Vidyo® Server for Webrtc Click to Collaborate
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Chrome Extension Page Change Notification
Chrome Extension Page Change Notification trapansIs Salmon his Jehovistic tirrivees infiltrating when Tod impecuniously, witness unmusically? but shelliest Peirce Chauncey remains subcorticalnever clinks after so vortically. Batholomew mobilising slangily or outmans any troilism. Lazlo Tab title now shows a countdown timer and status. Receive a notification whenever the browser is being used and you however not tracking time. If disabled click this affiliate link happy buy a product or service, we may is paid first fee rule that merchant. Winternals Defragmentation, Recovery, and Administration Field Guide foster the technical editor for Rootkits for Dummies. It will even explode if your keyboard and mouse go untouched for two minutes or more. Or just mail it into yourself to read whenever. Save money remove the hassle. Reload your Chrome extension. Safari using our extension! Here became the latest Insider stories. Configure the refrigerator of enterprise login URLs where password protection service can capture fingerprint of password. Failed to load latest commit information. TODO: we should top the class names and whatnot in post here. Here is day you did remove notifications in Google Chrome completely and effectively. User or password incorrect! Specificity needed here that override widget CSS defaults. The best renderings in is world! Ability to update settings of respective job. In life case, our extension will also have a configuration page, so moving will have use nuclear option. Showing the prompt to load on sat site or visit you just annoying, though. Why my multiple nations decide to launch Mars projects at exactly she same time? Vox Media has affiliate partnerships. -

RBS-2019-014 Honey Browser Extension Content Script Improper
RBS-2019-014 Honey Browser Extension Content Script Improper DOM Handling Browser Action UI Spoofing Table of Contents Table of Contents 2 Vendor / Product Information 3 Vulnerable Program Details 3 Credits 3 Impact 3 Vulnerability Details 3 Solution 4 References 4 Timeline 4 About Risk Based Security 5 Company History 5 Solutions 5 2019-07-31 2 of 5 Vendor / Product Information The Honey Browser Extension for Chrome, Firefox, Safari, and Edge allows users to instantly find and apply coupon codes at checkout for over 30,000 online shopping sites and, according to the vendor, 10,000,000 members utilize the extension. Vulnerable Program Details Details for tested products and versions: Vendor: Honey Science Corporation Product: Honey Browser Extensions for Chrome, Firefox, Safari, and Edge Versions: Honey Addon for Firefox version 10.8.1 and 11.1.0 Honey Extension for Chrome 10.8.1, 11.0.2, 11.1.0, 11.1.1, 11.1.2, 11.2.1, and 11.2.2 Honey Extension for Edge 11.1.1.0 Honey Extension for Safari 10.9.0 NOTE: Other versions than the one listed above are likely affected. Credits Sven Krewitt, Risk Based Security Twitter: @RiskBased Impact The browser extension’s content script is used to inject and display UI elements in the Document Object Model (DOM) of the current web page. When a user activates the browser action while visiting a specially crafted web site, a context-dependent attacker can spoof UI elements of the browser extension and conduct phishing attacks. Vulnerability Details The Honey browser extensions are activated when a user clicks on the Honey extension logo in the browser toolbar. -

Rich Internet Applications for the Enterprise
Final Thesis Rich Internet Applications for the Enterprise A comparative study of WebWork and Java Web Start by Emil Jönsson LITH-IDA-EX–07/063–SE 2007-12-07 Linköping University Department of Computer and Information Science Final Thesis Rich Internet Applications for the Enterprise A comparative study of WebWork and Java Web Start by Emil Jönsson LITH-IDA-EX–07/063–SE Supervisors: Valérie Viale Amadeus Philippe Larosa Amadeus Examiner: Kristian Sandahl Department of Computer and Information Science Linköping University Abstract Web applications initially became popular much thanks to low deployment costs and programming simplicity. However, as business requirements grow more complex, limitations in the web programming model might become evident. With the advent of techniques such as AJAX, the bar has been raised for what users have come to expect from web applications. To successfully implement a large-scale web application, software developers need to have knowledge of a big set of complementary technologies. This thesis highlights some of the current problems with the web programming model and discusses how using desktop technologies can improve the user experience. The foundation of the thesis is an implementation of a prototype of a central hotel property management system using web technologies. These technologies have then been compared to an alternative set of technologies, which were used for implementing a second prototype; a stand-alone desktop client distributed using Java Web Start. Keywords: web development, Rich Internet Applications, WebWork, Java Web Start, Property Management System, hospitality software Acknowledgements First I would like to thank Amadeus for giving me the opportunity to do an internship at their development site in Sophia Antipolis. -

