An Analysis of the Skype Peer-To-Peer Internet Telephony Protocol
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Course 5 Lesson 2
This material is based on work supported by the National Science Foundation under Grant No. 0802551 Any opinions, findings, and conclusions or recommendations expressed in this material are those of the author (s) and do not necessarily reflect the views of the National Science Foundation C5L3S1 With the advent of the Internet, social networking, and open communication, a vast amount of information is readily available on the Internet for anyone to access. Despite this trend, computer users need to ensure private or personal communications remain confidential and are viewed only by the intended party. Private information such as a social security numbers, school transcripts, medical histories, tax records, banking, and legal documents should be secure when transmitted online or stored locally. One way to keep data confidential is to encrypt it. Militaries,U the governments, industries, and any organization having a desire to maintain privacy have used encryption techniques to secure information. Encryption helps to boost confidence in the security of online commerce and is necessary for secure transactions. In this lesson, you will review encryption and examine several tools used to encrypt data. You will also learn to encrypt and decrypt data. Anyone who desires to administer computer networks and work with private data must have some familiarity with basic encryption protocols and techniques. C5L3S2 You should know what will be expected of you when you complete this lesson. These expectations are presented as objectives. Objectives are short statements of expectations that tell you what you must be able to do, perform, learn, or adjust after reviewing the lesson. -
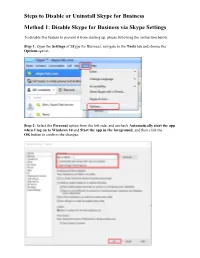
Steps to Disable Or Uninstall Skype for Business Method 1: Disable Skype for Business Via Skype Settings
Steps to Disable or Uninstall Skype for Business Method 1: Disable Skype for Business via Skype Settings To disable this feature to prevent it from starting up, please following the instruction below. Step 1: Open the Settings of Skype for Business, navigate to the Tools tab and choose the Options option. Step 2: Select the Personal option from the left side, and uncheck Automatically start the app when I log on to Windows 10 and Start the app in the foreground, and then click the OK button to confirm the changes. Step 3: Click the Settings button again on the Skype for Business interface and choose File then Exit. After the three steps, you have successfully disabled Skype for Business from your PC and you will no longer see it although it is still on your computer. Method 2: Uninstall Skype for Business via Control Panel This method requires you to clear all your profile cache for the Skype for Business account and then uninstall it from Windows 10 via Control Panel. Here is the detailed tutorial on uninstalling Skype for Business. Step 1: Open your Skype for business and then sign out of this application. Step 2: In the Sign in interface, please click the Delete my sign-in info option. Note: This step will clear all your profile cache for the Skype for Business account and will disable the auto sign-in when the application opens. Step 3: Close Skype for Business. Step 4: You should uninstall Skype for Business like any other software on your computer. Click on the Windows button in the bottom left of your screen and type Control Panel. -

VIRTUAL ENGAGEMENT BEST PRACTICES Student Leadership & Involvement | 211 University Center
VIRTUAL ENGAGEMENT BEST PRACTICES Student Leadership & Involvement | 211 University Center Table of Contents Click on any of the titles below to be navigated to that section SLI POLICIES ........................................................................................................................... 1 USING TIGERZONE TO YOUR ADVANTAGE .............................................................................. 1 ONLINE MEETING PLATFORMS ............................................................................................... 2 ONLINE BROADCASTING PLATFORMS ..................................................................................... 3 ONLINE CHAT PLATFORMS ..................................................................................................... 3 VIDEO CONFERENCE TIPS (for Zoom) ...................................................................................... 4 VIRTUAL ENGAGEMENT IDEAS ............................................................................................... 5 VIRTUAL ENTERTAINMENT ..................................................................................................... 6 SLI POLICIES During Phase 1 there are to be NO IN PERSON STUDENT EVENTS. This applies to events both ON and OFF campus. If your organization is found to be hosting in person events you will be given ONE warning from Student Leadership & Involvement. If your organization is found to be hosting student events a second time your organization will be suspended for the remainder of the 2020-2021 -

