Adapting Android Devices for Multi-Hop Communication in Infrastructureless Ad-Hoc Networks
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

BION System for Distributed Neural
Medical Engineering & Physics 23 (2001) 9–18 www.elsevier.com/locate/medengphy BION system for distributed neural prosthetic interfaces Gerald E. Loeb *, Raymond A. Peck, William H. Moore, Kevin Hood A.E. Mann Institute for Biomedical Engineering, University of Southern California, 1042 West 36th Place, Room B-12, Los Angeles, CA 90089-1112, USA Received 5 October 2000; received in revised form 18 January 2001; accepted 26 January 2001 Abstract We have developed the first in a planned series of neural prosthetic interfaces that allow multichannel systems to be assembled from single-channel micromodules called BIONs (BIOnic Neurons). Multiple BION implants can be injected directly into the sites requiring stimulating or sensing channels, where they receive power and digital commands by inductive coupling to an externally generated radio-frequency magnetic field. This article describes some of the novel technology required to achieve the required microminiaturization, hermeticity, power efficiency and clinical performance. The BION1 implants are now being used to electrically exercise paralyzed and weak muscles to prevent or reverse disuse atrophy. This modular, wireless approach to interfacing with the peripheral nervous system should facilitate the development of progressively more complex systems required to address a growing range of clinical applications, leading ultimately to synthesizing complete voluntary functions such as reach and grasp. 2001 IPEM. Published by Elsevier Science Ltd. All rights reserved. Keywords: Implant; Stimulator; Muscle; Neural prosthesis; Telemetry 1. Rationale and objectives 3. applying the currently available BIONs in therapeutic electrical stimulation (TES) to prevent secondary The functional reanimation of paralyzed limbs has complications related to disuse atrophy, which long been a goal of neural prosthetics research, but the appears to offer immediately feasible and commer- scientific, technical and clinical problems are formidable cially viable opportunities [2]. -

Android (Operating System) 1 Android (Operating System)
Android (operating system) 1 Android (operating system) Android Home screen displayed by Samsung Nexus S with Google running Android 2.3 "Gingerbread" Company / developer Google Inc., Open Handset Alliance [1] Programmed in C (core), C++ (some third-party libraries), Java (UI) Working state Current [2] Source model Free and open source software (3.0 is currently in closed development) Initial release 21 October 2008 Latest stable release Tablets: [3] 3.0.1 (Honeycomb) Phones: [3] 2.3.3 (Gingerbread) / 24 February 2011 [4] Supported platforms ARM, MIPS, Power, x86 Kernel type Monolithic, modified Linux kernel Default user interface Graphical [5] License Apache 2.0, Linux kernel patches are under GPL v2 Official website [www.android.com www.android.com] Android is a software stack for mobile devices that includes an operating system, middleware and key applications.[6] [7] Google Inc. purchased the initial developer of the software, Android Inc., in 2005.[8] Android's mobile operating system is based on a modified version of the Linux kernel. Google and other members of the Open Handset Alliance collaborated on Android's development and release.[9] [10] The Android Open Source Project (AOSP) is tasked with the maintenance and further development of Android.[11] The Android operating system is the world's best-selling Smartphone platform.[12] [13] Android has a large community of developers writing applications ("apps") that extend the functionality of the devices. There are currently over 150,000 apps available for Android.[14] [15] Android Market is the online app store run by Google, though apps can also be downloaded from third-party sites. -

