Two-Tier Signatures, Strongly Unforgeable Signatures, and Fiat-Shamir Without Random Oracles
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Mihir Bellare Curriculum Vitae Contents
Mihir Bellare Curriculum vitae August 2018 Department of Computer Science & Engineering, Mail Code 0404 University of California at San Diego 9500 Gilman Drive, La Jolla, CA 92093-0404, USA. Phone: (858) 534-4544 ; E-mail: [email protected] Web Page: http://cseweb.ucsd.edu/~mihir Contents 1 Research areas 2 2 Education 2 3 Distinctions and Awards 2 4 Impact 3 5 Grants 4 6 Professional Activities 5 7 Industrial relations 5 8 Work Experience 5 9 Teaching 6 10 Publications 6 11 Mentoring 19 12 Personal Information 21 2 1 Research areas ∗ Cryptography and security: Provable security; authentication; key distribution; signatures; encryp- tion; protocols. ∗ Complexity theory: Interactive and probabilistically checkable proofs; approximability ; complexity of zero-knowledge; randomness in protocols and algorithms; computational learning theory. 2 Education ∗ Massachusetts Institute of Technology. Ph.D in Computer Science, September 1991. Thesis title: Randomness in Interactive Proofs. Thesis supervisor: Prof. S. Micali. ∗ Massachusetts Institute of Technology. Masters in Computer Science, September 1988. Thesis title: A Signature Scheme Based on Trapdoor Permutations. Thesis supervisor: Prof. S. Micali. ∗ California Institute of Technology. B.S. with honors, June 1986. Subject: Mathematics. GPA 4.0. Class rank 4 out of 227. Summer Undergraduate Research Fellow 1984 and 1985. ∗ Ecole Active Bilingue, Paris, France. Baccalauréat Série C, June 1981. 3 Distinctions and Awards ∗ PET (Privacy Enhancing Technologies) Award 2015 for publication [154]. ∗ Fellow of the ACM (Association for Computing Machinery), 2014. ∗ ACM Paris Kanellakis Theory and Practice Award 2009. ∗ RSA Conference Award in Mathematics, 2003. ∗ David and Lucille Packard Foundation Fellowship in Science and Engineering, 1996. (Twenty awarded annually in all of Science and Engineering.) ∗ Test of Time Award, ACM CCS 2011, given for [81] as best paper from ten years prior. -

Design and Analysis of Secure Encryption Schemes
UNIVERSITY OF CALIFORNIA, SAN DIEGO Design and Analysis of Secure Encryption Schemes A dissertation submitted in partial satisfaction of the requirements for the degree Doctor of Philosophy in Computer Science by Michel Ferreira Abdalla Committee in charge: Professor Mihir Bellare, Chairperson Professor Yeshaiahu Fainman Professor Adriano Garsia Professor Mohan Paturi Professor Bennet Yee 2001 Copyright Michel Ferreira Abdalla, 2001 All rights reserved. The dissertation of Michel Ferreira Abdalla is approved, and it is acceptable in quality and form for publication on micro¯lm: Chair University of California, San Diego 2001 iii DEDICATION To my father (in memorian) iv TABLE OF CONTENTS Signature Page . iii Dedication . iv Table of Contents . v List of Figures . vii List of Tables . ix Acknowledgements . x Vita and Publications . xii Fields of Study . xiii Abstract . xiv I Introduction . 1 A. Encryption . 1 1. Background . 2 2. Perfect Privacy . 3 3. Modern cryptography . 4 4. Public-key Encryption . 5 5. Broadcast Encryption . 5 6. Provable Security . 6 7. Concrete Security . 7 B. Contributions . 8 II E±cient public-key encryption schemes . 11 A. Introduction . 12 B. De¯nitions . 17 1. Represented groups . 17 2. Message Authentication Codes . 17 3. Symmetric Encryption . 19 4. Asymmetric Encryption . 21 C. The Scheme DHIES . 23 D. Attributes and Advantages of DHIES . 24 1. Encrypting with Di±e-Hellman: The ElGamal Scheme . 25 2. De¯ciencies of ElGamal Encryption . 26 3. Overcoming De¯ciencies in ElGamal Encryption: DHIES . 29 E. Di±e-Hellman Assumptions . 31 F. Security against Chosen-Plaintext Attack . 38 v G. Security against Chosen-Ciphertext Attack . 41 H. ODH and SDH . -

