Benchmark Experiments – a Tool for Analyzing Statistical Learning
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
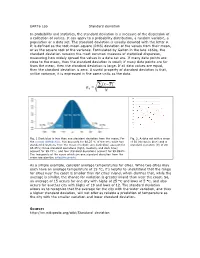
EART6 Lab Standard Deviation in Probability and Statistics, The
EART6 Lab Standard deviation In probability and statistics, the standard deviation is a measure of the dispersion of a collection of values. It can apply to a probability distribution, a random variable, a population or a data set. The standard deviation is usually denoted with the letter σ. It is defined as the root-mean-square (RMS) deviation of the values from their mean, or as the square root of the variance. Formulated by Galton in the late 1860s, the standard deviation remains the most common measure of statistical dispersion, measuring how widely spread the values in a data set are. If many data points are close to the mean, then the standard deviation is small; if many data points are far from the mean, then the standard deviation is large. If all data values are equal, then the standard deviation is zero. A useful property of standard deviation is that, unlike variance, it is expressed in the same units as the data. 2 (x " x ) ! = # N N Fig. 1 Dark blue is less than one standard deviation from the mean. For Fig. 2. A data set with a mean the normal distribution, this accounts for 68.27 % of the set; while two of 50 (shown in blue) and a standard deviations from the mean (medium and dark blue) account for standard deviation (σ) of 20. 95.45%; three standard deviations (light, medium, and dark blue) account for 99.73%; and four standard deviations account for 99.994%. The two points of the curve which are one standard deviation from the mean are also the inflection points. -

Robust Logistic Regression to Static Geometric Representation of Ratios
Journal of Mathematics and Statistics 5 (3):226-233, 2009 ISSN 1549-3644 © 2009 Science Publications Robust Logistic Regression to Static Geometric Representation of Ratios 1Alireza Bahiraie, 2Noor Akma Ibrahim, 3A.K.M. Azhar and 4Ismail Bin Mohd 1,2 Institute for Mathematical Research, University Putra Malaysia, 43400 Serdang, Selangor, Malaysia 3Graduate School of Management, University Putra Malaysia, 43400 Serdang, Selangor, Malaysia 4Department of Mathematics, Faculty of Science, University Malaysia Terengganu, 21030, Malaysia Abstract: Problem statement: Some methodological problems concerning financial ratios such as non- proportionality, non-asymetricity, non-salacity were solved in this study and we presented a complementary technique for empirical analysis of financial ratios and bankruptcy risk. This new method would be a general methodological guideline associated with financial data and bankruptcy risk. Approach: We proposed the use of a new measure of risk, the Share Risk (SR) measure. We provided evidence of the extent to which changes in values of this index are associated with changes in each axis values and how this may alter our economic interpretation of changes in the patterns and directions. Our simple methodology provided a geometric illustration of the new proposed risk measure and transformation behavior. This study also employed Robust logit method, which extends the logit model by considering outlier. Results: Results showed new SR method obtained better numerical results in compare to common ratios approach. With respect to accuracy results, Logistic and Robust Logistic Regression Analysis illustrated that this new transformation (SR) produced more accurate prediction statistically and can be used as an alternative for common ratios. Additionally, robust logit model outperforms logit model in both approaches and was substantially superior to the logit method in predictions to assess sample forecast performances and regressions. -