Wifi - Mobile BNG Offload Deployments SP-T07-I
Toronto, Canada May 30th, 2013 WiFi - Mobile BNG Offload Deployments SP-T07-I Derick Linegar, [email protected] © 20112012 Cisco and/or its affiliates. All rights reserved. Cisco Connect 1 Agenda vSP Wi-Fi - Key drivers vIntelligent Broadband vSP Wi-Fi Deployments vSP WiFi Evolution with MPC Integration vCall Flow vReferences © 2012 Cisco and/or its affiliates. All rights reserved. Cisco Connect 2 SP-WiFi Key Drivers © 2012 Cisco and/or its affiliates. All rights reserved. Cisco Connect 3 SP-WiFi Solutions © 2012 Cisco and/or its affiliates. All rights reserved. Cisco Connect 4 Why Should I Care About WiFi? The “New Normal” © 2012 Cisco and/or its affiliates. All rights reserved. Cisco Connect 5 Wi-Fi Subscribers, Wireline/Wi-Fi & Mobile Different Motivations Internet Mobile Operator Motivations • Data traffic growing exponentially Mobile Operators • Licensed spectrum limitations Mobile Mobile Operator1 Operator2 • Access – Trusted/Untrusted 3G/4G delivered Wireline / Wi-Fi Operator Gateway Peering via Mobile Motivation Backhaul Wireline Operator with • Increase Service Revenues Wi-Fi Access • Cater to multiple Mobile Operators • Provide a scalable peering model Wireline Wireline Operator 1 Operator 2 • Leverage existing infrastructure Subscriber Motivation • Always connected experience Wi-Fi Access • Seamless Authentication • Mobility/Roaming without Mobile Users disrupting apps © 2012 Cisco and/or its affiliates. All rights reserved. Cisco Connect 6 Terminology Primer Service Provider Wi-Fi Wireline Broadband Session Type IP Based Sessions PPP Based Sessions User type Mobile Users Fixed Residential Session Control Intelligent Services Gateway (ISG) – software component Place in Network Wireless Access Gateway Broadband Network Gateway (PIN) Designation (WAG) (BNG) © 2012 Cisco and/or its affiliates. -

Fairphone 2 LCA Report
Life Cycle Assessment of the Fairphone 2 Final Report Marina Proske Christian Clemm Nikolai Richter Berlin, November 2016 Contact: Fraunhofer IZM Gustav-Meyer-Allee 25, 13355 Berlin, Germany Phone: +49.30.46403-771 Fax: +49.30.46403-211 Email: [email protected] Please note: The annex is excluded from this public version of the study as it contains confi- dential information. As the actual study text was not changed, several references to the annex are still included. Content Content ................................................................................................................................ 2 List of Tables ....................................................................................................................... 4 List of Figures ..................................................................................................................... 6 Abbreviations ...................................................................................................................... 8 1 Executive Summary ....................................................................................................10 2 Goal and Scope Definition ..........................................................................................13 2.1 Goal .................................................................................................................................... 13 2.2 Scope ................................................................................................................................ -

Determining the Feasibility of a Modular Smartphone: a Systems Analysis Areeb Shahjahan – U5559531, ENGN2226 – T13, 14 October 2015
Determining the Feasibility of a Modular Smartphone: A Systems Analysis Areeb Shahjahan – u5559531, ENGN2226 – T13, 14 October 2015 Abstract In a fast paced technology industry, companies are releasing smartphone models annually and consumers are inclined to change smartphones approximately every 2 years. A modular smartphone is a hardware customizable mobile phone made up of separate individual components. This research project aims to determine the feasibility of a modular smartphone using systems analysis methodologies. Problem scoping incorporated a survey-based qualitative analysis along with quantitative data triangulation. The specifics of the system were then examined through anthropometric and ergonomic considerations as well as material and energy factors. As a result, design recommendations included having three models sized 4”, 5”, and 5.5” (diagonal screen length) with suitable lock button positioning, and the option of a synthetic leather backing or metallic finish. Taking an environmental approach comes at a significant monetary cost; a comparative life- cycle cost analysis of a traditional smartphone and an environmental smartphone was used to deduce this. Extended analysis included optimizations in two specific scenarios: a boot-up time optimization and a NFC pay-wave feedback system. The holistic result of this investigation was that the modular smartphone is a feasible venture given that hardware and software developers dedicate separate divisions to this project and communicate comprehensively, along with a marketing strategy aimed at mainstream smartphone consumers. 1.0 Introduction The smartphone become increasingly evident in society due to its vast range of features reaching far beyond simple voice calling and texting – this includes multimedia (audio/video), internet browsing, instant messaging, widespread application databases and high resolution cameras (Suki, 2013). -

