netzbetreiber unterscheiden. • Anwendungen und ihre Funktionen können sich je nach Land, Region oder Hardwarespezifikationen unterscheiden. Samsung übernimmt keinerlei Haftung für Leistungsprobleme, die von Anwendungen -

HR Kompatibilitätsübersicht
HR-imotion Kompatibilität/Compatibility 2018 / 11 Gerätetyp Telefon 22410001 23010201 22110001 23010001 23010101 22010401 22010501 22010301 22010201 22110101 22010701 22011101 22010101 22210101 22210001 23510101 23010501 23010601 23010701 23510320 22610001 23510420 Smartphone Acer Liquid Zest Plus Smartphone AEG Voxtel M250 Smartphone Alcatel 1X Smartphone Alcatel 3 Smartphone Alcatel 3C Smartphone Alcatel 3V Smartphone Alcatel 3X Smartphone Alcatel 5 Smartphone Alcatel 5v Smartphone Alcatel 7 Smartphone Alcatel A3 Smartphone Alcatel A3 XL Smartphone Alcatel A5 LED Smartphone Alcatel Idol 4S Smartphone Alcatel U5 Smartphone Allview P8 Pro Smartphone Allview Soul X5 Pro Smartphone Allview V3 Viper Smartphone Allview X3 Soul Smartphone Allview X5 Soul Smartphone Apple iPhone Smartphone Apple iPhone 3G / 3GS Smartphone Apple iPhone 4 / 4S Smartphone Apple iPhone 5 / 5S Smartphone Apple iPhone 5C Smartphone Apple iPhone 6 / 6S Smartphone Apple iPhone 6 Plus / 6S Plus Smartphone Apple iPhone 7 Smartphone Apple iPhone 7 Plus Smartphone Apple iPhone 8 Smartphone Apple iPhone 8 Plus Smartphone Apple iPhone SE Smartphone Apple iPhone X Smartphone Apple iPhone XR Smartphone Apple iPhone Xs Smartphone Apple iPhone Xs Max Smartphone Archos 50 Saphir Smartphone Archos Diamond 2 Plus Smartphone Archos Saphir 50x Smartphone Asus ROG Phone Smartphone Asus ZenFone 3 Smartphone Asus ZenFone 3 Deluxe Smartphone Asus ZenFone 3 Zoom Smartphone Asus Zenfone 5 Lite ZC600KL Smartphone Asus Zenfone 5 ZE620KL Smartphone Asus Zenfone 5z ZS620KL Smartphone Asus -

Phone Compatibility
Phone Compatibility • Compatible with iPhone models 4S and above using iOS versions 7 or higher. Last Updated: February 14, 2017 • Compatible with phone models using Android versions 4.1 (Jelly Bean) or higher, and that have the following four sensors: Accelerometer, Gyroscope, Magnetometer, GPS/Location Services. • Phone compatibility information is provided by phone manufacturers and third-party sources. While every attempt is made to ensure the accuracy of this information, this list should only be used as a guide. As phones are consistently introduced to market, this list may not be all inclusive and will be updated as new information is received. Please check your phone for the required sensors and operating system. Brand Phone Compatible Non-Compatible Acer Acer Iconia Talk S • Acer Acer Jade Primo • Acer Acer Liquid E3 • Acer Acer Liquid E600 • Acer Acer Liquid E700 • Acer Acer Liquid Jade • Acer Acer Liquid Jade 2 • Acer Acer Liquid Jade Primo • Acer Acer Liquid Jade S • Acer Acer Liquid Jade Z • Acer Acer Liquid M220 • Acer Acer Liquid S1 • Acer Acer Liquid S2 • Acer Acer Liquid X1 • Acer Acer Liquid X2 • Acer Acer Liquid Z200 • Acer Acer Liquid Z220 • Acer Acer Liquid Z3 • Acer Acer Liquid Z4 • Acer Acer Liquid Z410 • Acer Acer Liquid Z5 • Acer Acer Liquid Z500 • Acer Acer Liquid Z520 • Acer Acer Liquid Z6 • Acer Acer Liquid Z6 Plus • Acer Acer Liquid Zest • Acer Acer Liquid Zest Plus • Acer Acer Predator 8 • Alcatel Alcatel Fierce • Alcatel Alcatel Fierce 4 • Alcatel Alcatel Flash Plus 2 • Alcatel Alcatel Go Play • Alcatel Alcatel Idol 4 • Alcatel Alcatel Idol 4s • Alcatel Alcatel One Touch Fire C • Alcatel Alcatel One Touch Fire E • Alcatel Alcatel One Touch Fire S • 1 Phone Compatibility • Compatible with iPhone models 4S and above using iOS versions 7 or higher. -

