F5 Big-Ip Afm—Service Provider Security Platform
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Application Delivery Firewall Paradigm | F5 White Paper
White Paper The Application Delivery Firewall Paradigm The increasing sophistication, frequency, and diversity of today’s network attacks are overwhelming conventional stateful security devices at the edge of the data center. A new data center architecture based on the security services of the F5 application delivery firewall solution effectively combats modern attacks while providing significant CapEx savings. Lori MacVittie Senior Technical Marketing Manager David Holmes Senior Technical Marketing Manager White Paper The Application Delivery Firewall Paradigm Contents Introduction 3 Firewall Limitations 4 A New Data Center Architecture 6 Native Application Protocol Fluency 7 Advanced Network Protection 8 Advanced DNS Protection 9 Advanced Web Application Protection 9 Web Access Management 9 Cumulative Benefits 9 Conclusion 10 2 White Paper The Application Delivery Firewall Paradigm Introduction In most organizations, firewalls are the first line of defense for web and application services. The firewall is, and has been, the primary foundation around which conventional network security architectures are built. The conventional architecture has matured so that many security standards require the deployment of certified firewalls. For example, any data center that processes credit card numbers must comply with the Payment Card Industry (PCI) standard, which requires a certified network firewall. The de facto standard referenced by PCI auditors is an International Computer Security Association (ICSA) Labs–certified network firewall. ICSA defines a short list of firewalls that can be used for card processing purposes. But the conventional firewall is beginning to show its limitations in detecting and repelling modern attacks. Attacks targeted at the application or network layers are causing failures of these stateful—and often expensive—firewalls, and the number of such attacks is growing. -

NOTICE of ANNUAL MEETING of SHAREHOLDERS to Be Held on March 13, 2013
NOTICE OF ANNUAL MEETING OF SHAREHOLDERS To Be Held on March 13, 2013 TO SHAREHOLDERS OF F5 NETWORKS, INC.: The annual meeting of shareholders of F5 Networks, Inc. (the “Company”) for fiscal year 2012 will be held on March 13, 2013 at 11:00 a.m. Pacific Time at F5 Networks, Inc., 351 Elliott Avenue West, Seattle, Washington 98119 for the following purposes, as more fully described in the accompanying Proxy Statement: 1. to elect two Class I directors to hold office until the annual meeting of shareholders for fiscal year 2014, three Class II directors to hold office until the annual meeting of shareholders for fiscal year 2015, and one Class III director to hold office until the annual meeting of shareholders for fiscal year 2013 and until their successors are elected and qualified; 2. to ratify the selection of PricewaterhouseCoopers LLP as the Company’s independent registered public accounting firm for fiscal year 2013; 3. to conduct an advisory vote on compensation of our named executive officers; 4. to adopt and approve an amendment to our Second Amended and Restated Articles of Incorporation to declassify our Board of Directors and provide for an annual election of directors; and 5. to transact such other business as may properly come before the meeting and any adjournments or postponements thereof. Only shareholders of record at the close of business on January 7, 2013 are entitled to notice of, and to vote at, the annual meeting. By Order of the Board of Directors, JEFFREY A. CHRISTIANSON Secretary Seattle, Washington January 22, 2013 YOUR VOTE IS IMPORTANT! Whether or not you attend the annual meeting, it is important that your shares be represented and voted at the meeting. -
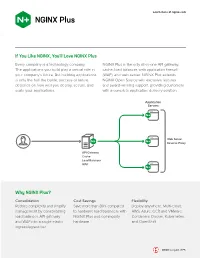
Why NGINX Plus?
Learn more at nginx.com If You Like NGINX, You’ll Love NGINX Plus Every company is a technology company. NGINX Plus is the only all-in-one API gateway, The applications you build play a critical role in cache, load balancer, web application firewall your company’s future. But building applications (WAF), and web server. NGINX Plus extends is only the half the battle; success or failure NGINX Open Source with exclusive features depends on how well you deploy, secure, and and award-winning support, providing customers scale your applications. with a complete application delivery solution. Application Servers Web Server Reverse Proxy API Gateway Cache Load Balancer WAF Why NGINX Plus? Consolidation Cost Savings Flexibility Reduce complexity and simplify Save more than 80% compared Deploy anywhere. Multi-cloud: management by consolidating to hardware load balancers with AWS, Azure, GCP, and VMware. load balancer, API gateway, NGINX Plus and commodity Containers: Docker, Kubernetes, and WAF into a single elastic hardware and OpenShift ingress/egress tier NGINX is a part of F5 NGINX Plus Features AUTHENTICATION PROGRAMMABILITY • HTTP Basic Authentication • NGINX JavaScript module for scripting and • HTTP authentication subrequests advanced configurations • X.509 client certificate authentication • Lua scripting language • NTLM authentication • Ansible, Chef, and Puppet integration • JSON Web Token (JWT) validation • Key-value store for dynamic configuration • OpenID Connect • NGINX Plus API for managing upstream servers, • Single sign-on: Keycloak, -