Etsi Ts 129 173 V14.0.0 (2017-03)
ETSI TS 129 173 V14.0.0 (2017-03) TECHNICAL SPECIFICATION Digital cellular telecommunications system (Phase 2+) (GSM); Universal Mobile Telecommunications System (UMTS); LTE; Location Services (LCS); Diameter-based SLh interface for Control Plane LCS (3GPP TS 29.173 version 14.0.0 Release 14) 3GPP TS 29.173 version 14.0.0 Release 14 1 ETSI TS 129 173 V14.0.0 (2017-03) Reference RTS/TSGC-0429173ve00 Keywords GSM,LTE,UMTS ETSI 650 Route des Lucioles F-06921 Sophia Antipolis Cedex - FRANCE Tel.: +33 4 92 94 42 00 Fax: +33 4 93 65 47 16 Siret N° 348 623 562 00017 - NAF 742 C Association à but non lucratif enregistrée à la Sous-Préfecture de Grasse (06) N° 7803/88 Important notice The present document can be downloaded from: http://www.etsi.org/standards-search The present document may be made available in electronic versions and/or in print. The content of any electronic and/or print versions of the present document shall not be modified without the prior written authorization of ETSI. In case of any existing or perceived difference in contents between such versions and/or in print, the only prevailing document is the print of the Portable Document Format (PDF) version kept on a specific network drive within ETSI Secretariat. Users of the present document should be aware that the document may be subject to revision or change of status. Information on the current status of this and other ETSI documents is available at https://portal.etsi.org/TB/ETSIDeliverableStatus.aspx If you find errors in the present document, please send your comment to one of the following services: https://portal.etsi.org/People/CommiteeSupportStaff.aspx Copyright Notification No part may be reproduced or utilized in any form or by any means, electronic or mechanical, including photocopying and microfilm except as authorized by written permission of ETSI. -

Cisco SCA BB Protocol Reference Guide
Cisco Service Control Application for Broadband Protocol Reference Guide Protocol Pack #60 August 02, 2018 Cisco Systems, Inc. www.cisco.com Cisco has more than 200 offices worldwide. Addresses, phone numbers, and fax numbers are listed on the Cisco website at www.cisco.com/go/offices. THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS. THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY. The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB’s public domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California. NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS” WITH ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE. IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. -

ULTIMA X Series 3 EC Declaration of Conformity MSA
Operating Manual ULTIMAX-Series Gas Monitors Order No. 10046690/09 MSA AUER GmbH Thiemannstrasse 1 D-12059 Berlin Germany © MSA AUER GmbH. All rights reserved MSA EC Declaration of Conformity EC Declaration of Conformity Manufactured by: Mine Safety Appliances Company 1000 Cranberry Woods Drive Cranberry Township, PA 16066 USA The manufacturer or the European Authorized Representative: MSA AUER GmbH, Thiemannstrasse 1, D-12059 Berlin declares that the ULTIMA XE Main product ULTIMA XE Main with HART Module based on the EC-Type Examination Certificate: DMT 02 ATEX E 202 X complies with the ATEX directive 94/9/EC, Annex III. Quality Assurance Notification complying with Annex IV of the ATEX Directive 94/9/EC has been issued by Ineris of France, Notified Body number: 0080. The product is in conformance with the EMC directive 2004 / 108/ EC, EN 50270 :2006 Type 2 *, EN 61000 - 6 - 4 : 2007 * EN 61000-4-6 : Ultima XE MAIN HART MODULE : occasional transmission error can appear at the 2-wire version. A fault check has to be used at the receiver unit. The product complies with the directive 96/98 / EC (MarED), based on the EC-Type Examination Certificate : SEE BG 213.038 The quality survaillance is under the control of SEE BG, Notified Body number: 0736 We further declare that the product complies with the provisions of LVD Directive 2006 / 95/ EC, with the following harmonised standard: EN 61010-1 :2002 MSA AUER GmbH Berlin, October 2008 Dr. Axel Schubert R&D Instruments ® GB ULTIMA X Series 3 EC Declaration of Conformity MSA EC Declaration of Conformity Manufactured by: Mine Safety Appliances Company 1000 Cranberry Woods Drive Cranberry Township, PA 16066 USA The manufacturer or the European Authorized Representative: MSA AUER GmbH, Thiemannstrasse 1, D-12059 Berlin declares that the product ULTIMA SENSOR XE based on the EC-Type Examination Certificate: DMT 02 ATEX E 202 X complies with the ATEX directive 94/9/EC, Annex III. -