ACM Honors Eminent Researchers for Technical Innovations That Have Improved How We Live and Work 2016 Recipients Made Contribu
Contact: Jim Ormond 212-626-0505 [email protected] ACM Honors Eminent Researchers for Technical Innovations That Have Improved How We Live and Work 2016 Recipients Made Contributions in Areas Including Big Data Analysis, Computer Vision, and Encryption NEW YORK, NY, May 3, 2017 – ACM, the Association for Computing Machinery (www.acm.org), today announced the recipients of four prestigious technical awards. These leaders were selected by their peers for making significant contributions that have had far-reaching impact on how we live and work. The awards reflect achievements in file sharing, broadcast encryption, information visualization and computer vision. The 2016 recipients will be formally honored at the ACM Awards Banquet on June 24 in San Francisco. The 2016 Award Recipients include: • Mahadev Satyanarayanan, Michael L. Kazar, Robert N. Sidebotham, David A. Nichols, Michael J. West, John H. Howard, Alfred Z. Spector and Sherri M. Nichols, recipients of the ACM Software System Award for developing the Andrew File System (AFS). AFS was the first distributed file system designed for tens of thousands of machines, and pioneered the use of scalable, secure and ubiquitous access to shared file data. To achieve the goal of providing a common shared file system used by large networks of people, AFS introduced novel approaches to caching, security, management and administration. AFS is still in use today as both an open source system and as the file system in commercial applications. It has also inspired several cloud-based storage applications. The 2016 Software System Award recipients designed and built the Andrew File System in the 1980s while working as a team at the Information Technology Center (ITC), a partnership between Carnegie Mellon University and IBM. -

Compact E-Cash and Simulatable Vrfs Revisited
Compact E-Cash and Simulatable VRFs Revisited Mira Belenkiy1, Melissa Chase2, Markulf Kohlweiss3, and Anna Lysyanskaya4 1 Microsoft, [email protected] 2 Microsoft Research, [email protected] 3 KU Leuven, ESAT-COSIC / IBBT, [email protected] 4 Brown University, [email protected] Abstract. Efficient non-interactive zero-knowledge proofs are a powerful tool for solving many cryptographic problems. We apply the recent Groth-Sahai (GS) proof system for pairing product equations (Eurocrypt 2008) to two related cryptographic problems: compact e-cash (Eurocrypt 2005) and simulatable verifiable random functions (CRYPTO 2007). We present the first efficient compact e-cash scheme that does not rely on a ran- dom oracle. To this end we construct efficient GS proofs for signature possession, pseudo randomness and set membership. The GS proofs for pseudorandom functions give rise to a much cleaner and substantially faster construction of simulatable verifiable random functions (sVRF) under a weaker number theoretic assumption. We obtain the first efficient fully simulatable sVRF with a polynomial sized output domain (in the security parameter). 1 Introduction Since their invention [BFM88] non-interactive zero-knowledge proofs played an important role in ob- taining feasibility results for many interesting cryptographic primitives [BG90,GO92,Sah99], such as the first chosen ciphertext secure public key encryption scheme [BFM88,RS92,DDN91]. The inefficiency of these constructions often motivated independent practical instantiations that were arguably conceptually less elegant, but much more efficient ([CS98] for chosen ciphertext security). We revisit two important cryptographic results of pairing-based cryptography, compact e-cash [CHL05] and simulatable verifiable random functions [CL07], that have very elegant constructions based on non-interactive zero-knowledge proof systems, but less elegant practical instantiations. -