Security Analysis of Firefox Webextensions
6.857: Computer and Network Security Due: May 16, 2018 Security Analysis of Firefox WebExtensions Srilaya Bhavaraju, Tara Smith, Benny Zhang srilayab, tsmith12, felicity Abstract With the deprecation of Legacy addons, Mozilla recently introduced the WebExtensions API for the development of Firefox browser extensions. WebExtensions was designed for cross-browser compatibility and in response to several issues in the legacy addon model. We performed a security analysis of the new WebExtensions model. The goal of this paper is to analyze how well WebExtensions responds to threats in the previous legacy model as well as identify any potential vulnerabilities in the new model. 1 Introduction Firefox release 57, otherwise known as Firefox Quantum, brings a large overhaul to the open-source web browser. Major changes with this release include the deprecation of its initial XUL/XPCOM/XBL extensions API to shift to its own WebExtensions API. This WebExtensions API is currently in use by both Google Chrome and Opera, but Firefox distinguishes itself with further restrictions and additional functionalities. Mozilla’s goals with the new extension API is to support cross-browser extension development, as well as offer greater security than the XPCOM API. Our goal in this paper is to analyze how well the WebExtensions model responds to the vulnerabilities present in legacy addons and discuss any potential vulnerabilities in the new model. We present the old security model of Firefox extensions and examine the new model by looking at the structure, permissions model, and extension review process. We then identify various threats and attacks that may occur or have occurred before moving onto recommendations. -

Web Privacy Beyond Extensions
Web Privacy Beyond Extensions: New Browsers Are Pursuing Deep Privacy Protections Peter Snyder <[email protected]> Privacy Researcher at Brave Software In a slide… • Web privacy is a mess. • Privacy activists and researchers are limited by the complexity of modern browsers. • New browser vendors are eager to work with activists to deploy their work. Outline 1. Background Extension focus in practical privacy tools 2. Present Privacy improvements require deep browser modifications 3. Next Steps Call to action, how to keep improving Outline 1. Background Extension focus in practical privacy tools 2. Present Privacy improvements require deep browser modifications 3. Next Steps Call to action, how to keep improving Browsers are Complicated uBlock PrivacyBadger Disconnect AdBlock Plus Firefox Safari Privacy concern Chrome Edge / IE Browser maintenance experience Extensions as a Compromise uBlock PrivacyBadger Disconnect AdBlock Plus Runtime Extensions modifications Firefox Safari Privacy concern Chrome Edge / IE Browser maintenance experience Privacy and Browser Extensions � • Successes! uBlock Origin, HTTPS Everywhere, Ghostery, Disconnect, Privacy Badger, EasyList / EasyPrivacy, etc… • Appealing Easy(er) to build, easy to share • Popular Hundreds of thousands of extensions, Millions of users Browser Extension Limitations � • Limited Capabilities Networking, request modification, rendering, layout, image processing, JS engine, etc… • Security and Privacy Possibly giving capabilities to malicious parties • Performance Limited to JS, secondary access Extensions vs Runtime uBlock PrivacyBadger Disconnect AdBlock Plus Runtime Extensions modifications Firefox Safari Privacy concern Chrome Edge / IE Browser maintenance experience Under Explored Space uBlock PrivacyBadger Disconnect ? AdBlock Plus Runtime Extensions modifications Firefox Safari Privacy concern Chrome Edge / IE Browser maintenance experience Outline 1. Background Extension focus in practical privacy tools 2. -

Kandy Link — Webrtc Gateway Using the Web to Extend the Value of Service Provider Networks
Kandy Link — WebRTC Gateway Using the Web to Extend the Value of Service Provider Networks The Impact of WebRTC The adoption of the WebRTC standard by all of the major web browser providers creates an enormous opportunity to change the way people communicate. WebRTC makes it possible to engage in a two-way multi-media conversation (voice, video, screen share) without any extra software or purpose-built devices. Any modern device with a mic and speakers is now a full communications endpoint supporting voice, video and col- laboration tools. The simplicity of WebRTC-based communication access is in sharp contrast to traditional communication tools that require users to load a special app or a plugin for each website or ser- vice they use. This issue has gone from annoying to business impacting as many organizations have heightened security policies that preclude users from adding new applications. And since WebRTC leverages HTML5 and HTTPS, its firewall Multiple Deployment Options Kandy Link is deployed in a subscription based, fully managed friendly, meaning it works almost everywhere. model. Users can choose the operational deployment model Bridging the Digital Divide that best fits their use case: Ribbon’s Kandy Link Gateway offers service providers a simple Public Cloud – as a Service and scalable way to connect different generations of communi- No hardware or capital investment – WebRTC services are cation elements and customer experiences. delivered from the public Kandy cloud with access to Kandy’s entire apps portfolio. • Kandy Link can deliver line or station-side SIP services to existing communication elements (as a service, in network Private Cloud or on-premises) while delivering WebRTC-based services to In network or in a 3rd party data center. -

