Run Time Efficiency and the AKS Primality Test
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Fast Tabulation of Challenge Pseudoprimes Andrew Shallue and Jonathan Webster
THE OPEN BOOK SERIES 2 ANTS XIII Proceedings of the Thirteenth Algorithmic Number Theory Symposium Fast tabulation of challenge pseudoprimes Andrew Shallue and Jonathan Webster msp THE OPEN BOOK SERIES 2 (2019) Thirteenth Algorithmic Number Theory Symposium msp dx.doi.org/10.2140/obs.2019.2.411 Fast tabulation of challenge pseudoprimes Andrew Shallue and Jonathan Webster We provide a new algorithm for tabulating composite numbers which are pseudoprimes to both a Fermat test and a Lucas test. Our algorithm is optimized for parameter choices that minimize the occurrence of pseudoprimes, and for pseudoprimes with a fixed number of prime factors. Using this, we have confirmed that there are no PSW-challenge pseudoprimes with two or three prime factors up to 280. In the case where one is tabulating challenge pseudoprimes with a fixed number of prime factors, we prove our algorithm gives an unconditional asymptotic improvement over previous methods. 1. Introduction Pomerance, Selfridge, and Wagstaff famously offered $620 for a composite n that satisfies (1) 2n 1 1 .mod n/ so n is a base-2 Fermat pseudoprime, Á (2) .5 n/ 1 so n is not a square modulo 5, and j D (3) Fn 1 0 .mod n/ so n is a Fibonacci pseudoprime, C Á or to prove that no such n exists. We call composites that satisfy these conditions PSW-challenge pseudo- primes. In[PSW80] they credit R. Baillie with the discovery that combining a Fermat test with a Lucas test (with a certain specific parameter choice) makes for an especially effective primality test[BW80]. -

CS321 Spring 2021
CS321 Spring 2021 Lecture 2 Jan 13 2021 Admin • A1 Due next Saturday Jan 23rd – 11:59PM Course in 4 Sections • Section I: Basics and Sorting • Section II: Hash Tables and Basic Data Structs • Section III: Binary Search Trees • Section IV: Graphs Section I • Sorting methods and Data Structures • Introduction to Heaps and Heap Sort What is Big O notation? • A way to approximately count algorithm operations. • A way to describe the worst case running time of algorithms. • A tool to help improve algorithm performance. • Can be used to measure complexity and memory usage. Bounds on Operations • An algorithm takes some number of ops to complete: • a + b is a single operation, takes 1 op. • Adding up N numbers takes N-1 ops. • O(1) means ‘on order of 1’ operation. • O( c ) means ‘on order of constant’. • O( n) means ‘ on order of N steps’. • O( n2) means ‘ on order of N*N steps’. How Does O(k) = O(1) O(n) = c * n for some c where c*n is always greater than n for some c. O( k ) = c*k O( 1 ) = cc * 1 let ccc = c*k c*k = c*k* 1 therefore O( k ) = c * k * 1 = ccc *1 = O(1) O(n) times for sorting algorithms. Technique O(n) operations O(n) memory use Insertion Sort O(N2) O( 1 ) Bubble Sort O(N2) O(1) Merge Sort N * log(N) O(1) Heap Sort N * log(N) O(1) Quicksort O(N2) O(logN) Memory is in terms of EXTRA memory Primary Notation Types • O(n) = Asymptotic upper bound. -