HR Kompatibilitätsübersicht
Kompatibilitätsübersicht HR-imotion HR-imotion Kompatibilität/Compatibility 2017 / 03 Gerätetyp Telefon 22410001 23010201 22110001 23010001 23010101 22010401 22010501 22010301 22010201 22110101 22010701 22011101 22010101 22210101 22210001 23510101 23010501 23010601 23010701 23510320 22610001 23510420 Smartphone Acer Liquid Zest Plus Smartphone AEG Voxtel M250 Smartphone Alcatel A3 Smartphone Alcatel A3 XL Smartphone Alcatel A5 LED Smartphone Alcatel Idol 4S Smartphone Alcatel U5 Smartphone Allview X3 Soul Smartphone Apple iPhone Smartphone Apple iPhone 3G / 3GS Smartphone Apple iPhone 4 / 4S Smartphone Apple iPhone 5 / 5S Smartphone Apple iPhone 5C Smartphone Apple iPhone 6 / 6S Smartphone Apple iPhone 6 Plus / 6S Plus Smartphone Apple iPhone 7 Smartphone Apple iPhone 7 Plus Smartphone Apple iPhone SE Smartphone Archos 50 Saphir Smartphone Archos Diamond 2 Plus Smartphone Asus ZenFone 3 Smartphone Asus ZenFone 3 Deluxe Smartphone Asus ZenFone 3 Zoom Smartphone Asus ZenFone AR Smartphone BlackBerry Classic Smartphone Blackberry DTEK 50 Smartphone Blackberry KEYOne Smartphone BlackBerry Passport Smartphone BlackBerry Priv Smartphone BlackBerry Z30 Smartphone BQ Aquaris X5 Smartphone BQ Aquaris X5 Plus Smartphone CAT B15 Smartphone Cubot P11 Smartphone Cubot S500 Smartphone Elephone P8000 Smartphone Emporia Pure Smartphone Gigaset GS160 Smartphone Gigaset ME Smartphone Gigaset ME Pro Smartphone Gigaset ME Pure Smartphone Google Nexus 5 Smartphone Google Nexus 5X Smartphone Google Nexus 6 Smartphone Google Nexus 6P Smartphone Google Pixel -

Baromètre Des Connexions Internet Mobiles En Polynésie Française. Publication Du 12 Mars 2020
Baromètre des Connexions Internet Mobiles en Polynésie Française. Publication du 12 Mars 2020 Rapport 2019 nPerf est un service proposé par la société nPerf, située 87 rue de Sèze 69006 LYON – France. Table des matières 1 Synthèse des résultats annuels globaux ..................................................................................... 2 1.1 Scores nPerf, toutes technologies confondues ................................................................... 2 1.2 Notre analyse ........................................................................................................................ 3 2 Les résultats annuels globaux ..................................................................................................... 3 2.1 Taux de réussite .................................................................................................................... 4 2.2 Débits descendants .............................................................................................................. 4 2.3 Débits montants .................................................................................................................... 5 2.4 Temps de réponse (Latence) ................................................................................................ 6 2.5 Qualité de service .................................................................................................................. 6 2.5.1 Navigation ..................................................................................................................... -