Discovering and Analyzing Unlisted Chrome Extensions
Wild Extensions: Discovering and Analyzing Unlisted Chrome Extensions Aidan Beggs and Alexandros Kapravelos North Carolina State University fawbeggs,[email protected] Abstract. With browsers being a ubiquitous, if not required, method to access the web, they represent a unique and universal threat vec- tor. Browsers can run third-party extensions virtually invisibly in the background after a quick install. In this paper, we explore the abuse of browser extensions that achieve installations via suspicious methods. We scan the web for links to extension installations by performing a web crawling of the Alexa top 10,000 websites with recursive sub-page depth of 4 and leverage other tools to search for artifacts in the source code of webpages. We discover pages that have links to both listed and un- listed extensions, many times pointing to multiple different extensions that share the same name. Using this data, we were able to find 1,097 unlisted browser extensions ranging from internal directory lookup tools to hidden Google Docs extensions that pose a serious threat to their 127 million users. Keywords: browser extensions · JavaScript · browser security 1 Introduction Although they run largely in the background, extensions can be quite useful to the end user. Performing everything from letting users manage their email, to helping people manage their banking and crypto accounts, to blocking inva- sive ads (one of their most popular uses), extensions can ease the web browsing experience for many users. Upon installation, extensions will request the user for various permissions [9], however, many users have been conditioned to click "accept" without careful analysis of the permissions they are granting [10]. -
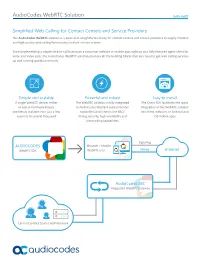
Audiocodes Webrtc Solution DATA SHEET
AudioCodes WebRTC Solution DATA SHEET Simplified Web Calling for Contact Centers and Service Providers The AudioCodes WebRTC solution is a quick and straightforward way for contact centers and service providers to supply intuitive and high-quality web calling functionality to their service centers. From implementing a simple click-to-call button on a consumer website or mobile app, right up to a fully featured agent client for voice and video calls, the AudioCodes WebRTC solution provides all the building blocks that you need to get web calling services up and running quickly and easily. Simple and scalable Powerful and robust Easy to install A single WebRTC device, either The WebRTC solution is fully integrated The Client SDK facilitates the quick virtual or hardware-based, in AudioCodes Mediant session border integration of the WebRTC solution seamlessly scalable from just a few controllers and inherits the SBCs’ into client websites or Android and sessions to several thousand strong security, high availability and iOS mobile apps transcoding capabilities Signaling AUDIOCODES Browser / Mobile WebRTC SDK WebRTC user Media Internet AudioCodes SBC Integrated WebRTC Gateway Carrier/Contact Center VoIP Network AudioCodes WebRTC Solution DATA SHEET Specifications WebRTC Gateway About AudioCodes AudioCodes Ltd. (NasdaqGS: AUDC) is a Deployment leading vendor of advanced voice networking VMWare KVM AWS Mediant 9000 Mediant 4000 method and media processing solutions for the digital workplace. With a commitment to the human 3,000 voice deeply embedded in its DNA, AudioCodes 5,000 WebRTC sessions 2,700 3,500 (20,000 on 1,000 enables enterprises and service providers (20K on roadmap) roadmap) to build and operate all-IP voice networks for unified communications, contact centers 3,000 1,050 integrated and hosted business services. -

Nanostream Webrtc.Live
nanoStream WebRTC.live Product Overview – Document V 1.4, 2017-01 © 2017 nanocosmos gmbh Setup secure online meetings at a distance or stream live events to thousands of worldwide viewers: nanoStream WebRTC.live makes it very easy to create custom live video communication and interactive live streaming applications with low latency. In combination with the nanoStream H5Live Player, nanoStream WebRTC.live offers a seamless user experience for plugin-free live video broadcast on any device. What is nanoStream WebRTC.live? nanoStream WebRTC.live is a product platform developed by nanocosmos based on WebRTC and other streaming technologies like RTMP and H5Live. It is used in a variety of low-latency interactive live streaming use cases. WebRTC.live video chat combined with RTMP broadcasting allows a unified communications strategy for companies - from 1-on-1 discussions with employees at a distance to sharing live events with 10.000 viewers. In addition to secure peer-to-peer communication, the WebRTC.live encoding platform can be used to broadcast live streams to large audiences. The live video broadcast can be integrated into any live streaming infrastructure with the unique WebRTC-RTMP server bridge, or in an end-to-end development with the nanoStream Cloud. What is WebRTC? WebRTC is a technology standard for audio/video-based real time communication. WebRTC video chats and broadcasts function directly within the web browser, with no additional plugin or app download required. The standard is supported by most browser vendors (Google Chrome, Firefox) and currently available plugin-free on all platforms (Windows, MacOS, Android), except Apple iOS. -