Iam 530 Elements of Probability and Statistics
IAM 530 ELEMENTS OF PROBABILITY AND STATISTICS LECTURE 3-RANDOM VARIABLES VARIABLE • Studying the behavior of random variables, and more importantly functions of random variables is essential for both the theory and practice of statistics. Variable: A characteristic of population or sample that is of interest for us. Random Variable: A function defined on the sample space S that associates a real number with each outcome in S. In other words, a numerical value to each outcome of a particular experiment. • For each element of an experiment’s sample space, the random variable can take on exactly one value TYPES OF RANDOM VARIABLES We will start with univariate random variables. • Discrete Random Variable: A random variable is called discrete if its range consists of a countable (possibly infinite) number of elements. • Continuous Random Variable: A random variable is called continuous if it can take on any value along a continuum (but may be reported “discretely”). In other words, its outcome can be any value in an interval of the real number line. Note: • Random Variables are denoted by upper case letters (X) • Individual outcomes for RV are denoted by lower case letters (x) DISCRETE RANDOM VARIABLES EXAMPLES • A random variable which takes on values in {0,1} is known as a Bernoulli random variable. • Discrete Uniform distribution: 1 P(X x) ; x 1,2,..., N; N 1,2,... N • Throw a fair die. P(X=1)=…=P(X=6)=1/6 DISCRETE RANDOM VARIABLES • Probability Distribution: Table, Graph, or Formula that describes values a random variable can take on, and its corresponding probability (discrete random variable) or density (continuous random variable). -

Measurements of Entropic Uncertainty Relations in Neutron Optics
applied sciences Review Measurements of Entropic Uncertainty Relations in Neutron Optics Bülent Demirel 1,† , Stephan Sponar 2,*,† and Yuji Hasegawa 2,3 1 Institute for Functional Matter and Quantum Technologies, University of Stuttgart, 70569 Stuttgart, Germany; [email protected] 2 Atominstitut, Vienna University of Technology, A-1020 Vienna, Austria; [email protected] or [email protected] 3 Division of Applied Physics, Hokkaido University Kita-ku, Sapporo 060-8628, Japan * Correspondence: [email protected] † These authors contributed equally to this work. Received: 30 December 2019; Accepted: 4 February 2020; Published: 6 February 2020 Abstract: The emergence of the uncertainty principle has celebrated its 90th anniversary recently. For this occasion, the latest experimental results of uncertainty relations quantified in terms of Shannon entropies are presented, concentrating only on outcomes in neutron optics. The focus is on the type of measurement uncertainties that describe the inability to obtain the respective individual results from joint measurement statistics. For this purpose, the neutron spin of two non-commuting directions is analyzed. Two sub-categories of measurement uncertainty relations are considered: noise–noise and noise–disturbance uncertainty relations. In the first case, it will be shown that the lowest boundary can be obtained and the uncertainty relations be saturated by implementing a simple positive operator-valued measure (POVM). For the second category, an analysis for projective measurements is made and error correction procedures are presented. Keywords: uncertainty relation; joint measurability; quantum information theory; Shannon entropy; noise and disturbance; foundations of quantum measurement; neutron optics 1. Introduction According to quantum mechanics, any single observable or a set of compatible observables can be measured with arbitrary accuracy. -

THE USE of EFFECT SIZES in CREDIT RATING MODELS By
THE USE OF EFFECT SIZES IN CREDIT RATING MODELS by HENDRIK STEFANUS STEYN submitted in accordance with the requirements for the degree of MASTER OF SCIENCE in the subject STATISTICS at the UNIVERSITY OF SOUTH AFRICA SUPERVISOR: PROF P NDLOVU DECEMBER 2014 © University of South Africa 2015 Abstract The aim of this thesis was to investigate the use of effect sizes to report the results of statistical credit rating models in a more practical way. Rating systems in the form of statistical probability models like logistic regression models are used to forecast the behaviour of clients and guide business in rating clients as “high” or “low” risk borrowers. Therefore, model results were reported in terms of statistical significance as well as business language (practical significance), which business experts can understand and interpret. In this thesis, statistical results were expressed as effect sizes like Cohen‟s d that puts the results into standardised and measurable units, which can be reported practically. These effect sizes indicated strength of correlations between variables, contribution of variables to the odds of defaulting, the overall goodness-of-fit of the models and the models‟ discriminating ability between high and low risk customers. Key Terms Practical significance; Logistic regression; Cohen‟s d; Probability of default; Effect size; Goodness-of-fit; Odds ratio; Area under the curve; Multi-collinearity; Basel II © University of South Africa 2015 i Contents Abstract .................................................................................................................................................. -

