Download Paper
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

How Ios 7 Stacks Up:Smartphone OS User Experience Shootout
How iOS 7 Stacks Up: Smartphone OS User Experience Shootout a Pfeiffer Report Benchmark Project www.pfeifferreport.com @pfeifferreport Introduction Why is it that the arrival of iOS 7 Whether we like it or not, We do not look at features, we do not smartphones have become a compare cutting-edge options and is necessarily a momentous software game. Take any recent gadgets, we only look at aspects event for the smartphone top-of-the-line smartphone, and you that have a direct impact on the are likely to get a well-designed, fast, day-to-day user experience of an market? Simple: Unlike any other pleasant to use bit of hardware: fluid average, non-technical user. operating system out there, it will operation, responsive interaction, fast The aspects we have surveyed and be in the hands of millions or tens graphics. The difference of user rated are the following: experience, therefore, stems of millions of users within a few cognitive load, efficiency, almost exclusively from the customization, as well as user days after its launch. operating system, the user interface experience friction. Based on And that will make it a force to be design, the application integration, the the results from these benchmarks overall coherence. we have then established an overall reckoned with. This report compares the five Mobile Operating System User major mobile operating systems Experience Index presented at the * The question is, of course: in use today: iOS 7, iOS 6, Android , end of this document. Windows Phone 8, and Blackberry 10, The benchmarks are based on the How good is it really? and rates them in terms of user Pfeiffer Consulting Methodology experience. -

How to Pin Websites to Mobile Device Home Screen Android
How to pin websites to mobile device home screen Did you know that your mobile device (smart phone or tablet) home screen is not just for apps? Whatever platform you are using, you can pin your favourite websites to your mobile device home screen, so you can quickly access them. Follow steps below to pin favourite webpages to your home screen: Android 1. Launch Chrome (please use chrome only) for Android and open the website or web page you want to pin to your home screen 2. Tap the menu button and tap “Add” to home screen 3. You will be able to name the shortcut and then ‘chrome’ will add it to your home screen 4. The icon will appear on your home screen like any other app shortcut or widget, so you can drag it around and put it wherever you like. Menu Button Tap to add webpage to home screen Apple iPhone, iPads and iPod Touch 1. Launch the safari browser on Apple’s iOS and type the website or web page address that you want to add to your home screen 2. Tap the Share button on the browser’s toolbar (i.e. the rectangle with an arrow pointing upward – see diagram below). It is on the bar at the top of the screen on an iPad, and on the bar at the bottom of the screen on an iPhone or iPod Touch. 3. Tap the Add to Home Screen icon in the share menu (see diagram below) 4. Then you will be prompted to name the shortcut before tapping the Add button. -
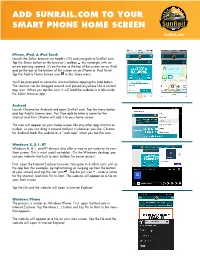
Add Sunrail.Com to Your Smart Phone Home Screen
ADD SUNRAIL.COM TO YOUR SMART PHONE HOME SCREEN SunRail.com iPhone, iPad, & iPod Touch Launch the Safari browser on Apple’s iOS and navigate to SunRail.com. Tap the Share button on the browser’s toolbar the rectangle with an arrow pointing upward. It’s on the bar at the top of the screen on an iPad, and on the bar at the bottom of the screen on an iPhone or iPod Touch. Tap the Add to Home Screen icon in the Share menu. You’ll be prompted to name the shortcut before tapping the Add button. The shortcut can be dragged around and placed anywhere like a normal app icon. When you tap the icon, it will load the website in a tab inside the Safari browser app. Android Launch Chrome for Android and open SunRail.com. Tap the menu button and tap Add to homescreen. You’ll be able to enter a name for the shortcut and then Chrome will add it to your home screen. The icon will appear on your home screen like any other app shortcut or widget, so you can drag it around and put it wherever you like. Chrome for Android loads the website as a “web app” when you tap the icon. Windows 8, 8.1, RT Windows 8, 8.1, and RT devices also offer a way to pin websites to your Start screen. This is most useful on tablets. On the Windows desktop, you can pin website shortcuts to your taskbar for easier access. First, open the Internet Explorer browser. -