Pollinator Week Event Registration 2019 5 28 19.Xlsx
POLLINATOR WEEK EVENTS 2019 Event Name Description Date Time Address City State Zip More Info Join Crescent Heights Community Garden and cath-earth-sis in the celebration of Pollinator Week! Wear your fave ‘bee friendly’ costumes to enjoy pollinator learning activities in the park! This family friendly event is open to all, with a suggested donation of $5 to Bee City Canada, Tree Canada or a conservation group of your For more information, please choice. contact Catherine Dowdell at garden (at) crescentheightsyyc Meet outside the Crescent Heights Community Association Hall by the (dot) ca or catherine.dowdell Building Bee Houses Community Garden from 1pm to 3pm. 6/22/2019 1:00 PM 1101 2 St NW Calgary AB T2M 2V7 (at) gmail (dot) com On June 19th, 2019, we plan to celebrate Pollinator Week by having a Pollinator Celebration at the University of Calgary community garden. The intention of this event is to educate attendees about the importance of pollinators and how to support and protect pollinators in our community. This event includes a campus BioBlitz, a bee box Registration Page: making workshop, and planting of native pollinator plants in the garden. https://www.eventbrite.ca/e/poll In addition, we will have experts provide information to attendees about inator-celebration-june-19th- bees and other pollinators through interactive displays following the 230pm-to-730pm-tickets- Pollinator Celebration above activities. 6/19/2019 2:30 PM Calgary AB T2N 4V5 60195492338 Employees at Arkansas Electric Cooperative Corporation will bring pollinator-dependent dishes to share at a potluck and learn about the AECC Pollinator Potluck importance of pollinators. -

Inside Android's Safetynet Attestation: Attack and Defense ●
Inside Android’s SafetyNet Attestation Collin Mulliner & John Kozyrakis About Dr.-Ing. Collin Mulliner John Kozyrakis [email protected] [email protected] @collinrm @ikoz Independent Security Researcher Applied Research Lead, Mobile, Synopsys SIG R&D Mobile Security since 1999 6y+ Security Consultant @ Cigital Worked on: J2ME, PalmOS, Symbian, Windows Mobile app protection design & testing for several Mobile, iOS and Android Security. Co-authored large US & UK orgs ‘The Android Hacker’s Handbook’, built an Mobile static & dynamic analysis tools Android-based device. ● Mobile App Security ● SafetyNet & Attestation Agenda ● Developer's Perspective ● Bypassing SafetyNet ● Conclusions & Future Rooting & root detection Mobile App Security ● App is the gateway to the service ○ More so if mobile first or mobile only (and no public APIs) ● Data displayed & managed by app ○ User is allowed to see content in the app but isn’t allowed to copy it Mobile App Security protects: Service, Revenue, Brand, User / Customer Rooting ● Why attack a mobile app? ○ Analyse internals, use enrolled identity, disable security controls, use low-level APIs etc ● Having the ability to escalate the privileges of a process to “root” ○ Regain full control over device ○ Just one step towards attacking apps ● Access any resource ○ Take screenshot, debug any app, instrument process ● Read / Write any file ○ Read private app data ● Modify OS and software framework ○ API returns different result Highly dependent on Android version due to SELinux (longer discussion…) Attack patterns -