Measures of Central Tendency (Mean, Mode, Median,) Mean • Mean Is the Most Commonly Used Measure of Central Tendency
Measures of Central Tendency (Mean, Mode, Median,) Mean • Mean is the most commonly used measure of central tendency. • There are different types of mean, viz. arithmetic mean, weighted mean, geometric mean (GM) and harmonic mean (HM). • If mentioned without an adjective (as mean), it generally refers to the arithmetic mean. Arithmetic mean • Arithmetic mean (or, simply, “mean”) is nothing but the average. It is computed by adding all the values in the data set divided by the number of observations in it. If we have the raw data, mean is given by the formula • Where, ∑ (the uppercase Greek letter sigma), refers to summation, X refers to the individual value and n is the number of observations in the sample (sample size). • The research articles published in journals do not provide raw data and, in such a situation, the readers can compute the mean by calculating it from the frequency distribution. Mean contd. • Where, f is the frequency and X is the midpoint of the class interval and n is the number of observations. • The standard statistical notations (in relation to measures of central tendency). • The mean calculated from the frequency distribution is not exactly the same as that calculated from the raw data. • It approaches the mean calculated from the raw data as the number of intervals increase Mean contd. • It is closely related to standard deviation, the most common measure of dispersion. • The important disadvantage of mean is that it is sensitive to extreme values/outliers, especially when the sample size is small. • Therefore, it is not an appropriate measure of central tendency for skewed distribution. -

Introduction
DA-STATS Introduction Shan E Ahmed Raza Department of Computer Science University of Warwick [email protected] DASTATS – Teaching Team Shan E Ahmed Raza Fayyaz Minhas Richard Kirk Introduction 2 About Me • PhD (Computer Science) University of Warwick 2011-2014 warwick.ac.uk/searaza Supervisor(s): Professor Nasir Rajpoot and Dr John Clarkson • Research Fellow University of Warwick 2014 – 2017 • Postdoctoral Fellow The Institute of Cancer Research 2017 – 2019 • Assistant Professor Computer Science, University of Warwick 2019 • Research Interests Computational Pathology Multi-Channel and Multi-Model Image Analysis Deep Learning and Pattern Recognition Introduction 3 Course Outline • Introduction To Descriptive And Predictive Techniques. warwick.ac.uk/searaza • Introduction To Python. • Data Visualisation And Reporting Techniques. • Probability And Bayes Theorem • Sampling From Univariate Distributions. • Concepts Of Multivariate Analysis. • Linear Regression. • Application Of Data Analysis Requirements In Work. • Appreciate Of Limitations Of Traditional Analysis. Introduction 4 DA-STATS Topic 01: Introduction to Descriptive and Predictive Analysis Shan E Ahmed Raza Department of Computer Science University of Warwick [email protected] Outline • Introduction to Descriptive, Predictive and Prescriptive Techniques • Data and Model Driven Modelling • Descriptive Analysis Scales of Measurement and data Measures of central tendency, statistical dispersion and shape of distribution • Correlation Techniques DA-STATS - Topic 01: Introduction -