Manual Samsung Galaxy Ace Duos Gt S6802b Price in India 2012
Manual Samsung Galaxy Ace Duos Gt S6802b Price In India 2012 Samsung S6802 (5 Jul 2015) - Samsung S6802 price in India now at Rs 8197. Phone comes with Charger + Headphones. its a 2012 Model. Samsung Galaxy Ace Duos S6802 Vs Samsung Galaxy S Duos S7562 · Samsung S6802 Vs. Junglee.com: Buy Samsung Galaxy Ace Duos S6802 Battery at Lowest Price from online sellers within India. Read Samsung If you have a Samsung Galaxy Ace Duos S6802, we have good news for you. The good news is Follow us. Conditions of Use & Sale · Privacy Notice, © 2012-2015 Junglee.com or its affiliates. ». Always On with GALAXY Ace DUOS You always go 100% - whether you're at work or at play. That's why you'll settle for nothing less than Samsung's GALAXY. Minimum Order is 3 Phones To Qualify For These Trade Prices G808, G810, Galaxy Ace 3 Duos - GT-S7272C, Galaxy Ace 3 LTE - GT-S7275B, Galaxy Ace 3. Compare Samsung Galaxy Ace S5830I Prices in India and Buy online across Box Contents, Handset, Battery, Charger, Earphone, USB Cable, User Manual, Warranty Card. Also Known As, Samsung Galaxy Ace GT-S5830i Samsung Galaxy Ace Duos S6802 Price: Rs. 6,999. 47 Like · Reply · Oct 31, 2012 12:44am. View Delivery Options & Pricing. Ask us something. Questions about this item? Email us. Why Mobile Fun? Unbeatable Range & Choice, Order By 6pm For. Manual Samsung Galaxy Ace Duos Gt S6802b Price In India 2012 >>>CLICK HERE<<< We now have 374 ads from 15 sites for samsung galaxy s duos price black, Released 2012, September BODY Dimensions 121.5 x. -

Fnac Reprise
FNAC REPRISE Liste des smartphones éligibles au programme de reprise au 19/08/2016 ACER LIQUID Z4 APPLE IPHONE 5 BLACK 64GB ACER INCORPORATED LIQUID Z530S APPLE IPHONE 5 WHITE 16GB ACER INCORPORATED LIQUID Z630S APPLE IPHONE 5 WHITE 32GB ALBA ALBA 4.5INCH 5MP 4G 8GB APPLE IPHONE 5 WHITE 64GB ALBA DUAL SIM APPLE IPHONE 5C ALCATEL IDOL 3 8GB APPLE IPHONE 5C BLUE 16GB ALCATEL ONE TOUCH 228 APPLE IPHONE 5C BLUE 32GB ALCATEL ONE TOUCH 903 APPLE IPHONE 5C BLUE 8GB ALCATEL ONE TOUCH 903X APPLE IPHONE 5C GREEN 16GB ALCATEL ONE TOUCH IDOL 2 MINI S APPLE IPHONE 5C GREEN 32GB ALCATEL ONE TOUCH TPOP APPLE IPHONE 5C GREEN 8GB ALCATEL ONETOUCH POP C3 APPLE IPHONE 5C PINK 16GB AMAZON FIRE PHONE APPLE IPHONE 5C PINK 32GB APPLE APPLE WATCH EDITION 42MM APPLE IPHONE 5C PINK 8GB APPLE IPHONE 3G APPLE IPHONE 5C WHITE 16GB APPLE IPHONE 3G BLACK 16GB APPLE IPHONE 5C WHITE 32GB APPLE IPHONE 3G BLACK 8GB APPLE IPHONE 5C WHITE 8GB APPLE IPHONE 3G WHITE 16GB APPLE IPHONE 5C YELLOW 16GB APPLE IPHONE 3GS APPLE IPHONE 5C YELLOW 32GB APPLE IPHONE 3GS 8GB APPLE IPHONE 5C YELLOW 8GB APPLE IPHONE 3GS BLACK 16GB APPLE IPHONE 5S APPLE IPHONE 3GS BLACK 32GB APPLE IPHONE 5S BLACK 16GB APPLE IPHONE 3GS WHITE 16GB APPLE IPHONE 5S BLACK 32GB APPLE IPHONE 3GS WHITE 32GB APPLE IPHONE 5S BLACK 64GB APPLE IPHONE 4 APPLE IPHONE 5S GOLD 16GB APPLE IPHONE 4 BLACK 16GB APPLE IPHONE 5S GOLD 32GB APPLE IPHONE 4 BLACK 32GB APPLE IPHONE 5S GOLD 64GB APPLE IPHONE 4 BLACK 8GB APPLE IPHONE 5S WHITE 16GB APPLE IPHONE 4 WHITE 16GB APPLE IPHONE 5S WHITE 32GB APPLE IPHONE 4 WHITE 32GB APPLE IPHONE -

