Ipres Jlj Bl Fx
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Ling Chia Wang (Student) and Masato R. Nakamura (Advisor) Background Objectives Comparison of PC Cooling Systems Summary Summer
Heat Transfer Analysis of Computer Components for Electronic Waste (e-waste) Reduction: Cardboard PC Case Design Project Ling Chia Wang (student) and Masato R. Nakamura (advisor) Department of Mechanical Engineering and Industrial Design Technology New York City College of Technology (City Tech), City University of New York (CUNY), Brooklyn, NY 11201 Background Comparison of PC Cooling Systems Cardboard PC Case Design Fans Low-noise CPU cooler GPU HDD and Reducing electric wastes (e-wastes) has been one of the main concerns DVD/Blu-ray Drive • A low-noise CPU cooler was proposed in 2012 that provides a more efficient heat in sustainable solid waste management since the development of dissipation capacity from the CPU to a finned heatsink without adding more heat pipes at Information Technology (IT) was started to accelerate. a lownoise level of a small fan under the confined space constraints of a computer chassis. Computational fluid dynamics (CFD) simulations were used to search for a • A short life cycle of computers demands an efficient recycling process, as 2 proper cooling design . Motherboard well as re-design of computer components. • E-waste of desktop PC in China and South Africa will rise by 500% in 2020 compared to their 2007 levels. Summary • One of the major components of desktop computers is a PC case: 49.8% by weight of wasted desktop computers. • During the e-waste recycling process, dismantling obsolete computers 2 Figure 5: Tentative design of cardboard PC (mainly liberating components from computer cases) takes a lot of Figure 2: schematic diagram of cooler (left), calculated temperature distribution (center), calculated velocity distribution (right) workload of skilled workers. -

In This Video We Are Going to See How a Personal Computer Hardware Is Organised the PC Was Designed with an Open Architecture
In this video we are going to see how a personal computer hardware is organised The PC was designed with an open architecture. This means that it uses standard modular components. We can add, replace, update or swap them easily and the computer will identify and handle the new devices automatically. The main component of a computer system is the motherboard or main board. It is a printed circuit board (PCB) that holds the main components of the computer and the electronics needed to communicate between them and to expand the system. We could say that it is the central nervous system of the computer. A motherboard provides the electrical connections by which the other components of the system communicate. Unlike a backplane, it also contains the central processing unit and hosts other subsystems and devices The form factor is the specification of a motherboard – the dimensions, power supply type, location of mounting holes, number of ports on the back panel, etc. In the IBM PC compatible industry, standard form factors ensure that parts are interchangeable across competing vendors and generations of technology, while in enterprise computing, form factors ensure that server modules fit into existing rack mount systems. Traditionally, the most significant specification is for that of the motherboard, which generally dictates the overall size of the case. The most used form factor for IBM PC compatible motherboards is ATX (Advanced Technology Extended) and its derivatives. For small form factor mainboards mini ITX is the de facto standard. A power supply unit (PSU) converts mains AC to low- voltage regulated DC power for the internal components of a computer. -

Antec NSK 4482B-GB Owner's Manual
Antec NSK-4482B Computer Cases owner's manual Free Online Library This website has one of the largest libraries with thousands different manuals and ebooks that will help you to understand absolutely any device and how to use it. Many people are searching for Antec NSK-4482B owner's manual, so you should take a closer look into our library, because we have couple of them right here. Every day we are uploading more informative books and documents about different appliances, devices and software. You can even print these PDF files and have all the necessary papers with you, no matter where you are. Antec NSK-4482B owner's manual Click here to read (36 pages) Browse this massive electronic library for more information about all de This is the list with most popular files that will tell you more about Antec (NSK 4482B-GB) device: Antec Piano Black Quiet Super Mini Tower. EC version setup guide Status: Available Download link: manualstorrent.com/share/12828/setup_guide/Piano-Black-Quiet-Super-Mini-Tower.-EC-version.pdf Antec Piano Black Quiet Super Mini Tower. EC version user guide Status: Available Download link: manualstorrent.com/share/12828/user_guide/Piano-Black-Quiet-Super-Mini-Tower.-EC-version.pdf Antec Piano Black Quiet Super Mini Tower. EC version operating instruction Status: Available Download link: manualstorrent.com/share/12828/operating_instruction/Piano-Black-Quiet-Super-Mini-Tower.-EC- version.pdf Antec 3U20ATX300EC Rack 300W 4x3.5"2x5.25" ATX operating instruction Status: Available Download link: manualstorrent.com/share/12830/operating_instruction/3U20ATX300EC-Rack-300W-4x3.5% -