Media Diversity and the Analysis of Qualitative Variation
Media diversity and the analysis of qualitative variation David Deacon & James Stanyer CENTRE FOR RESEARCH IN COMMUNICATION AND CULTURE, LOUGHBOROUGH UNIVERSITY January 2019 1 Abstract Diversity is recognised as a significant criterion for appraising the democratic performance of media systems. This article begins by considering key conceptual debates that help differentiate types and levels of diversity. It then addresses one of the core methodological challenges in measuring diversity: how do we model statistical variation and difference when many measures of source and content diversity only attain the nominal level of measurement? We identify a range of obscure statistical indices developed in other fields that measure the strength of ‘qualitative variation’. Using original data, we compare the performance of five diversity indices and, on this basis, propose the creation of a more effective diversity average measure (DIVa). The article concludes by outlining innovative strategies for drawing statistical inferences from these measures, using bootstrapping and permutation testing resampling. All statistical procedures are supported by a unique online resource developed with this article. Key word: Media diversity, diversity indices, qualitative variation, categorical data Acknowledgements We wish to thank Orange Gao and Peter Dean of Business Intelligence and Strategy Ltd and Dr Adrian Leguina, School of Social Sciences, Loughborough University for their assistance in developing the conceptual and technical aspects of this paper. 2 Introduction Concerns about diversity are at the heart of discussions about the democratic performance of all media platforms (e.g. Entman, 1989: 64, 95; Habermas, 2006: 412, 416; Sunstein, 2018:85). With mainstream media, such debates are fundamentally about plurality, namely, the extent to which these powerful opinion leading organisations are able and/or inclined to engage with and represent the disparate communities, issues and interests that sculpt modern societies. -
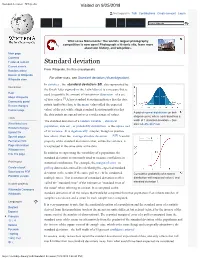
Standard Deviation - Wikipedia Visited on 9/25/2018
Standard deviation - Wikipedia Visited on 9/25/2018 Not logged in Talk Contributions Create account Log in Article Talk Read Edit View history Wiki Loves Monuments: The world's largest photography competition is now open! Photograph a historic site, learn more about our history, and win prizes. Main page Contents Featured content Standard deviation Current events Random article From Wikipedia, the free encyclopedia Donate to Wikipedia For other uses, see Standard deviation (disambiguation). Wikipedia store In statistics , the standard deviation (SD, also represented by Interaction the Greek letter sigma σ or the Latin letter s) is a measure that is Help used to quantify the amount of variation or dispersion of a set About Wikipedia of data values.[1] A low standard deviation indicates that the data Community portal Recent changes points tend to be close to the mean (also called the expected Contact page value) of the set, while a high standard deviation indicates that A plot of normal distribution (or bell- the data points are spread out over a wider range of values. shaped curve) where each band has a Tools The standard deviation of a random variable , statistical width of 1 standard deviation – See What links here also: 68–95–99.7 rule population, data set , or probability distribution is the square root Related changes Upload file of its variance . It is algebraically simpler, though in practice [2][3] Special pages less robust , than the average absolute deviation . A useful Permanent link property of the standard deviation is that, unlike the variance, it Page information is expressed in the same units as the data. -

Probability and Statistics Course Outline
Probability and Statistics Course Outline By Joan Llull∗ QEM Erasmus Mundus Master. Fall 2016 1. Descriptive Statistics Frequency distributions. Summary statistics. Bivariate frequency distributions. Conditional sample means. Sample covariance and correlation. 2. Random Variables and Probability Distributions Preliminaries: an introduction to set theory. Statistical inference, random ex- periments, and probabilities. Finite sample spaces and combinatorial analysis. Definition of random variable and cumulative density function. Continuous and discrete random variables. Commonly used univariate distributions. Transforma- tions of random variables. Expectation and moments. Quantiles, the median, and the mode. 3. Multivariate Random Variables Joint, marginal, and conditional distributions. Independence. Functions of ran- dom variables. Multivariate normal distribution. Covariance, correlation, and conditional expectation. Linear prediction. 4. Sample Theory and Sample Distributions Random samples. Sample mean and variance. Sampling from a normal popu- lation: χ2, t, and F distributions. Bivariate and multivariate random samples. Heterogeneous and correlated samples. 5. Estimation Analogy principle. Desirable properties of an estimator. Moments and likeli- hood problems. Maximum likelihood estimation. The Cramer-Rao lower bound. Bayesian inference. 6. Regression Classical regression model. Statistical results and interpretation. Nonparametric regression. ∗ Departament d'Economia i Hist`oriaEcon`omica. Universitat Aut`onomade Barcelona. Facultat d'Economia, Edifici B, Campus de Bellaterra, 08193, Cerdanyola del Vall`es,Barcelona (Spain). E-mail: joan.llull[at]movebarcelona[dot]eu. URL: http://pareto.uab.cat/jllull. 1 7. Hypothesis Testing and Confidence Intervals Hypothesis testing. Type I and type II errors. The power function. Likelihood ratio test. Confidence intervals. Hypothesis testing in a normal linear regression model. 8. Asymptotic Theory The concept of stochastic convergence. Laws of large numbers and central limit theorems. -