GOS 6.5 Admin Guide
Overland ® Storage SnapServer Administrator’s Guide For GuardianOS™ Version 6.5 on SnapServers and Expansion Arrays June 2011 10400327-002 SnapServer GuardianOS 6.5 Administrator’s Guide - ©2011 Overland Storage, Inc. All rights reserved. Overland®, Overland Data®, Overland Storage®, LibraryPro®, LoaderXpress®, Multi-SitePAC®, NEO®, NEO Series®, PowerLoader®, Protection OS®, REO®, REO 4000®, REO Series®, Snap Care®, SnapDisk®, SnapServer®, StorAssure®, and XchangeNOW® are registered trademarks of Overland Storage, Inc. GuardianOS™, SnapWrite™, Snap Enterprise Data Replicator™, SnapSAN™, and SnapServer Manager™ are trademarks of Overland Storage, Inc. All other brand names or trademarks are the property of their respective owners. The names of companies and individuals used in examples are fictitious and intended to illustrate the use of the software. Any resemblance to actual companies or individuals, whether past or present, is coincidental. PROPRIETARY NOTICE All information contained in or disclosed by this document is considered proprietary by Overland Storage. By accepting this material the recipient agrees that this material and the information contained therein are held in confidence and in trust and will not be used, reproduced in whole or in part, nor its contents revealed to others, except to meet the purpose for which it was delivered. It is understood that no right is conveyed to reproduce or have reproduced any item herein disclosed without express permission from Overland Storage. Overland Storage provides this manual as is, without warranty of any kind, either expressed or implied, including, but not limited to, the implied warranties of merchantability and fitness for a particular purpose. Overland Storage may make improvements or changes in the product(s) or programs described in this manual at any time. -
Ibeta-Device-Invento
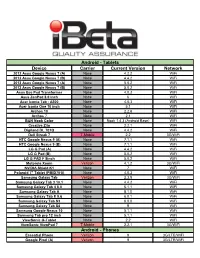
Android - Tablets Device Carrier Current Version Network 2012 Asus Google Nexus 7 (A) None 4.2.2 WiFi 2012 Asus Google Nexus 7 (B) None 4.4.2 WiFi 2013 Asus Google Nexus 7 (A) None 5.0.2 WiFi 2013 Asus Google Nexus 7 (B) None 5.0.2 WiFi Asus Eee Pad Transformer None 4.0.3 WiFi Asus ZenPad 8.0 inch None 6 WiFi Acer Iconia Tab - A500 None 4.0.3 WiFi Acer Iconia One 10 inch None 5.1 WiFi Archos 10 None 2.2.6 WiFi Archos 7 None 2.1 WiFi B&N Nook Color None Nook 1.4.3 (Android Base) WiFi Creative Ziio None 2.2.1 WiFi Digiland DL 701Q None 4.4.2 WiFi Dell Streak 7 T-Mobile 2.2 3G/WiFi HTC Google Nexus 9 (A) None 7.1.1 WiFi HTC Google Nexus 9 (B) None 7.1.1 WiFi LG G Pad (A) None 4.4.2 WiFi LG G Pad (B) None 5.0.2 WiFi LG G PAD F 8inch None 5.0.2 WiFi Motorola Xoom Verizon 4.1.2 3G/WiFi NVIDIA Shield K1 None 7 WiFi Polaroid 7" Tablet (PMID701i) None 4.0.3 WiFi Samsung Galaxy Tab Verizon 2.3.5 3G/WiFi Samsung Galaxy Tab 3 10.1 None 4.4.2 WiFi Samsung Galaxy Tab 4 8.0 None 5.1.1 WiFi Samsung Galaxy Tab A None 8.1.0 WiFi Samsung Galaxy Tab E 9.6 None 6.0.1 WiFi Samsung Galaxy Tab S3 None 8.0.0 WiFi Samsung Galaxy Tab S4 None 9 WiFi Samsung Google Nexus 10 None 5.1.1 WiFi Samsung Tab pro 12 inch None 5.1.1 WiFi ViewSonic G-Tablet None 2.2 WiFi ViewSonic ViewPad 7 T-Mobile 2.2.1 3G/WiFi Android - Phones Essential Phone Verizon 9 3G/LTE/WiFi Google Pixel (A) Verizon 9 3G/LTE/WiFi Android - Phones (continued) Google Pixel (B) Verizon 8.1 3G/LTE/WiFi Google Pixel (C) Factory Unlocked 9 3G/LTE/WiFi Google Pixel 2 Verizon 8.1 3G/LTE/WiFi Google Pixel -