CCIA Comments in ITU CWG-Internet OTT Open Consultation.Pdf
CCIA Response to the Open Consultation of the ITU Council Working Group on International Internet-related Public Policy Issues (CWG-Internet) on the “Public Policy considerations for OTTs” Summary. The Computer & Communications Industry Association welcomes this opportunity to present the views of the tech sector to the ITU’s Open Consultation of the CWG-Internet on the “Public Policy considerations for OTTs”.1 CCIA acknowledges the ITU’s expertise in the areas of international, technical standards development and spectrum coordination and its ambition to help improve access to ICTs to underserved communities worldwide. We remain supporters of the ITU’s important work within its current mandate and remit; however, we strongly oppose expanding the ITU’s work program to include Internet and content-related issues and Internet-enabled applications that are well beyond its mandate and core competencies. Furthermore, such an expansion would regrettably divert the ITU’s resources away from its globally-recognized core competencies. The Internet is an unparalleled engine of economic growth enabling commerce, social development and freedom of expression. Recent research notes the vast economic and societal benefits from Rich Interaction Applications (RIAs), a term that refers to applications that facilitate “rich interaction” such as photo/video sharing, money transferring, in-app gaming, location sharing, translation, and chat among individuals, groups and enterprises.2 Global GDP has increased US$5.6 trillion for every ten percent increase in the usage of RIAs across 164 countries over 16 years (2000 to 2015).3 However, these economic and societal benefits are at risk if RIAs are subjected to sweeping regulations. -

Skype Voip Service- Architecture and Comparison Hao Wang Institute of Communication Networks and Computer Engineering University of Stuttgart Mentor: Dr.-Ing
INFOTECH Seminar Advanced Communication Services (ACS), 2005 Skype VoIP service- architecture and comparison Hao Wang Institute of Communication Networks and Computer Engineering University of Stuttgart Mentor: Dr.-Ing. S. Rupp ABSTRACT Skype is a peer-to-peer (P2P) overlay network for VoIP and other applications, developed by KaZaa in 2003. Skype can traverse NAT and firewall more efficiently than traditional VoIP networks and it offers better voice quality. To find and locate users, Skype uses “supernodes” that are running on peer machines. In contrast, traditional systems use fixed central servers. Also Skype uses encrypted media channel to protect the dada. The main contribution of this article is illustrating the architecture and components of Skype networks and basically analyzing key Skype functions such as login, NAT and firewall traversal. Furthermore, it contains comparisons of Skype networks with VoIP networks regarding different scenarios. On that basis it reveals some reasons why Skype has much better performance than previous VoIP products. Keywords Voice over IP (VoIP), Skype, Peer-to-peer (p2p), Super Node (SN) 1. Introduction It is expected that real-time person-to-person communication, like IP telephony (VoIP), instant messaging, voice, video and data collaboration will be the next big wave of Internet usage. VoIP refers to technology that enables routing of voice conversations over the Internet or any other IP network. Another technology is peer-to-peer, which is used for sharing content like audio, video, data or anything in digital format. Skype is a combination of these two technologies. It has much better performance by making use of advantages of both technologies. -

IM Security Documentation on Page Vi
Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release notes, and/or the latest version of the applicable documentation, which are available from the Trend Micro website at: http://docs.trendmicro.com/en-us/enterprise/trend-micro-im-security.aspx Trend Micro, the Trend Micro t-ball logo, Control Manager, MacroTrap, and TrendLabs are trademarks or registered trademarks of Trend Micro Incorporated. All other product or company names may be trademarks or registered trademarks of their owners. Copyright © 2016. Trend Micro Incorporated. All rights reserved. Document Part No.: TIEM16347/140311 Release Date: September 2016 Protected by U.S. Patent No.: Pending This documentation introduces the main features of the product and/or provides installation instructions for a production environment. Read through the documentation before installing or using the product. Detailed information about how to use specific features within the product may be available at the Trend Micro Online Help Center and/or the Trend Micro Knowledge Base. Trend Micro always seeks to improve its documentation. If you have questions, comments, or suggestions about this or any Trend Micro document, please contact us at [email protected]. Evaluate this documentation on the following site: http://www.trendmicro.com/download/documentation/rating.asp Privacy and Personal Data Collection Disclosure Certain features available in Trend Micro products collect and send feedback regarding product usage and detection information to Trend Micro. Some of this data is considered personal in certain jurisdictions and under certain regulations. -

