Mcoe: a Family of Almost Foolproof On-Line Authenticated Encryption Schemes
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Mihir Bellare Curriculum Vitae Contents
Mihir Bellare Curriculum vitae August 2018 Department of Computer Science & Engineering, Mail Code 0404 University of California at San Diego 9500 Gilman Drive, La Jolla, CA 92093-0404, USA. Phone: (858) 534-4544 ; E-mail: [email protected] Web Page: http://cseweb.ucsd.edu/~mihir Contents 1 Research areas 2 2 Education 2 3 Distinctions and Awards 2 4 Impact 3 5 Grants 4 6 Professional Activities 5 7 Industrial relations 5 8 Work Experience 5 9 Teaching 6 10 Publications 6 11 Mentoring 19 12 Personal Information 21 2 1 Research areas ∗ Cryptography and security: Provable security; authentication; key distribution; signatures; encryp- tion; protocols. ∗ Complexity theory: Interactive and probabilistically checkable proofs; approximability ; complexity of zero-knowledge; randomness in protocols and algorithms; computational learning theory. 2 Education ∗ Massachusetts Institute of Technology. Ph.D in Computer Science, September 1991. Thesis title: Randomness in Interactive Proofs. Thesis supervisor: Prof. S. Micali. ∗ Massachusetts Institute of Technology. Masters in Computer Science, September 1988. Thesis title: A Signature Scheme Based on Trapdoor Permutations. Thesis supervisor: Prof. S. Micali. ∗ California Institute of Technology. B.S. with honors, June 1986. Subject: Mathematics. GPA 4.0. Class rank 4 out of 227. Summer Undergraduate Research Fellow 1984 and 1985. ∗ Ecole Active Bilingue, Paris, France. Baccalauréat Série C, June 1981. 3 Distinctions and Awards ∗ PET (Privacy Enhancing Technologies) Award 2015 for publication [154]. ∗ Fellow of the ACM (Association for Computing Machinery), 2014. ∗ ACM Paris Kanellakis Theory and Practice Award 2009. ∗ RSA Conference Award in Mathematics, 2003. ∗ David and Lucille Packard Foundation Fellowship in Science and Engineering, 1996. (Twenty awarded annually in all of Science and Engineering.) ∗ Test of Time Award, ACM CCS 2011, given for [81] as best paper from ten years prior. -

Design and Analysis of Secure Encryption Schemes
UNIVERSITY OF CALIFORNIA, SAN DIEGO Design and Analysis of Secure Encryption Schemes A dissertation submitted in partial satisfaction of the requirements for the degree Doctor of Philosophy in Computer Science by Michel Ferreira Abdalla Committee in charge: Professor Mihir Bellare, Chairperson Professor Yeshaiahu Fainman Professor Adriano Garsia Professor Mohan Paturi Professor Bennet Yee 2001 Copyright Michel Ferreira Abdalla, 2001 All rights reserved. The dissertation of Michel Ferreira Abdalla is approved, and it is acceptable in quality and form for publication on micro¯lm: Chair University of California, San Diego 2001 iii DEDICATION To my father (in memorian) iv TABLE OF CONTENTS Signature Page . iii Dedication . iv Table of Contents . v List of Figures . vii List of Tables . ix Acknowledgements . x Vita and Publications . xii Fields of Study . xiii Abstract . xiv I Introduction . 1 A. Encryption . 1 1. Background . 2 2. Perfect Privacy . 3 3. Modern cryptography . 4 4. Public-key Encryption . 5 5. Broadcast Encryption . 5 6. Provable Security . 6 7. Concrete Security . 7 B. Contributions . 8 II E±cient public-key encryption schemes . 11 A. Introduction . 12 B. De¯nitions . 17 1. Represented groups . 17 2. Message Authentication Codes . 17 3. Symmetric Encryption . 19 4. Asymmetric Encryption . 21 C. The Scheme DHIES . 23 D. Attributes and Advantages of DHIES . 24 1. Encrypting with Di±e-Hellman: The ElGamal Scheme . 25 2. De¯ciencies of ElGamal Encryption . 26 3. Overcoming De¯ciencies in ElGamal Encryption: DHIES . 29 E. Di±e-Hellman Assumptions . 31 F. Security against Chosen-Plaintext Attack . 38 v G. Security against Chosen-Ciphertext Attack . 41 H. ODH and SDH . -