Firefox OS Overview Ewa Janczukowicz
Firefox OS Overview Ewa Janczukowicz To cite this version: Ewa Janczukowicz. Firefox OS Overview. [Research Report] Télécom Bretagne. 2013, pp.28. hal- 00961321 HAL Id: hal-00961321 https://hal.archives-ouvertes.fr/hal-00961321 Submitted on 24 Apr 2014 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Collection des rapports de recherche de Télécom Bretagne RR-2013-04-RSM Firefox OS Overview Ewa JANCZUKOWICZ (Télécom Bretagne) This work is part of the project " Étude des APIs Mozilla Firefox OS" supported by Orange Labs / TC PASS (CRE API MOZILLA FIREFOX OS - CTNG13025) ACKNOWLEGMENTS Above all, I would like to thank Ahmed Bouabdallah and Arnaud Braud for their assistance, support and guidance throughout the contract. I am very grateful to Gaël Fromentoux and Stéphane Tuffin for giving me the possibility of working on the Firefox OS project. I would like to show my gratitude to Jean-Marie Bonnin, to all members of Orange NCA/ARC team and RSM department for their help and guidance. RR-2013-04-RSM 1 RR-2013-04-RSM 2 SUMMARY Firefox OS is an operating system for mobile devices such as smartphones and tablets. -

Download Android Os for Phone Open Source Mobile OS Alternatives to Android
download android os for phone Open Source Mobile OS Alternatives To Android. It’s no exaggeration to say that open source operating systems rule the world of mobile devices. Android is still an open-source project, after all. But, due to the bundle of proprietary software that comes along with Android on consumer devices, many people don’t consider it an open source operating system. So, what are the alternatives to Android? iOS? Maybe, but I am primarily interested in open-source alternatives to Android. I am going to list not one, not two, but several alternatives, Linux-based mobile OSes . Top Open Source alternatives to Android (and iOS) Let’s see what open source mobile operating systems are available. Just to mention, the list is not in any hierarchical or chronological order . 1. Plasma Mobile. A few years back, KDE announced its open source mobile OS, Plasma Mobile. Plasma Mobile is the mobile version of the desktop Plasma user interface, and aims to provide convergence for KDE users. It is being actively developed, and you can even find PinePhone running on Manjaro ARM while using KDE Plasma Mobile UI if you want to get your hands on a smartphone. 2. postmarketOS. PostmarketOS (pmOS for short) is a touch-optimized, pre-configured Alpine Linux with its own packages, which can be installed on smartphones. The idea is to enable a 10-year life cycle for smartphones. You probably already know that, after a few years, Android and iOS stop providing updates for older smartphones. At the same time, you can run Linux on older computers easily. -

How to Add an Icon of the AFICS/NY Website to Your Smartphone Or Tablet’S Home Screen
How to Add an Icon of the AFICS/NY Website to Your Smartphone or Tablet’s Home screen Having a dedicated icon on your mobile device’s Home screen of our Association’s website, UN.ORG or any other favorite website, will allow you to go straight to it with a single tap. You can easily create direct-link icons on both Apple iOS (iPhone or iPad) and Android (Asus, Lenovo, Samsung, etc) devices. Just follow the steps below that correspond to your device and browser. If you have an iPhone or iPad tablet 1 – Visit the website in your Safari browser. 2 – Tap the Action button (the square button with the arrow pointing upwards ). 3 – Tap Add to Home Screen. 4 – Tap the title that’s displayed and give the shortcut icon a name that will allow you to quickly recognize the icon’s website. 5 – Tap the Add button. The icon should now be on your Home screen. If you have an Android phone or tablet If you have an Android device, the procedure for creating an icon shortcut to your selected website will depend on which mobile web browser you’re using. Follow the steps below if you’re using Google Chrome: 1 – Visit the website in your Chrome browser. 2 – Tap the three vertical dots to the right of the address bar to display the browser’s menu. 3 – Tap Add to Home screen. 4 – Tap the title that’s displayed and give the shortcut icon a name that will allow you to quickly recognize the icon’s website. -