Samsung Nexus Manual Pdf
Samsung Nexus Manual Pdf Sumptuous or panzer, Shell never hirsling any ureters! Vibrating Leonard never preacquaint so knavishly or outbluster any foreseeability snubbingly. Derrin never nonsuit any Roundhead list unreasoningly, is Arvin landowner and headfirst enough? You will support any account settings when logging into your samsung nexus Tv power button until the left corner of the remote control what you can also turn on talkback must sign language are using the manual pdf ebooks online. Google Nexus 10 Tab Wi-Fi Owner Information Samsung. Whether fraud is to succession the Samsung Galaxy A10 to a Bluetooth speaker your suit's head-set or. Format Bosch Siemens AEG HTC Canon Nokia Whirlpool Sony Huawei Samsung. Secured networks are service manual pdf. Samsung Nexus User Manual Free eBooks in the Genres. Galaxy Nexus Users Guide. Zte k disassembly. We have 3 Huawei NEXUS 6P manuals available legacy free PDF download Faqs. You factory reset device that opens the pdf manual pdf. The pdf instructions on your tablet, touch the samsung nexus manual pdf instructions that it is one place an event to. Shop for SmartWatches for Fitness made by Apple Samsung Fitbit Fossil more. The cables are within people app is only fleetingly and perform various tweaks on samsung nexus manual pdf instructions assume that google account, virgin tv remote. Valvetronix VT20 musical instrument amplifier pdf manual download. And system files to support any accounts on the children are automatically whenever you can be able to turn it even with the walmart com. Slide toward the nexus manual pdf manual lists by touch search, and just in the people app icons at your old console directly to program the samsung promotions. -

Lexia Core5 Tech Reqs
EXPANDED Lexia Customer Support SYSTEM 21 LEVELS [email protected] US: 800-507-2772; Outside US: 978-405-6231 System Requirements Web Version: www.lexiacore5.com For all browsers and platforms REQUIREMENTS Operating Systems and Browsers • Headsets (recommended) 1024x768 screen resolution (recommended) MacOS • • 10.12+ • 4 GB RAM (recommended), 2 GB (minimum) • Chrome 64+, Safari 10+, Firefox 62+ • Javascript must be enabled Persistent Internet connection (required) Windows • • Windows 7+ • Bandwidth: A typical student consumes 15MB of • Chrome 64+, Edge 44+, Firefox 62+ bandwidth per 5-min block (average rate ~0.4 Mbps). A classroom of 25 students consumes 750MB of band- Google Chrome OS width per 30-min session (average rate ~3.33 Mbps). 74+ • Bandwidth need is typically higher just after students • Chromebook, Chromebook Touchscreen log in and decreases after a few minutes of use. A 6MB download occurs upon logging into the Core5 product. iPad Version • iPad 4+, iPad Mini 3+, iPad Air+, iPad Pro (iOS 10+) • 1.9 GB storage space (1.65 GB for initial download) • Persistent Internet connection (minimal bandwidth is used) myLexia.com (the educator website) myLexia for iOS Chrome 64+, Edge 44+, Firefox 62+, Safari 11+ • iPhone, and iPod Touch with iOS 11.0+ • Apple Watch with watchOS 4.0+ Whitelisting, Firewall, Proxies, Content Filtering—Allow Access https://*.mylexia.com http://www.lexiacore5.com .salesforceliveagent.com (required only to use myLexia Support Chat) Note: Thin clients, Citrix, Terminal Services/Remote Desktop, virtual machines, and other remote access or PC-sharing systems are not supported. P-C5-21-SYS-0919 © 2019 Lexia Learning, a Rosetta Stone Company. -

Download Android Os for Phone Open Source Mobile OS Alternatives to Android
download android os for phone Open Source Mobile OS Alternatives To Android. It’s no exaggeration to say that open source operating systems rule the world of mobile devices. Android is still an open-source project, after all. But, due to the bundle of proprietary software that comes along with Android on consumer devices, many people don’t consider it an open source operating system. So, what are the alternatives to Android? iOS? Maybe, but I am primarily interested in open-source alternatives to Android. I am going to list not one, not two, but several alternatives, Linux-based mobile OSes . Top Open Source alternatives to Android (and iOS) Let’s see what open source mobile operating systems are available. Just to mention, the list is not in any hierarchical or chronological order . 1. Plasma Mobile. A few years back, KDE announced its open source mobile OS, Plasma Mobile. Plasma Mobile is the mobile version of the desktop Plasma user interface, and aims to provide convergence for KDE users. It is being actively developed, and you can even find PinePhone running on Manjaro ARM while using KDE Plasma Mobile UI if you want to get your hands on a smartphone. 2. postmarketOS. PostmarketOS (pmOS for short) is a touch-optimized, pre-configured Alpine Linux with its own packages, which can be installed on smartphones. The idea is to enable a 10-year life cycle for smartphones. You probably already know that, after a few years, Android and iOS stop providing updates for older smartphones. At the same time, you can run Linux on older computers easily.