Devicelock® DLP 8.3 User Manual
DeviceLock® DLP 8.3 User Manual © 1996-2020 DeviceLock, Inc. All Rights Reserved. Information in this document is subject to change without notice. No part of this document may be reproduced or transmitted in any form or by any means for any purpose other than the purchaser’s personal use without the prior written permission of DeviceLock, Inc. Trademarks DeviceLock and the DeviceLock logo are registered trademarks of DeviceLock, Inc. All other product names, service marks, and trademarks mentioned herein are trademarks of their respective owners. DeviceLock DLP - User Manual Software version: 8.3 Updated: March 2020 Contents About This Manual . .8 Conventions . 8 DeviceLock Overview . .9 General Information . 9 Managed Access Control . 13 DeviceLock Service for Mac . 17 DeviceLock Content Security Server . 18 How Search Server Works . 18 ContentLock and NetworkLock . 20 ContentLock and NetworkLock Licensing . 24 Basic Security Rules . 25 Installing DeviceLock . .26 System Requirements . 26 Deploying DeviceLock Service for Windows . 30 Interactive Installation . 30 Unattended Installation . 35 Installation via Microsoft Systems Management Server . 36 Installation via DeviceLock Management Console . 36 Installation via DeviceLock Enterprise Manager . 37 Installation via Group Policy . 38 Installation via DeviceLock Enterprise Server . 44 Deploying DeviceLock Service for Mac . 45 Interactive Installation . 45 Command Line Utility . 47 Unattended Installation . 48 Installing Management Consoles . 49 Installing DeviceLock Enterprise Server . 52 Installation Steps . 52 Installing and Accessing DeviceLock WebConsole . 65 Prepare for Installation . 65 Install the DeviceLock WebConsole . 66 Access the DeviceLock WebConsole . 67 Installing DeviceLock Content Security Server . 68 Prepare to Install . 68 Start Installation . 70 Perform Configuration and Complete Installation . 71 DeviceLock Consoles and Tools . -

CPON-HFC Light Link Direct® FTTH Node
® 969 Horsham Road CPON-HFC Light Link Direct FTTH Node Horsham, Pennsylvania 19044 USA 1 GHz Two Way FTTH Customer Premises Node Description Features The Light Link® Direct CPON-HFC customer Delivers full bandwidth CATV services to 1 GHz. premises optical node for FTTH networks offering The duplex unit is suitable for advanced DOCSIS full bandwidth cable television delivery, plus broad- with Telephony and Internet. band access via DOCSIS cable modems. High-performance optical receiver for CATV deliv- ery over glass (fibre) with 110 NTSC channels or Fiber-to-the-home (FTTH) is a reality today. The 91 PAL channels capacity. CPON-HFC is designed as an economic single port Suitable for transmission of PAL or NTSC ana- PBN CPON-HFC Light Link node customer premise deployment providing sim- logue TV channels as well as DVB-C or DVB-T plex or full duplex RF connectivity. digital television standards. Wide optical input range permits easy installation Employing leading edge designs for optical and without on-site alignment. electronic circuitry inside a die-cast metal housing, Optional return path transmitter to suit DOCSIS the CPON-HFC provides top class services and compliant cable modems and RF based pay-per- permits easy installation in home wiring closets or view systems. other confined spaces. Powered by either a direct coax 11 ~ 16 Vdc feed or DC power port. The core of the CPON-HFC is a high performance The compact and sturdy enclosure fits easily into low-noise optical receiver module for CATV to 1 wiring closets or network termination boxes. GHz, together with an optional return path transmit- ter module. -

Insight Into the Gtalk Protocol
1 Insight into the Gtalk Protocol Riyad Alshammari and A. Nur Zincir-Heywood Dalhousie University, Faculty of Computer Science Halifax NS B3H 1W5, Canada (riyad,zincir)@cs.dal.ca Abstract Google talk (Gtalk) is an instant messeger and voice over IP client developed by Google in 2005. Gtalk can work across firewalls and has very good voice quality. It encrypts calls end-to-end, and stores user information in a centralized fashion. This paper analyzes fundamental Gtalk functions such as login, firewall traversal, and call establishment under different network scenarios. The analysis is performed by both active and passive measurement techniques to understand the Gtalk network traffic. Based on our analysis, we devised algorithms for login and call establishment processes as well as data flow models. I. INTRODUCTION Voice over IP (VoIP) is becoming a major communication service for enterprises and individuals since the cost of VoIP calls is low and the voice quality is getting better. To date, there are many VoIP products that are able to provide high call quality such as Skype [1], Google Talk (Gtalk) [2], Microsoft Messenger (MSN) [3], and Yahoo! Messenger (YMSG) [4]. However, few information has been documented about protocol design used by these VoIP clients since the protocols are not standardized, many of them are proprietary, and the creators of these softwares want to keep their information confidential and protect their protocol design form competitors. In this paper, we have generated and captured network traffic in order to determine the broad characteristics of one of the most recent and fast growing VoIP applications, Google Talk.