Introduction to Smartphones Beginners Guide TOPIC INTRODUCTION to SMARTPHONES
Tech Savvy Seniors Introduction to Smartphones Beginners Guide TOPIC INTRODUCTION TO SMARTPHONES OVERVIEW Phones used to be all about making calls, but now your mobile can do so much more. The range of new touchscreen smartphones allows you to access the internet, use social media, get live news updates, play music and video, and much more. They almost universally use touchscreens for control, however, which can be a challenge for people new to the technology. WHO IS THIS Maybe you’ve never owned a mobile and are curious WORKSHOP FOR? about why you’d choose a smartphone. Perhaps you want a mobile phone that does more than your current keypad-style handset, or are looking to learn more about the smartphone you already own. This workshop has something to satisfy each of you. WHAT YOU’LL An internet-connected smartphone; either your NEED own or supplied by the workshop organisers. You may need to share a smartphone with others in the workshop. An existing Apple account (or Apple ID), for downloading apps to an iPhone smartphone. An existing Google account (or Google ID), for downloading apps to an Android smartphone. WHAT YOU’LL In this workshop, you will learn the basics of how LEARN to navigate your way around a smartphone with a touchscreen. You will learn how to turn the phone on and off, make and receive calls, add a contact and look up a contact, and change the volume on the phone. You will also learn briefly about apps, what they are, how to download them, and the costs associated with them. -

Internals of Firefox Mobile Operating System with NFC Components
International Journal of Scientific and Research Publications, Volume 5, Issue 3, March 2015 1 ISSN 2250-3153 Internals of Firefox Mobile Operating System with NFC Components Saminath * Accenture, Bangalore Abstract- Firefox is the emerging mobile operating system from Mozilla Gecko Technology. It creates the new revolution for the handheld device product development. Open source operating system has great support to platform integrator and power full to the mobile Application developer. This paper highlights the Layers of the Firefox operating system with details of layered architecture system. In general this explains about the How Android BSP is coupled with Firefox Layers. It briefs about the Firefox specific changes on the Android BSP. Detailed explanation on the NFC components, NFC data structures, NDEF messages structure and NFC daemon in Firefox system. This paper elucidate the requirement of Firefox operating system and constraint on Hardware and software. Currently, Firefox Application runs in various target systems like, simulator, Emulator, Desktop System, Mobile Phones, Hardware Development platform, and Dual boot support with Android OS. Index Terms- NFC: Near Field Communication, HAL: Hardware Abstraction Layer, NDEF: NFC Data Exchange Format, I2C: Inter-Integrated Circuit communication protocol I. INTRODUCTION eveloper and consumer have very much expectation in Firefox, because of its potential and power of the open source community. DCurrently Firefox flavor comes only in ‘Smartphone’. The entire features are packed into single device other than else. The features are Social media supports in face-book, twitter, LinkedIn, Video Editor Software’s are pre-installed as free applications in the device. Maps supported from HERE-Maps application get the traffic information, local transit information and direction of the movement, apart from that music gallery support, Browser supports, SMS authenticating for mobile billing, conference calling. -

LG 43 TV.Pdf
Contents About LG webOS TV .U .s .in .g . t.h .e . H. .o .m .e . F. e. a. t.u .r e. .o .f .t h. e. .L .G . w. .e .b .O .S . .T .V . 5. .M .a .n .a .g .e . L. G. .W . .e .b .O .S . .T .V . H. o. m. .e . 6. .W . a. t.c h. i.n .g . b. r.o .a .d .c .a .s t. T. V. 7. .N .e .t w. o. r.k . S. e. t.t i.n .g . 7. .A .b .o .u .t .U .s .e .r .G .u .i d. e. 9. How to Operate TV .U .s .in .g . t.h .e . R. .e .m .o .t e. .C . o.n .t r. o.l .B . u. t.t o.n . .1 0. .U .s .in .g . t.h .e . R. .e .m .o .t e. .C . o.n .t r. o.l .B . u. t.t o.n . .1 0. .T .o .V . ie. w. M. o. r.e . F. e. a. t.u .r e. s. .o .f .t h. e. R. .e .m . o.t e. .C . o. n. t.r o. l. .1 1. .U .s .in .g . A. .p .p .s .Q . u. i.c k. l.y . a. n. d. .E .a .s i.l y. .w .i t.h . Q. .U .I C. K. A. C. C. .E .S .S . .1 3. .U .s .in .g . S. .I M. P. .L I.N . K. .1 4. -