High-Performance Application Delivery Firewall
Solution Profile | Security High-Performance Application Delivery Firewall F5 solutions sit at the strategic point of control in the network to deliver applications, which Key features is also the ideal place to perform security functions such as network firewalling, advanced • Scalability and Performance— authentication, web application firewalling, availability monitoring, SSL termination, and Provides optimal scalability because it is distributed denial-of-service (DDoS) mitigation. The F5 application delivery firewall solution built on the highest-performing ADC on combines scalability, application fluency, and intelligence to deliver data and applications safely. the market • Stateful Firewall—Maintains security Evolving Threats with a network firewall certified by ICSA • Protocol Security—Appears as a TCP Internet data centers and public-facing web properties are constant targets for large-scale peer to both client and server attacks by hacker/hacktivist communities and others looking to grab intellectual property or • Application Security—Protects cause a service outage. Organizations must prepare for the normal load of users, but they applications with the industry-leading also must defend their infrastructures from the daily barrage of malicious attackers. web application firewall, BIG-IP® Traditional firewalls are not meeting fundamental functional requirements, let alone Application Security Manager™ performance needs. Dynamic and layered attacks that necessitate multiple point solutions • DDoS Attack Prevention—Protects add to administrative distress. Traditional firewalls can be overwhelmed by their limited against both network and application ability to scale under a DDoS attack while keeping peak connection performance for valid attacks, including DNS DDoS, while users, which renders not only the firewalls themselves unresponsive, but the websites they delivering uninterrupted service for legitimate connections are supposed to protect. -

F5 Networks, Inc. (Exact Name of Registrant As Specified in Its Charter)
Table of Contents UNITED STATES SECURITIES AND EXCHANGE COMMISSION Washington, D.C. 20549 Form 10-K (Mark One) ☒ ANNUAL REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the fiscal year ended September 30, 2019 or ☐ TRANSITION REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the transition period from to . Commission File Number 000-26041 F5 Networks, Inc. (Exact name of Registrant as specified in its charter) Washington 91-1714307 (State or other jurisdiction of (I.R.S. Employer incorporation or organization) Identification No.) 801 5th Avenue Seattle, Washington 98104 (Address of principal executive offices, including zip code) (206) 272-5555 (Registrant’s telephone number, including area code) Securities registered pursuant to Section 12(b) of the Act: Title of Each Class Trading Symbol(s) Name of Each Exchange on Which Registered Common stock, no par value FFIV NASDAQ Global Select Market Securities registered pursuant to Section 12(g) of the Act: None Indicate by check mark if the registrant is a well-known seasoned issuer, as defined in Rule 405 of the Securities Act. Yes ☒ No ☐ Indicate by check mark if the registrant is not required to file reports pursuant to Section 13 or Section 15(d) of the Act. Yes ☐ No ☒ Indicate by check mark whether the registrant (1) has filed all reports required to be filed by Section 13 or 15(d) of the Securities Exchange Act of 1934 during the preceding 12 months (or for such shorter period that the Registrant was required to file such reports), and (2) has been subject to such filing requirements for the past 90 days. -

The F5 Handbook for Service Providers
Guide The F5 Handbook for Service Providers VERSION 2, REVISED 2018 Table of Contents Security Solutions 4 S/Gi Firewall 4 Carrier-Grade NAT 6 Secure DNS 8 VoLTE and IMS Security 10 Data Center Firewall 12 Optimize, Secure, DDoS Mitigation 14 GTP Security 16 and Monetize Data Traffic Management Solutions 18 Subscriber, Application, and Policy Aware Bandwidth Control 18 Your Network Charging and Quota Management 20 Fair Usage Policy 22 Mobile consumers are growing accustomed to anytime/anywhere Tiered Service Plans 24 access to resource-intensive content, such as streaming video and Over-the-Top (OTT) Monetization 26 high-bandwidth applications from their mobile devices. Mass-market Bandwidth On-Demand 28 consumption of smartphones and other connected mobile devices, Service Function Chaining/Intelligent Traffic Steering 30 along with advanced 4G LTE network deployments, have led to IP Traffic Optimization 32 massive and sustained growth in data usage. As a result, operating URL Filtering 34 costs are rising while average revenue per user (ARPU) has trended flat to negative. Header Enrichment and Content Insertion 36 Visibility, Reporting, and Analytics 38 To remain profitable, service providers must find new ways to support increased demands on their networks with more efficient Signaling Solutions 40 resource utilization, while maintaining the ability to support rapid Intelligent DNS for the Mobile Core 40 rollout of new revenue-generating services. Intelligent DNS Infrastructure 42 F5 offers solutions for fixed and mobile service providers to achieve LTE Roaming 44 maximum optimization, security, and monetization of their networks. SIP/IMS 46 The sections on the following pages feature use cases that illustrate Network Functions Virtualization 48 how you can maintain top network performance and profitability. -

F5 EMEA Product Guide
F5 PRODUCT GUIDE EMEA | APRIL 2021 TABLE OF CONTENTS Adaptive Applications ................................................................................................................................................................................................................ 3 Intelligent Application Traffic Management ...................................................................................................................................................................... 4 BIG-IP Local Traffic Manager ............................................................................................................................................................................................ 4 VELOS Local Traffic Manager (LTM) Systems ............................................................................................................................................................. 7 VIPRION Local Traffic Manager (LTM) Systems .......................................................................................................................................................... 7 BIG-IP Better and Best Bundles ...................................................................................................................................................................................... 8 NGINX Plus Application Delivery Controller ............................................................................................................................................................... 9 BIG-IP DNS Delivery