IMPLEMENTATION and BENCHMARKING of PADDING UNITS and HMAC for SHA-3 CANDIDATES in FPGAS and ASICS by Ambarish Vyas a Thesis Subm
IMPLEMENTATION AND BENCHMARKING OF PADDING UNITS AND HMAC FOR SHA-3 CANDIDATES IN FPGAS AND ASICS by Ambarish Vyas A Thesis Submitted to the Graduate Faculty of George Mason University in Partial Fulfillment of The Requirements for the Degree of Master of Science Computer Engineering Committee: Dr. Kris Gaj, Thesis Director Dr. Jens-Peter Kaps. Committee Member Dr. Bernd-Peter Paris. Committee Member Dr. Andre Manitius, Department Chair of Electrical and Computer Engineering Dr. Lloyd J. Griffiths. Dean, Volgenau School of Engineering Date: ---J d. / q /9- 0 II Fall Semester 2011 George Mason University Fairfax, VA Implementation and Benchmarking of Padding Units and HMAC for SHA-3 Candidates in FPGAs and ASICs A thesis submitted in partial fulfillment of the requirements for the degree of Master of Science at George Mason University By Ambarish Vyas Bachelor of Science University of Pune, 2009 Director: Dr. Kris Gaj, Associate Professor Department of Electrical and Computer Engineering Fall Semester 2011 George Mason University Fairfax, VA Copyright c 2011 by Ambarish Vyas All Rights Reserved ii Acknowledgments I would like to use this oppurtunity to thank the people who have supported me throughout my thesis. First and foremost my advisor Dr.Kris Gaj, without his zeal, his motivation, his patience, his confidence in me, his humility, his diverse knowledge, and his great efforts this thesis wouldn't be possible. It is difficult to exaggerate my gratitude towards him. I also thank Ekawat Homsirikamol for his contributions to this project. He has significantly contributed to the designs and implementations of the architectures. Additionally, I am indebted to my student colleagues in CERG for providing a fun environment to learn and giving invaluable tips and support. -

Compact E-Cash and Simulatable Vrfs Revisited
Compact E-Cash and Simulatable VRFs Revisited Mira Belenkiy1, Melissa Chase2, Markulf Kohlweiss3, and Anna Lysyanskaya4 1 Microsoft, [email protected] 2 Microsoft Research, [email protected] 3 KU Leuven, ESAT-COSIC / IBBT, [email protected] 4 Brown University, [email protected] Abstract. Efficient non-interactive zero-knowledge proofs are a powerful tool for solving many cryptographic problems. We apply the recent Groth-Sahai (GS) proof system for pairing product equations (Eurocrypt 2008) to two related cryptographic problems: compact e-cash (Eurocrypt 2005) and simulatable verifiable random functions (CRYPTO 2007). We present the first efficient compact e-cash scheme that does not rely on a ran- dom oracle. To this end we construct efficient GS proofs for signature possession, pseudo randomness and set membership. The GS proofs for pseudorandom functions give rise to a much cleaner and substantially faster construction of simulatable verifiable random functions (sVRF) under a weaker number theoretic assumption. We obtain the first efficient fully simulatable sVRF with a polynomial sized output domain (in the security parameter). 1 Introduction Since their invention [BFM88] non-interactive zero-knowledge proofs played an important role in ob- taining feasibility results for many interesting cryptographic primitives [BG90,GO92,Sah99], such as the first chosen ciphertext secure public key encryption scheme [BFM88,RS92,DDN91]. The inefficiency of these constructions often motivated independent practical instantiations that were arguably conceptually less elegant, but much more efficient ([CS98] for chosen ciphertext security). We revisit two important cryptographic results of pairing-based cryptography, compact e-cash [CHL05] and simulatable verifiable random functions [CL07], that have very elegant constructions based on non-interactive zero-knowledge proof systems, but less elegant practical instantiations. -