Alcatel One Touch Go Play 7048 Alcatel One Touch
Acer Liquid Jade S Alcatel Idol 3 4,7" Alcatel Idol 3 5,5" Alcatel One Touch Go Play 7048 Alcatel One Touch Pop C3/C2 Alcatel One Touch POP C7 Alcatel Pixi 4 4” Alcatel Pixi 4 5” (5045x) Alcatel Pixi First Alcatel Pop 3 5” (5065x) Alcatel Pop 4 Lte Alcatel Pop 4 plus Alcatel Pop 4S Alcatel Pop C5 Alcatel Pop C9 Allview C6 Quad Apple Iphone 4 / 4s Apple Iphone 5 / 5s / SE Apple Iphone 5c Apple Iphone 6/6s 4,7" Apple Iphone 6 plus / 6s plus Apple Iphone 7 Apple Iphone 7 plus Apple Iphone 8 Apple Iphone 8 plus Apple Iphone X HTC 8S HTC Desire 320 HTC Desire 620 HTC Desire 626 HTC Desire 650 HTC Desire 820 HTC Desire 825 HTC 10 One M10 HTC One A9 HTC One M7 HTC One M8 HTC One M8s HTC One M9 HTC U11 Huawei Ascend G620s Huawei Ascend G730 Huawei Ascend Mate 7 Huawei Ascend P7 Huawei Ascend Y530 Huawei Ascend Y540 Huawei Ascend Y600 Huawei G8 Huawei Honor 5x Huawei Honor 7 Huawei Honor 8 Huawei Honor 9 Huawei Mate S Huawei Nexus 6p Huawei P10 Lite Huawei P8 Huawei P8 Lite Huawei P9 Huawei P9 Lite Huawei P9 Lite Mini Huawei ShotX Huawei Y3 / Y360 Huawei Y3 II Huawei Y5 / Y541 Huawei Y5 / Y560 Huawei Y5 2017 Huawei Y5 II Huawei Y550 Huawei Y6 Huawei Y6 2017 Huawei Y6 II / 5A Huawei Y6 II Compact Huawei Y6 pro Huawei Y635 Huawei Y7 2017 Lenovo Moto G4 Plus Lenovo Moto Z Lenovo Moto Z Play Lenovo Vibe C2 Lenovo Vibe K5 LG F70 LG G Pro Lite LG G2 LG G2 mini D620 LG G3 LG G3 s LG G4 LG G4c H525 / G4 mini LG G5 / H830 LG K10 / K10 Lte LG K10 2017 / K10 dual 2017 LG K3 LG K4 LG K4 2017 LG K7 LG K8 LG K8 2017 / K8 dual 2017 LG L Fino LG L5 II LG L7 LG -

HR-Imotion Kompatibilitätsübersicht So Vergleichen Sie Ob Ihr Smartphone Oder Tablet in Den Gerätehalter Passt*
HR-imotion Kompatibilitätsübersicht So vergleichen Sie ob Ihr Smartphone oder Tablet in den Gerätehalter passt*. 1. Überprüfen Sie die Artikel Nummer des Gerätehalter. Sie finden die Nummer auf der Unterseite der Verpackung über dem Strichcode Auf der Amazon Webseite im Produkttitel oder im Produktinformationsbereich 2. Suchen Sie nun Ihr Telefon oder Tablet in der auf der nächsten Seite startenden Geräteübersicht Sollte Ihr Tablet oder Smartphone nicht auftauchen, so messen Sie bitte die Länge und Breite des Smartphone oder Tablet ab und vergleichen Sie es mit den genannten Abmessungen in der Beschreibung / Stichpunkten. 3. Schauen Sie nun in der Spalte mit der heraus gesuchten Artikelnummer ob Ihr Telefon oder Tablet passt: = Produkt passt in die Halterung = Produkt passt nicht in die Halterung *Alle Angaben ohne Gewähr. Überprüft werden nur die Abmessungen der Geräte. Beispiel Sie besitzen ein Google Nexus 6P und möchten ent- weder wissen, welche Halterung Sie nutzen können oder ob die Quicky Lüftungshalterung (Art. Nr. 22110101) passt. HR-imotion Kompatibilität/Compatibility 2018 / 07 Gerätetyp Telefon 22410001 23010201 22110001 23010001 23010101 22010401 22010501 22010301 22010201 22110101 22010701 22011101 22010101 22210101 22210001 23510101 23010501 23010601 23010701 23510320 22610001 23510420 Smartphone Acer Liquid Zest Plus Smartphone AEG Voxtel M250 Smartphone Alcatel 1X Smartphone Alcatel 3 Smartphone Alcatel 3C Smartphone Alcatel 3V Smartphone Alcatel 3X Smartphone Alcatel 5 Smartphone Alcatel A3 Smartphone Alcatel A3 XL Smartphone