Transferable Constant-Size Fair E-Cash
Transferable Constant-Size Fair E-Cash Georg Fuchsbauer, David Pointcheval, and Damien Vergnaud Ecole´ normale sup´erieure,LIENS - CNRS - INRIA, Paris, France http://www.di.ens.fr/f~fuchsbau,~pointche,~vergnaudg Abstract. We propose an efficient blind certification protocol with interesting properties. It falls in the Groth-Sahai framework for witness-indistinguishable proofs, thus extended to a certified signature it immediately yields non-frameable group signatures. We use blind certification to build an efficient (offline) e-cash system that guarantees user anonymity and transferability of coins without increasing their size. As required for fair e-cash, in case of fraud, anonymity can be revoked by an authority, which is also crucial to deter from double spending. 1 Introduction 1.1 Motivation The issue of anonymity in electronic transactions was introduced for e-cash and e-mail in the early 1980's by Chaum, with the famous primitive of blind signatures [Cha83,Cha84]: a signer accepts to sign a message, without knowing the message itself, and without being able to later link a message- signature pair to the transaction it originated from. In e-cash systems, the message is a serial number to make a coin unique. The main security property is resistance to \one-more forgeries" [PS00], which guarantees the signer that after t transactions a user cannot have more than t valid signatures. Blind signatures have thereafter been widely used for many variants of e-cash systems; in particular fair blind signatures [SPC95], which allow to provide revocable anonymity. They deter from abuse since in such a case the signer can ask an authority to reveal the identity of the defrauder. -

Data Structures Meet Cryptography: 3SUM with Preprocessing
Data Structures Meet Cryptography: 3SUM with Preprocessing Alexander Golovnev Siyao Guo Thibaut Horel Harvard NYU Shanghai MIT [email protected] [email protected] [email protected] Sunoo Park Vinod Vaikuntanathan MIT & Harvard MIT [email protected] [email protected] Abstract This paper shows several connections between data structure problems and cryptography against preprocessing attacks. Our results span data structure upper bounds, cryptographic applications, and data structure lower bounds, as summarized next. First, we apply Fiat–Naor inversion, a technique with cryptographic origins, to obtain a data structure upper bound. In particular, our technique yields a suite of algorithms with space S and (online) time T for a preprocessing version of the N-input 3SUM problem where S3 T = O(N 6). This disproves a strong conjecture (Goldstein et al., WADS 2017) that there is no data· structure − − that solves this problem for S = N 2 δ and T = N 1 δ for any constant δ > 0. e Secondly, we show equivalence between lower bounds for a broad class of (static) data struc- ture problems and one-way functions in the random oracle model that resist a very strong form of preprocessing attack. Concretely, given a random function F :[N] [N] (accessed as an oracle) we show how to compile it into a function GF :[N 2] [N 2] which→ resists S-bit prepro- cessing attacks that run in query time T where ST = O(N 2−→ε) (assuming a corresponding data structure lower bound on 3SUM). In contrast, a classical result of Hellman tells us that F itself can be more easily inverted, say with N 2/3-bit preprocessing in N 2/3 time. -
Proving Tight Security for Rabin/Williams Signatures
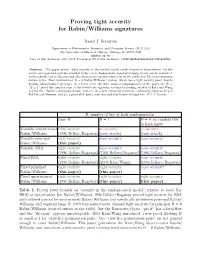
Proving tight security for Rabin/Williams signatures Daniel J. Bernstein Department of Mathematics, Statistics, and Computer Science (M/C 249) The University of Illinois at Chicago, Chicago, IL 60607–7045 [email protected] Date of this document: 2007.10.07. Permanent ID of this document: c30057d690a8fb42af6a5172b5da9006. Abstract. This paper proves “tight security in the random-oracle model relative to factorization” for the lowest-cost signature systems available today: every hash-generic signature-forging attack can be converted, with negligible loss of efficiency and effectiveness, into an algorithm to factor the public key. The most surprising system is the “fixed unstructured B = 0 Rabin/Williams” system, which has a tight security proof despite hashing unrandomized messages. At a lower level, the three main accomplishments of the paper are (1) a “B ≥ 1” proof that handles some of the lowest-cost signature systems by pushing an idea of Katz and Wang beyond the “claw-free permutation pair” context; (2) a new expository structure, elaborating upon an idea of Koblitz and Menezes; and (3) a proof that uses a new idea and that breaks through the “B ≥ 1” barrier. B, number of bits of hash randomization large B B = 1 B = 0: no random bits in hash input Variable unstructured tight security no security no security Rabin/Williams (1996 Bellare/Rogaway) (easy attack) (easy attack) Variable principal tight security loose security loose security∗ Rabin/Williams (this paper) Variable RSA tight security loose security loose security (1996 Bellare/Rogaway) (1993 Bellare/Rogaway) (1993 Bellare/Rogaway) Fixed RSA tight security tight security loose security (1996 Bellare/Rogaway) (2003 Katz/Wang) (1993 Bellare/Rogaway) Fixed principal tight security tight security loose security∗ Rabin/Williams (this paper) (this paper) Fixed unstructured tight security tight security tight security Rabin/Williams (1996 Bellare/Rogaway) (this paper) (this paper) Table 1. -