The Boomerang Attacks on the Round-Reduced Skein-512 *
The Boomerang Attacks on the Round-Reduced Skein-512 ? Hongbo Yu1, Jiazhe Chen3, and Xiaoyun Wang2;3 1 Department of Computer Science and Technology, Tsinghua University, Beijing 100084, China 2 Institute for Advanced Study, Tsinghua University, Beijing 100084, China fyuhongbo,[email protected] 3 Key Laboratory of Cryptologic Technology and Information Security, Ministry of Education, School of Mathematics, Shandong University, Jinan 250100, China [email protected] Abstract. The hash function Skein is one of the ¯ve ¯nalists of the NIST SHA-3 competition; it is based on the block cipher Three¯sh which only uses three primitive operations: modular addition, rotation and bitwise XOR (ARX). This paper studies the boomerang attacks on Skein-512. Boomerang distinguishers on the compression function reduced to 32 and 36 rounds are proposed, with complexities 2104:5 and 2454 respectively. Examples of the distinguishers on 28-round and 31- round are also given. In addition, the boomerang distinguishers are applicable to the key-recovery attacks on reduced Three¯sh-512. The complexities for key-recovery attacks reduced to 32-/33- /34-round are about 2181, 2305 and 2424. Because Laurent et al. [14] pointed out that the previous boomerang distinguishers for Three¯sh-512 are in fact not compatible, our attacks are the ¯rst valid boomerang attacks for the ¯nal round Skein-512. Key words: Hash function, Boomerang attack, Three¯sh, Skein 1 Introduction Cryptographic hash functions, which provide integrity, authentication and etc., are very impor- tant in modern cryptology. In 2005, as the most widely used hash functions MD5 and SHA-1 were broken by Wang et al. -

An Analytic Attack Against ARX Addition Exploiting Standard Side-Channel Leakage
An Analytic Attack Against ARX Addition Exploiting Standard Side-Channel Leakage Yan Yan1, Elisabeth Oswald1 and Srinivas Vivek2 1University of Klagenfurt, Klagenfurt, Austria 2IIIT Bangalore, India fyan.yan, [email protected], [email protected] Keywords: ARX construction, Side-channel analysis, Hamming weight, Chosen plaintext attack Abstract: In the last few years a new design paradigm, the so-called ARX (modular addition, rotation, exclusive-or) ciphers, have gained popularity in part because of their non-linear operation’s seemingly ‘inherent resilience’ against Differential Power Analysis (DPA) Attacks: the non-linear modular addition is not only known to be a poor target for DPA attacks, but also the computational complexity of DPA-style attacks grows exponentially with the operand size and thus DPA-style attacks quickly become practically infeasible. We however propose a novel DPA-style attack strategy that scales linearly with respect to the operand size in the chosen-message attack setting. 1 Introduction ever are different: they offer a potentially ‘high reso- lution’ for the adversary. In principle, under suitably Ciphers that base their round function on the sim- strong assumptions, adversaries can not only observe ple combination of modular addition, rotation, and leaks for all instructions that are executed on a proces- exclusive-or, (short ARX) have gained recent popu- sor, but indeed attribute leakage points (more or less larity for their lightweight implementations that are accurately) to instructions (Mangard et al., 2007). suitable for resource constrained devices. Some re- Achieving security in this scenario has proven to cent examples include Chacha20 (Nir and Langley, be extremely challenging, and countermeasures such 2015) and Salsa20 (Bernstein, 2008) family stream as masking (secret sharing) are well understood but ciphers, SHA-3 finalists BLAKE (Aumasson et al., costly (Schneider et al., 2015). -

SHA-3 Conference, March 2012, Skein: More Than Just a Hash Function
Skein More than just a hash function Third SHA-3 Candidate Conference 23 March 2012 Washington DC 1 Skein is Skein-512 • Confusion is common, partially our fault • Skein has two special-purpose siblings: – Skein-256 for extreme memory constraints – Skein-1024 for the ultra-high security margin • But for SHA-3, Skein is Skein-512 – One hash function for all output sizes 2 Skein Architecture • Mix function is 64-bit ARX • Permutation: relocation of eight 64-bit words • Threefish: tweakable block cipher – Mix + Permutation – Simple key schedule – 72 rounds, subkey injection every four rounds – Tweakable-cipher design key to speed, security • Skein chains Threefish with UBI chaining mode – Tweakable mode based on MMO – Provable properties – Every hashed block is unique • Variable size output means flexible to use! – One function for any size output 3 The Skein/Threefish Mix 4 Four Threefish Rounds 5 Skein and UBI chaining 6 Fastest in Software • 5.5 cycles/byte on 64-bit reference platform • 17.4 cycles/byte on 32-bit reference platform • 4.7 cycles/byte on Itanium • 15.2 cycles/byte on ARM Cortex A8 (ARMv7) – New numbers, best finalist on ARMv7 (iOS, Samsung, etc.) 7 Fast and Compact in Hardware • Fast – Skein-512 at 32 Gbit/s in 32 nm in 58 k gates – (57 Gbit/s if processing two messages in parallel) • To maximize hardware performance: – Use a fast adder, rely on simple control structure, and exploit Threefish's opportunities for pipelining – Do not trust your EDA tool to generate an efficient implementation • Compact design: – Small FPGA -