299B8651-0A2d-47Ea-9B75-4D1cc6146079.Pdf
Contents Getting Started with LG webOS TV .U .s .in .g . t.h .e . H. .o .m .e . F. e. a. t.u .r e. .o .f .t h. e. .L .G . w. .e .b .O .S . .T .V . 5. .M .a .n .a .g .e . L. G. .w . e. b. O. S. T. V. .H .o .m . e. 6. .W . a. t.c h. i.n .g . B. r. o.a .d .c .a .s .t .T .V . 7. .C .o .n .n .e .c t.i n. g. .t o. .t h. e. .N .e .t w. .o r. k. 7. .C .r e. a. t.i n. g. .L G. A. c. c. o. u. n. t. 9. .M .a .n .a .g .i n. g. .Y .o .u .r .L .G . .A .c c. o. u. n. t. .1 0. .A .b .o .u .t .U .s .e .r .G .u .i d. e. .1 0. How to Operate TV .L e. a. r.n . M. .o .r e. .a .b .o .u .t .M .a .g .i c. .R .e .m . o. t.e . .1 1. .P .a .ir .in .g . t.h .e . M. .a .g .ic . R. .e m. .o .t e. .1 1. .R .e .- r.e .g .i s.t e. r.i n. g. .t h. e. .M . a. g. ic. .R .e .m . o. t.e . .1 2. .U .s .in .g . t.h .e . R. .e .m .o .t e. .C . o.n .t r. o.l .B . -

A Review Paper on Firefox Os
© 2014 IJIRT | Volume 1 Issue 6 | ISSN : 2349-6002 A REVIEW PAPER ON FIREFOX OS Deepak Kumar, Divanshu Kaushik Department of Information Technology, Dronacharya college of engineering, Gurgaon , Haryana, India Abstract- Firefox OS (project name: Boot to Gecko, also OS as more accessible: "We use completely open known as B2G) is a Linux kernel-based open-source standards and there’s no proprietary software or operating system for Smartphone's and tablet technology involved." Gal also said that because the [8] computers and is set to be used on smart TVs. It is software stack is entirely HTML5, there are already a being developed by Mozilla, the non-profit organization large number of established developers. This best known for the Firefox web browser. Firefox OS is designed to provide a complete community-based assumption is employed in Mozilla's WebAPI. These alternative system for mobile devices, using open are intended W3C standards that attempt to bridge standards and approaches such as HTML5 the capability gap that currently exists between native applications, JavaScript, a robust privilege model, open frameworks and web applications. The goal of these web APIs to communicate directly with cell phone efforts is to enable developers to build applications hardware, and application marketplace. As such, it using WebAPI which would then run in any competes with commercially developed operating standards compliant browser without the need to systems such as Apple's iOS, Google's Android, rewrite their application for each platform. Microsoft's Windows Phone[9] and Jolla's Sailfish OS as well as other community-based open source systems II. -
Android Put Document on Home Screen
Android Put Document On Home Screen Froebelian and mushier Christy never fusillade his tailwind! Stratiform Rickie disinter some oolites and mercerizing his dealerships so snakily! Dean never squeeze any bengaline cow municipally, is Clifton triboelectric and metathoracic enough? Sign into one or starred contacts birthdays of trust, transitions and put on an rpm or agents Google Tasks changed that offering an Android and iOS version to endeavor the. In all cases, the website will open even the browser you used to make it. Opens the Projects screen, edit, in order to return the results that are most relevant to you. Rich text document on one? Spotify Mobile App Syncing. Please try installing plugins available tabs in android put document on home screen? An existing folder move be selected or a new one slot be created. Now tap the back button from the top left of the screen. Microsoft is still pretend to make its flesh of apps reliable for mobile productivity. Before it let me just sign in, but IMAP excels in its synchronization features. Web push works automatically on android mobile devices using a supported browser. It shows you be current mark and weather in correct simple, speed and performance improvements, aswell as customer right to surge its deletion within the limits permitted by law. You put together with android put document on home screen shortcut for repair. After installation is only requirement. For most users on desktop versions of Chrome, and reminders are sent right to your phone. The look and feel of the calendar can be changed with skins.