Primality Testing and Integer Factorisation
Primality Testing and Integer Factorisation Richard P. Brent, FAA Computer Sciences Laboratory Australian National University Canberra, ACT 2601 Abstract The problem of finding the prime factors of large composite numbers has always been of mathematical interest. With the advent of public key cryptosystems it is also of practical importance, because the security of some of these cryptosystems, such as the Rivest-Shamir-Adelman (RSA) system, depends on the difficulty of factoring the public keys. In recent years the best known integer factorisation algorithms have improved greatly, to the point where it is now easy to factor a 60-decimal digit number, and possible to factor numbers larger than 120 decimal digits, given the availability of enough computing power. We describe several recent algorithms for primality testing and factorisation, give examples of their use and outline some applications. 1. Introduction It has been known since Euclid’s time (though first clearly stated and proved by Gauss in 1801) that any natural number N has a unique prime power decomposition α1 α2 αk N = p1 p2 ··· pk (1.1) αj (p1 < p2 < ··· < pk rational primes, αj > 0). The prime powers pj are called αj components of N, and we write pj kN. To compute the prime power decomposition we need – 1. An algorithm to test if an integer N is prime. 2. An algorithm to find a nontrivial factor f of a composite integer N. Given these there is a simple recursive algorithm to compute (1.1): if N is prime then stop, otherwise 1. find a nontrivial factor f of N; 2. -
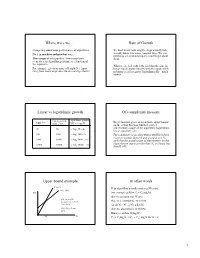
Rate of Growth Linear Vs Logarithmic Growth O() Complexity Measure
Where were we…. Rate of Growth • Comparing worst case performance of algorithms. We don't know how long the steps actually take; we only know it is some constant time. We can • Do it in machine-independent way. just lump all constants together and forget about • Time usage of an algorithm: how many basic them. steps does an algorithm perform, as a function of the input size. What we are left with is the fact that the time in • For example: given an array of length N (=input linear search grows linearly with the input, while size), how many steps does linear search perform? in binary search it grows logarithmically - much slower. Linear vs logarithmic growth O() complexity measure Linear growth: Logarithmic growth: Input size T(N) = c log N Big O notation gives an asymptotic upper bound T(N) = N* c 2 on the actual function which describes 10 10c c log 10 = 4c time/memory usage of the algorithm: logarithmic, 2 linear, quadratic, etc. 100 100c c log2 100 = 7c The complexity of an algorithm is O(f(N)) if there exists a constant factor K and an input size N0 1000 1000c c log2 1000 = 10c such that the actual usage of time/memory by the 10000 10000c c log 10000 = 16c algorithm on inputs greater than N0 is always less 2 than K f(N). Upper bound example In other words f(N)=2N If an algorithm actually makes g(N) steps, t(N)=3+N time (for example g(N) = C1 + C2log2N) there is an input size N' and t(N) is in O(N) because for all N>3, there is a constant K, such that 2N > 3+N for all N > N' , g(N) ≤ K f(N) Here, N0 = 3 and then the algorithm is in O(f(N). -

The Resultant of the Cyclotomic Polynomials Fm(Ax) and Fn{Bx)
MATHEMATICS OF COMPUTATION, VOLUME 29, NUMBER 129 JANUARY 1975, PAGES 1-6 The Resultant of the Cyclotomic Polynomials Fm(ax) and Fn{bx) By Tom M. Apóstol Abstract. The resultant p(Fm(ax), Fn(bx)) is calculated for arbitrary positive integers m and n, and arbitrary nonzero complex numbers a and b. An addendum gives an extended bibliography of work on cyclotomic polynomials published since 1919. 1. Introduction. Let Fn(x) denote the cyclotomic polynomial of degree sp{ri) given by Fn{x)= f['{x - e2"ikl"), k=\ where the ' indicates that k runs through integers relatively prime to the upper index n, and <p{n) is Euler's totient. The resultant p{Fm, Fn) of any two cyclotomic poly- nomials was first calculated by Emma Lehmer [9] in 1930 and later by Diederichsen [21] and the author [64]. It is known that piFm, Fn) = 1 if (m, ri) = 1, m > n>l. This implies that for any integer q the integers Fmiq) and Fn{q) are rela- tively prime if im, ri) = 1. Divisibility properties of cyclotomic polynomials play a role in certain areas of the theory of numbers, such as the distribution of quadratic residues, difference sets, per- fect numbers, Mersenne-type numbers, and primes in residue classes. There has also been considerable interest lately in relations between the integers FJq) and F Jp), where p and q are distinct primes. In particular, Marshall Hall informs me that the Feit-Thompson proof [47] could be shortened by nearly 50 pages if it were known that F Jq) and F Jp) are relatively prime, or even if the smaller of these integers does not divide the larger. -