Security Policy: Informacast Java Crypto Library
FIPS 140-2 Non-Proprietary Security Policy: InformaCast Java Crypto Library FIPS 140-2 Non-Proprietary Security Policy InformaCast Java Crypto Library Software Version 3.0 Document Version 1.2 June 26, 2017 Prepared For: Prepared By: Singlewire Software SafeLogic Inc. 1002 Deming Way 530 Lytton Ave, Suite 200 Madison, WI 53717 Palo Alto, CA 94301 www.singlewire.com www.safelogic.com Document Version 1.2 © Singlewire Software Page 1 of 35 FIPS 140-2 Non-Proprietary Security Policy: InformaCast Java Crypto Library Abstract This document provides a non-proprietary FIPS 140-2 Security Policy for InformaCast Java Crypto Library. Document Version 1.2 © Singlewire Software Page 2 of 35 FIPS 140-2 Non-Proprietary Security Policy: InformaCast Java Crypto Library Table of Contents 1 Introduction .................................................................................................................................................. 5 1.1 About FIPS 140 ............................................................................................................................................. 5 1.2 About this Document.................................................................................................................................... 5 1.3 External Resources ....................................................................................................................................... 5 1.4 Notices ......................................................................................................................................................... -

Authenticated Encryption with Small Stretch (Or, How to Accelerate AERO) ⋆
Authenticated Encryption with Small Stretch (or, How to Accelerate AERO) ? Kazuhiko Minematsu NEC Corporation, Japan [email protected] Abstract. Standard form of authenticated encryption (AE) requires the ciphertext to be expanded by the nonce and the authentication tag. These expansions can be problematic when messages are relatively short and communication cost is high. To overcome the problem we propose a new form of AE scheme, MiniAE, which expands the ciphertext only by the single variable integrating nonce and tag. An important feature of MiniAE is that it requires the receiver to be stateful not only for detecting replays but also for detecting forgery of any type. McGrew and Foley already proposed a scheme having this feature, called AERO, however, there is no formal security guarantee based on the provable security framework. We provide a provable security analysis for MiniAE, and show several provably-secure schemes using standard symmetric crypto primitives. This covers a generalization of AERO, hence our results imply a provable security of AERO. Moreover, one of our schemes has a similar structure as OCB mode of operation and enables rate-1 operation, i.e. only one blockcipher call to process one input block. This implies that the computation cost of MiniAE can be as small as encryption-only schemes. Keywords: Authenticated Encryption, Stateful Decryption, Provable Security, AERO, OCB 1 Introduction Authenticated encryption (AE) is a symmetric-key cryptographic function for communication which provides both confidentiality and integrity of messages. A standard form of AE requires the ciphertext to be expanded by the amount of nonce, a never-repeating value maintained by the sender, and the authentication tag. -

Bicliques for Preimages: Attacks on Skein-512 and the SHA-2 Family
Bicliques for Preimages: Attacks on Skein-512 and the SHA-2 family Dmitry Khovratovich1 and Christian Rechberger2 and Alexandra Savelieva3 1Microsoft Research Redmond, USA 2DTU MAT, Denmark 3National Research University Higher School of Economics, Russia Abstract. We present the new concept of biclique as a tool for preimage attacks, which employs many powerful techniques from differential cryptanalysis of block ciphers and hash functions. The new tool has proved to be widely applicable by inspiring many authors to publish new re- sults of the full versions of AES, KASUMI, IDEA, and Square. In this paper, we demonstrate how our concept results in the first cryptanalysis of the Skein hash function, and describe an attack on the SHA-2 hash function with more rounds than before. Keywords: SHA-2, SHA-256, SHA-512, Skein, SHA-3, hash function, meet-in-the-middle attack, splice-and-cut, preimage attack, initial structure, biclique. 1 Introduction The last years saw an exciting progress in preimage attacks on hash functions. In contrast to collision search [29, 26], where differential cryptanalysis has been in use since 90s, there had been no similarly powerful tool for preimages. The situation changed dramatically in 2008, when the so-called splice-and-cut framework has been applied to MD4 and MD5 [2, 24], and later to SHA-0/1/2 [1, 3], Tiger [10], and other primitives. Despite amazing results on MD5, the applications to SHA-x primitives seemed to be limited by the internal properties of the message schedule procedures. The only promising element, the so-called initial structure tool, remained very informal and complicated. -