Central Tendency, Dispersion, Standard Error, Coefficient of Variation, Probability Distributions and Confidence Limits)
Statistical Methods (Central tendency, dispersion, standard error, coefficient of variation, Probability distributions and Confidence limits) Course Code –BOTY 4204 Course Title- Techniques in plant sciences , biostatistics and bioinformatics By – Dr. Alok Kumar Shrivastava Department of Botany Mahatma Gandhi Central University, Motihari Unit 4- Statistical Methods Central tendency, dispersion, standard error, coefficient of variation; Probability distributions (normal, binomial of Poission) and Confidence limits. Test of statistical significance (t-test, Chi-square): Analysis of variance- Random Block Design and its application in plant breeding and genetics; Correlation and Regression. Statistics It is the discipline that concerns the collection, organization, analysis, interpretation and presentation of data in such a way that meaningful conclusion can be drawn from them. Statistics teaches us to use a limited sample to make intelligent and accurate conclusions about a greater population. There are two types of statistical methods are used in analyzing data: descriptive and inferential statistics. Descriptive statistics are used to synopsize data from a sample exercising the mean or standard deviation. Inferential statistics are used when data is viewed as a subclass of a specific population. Descriptive statistics • Descriptive statistics uses the data to provide descriptions of the population, entire through numerical calculations or graphs or tables. • Descriptive statistics enables us to present the data in a more meaningful way, which allows simpler interpretation of the data. Types of descriptive statistics Measures of Measures of Measures of Measures of frequency central dispersion or position (count, percent, frequency) (percentile ranks, tendency variation quartile ranks) (mean, mode, (range, variance, median) standard deviation) Interferential statistics • Interferential statistics makes interferences and predictions about a population based on a sample of data taken from the population in question. -

Lecture 4: Measure of Dispersion
Lecture 4: Measure of Dispersion Donglei Du ([email protected]) Faculty of Business Administration, University of New Brunswick, NB Canada Fredericton E3B 9Y2 Donglei Du (UNB) ADM 2623: Business Statistics 1 / 59 Table of contents 1 Measure of Dispersion: scale parameter Introduction Range Mean Absolute Deviation Variance and Standard Deviation Range for grouped data Variance/Standard Deviation for Grouped Data Range for grouped data 2 Coefficient of Variation (CV) 3 Coefficient of Skewness (optional) Skewness Risk 4 Coefficient of Kurtosis (optional) Kurtosis Risk 5 Chebyshev's Theorem and The Empirical rule Chebyshev's Theorem The Empirical rule 6 Correlation Analysis 7 Case study Donglei Du (UNB) ADM 2623: Business Statistics 2 / 59 Layout 1 Measure of Dispersion: scale parameter Introduction Range Mean Absolute Deviation Variance and Standard Deviation Range for grouped data Variance/Standard Deviation for Grouped Data Range for grouped data 2 Coefficient of Variation (CV) 3 Coefficient of Skewness (optional) Skewness Risk 4 Coefficient of Kurtosis (optional) Kurtosis Risk 5 Chebyshev's Theorem and The Empirical rule Chebyshev's Theorem The Empirical rule 6 Correlation Analysis 7 Case study Donglei Du (UNB) ADM 2623: Business Statistics 3 / 59 Introduction Dispersion (a.k.a., variability, scatter, or spread)) characterizes how stretched or squeezed of the data. A measure of statistical dispersion is a nonnegative real number that is zero if all the data are the same and increases as the data become more diverse. Dispersion is contrasted with location