8000 Plus Magazine Issue 17
THE BEST SELLIINIG IVI A<3 AZI INI E EOF=t THE AMSTRAD PCW Ten copies ofMin^g/jf^^ Office Professional to be ISSUE 17 • FEBRUARY 1988* £1.50 Could AMS's new desktop publishing package be the best yet? f PLUS: Complete buyer's guide to word processing, accounts, utilities and DTP software jgl- ) MASTERFILE 8000 FOR ALL AMSTRAD PCW COMPUTERS MASTERFILE 8000, the subject of so many Any file can make RELATIONAL references to up enquiries, is now available. to EIGHT read-only keyed files, the linkage being effected purely by the use of matching file and MASTERFILE 8000 is a totally new database data names. product. While drawing on the best features of the CPC versions, it has been designed specifically for You can import/merge ASCII files (e.g. from the PCW range. The resulting combination of MASTERFILE III), or export any data (e.g. to a control and power is a delight to use. word-processor), and merge files. For keyed files this is a true merge, not just an append operation. Other products offer a choice between fast but By virtue of export and re-import you can make a limited-capacity RAM files, and large-capacity but copy of a file in another key sequence. New data cumbersome fixed-length, direct-access disc files. fields can be added at any time. MASTERFILE 8000 and the PCW RAM disc combine to offer high capacity with fast access to File searches combine flexibility with speed. variable-length data. File capacity is limited only (MASTERFILE 8000 usually waits for you, not by the size of your RAM disc. -

Quick Start Thank You for Purchasing the MSI® MEG Z390 GODLIKE Motherboard
Quick Start Thank you for purchasing the MSI® MEG Z390 GODLIKE motherboard. This Quick Start section provides demonstration diagrams about how to install your computer. Some of the installations also provide video demonstrations. Please link to the URL to watch it with the web browser on your phone or tablet. You may have even link to the URL by scanning the QR code. Preparing Tools and Components Intel® LGA 1151 CPU CPU Fan Chassis DDR4 Memory Power Supply Unit Graphics Card Thermal Paste SATA Hard Disk Drive SATA DVD Drive Phillips Screwdriver A Package of Screws Quick Start 1 Safety Information y The components included in this package are prone to damage from electrostatic discharge (ESD). Please adhere to the following instructions to ensure successful computer assembly. y Ensure that all components are securely connected. Loose connections may cause the computer to not recognize a component or fail to start. y Hold the motherboard by the edges to avoid touching sensitive components. y It is recommended to wear an electrostatic discharge (ESD) wrist strap when handling the motherboard to prevent electrostatic damage. If an ESD wrist strap is not available, discharge yourself of static electricity by touching another metal object before handling the motherboard. y Store the motherboard in an electrostatic shielding container or on an anti-static pad whenever the motherboard is not installed. y Before turning on the computer, ensure that there are no loose screws or metal components on the motherboard or anywhere within the computer case. y Do not boot the computer before installation is completed. -

Fractal Design Define R4 Offers Minimalistic and Stunning Scandina- Vian Design Fused with Maximum Sound Reduction, Configurability and Functionality
Product Sheet Define R4 As part of the Define series of computer cases, the Fractal Design Define R4 offers minimalistic and stunning Scandina- vian design fused with maximum sound reduction, configurability and functionality. The Define R4 side and front door panels are fitted with dense, sound-absorbing material making it a benchmark for noise reduction. Moreover, the Define R4 accommodates up to 8 HDDs, all modern graphics card sizes, and multiple ventilation options - including two standard Silent Series R2 hydraulic bearing fans - to keep internal components at optimal temperatures. For ultimate functionality, the Define R4 features a front interface with USB 3.0 and an integrated three-speed fan controller behind the front panel door. Key features • High density noise-reducing material for an optimal silent case **To achieve a high level of noise reduction, material with mass should be incorporated which is what we strive to achieve with the dense bitumen used on the side panels • Patent pending ModuVent™ design allowing the user to choose between optimal silence or maximum airflow • Top HDD cage (5 trays total) can be rotated 90 degrees or removed for additional airflow or to accommodate long graphic cards up to 430mm in length • Three-speed fan controller is strategically integrated in the front panel and supports up to 3 fans • Two Silent Series R2 fans included, featuring hydraulic bearings contributing to a longer life expectancy – Silent Series R2 retail fans will now come standard in all cases • Wider case body that allows -