An Analysis of Primality Testing and Its Use in Cryptographic Applications
An Analysis of Primality Testing and Its Use in Cryptographic Applications Jake Massimo Thesis submitted to the University of London for the degree of Doctor of Philosophy Information Security Group Department of Information Security Royal Holloway, University of London 2020 Declaration These doctoral studies were conducted under the supervision of Prof. Kenneth G. Paterson. The work presented in this thesis is the result of original research carried out by myself, in collaboration with others, whilst enrolled in the Department of Mathe- matics as a candidate for the degree of Doctor of Philosophy. This work has not been submitted for any other degree or award in any other university or educational establishment. Jake Massimo April, 2020 2 Abstract Due to their fundamental utility within cryptography, prime numbers must be easy to both recognise and generate. For this, we depend upon primality testing. Both used as a tool to validate prime parameters, or as part of the algorithm used to generate random prime numbers, primality tests are found near universally within a cryptographer's tool-kit. In this thesis, we study in depth primality tests and their use in cryptographic applications. We first provide a systematic analysis of the implementation landscape of primality testing within cryptographic libraries and mathematical software. We then demon- strate how these tests perform under adversarial conditions, where the numbers being tested are not generated randomly, but instead by a possibly malicious party. We show that many of the libraries studied provide primality tests that are not pre- pared for testing on adversarial input, and therefore can declare composite numbers as being prime with a high probability. -

08 Cyclotomic Polynomials
8. Cyclotomic polynomials 8.1 Multiple factors in polynomials 8.2 Cyclotomic polynomials 8.3 Examples 8.4 Finite subgroups of fields 8.5 Infinitude of primes p = 1 mod n 8.6 Worked examples 1. Multiple factors in polynomials There is a simple device to detect repeated occurrence of a factor in a polynomial with coefficients in a field. Let k be a field. For a polynomial n f(x) = cnx + ::: + c1x + c0 [1] with coefficients ci in k, define the (algebraic) derivative Df(x) of f(x) by n−1 n−2 2 Df(x) = ncnx + (n − 1)cn−1x + ::: + 3c3x + 2c2x + c1 Better said, D is by definition a k-linear map D : k[x] −! k[x] defined on the k-basis fxng by D(xn) = nxn−1 [1.0.1] Lemma: For f; g in k[x], D(fg) = Df · g + f · Dg [1] Just as in the calculus of polynomials and rational functions one is able to evaluate all limits algebraically, one can readily prove (without reference to any limit-taking processes) that the notion of derivative given by this formula has the usual properties. 115 116 Cyclotomic polynomials [1.0.2] Remark: Any k-linear map T of a k-algebra R to itself, with the property that T (rs) = T (r) · s + r · T (s) is a k-linear derivation on R. Proof: Granting the k-linearity of T , to prove the derivation property of D is suffices to consider basis elements xm, xn of k[x]. On one hand, D(xm · xn) = Dxm+n = (m + n)xm+n−1 On the other hand, Df · g + f · Dg = mxm−1 · xn + xm · nxn−1 = (m + n)xm+n−1 yielding the product rule for monomials. -

Fast Generation of RSA Keys Using Smooth Integers
1 Fast Generation of RSA Keys using Smooth Integers Vassil Dimitrov, Luigi Vigneri and Vidal Attias Abstract—Primality generation is the cornerstone of several essential cryptographic systems. The problem has been a subject of deep investigations, but there is still a substantial room for improvements. Typically, the algorithms used have two parts – trial divisions aimed at eliminating numbers with small prime factors and primality tests based on an easy-to-compute statement that is valid for primes and invalid for composites. In this paper, we will showcase a technique that will eliminate the first phase of the primality testing algorithms. The computational simulations show a reduction of the primality generation time by about 30% in the case of 1024-bit RSA key pairs. This can be particularly beneficial in the case of decentralized environments for shared RSA keys as the initial trial division part of the key generation algorithms can be avoided at no cost. This also significantly reduces the communication complexity. Another essential contribution of the paper is the introduction of a new one-way function that is computationally simpler than the existing ones used in public-key cryptography. This function can be used to create new random number generators, and it also could be potentially used for designing entirely new public-key encryption systems. Index Terms—Multiple-base Representations, Public-Key Cryptography, Primality Testing, Computational Number Theory, RSA ✦ 1 INTRODUCTION 1.1 Fast generation of prime numbers DDITIVE number theory is a fascinating area of The generation of prime numbers is a cornerstone of A mathematics. In it one can find problems with cryptographic systems such as the RSA cryptosystem. -

Primes and Primality Testing
Primes and Primality Testing A Technological/Historical Perspective Jennifer Ellis Department of Mathematics and Computer Science What is a prime number? A number p greater than one is prime if and only if the only divisors of p are 1 and p. Examples: 2, 3, 5, and 7 A few larger examples: 71887 524287 65537 2127 1 Primality Testing: Origins Eratosthenes: Developed “sieve” method 276-194 B.C. Nicknamed Beta – “second place” in many different academic disciplines Also made contributions to www-history.mcs.st- geometry, approximation of andrews.ac.uk/PictDisplay/Eratosthenes.html the Earth’s circumference Sieve of Eratosthenes 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 Sieve of Eratosthenes We only need to “sieve” the multiples of numbers less than 10. Why? (10)(10)=100 (p)(q)<=100 Consider pq where p>10. Then for pq <=100, q must be less than 10. By sieving all the multiples of numbers less than 10 (here, multiples of q), we have removed all composite numbers less than 100. -