Transferable Constant-Size Fair E-Cash
Transferable Constant-Size Fair E-Cash Georg Fuchsbauer, David Pointcheval, and Damien Vergnaud Ecole´ normale sup´erieure,LIENS - CNRS - INRIA, Paris, France http://www.di.ens.fr/f~fuchsbau,~pointche,~vergnaudg Abstract. We propose an efficient blind certification protocol with interesting properties. It falls in the Groth-Sahai framework for witness-indistinguishable proofs, thus extended to a certified signature it immediately yields non-frameable group signatures. We use blind certification to build an efficient (offline) e-cash system that guarantees user anonymity and transferability of coins without increasing their size. As required for fair e-cash, in case of fraud, anonymity can be revoked by an authority, which is also crucial to deter from double spending. 1 Introduction 1.1 Motivation The issue of anonymity in electronic transactions was introduced for e-cash and e-mail in the early 1980's by Chaum, with the famous primitive of blind signatures [Cha83,Cha84]: a signer accepts to sign a message, without knowing the message itself, and without being able to later link a message- signature pair to the transaction it originated from. In e-cash systems, the message is a serial number to make a coin unique. The main security property is resistance to \one-more forgeries" [PS00], which guarantees the signer that after t transactions a user cannot have more than t valid signatures. Blind signatures have thereafter been widely used for many variants of e-cash systems; in particular fair blind signatures [SPC95], which allow to provide revocable anonymity. They deter from abuse since in such a case the signer can ask an authority to reveal the identity of the defrauder. -
Proving Tight Security for Rabin/Williams Signatures
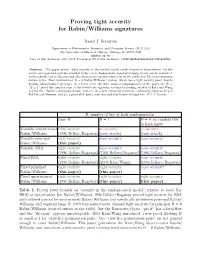
Proving tight security for Rabin/Williams signatures Daniel J. Bernstein Department of Mathematics, Statistics, and Computer Science (M/C 249) The University of Illinois at Chicago, Chicago, IL 60607–7045 [email protected] Date of this document: 2007.10.07. Permanent ID of this document: c30057d690a8fb42af6a5172b5da9006. Abstract. This paper proves “tight security in the random-oracle model relative to factorization” for the lowest-cost signature systems available today: every hash-generic signature-forging attack can be converted, with negligible loss of efficiency and effectiveness, into an algorithm to factor the public key. The most surprising system is the “fixed unstructured B = 0 Rabin/Williams” system, which has a tight security proof despite hashing unrandomized messages. At a lower level, the three main accomplishments of the paper are (1) a “B ≥ 1” proof that handles some of the lowest-cost signature systems by pushing an idea of Katz and Wang beyond the “claw-free permutation pair” context; (2) a new expository structure, elaborating upon an idea of Koblitz and Menezes; and (3) a proof that uses a new idea and that breaks through the “B ≥ 1” barrier. B, number of bits of hash randomization large B B = 1 B = 0: no random bits in hash input Variable unstructured tight security no security no security Rabin/Williams (1996 Bellare/Rogaway) (easy attack) (easy attack) Variable principal tight security loose security loose security∗ Rabin/Williams (this paper) Variable RSA tight security loose security loose security (1996 Bellare/Rogaway) (1993 Bellare/Rogaway) (1993 Bellare/Rogaway) Fixed RSA tight security tight security loose security (1996 Bellare/Rogaway) (2003 Katz/Wang) (1993 Bellare/Rogaway) Fixed principal tight security tight security loose security∗ Rabin/Williams (this paper) (this paper) Fixed unstructured tight security tight security tight security Rabin/Williams (1996 Bellare/Rogaway) (this paper) (this paper) Table 1.