Test-Drive Form That Follows Will Give You a Written Record to Reference at Your Own Pace in Your Own Home
56 Would You Buy a Car Without Test-Driving It? realize it isn’t such a big deal, and then continue learning more about the computer before you make your investment. It’s empowering to know that this is nothing more than a research expedition. No obligation, no financial outlay, no decision making. If you don’t want to go back, there is always the option of mail order or purchasing from the store by phone so you never have to reenter the place. And remember, if the salesperson you are dealing with really doesn’t appeal to you, give him the brushoff, let him get out of sight, smile sweetly at another salesperson, and watch her come running. Initially the computer store can sometimes add to any confusion you might have, especially after you get home and try to remember all you saw. The Test-Drive Form that follows will give you a written record to reference at your own pace in your own home. Copy these pages to bring with you to the store. If it’s easier, rip the pages out to make the copies. Test-Drive form 1. Store: Salesperson: Note the address and phone number of the store and the name of the salesperson you spoke with. 2. Brand & Model of Computer: Include any numbers that follow the brand name—this will indicate the model. For example: Dell Dimension 966. 3. Cost: Note the basic cost and any additional costs. For example: $499 plus $50 for RAM upgrade = $549. sYsTeM iNforMaTioN 4. Computer Case: h Standard h Tower Is the computer case a standard model or a tower model that will go on the floor? Test-Drive 57 5. -

M the Official Amstrad Business Magazine
Vol. 1 No. 4 December 1986 AMSTRAD£1.25 | COMPUTING- V; ■ I mm m >■ V aL- The Official Amstrad Business Magazine The Condor 1 Commands - They couldn’t be simpler! Database Creation and Maintenance DEFINE Create, redefine or describe a database DESTROY Eliminate a database or file FORMAT Create or revise a form or HELP screen REORG Reorganize the structure of a database; add or delete items Information Input and Update APPEND Attach records of one database to another EMPTY Eliminate all data in a database ENTER Insert new data into a database POST Update entries in one database with those from another UPDATE Change entries in a J--.abase meeting specified cni Jiiitions Informations* ssingand Report Writing COMPARE ' ;v*i.*are orgies in two ■■■...•.vjfcsfa- /not) n • hing o editions and The Database Manager and Reporter. c. < RE ;• i JLT database COMPUTE . ie<: iesina You know that Caxton only publish superior software products. LIST 0; datf.'i j;,se records in Cardbox is the world’s best-selling simple electronic card index. sesjc :?-^er Brainstorm is the world’s first ideas processor. Scratchpad plus is the PRINT Pirfctf. shtab^va records in ewisr only enhanced Virtual Memory Spreadsheet available foryour PRINTER Pri; ;lei output control and Amstrad. And Touch ’n’ Go is the UK’s most highly respected disk- refection SELECT Select database records based typing T\itor. meeting specified conditions, creating a Now we present Condor 1 - Mainframe computing for your Amstrad. RESULT database SORT Sort database records by Condor 1 is an extensive database management and reporting system entries STAX View or print statistics of for the non-programmer. -

Copyright Disclaimer Federal Communications Commission (FCC
Copyright © Copyright 2004. All rights reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated into any language or computer language, in any form or by any means, electronic, mechanical, magnetic, optical, chemical, manual or otherwise, without the prior written permission of our company. All brand and product names are trademarks and/or registered trademarks of their respective holders. Disclaimer We make no representations or warranties, either expressed or implied, with respect to the contents hereof and specifically disclaims any warranties, merchantability or fitness for any particular purpose. Any software described in this manual is sold or licensed “as is”. Should the programs prove defective following their purchase, the buyer (and not our company., its distributor, or its dealer) assumes the entire cost of all necessary servicing, repair, and any incidental or consequential damages resulting from any defect in the software. Further, we reserve the right to revise this publication and to make changes from time to time in the contents hereof without obligation to notify any person of such revision or changes. Federal Communications Commission (FCC) Statement This equipment has been tested and found to comply with the limits for a class B device, pursuant to part 15 of the FCC rules. These limits are designed to provide reasonable protection against harmful interference in residential installation. This equipment generates, uses, and can radiate radio frequency energy and, if not installed and used in accordance with the instructions may cause harmful interference to radio communications. However, there is no guarantee that interference will not occur in a particular installation. -