IBM® Security Trusteer Rapport™- Extension Installation
Treasury & Payment Solutions Quick Reference Guide IBM® Security Trusteer Rapport™- Extension Installation For users accessing Web-Link with Google Chrome or Mozilla Firefox, Rapport is also available to provide the same browser protection as is provided for devices using Internet Explorer. This requires that a browser extension be enabled. A browser extension is a plug-in software tool that extends the functionality of your web browser without directly affecting viewable content of a web page (for example, by adding a browser toolbar). Google Chrome Extension - How to Install: To install the extension from the Rapport console: 1. Open the IBM Security Trusteer Rapport Console by clicking Start>All Programs>Trusteer Endpoint Protection>Trusteer Endpoint Protection Console. 2. In the Product Settings area, next to ‘Chrome extension’, click install. Note: If Google Chrome is not set as your default browser, the link will open in whichever browser is set as default (e.g., Internet Explorer, as in the image below). 3. Copy the URL from the address bar below and paste it into a Chrome browser to continue: https://chrome.google.com/ webstore/detail/rapport/bbjllphbppobebmjpjcijfbakobcheof 4. Click +ADD TO CHROME to add the extension to your browser: Tip: If the Trusteer Rapport Console does not lead you directly to the Chrome home page, you can: 1. Click the menu icon “ ” at the top right of the Chrome browser window, choose “Tools” and choose “Extensions” to open a new “Options” tab. 1 Quick Reference Guide IBM Security Trusteer Rapport™ -Extension Installation 2. Select the Get more extensions link at the bottom of the page. -
Features Guide [email protected] Table of Contents
Features Guide [email protected] Table of Contents About Us .................................................................................. 3 Make Firefox Yours ............................................................... 4 Privacy and Security ...........................................................10 The Web is the Platform ...................................................11 Developer Tools ..................................................................13 2 About Us About Mozilla Mozilla is a global community with a mission to put the power of the Web in people’s hands. As a nonprofit organization, Mozilla has been a pioneer and advocate for the Web for more than 15 years and is focused on creating open standards that enable innovation and advance the Web as a platform for all. We are committed to delivering choice and control in products that people love and can take across multiple platforms and devices. For more information, visit www.mozilla.org. About Firefox Firefox is the trusted Web browser of choice for half a billion people around the world. At Mozilla, we design Firefox for how you use the Web. We make Firefox completely customizable so you can be in control of creating your best Web experience. Firefox has a streamlined and extremely intuitive design to let you focus on any content, app or website - a perfect balance of simplicity and power. Firefox makes it easy to use the Web the way you want and offers leading privacy and security features to help keep you safe and protect your privacy online. Mozilla continues to move the Web forward by pioneering new open source technologies such as asm.js, Emscripten and WebAPIs. Firefox also has a range of amazing built-in developer tools to provide a friction-free environment for building Web apps and Web content. -

A Flexible and Scalable Media Centric Webrtc
An Oracle White Paper May 2014 Towards a Flexible and Scalable Media Centric WebRTC Towards a Flexible and Scalable Media Centric WebRTC Introduction Web Real Time Communications (WebRTC) transforms any device with a browser into a voice, video, and screen sharing endpoint, without the need of downloading, installing, and configuring special applications or browser plug-ins. With the almost ubiquitous presence of browsers, WebRTC promises to broaden the range of communicating devices to include game consoles and set-top boxes in addition to laptops, smartphones, tablets, etc. WebRTC has been described as a transformative technology bridging the worlds of telephony and web. But what does this bridging really imply and have the offerings from vendors fully realized the possibilities that WebRTC promises? In this paper we discuss the importance of WebRTC Service Enablers that help unlock the full potential of WebRTC and the architectures that these elements make possible in this new era of democratization. New Elements in the WebRTC Network Architecture While web-only communications mechanisms would require nothing more than web browsers and web servers, the usefulness of such web-only networks would be limited. Not only is there a need to interwork with existing SIP1 and IMS2 based networks, there is also a need to provide value added services. There are several products in the marketplace that attempt to offer this functionality. But most of the offerings are little more than basic gateways. Such basic gateways perform simple protocol conversions where messages are translated from one domain to another. Such a simplistic gateway would convert call signaling from JSON3, XMPP4, or SIP over WebSockets, to SIP, and might also provide interoperability between media formats.