Implementation of Secure Image Transferring by Using Rsa and Sha-1
© IJCIRAS | ISSN (O) - 2581-5334 April 2020 | Vol. 2 Issue. 11 IMPLEMENTATION OF SECURE IMAGE TRANSFERRING BY USING RSA AND SHA-1 Khet Khet Khaing Oo1, Yan Naung Soe2 Faculty of Computer System and Technologies, University of Computer Studies, Myitkyina and 1011, Myanmar encryption. A public key which encrypted data only be Abstract decrypted key but it requires a private key which is Nowadays, security is an important thing that needs associated together. It must be careful that the to transfer data from admin to user safely. encrypted public key and decrypted public key must not Communication security requires the integration of be the same. people, process, and technology. There are so many different techniques should be used to safe 2.PUBLIC KEY CRYPTOSYSTEM confidential image data from unauthorized access. Information security is becoming more in data RSA cryptosystem was invented by Ron Rivest, Adi storage and transmission from data exchange in Shamir, and Leonard Adleman at MIT in 1978. [4,6] RSA electronic way. Industrial process is used to images, (Rivest–Shamir–Adleman) algorithm is a public-key this is useful to protect the secure image data files cryptography system. These algorithm is profoundly from unauthorized access. To implement this system used in electronic commerce protocols, and is confided RSA ( Rivest Shamir Adelman) public key to be secure given enough long keys and the use of up- cryptography with OAEP (Optimal Asymmetric to-date implementations. They went on to patent the Encryption Padding ) and SHA-1 hash algorithms are system and to form a company of the same name— used. -

Design Principles and Patterns for Computer Systems That Are
Bibliography [AB04] Tom Anderson and David Brady. Principle of least astonishment. Ore- gon Pattern Repository, November 15 2004. http://c2.com/cgi/wiki? PrincipleOfLeastAstonishment. [Acc05] Access Data. Forensic toolkit—overview, 2005. http://www.accessdata. com/Product04_Overview.htm?ProductNum=04. [Adv87] Display ad 57, February 8 1987. [Age05] US Environmental Protection Agency. Wastes: The hazardous waste mani- fest system, 2005. http://www.epa.gov/epaoswer/hazwaste/gener/ manifest/. [AHR05a] Ben Adida, Susan Hohenberger, and Ronald L. Rivest. Fighting Phishing Attacks: A Lightweight Trust Architecture for Detecting Spoofed Emails (to appear), 2005. Available at http://theory.lcs.mit.edu/⇠rivest/ publications.html. [AHR05b] Ben Adida, Susan Hohenberger, and Ronald L. Rivest. Separable Identity- Based Ring Signatures: Theoretical Foundations For Fighting Phishing Attacks (to appear), 2005. Available at http://theory.lcs.mit.edu/⇠rivest/ publications.html. [AIS77] Christopher Alexander, Sara Ishikawa, and Murray Silverstein. A Pattern Lan- guage: towns, buildings, construction. Oxford University Press, 1977. (with Max Jacobson, Ingrid Fiksdahl-King and Shlomo Angel). [AKM+93] H. Alvestrand, S. Kille, R. Miles, M. Rose, and S. Thompson. RFC 1495: Map- ping between X.400 and RFC-822 message bodies, August 1993. Obsoleted by RFC2156 [Kil98]. Obsoletes RFC987, RFC1026, RFC1138, RFC1148, RFC1327 [Kil86, Kil87, Kil89, Kil90, HK92]. Status: PROPOSED STANDARD. [Ale79] Christopher Alexander. The Timeless Way of Building. Oxford University Press, 1979. 429 430 BIBLIOGRAPHY [Ale96] Christopher Alexander. Patterns in architecture [videorecording], October 8 1996. Recorded at OOPSLA 1996, San Jose, California. [Alt00] Steven Alter. Same words, different meanings: are basic IS/IT concepts our self-imposed Tower of Babel? Commun. AIS, 3(3es):2, 2000. -