Chapter 1 PC Architecture
Chapter PC Architecture THE FOLLOWING OBJECTIVES ARE COVERED IN THIS CHAPTER: 1 1.1 Identify the names, purpose, and characteristics, of system modules. Recognize these modules by sight or definition. 1.5 Identify the names, purposes, and performance characteristics, of standardized/common peripheral ports, associated cabling, and their connectors. Recognize ports, cabling, and connectors, by sight. COPYRIGHTED MATERIAL A personal computer (PC) is a computing device made up of many distinct electronic components that all function together in order to accomplish some useful task (such as adding up the numbers in a spreadsheet or helping you write a letter). By this definition, note that we’re describing a computer as having many distinct parts that work together. Most computers today are modular. That is, they have components that can be removed and replaced with a component of similar function in order to improve performance. Each component has a very specific function. In this chapter, you will learn about the components that make up a typical PC, what their function is, and how they work together inside the PC. Unless specifically mentioned otherwise, throughout this book the terms PC and computer can be used interchangeably. The components in most computers include: The case The power supply The motherboard The processor /CPU Memory Storage devices The adapter cards Display devices Ports and cables As you read this chapter, please keep in mind that many of these parts will be covered in more detail in later chapters. Figure 1.1 shows an example of a typical PC and illustrates how some of these parts fit together. -

Hardware Components and Internal PC Connections
Technological University Dublin ARROW@TU Dublin Instructional Guides School of Multidisciplinary Technologies 2015 Computer Hardware: Hardware Components and Internal PC Connections Jerome Casey Technological University Dublin, [email protected] Follow this and additional works at: https://arrow.tudublin.ie/schmuldissoft Part of the Engineering Education Commons Recommended Citation Casey, J. (2015). Computer Hardware: Hardware Components and Internal PC Connections. Guide for undergraduate students. Technological University Dublin This Other is brought to you for free and open access by the School of Multidisciplinary Technologies at ARROW@TU Dublin. It has been accepted for inclusion in Instructional Guides by an authorized administrator of ARROW@TU Dublin. For more information, please contact [email protected], [email protected]. This work is licensed under a Creative Commons Attribution-Noncommercial-Share Alike 4.0 License Higher Cert/Bachelor of Technology – DT036A Computer Systems Computer Hardware – Hardware Components & Internal PC Connections: You might see a specification for a PC 1 such as "containing an Intel i7 Hexa core processor - 3.46GHz, 3200MHz Bus, 384 KB L1 cache, 1.5MB L2 cache, 12 MB L3 cache, 32nm process technology; 4 gigabytes of RAM, ATX motherboard, Windows 7 Home Premium 64-bit operating system, an Intel® GMA HD graphics card, a 500 gigabytes SATA hard drive (5400rpm), and WiFi 802.11 bgn". This section aims to discuss a selection of hardware parts, outline common metrics and specifications -
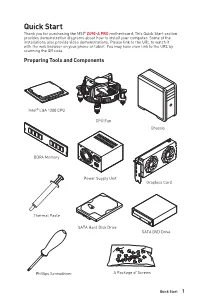
Quick Start Section Provides Demonstration Diagrams About How to Install Your Computer
ThankQuick you for Start purchasing the MSI® Z490-A PRO motherboard. This Quick Start section provides demonstration diagrams about how to install your computer. Some of the installations also provide video demonstrations. Please link to the URL to watch it with the web browser on your phone or tablet. You may have even link to the URL by scanning the QR code. Preparing Tools and Components Intel® LGA 1200 CPU CPU Fan Chassis DDR4 Memory Power Supply Unit Graphics Card Thermal Paste SATA Hard Disk Drive SATA DVD Drive Phillips Screwdriver A Package of Screws Quick Start 1 Safety Information ∙ The components included in this package are prone to damage from electrostatic discharge (ESD). Please adhere to the following instructions to ensure successful computer assembly. ∙ Ensure that all components are securely connected. Loose connections may cause the computer to not recognize a component or fail to start. ∙ Hold the motherboard by the edges to avoid touching sensitive components. ∙ It is recommended to wear an electrostatic discharge (ESD) wrist strap when handling the motherboard to prevent electrostatic damage. If an ESD wrist strap is not available, discharge yourself of static electricity by touching another metal object before handling the motherboard. ∙ Store the motherboard in an electrostatic shielding container or on an anti-static pad whenever the motherboard is not installed. ∙ Before turning on the computer, ensure that there are no loose screws or metal components on the motherboard or anywhere within the computer case. ∙ Do not boot the computer before installation is completed. This could cause permanent damage to the components as well as injury to the user.