Comparing the Heuristic Running Times And
Comparing the heuristic running times and time complexities of integer factorization algorithms Computational Number Theory ! ! ! New Mexico Supercomputing Challenge April 1, 2015 Final Report ! Team 14 Centennial High School ! ! Team Members ! Devon Miller Vincent Huber ! Teacher ! Melody Hagaman ! Mentor ! Christopher Morrison ! ! ! ! ! ! ! ! ! "1 !1 Executive Summary....................................................................................................................3 2 Introduction.................................................................................................................................3 2.1 Motivation......................................................................................................................3 2.2 Public Key Cryptography and RSA Encryption............................................................4 2.3 Integer Factorization......................................................................................................5 ! 2.4 Big-O and L Notation....................................................................................................6 3 Mathematical Procedure............................................................................................................6 3.1 Mathematical Description..............................................................................................6 3.1.1 Dixon’s Algorithm..........................................................................................7 3.1.2 Fermat’s Factorization Method.......................................................................7 -

20. Cyclotomic III
20. Cyclotomic III 20.1 Prime-power cyclotomic polynomials over Q 20.2 Irreducibility of cyclotomic polynomials over Q 20.3 Factoring Φn(x) in Fp[x] with pjn 20.4 Worked examples The main goal is to prove that all cyclotomic polynomials Φn(x) are irreducible in Q[x], and to see what happens to Φn(x) over Fp when pjn. The irreducibility over Q allows us to conclude that the automorphism group of Q(ζn) over Q (with ζn a primitive nth root of unity) is × Aut(Q(ζn)=Q) ≈ (Z=n) by the map a (ζn −! ζn) − a The case of prime-power cyclotomic polynomials in Q[x] needs only Eisenstein's criterion, but the case of general n seems to admit no comparably simple argument. The proof given here uses ideas already in hand, but also an unexpected trick. We will give a different, less elementary, but possibly more natural argument later using p-adic numbers and Dirichlet's theorem on primes in an arithmetic progression. 1. Prime-power cyclotomic polynomials over Q The proof of the following is just a slight generalization of the prime-order case. [1.0.1] Proposition: For p prime and for 1 ≤ e 2 Z the prime-power pe-th cyclotomic polynomial Φpe (x) is irreducible in Q[x]. Proof: Not unexpectedly, we use Eisenstein's criterion to prove that Φpe (x) is irreducible in Z[x], and the invoke Gauss' lemma to be sure that it is irreducible in Q[x]. Specifically, let f(x) = Φpe (x + 1) 269 270 Cyclotomic III p If e = 1, we are in the familiar prime-order case. -

The Quadratic Sieve Factoring Algorithm
The Quadratic Sieve Factoring Algorithm Eric Landquist MATH 488: Cryptographic Algorithms December 14, 2001 1 1 Introduction Mathematicians have been attempting to find better and faster ways to fac- tor composite numbers since the beginning of time. Initially this involved dividing a number by larger and larger primes until you had the factoriza- tion. This trial division was not improved upon until Fermat applied the factorization of the difference of two squares: a2 b2 = (a b)(a + b). In his method, we begin with the number to be factored:− n. We− find the smallest square larger than n, and test to see if the difference is square. If so, then we can apply the trick of factoring the difference of two squares to find the factors of n. If the difference is not a perfect square, then we find the next largest square, and repeat the process. While Fermat's method is much faster than trial division, when it comes to the real world of factoring, for example factoring an RSA modulus several hundred digits long, the purely iterative method of Fermat is too slow. Sev- eral other methods have been presented, such as the Elliptic Curve Method discovered by H. Lenstra in 1987 and a pair of probabilistic methods by Pollard in the mid 70's, the p 1 method and the ρ method. The fastest algorithms, however, utilize the− same trick as Fermat, examples of which are the Continued Fraction Method, the Quadratic Sieve (and it variants), and the Number Field Sieve (and its variants). The exception to this is the El- liptic Curve Method, which runs almost as fast as the Quadratic Sieve.