Human Identity and the Quest to Replace Passwords Continued
Human identity and the quest to replace passwords continued Sirvan Almasi William J.Knottenbelt Department of Computing Department of Computing Imperial College London Imperial College London London, UK London, UK [email protected] [email protected] Abstract—Identification and authentication are vital Blockchain is proving to have many more important ap- components of many online services. For authentica- plications beyond its primary conceived application of tion, password has remained the most practical solution digital cash (Bitcoin [3] since 2009). Using it as a public- despite it being a weak form of security; whilst public- key cryptography is more secure, developing a practical key infrastructure (PKI) and identity management is two system has been an impediment to its adoption. For important examples that have tremendous implications for identification there is a lack of widely adopted protocol web applications. The likes of Namecoin [4], Blockstack [5] that isn’t dependent on trusted third parties or a and Certcoin [6] are examples of organisations attempting centralised public-key infrastructure. The Fiat–Shamir to recreate DNS, identity and certification services using identification scheme solved this issue but by assuming there was a single identity issuer to begin with, whilst blockchain. Other examples that have used the blockchain in reality you would have multiple identity issuers. as a PKI include [7] for IoT devices and [8] for identity Here we introduce deeID, a blockchain-based public- management. key infrastructure that enables multiple Fiat–Shamir The role and security of our identity in the digital identity issuers for identification. At the same time the ecosystem has taken a centre stage as the significance system is used for authentication that enables better than password security whilst remaining practical. -

Practical Divisible E-Cash
Practical Divisible E-Cash Patrick Märtens Mathematisches Institut, Justus-Liebig-Universität Gießen [email protected] April 9, 2015 Abstract. Divisible e-cash systems allow a user to withdraw a wallet containing K coins and to spend k ≤ K coins in a single operation, respectively. Independent of the new work of Canard, Pointcheval, Sanders and Traoré (Proceedings of PKC ’15) we present a practical and secure divisible e-cash system in which the bandwidth of each protocol is constant while the system fulfills the standard security requirements (especially which is unforgeable and truly anonymous) in the random oracle model. In other existing divisible e-cash systems that are truly anonymous, either the bandwidth of withdrawing depends on K or the bandwidth of spending depends on k. Moreover, using some techniques of the work of Canard, Pointcheval, Sanders and Traoré we are also able to prove the security in the standard model. Furthermore, we show an efficient attack against the unforgeability of Canard and Gouget’s divisible e-cash scheme (FC ’10). Finally, we extend our scheme to a divisible e-cash system that provides withdrawing and spending of an arbitrary value of coins (not necessarily a power of two) and give an extension to a fair e-cash scheme. Keywords: E-Cash, divisible, constant-size, accumulator, pairings, standard model 1 Introduction Electronic cash (e-cash) was introduced by Chaum [Cha83] as the digital analogue of regular money. Basically, an (offline) e-cash system consists of three parties (the bank B, user U, and merchant M) and three protocols (Withdrawal, Spend, and Deposit). -

Deterministic Massively Parallel Connectivity
Deterministic Massively Parallel Connectivity∗ Sam Coy Artur Czumaj Department of Computer Science Centre for Discrete Mathematics and its Applications University of Warwick August 10, 2021 Abstract We consider the problem of designing fundamental graph algorithms on the model of Massive Parallel Computation (MPC). The input to the problem is an undirected graph G with n vertices and m edges, and with D being the maximum diameter of any connected component in G. We consider the MPC with low local space, allowing each machine to store only Θ(nδ) words for an arbitrarily constant δ > 0, and with linear global space (which is equal to the number of machines times the local space available), that is, with optimal utilization. In a recent breakthrough, Andoni et al. (FOCS’18) and Behnezhad et al. (FOCS’19) designed parallel randomized algorithms that in O(log D + log log n) rounds on an MPC with low local space determine all connected components of an input graph, improving upon the classic bound of O(log n) derived from earlier works on PRAM algorithms. In this paper, we show that asymptotically identical bounds can be also achieved for de- terministic algorithms: we present a deterministic MPC low local space algorithm that in O(log D + log log n) rounds determines all connected components of the input graph. arXiv:2108.04102v1 [cs.DS] 9 Aug 2021 ∗Research supported in part by the Centre for Discrete Mathematics and its Applications (DIMAP), by EPSRC award EP/V01305X/1, by an EPSRC studentship, by a Weizmann-UK Making Connections Grant, and by an IBM Award.