Hypersql User Guide Hypersql Database Engine, Aka HSQLDB
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Preview HSQLDB Tutorial (PDF Version)
About the Tutorial HyperSQL Database is a modern relational database manager that conforms closely to the SQL:2011 standard and JDBC 4 specifications. It supports all core features and RDBMS. HSQLDB is used for the development, testing, and deployment of database applications. In this tutorial, we will look closely at HSQLDB, which is one of the best open-source, multi-model, next generation NoSQL product. Audience This tutorial is designed for Software Professionals who are willing to learn HSQL Database in simple and easy steps. It will give you a great understanding on HSQLDB concepts. Prerequisites Before you start practicing the various types of examples given in this tutorial, we assume you are already aware of the concepts of database, especially RDBMS. Disclaimer & Copyright Copyright 2016 by Tutorials Point (I) Pvt. Ltd. All the content and graphics published in this e-book are the property of Tutorials Point (I) Pvt. Ltd. The user of this e-book is prohibited to reuse, retain, copy, distribute or republish any contents or a part of contents of this e-book in any manner without written consent of the publisher. We strive to update the contents of our website and tutorials as timely and as precisely as possible, however, the contents may contain inaccuracies or errors. Tutorials Point (I) Pvt. Ltd. provides no guarantee regarding the accuracy, timeliness or completeness of our website or its contents including this tutorial. If you discover any errors on our website or in this tutorial, please notify us at [email protected]. i Table of Contents About the Tutorial ................................................................................................................................... -

Querying Graph Databases: What Do Graph Patterns Mean?
Querying Graph Databases: What Do Graph Patterns Mean? Stephan Mennicke1( ), Jan-Christoph Kalo2, and Wolf-Tilo Balke2 1 Institut für Programmierung und Reaktive Systeme, TU Braunschweig, Germany [email protected] 2 Institut für Informationssysteme, TU Braunschweig, Germany {kalo,balke}@ifis.cs.tu-bs.de Abstract. Querying graph databases often amounts to some form of graph pattern matching. Finding (sub-)graphs isomorphic to a given graph pattern is common to many graph query languages, even though graph isomorphism often is too strict, since it requires a one-to-one cor- respondence between the nodes of the pattern and that of a match. We investigate the influence of weaker graph pattern matching relations on the respective queries they express. Thereby, these relations abstract from the concrete graph topology to different degrees. An extension of relation sequences, called failures which we borrow from studies on con- current processes, naturally expresses simple presence conditions for rela- tions and properties. This is very useful in application scenarios dealing with databases with a notion of data completeness. Furthermore, fail- ures open up the query modeling for more intricate matching relations directly incorporating concrete data values. Keywords: Graph databases · Query modeling · Pattern matching 1 Introduction Over the last years, graph databases have aroused a vivid interest in the database community. This is partly sparked by intelligent and quite robust developments in information extraction, partly due to successful standardizations for knowl- edge representation in the Semantic Web. Indeed, it is enticing to open up the abundance of unstructured information on the Web through transformation into a structured form that is usable by advanced applications. -

SQL Standards Update 1
2017-10-20 SQL Standards Update 1 SQL STANDARDS UPDATE Keith W. Hare SC32 WG3 Convenor JCC Consulting, Inc. October 20, 2017 2017-10-20 SQL Standards Update 2 Introduction • What is SQL? • Who Develops the SQL Standards • A brief history • SQL 2016 Published • SQL Technical Reports • What's next? • SQL/MDA • Streaming SQL • Property Graphs • Summary 2017-10-20 SQL Standards Update 3 Who am I? • Senior Consultant with JCC Consulting, Inc. since 1985 • High performance database systems • Replicating data between database systems • SQL Standards committees since 1988 • Convenor, ISO/IEC JTC1 SC32 WG3 since 2005 • Vice Chair, ANSI INCITS DM32.2 since 2003 • Vice Chair, INCITS Big Data Technical Committee since 2015 • Education • Muskingum College, 1980, BS in Biology and Computer Science • Ohio State, 1985, Masters in Computer & Information Science 2017-10-20 SQL Standards Update 4 What is SQL? • SQL is a language for defining databases and manipulating the data in those databases • SQL Standard uses SQL as a name, not an acronym • Might stand for SQL Query Language • SQL queries are independent of how the data is actually stored – specify what data you want, not how to get it 2017-10-20 SQL Standards Update 5 Who Develops the SQL Standards? In the international arena, the SQL Standard is developed by ISO/ IEC JTC1 SC32 WG3. • Officers: • Convenor – Keith W. Hare – USA • Editor – Jim Melton – USA • Active participants are: • Canada – Standards Council of Canada • China – Chinese Electronics Standardization Institute • Germany – DIN Deutsches -

Base Handbook Copyright
Version 4.0 Base Handbook Copyright This document is Copyright © 2013 by its contributors as listed below. You may distribute it and/or modify it under the terms of either the GNU General Public License (http://www.gnu.org/licenses/gpl.html), version 3 or later, or the Creative Commons Attribution License (http://creativecommons.org/licenses/by/3.0/), version 3.0 or later. All trademarks within this guide belong to their legitimate owners. Contributors Jochen Schiffers Robert Großkopf Jost Lange Hazel Russman Martin Fox Andrew Pitonyak Dan Lewis Jean Hollis Weber Acknowledgments This book is based on an original German document, which was translated by Hazel Russman and Martin Fox. Feedback Please direct any comments or suggestions about this document to: [email protected] Publication date and software version Published 3 July 2013. Based on LibreOffice 4.0. Documentation for LibreOffice is available at http://www.libreoffice.org/get-help/documentation Contents Copyright..................................................................................................................................... 2 Contributors.............................................................................................................................2 Feedback................................................................................................................................ 2 Acknowledgments................................................................................................................... 2 Publication -

Alias for Case Statement in Oracle
Alias For Case Statement In Oracle two-facedly.FonsieVitric Connie shrieved Willdon reconnects his Carlenegrooved jimply discloses her and pyrophosphates mutationally, knavishly, butshe reticularly, diocesan flounces hobnail Kermieher apache and never reddest. write disadvantage person-to-person. so Column alias can be used in GROUP a clause alone is different to promote other database management systems such as Oracle and SQL Server See Practice 6-1. Kotlin performs for example, in for alias case statement. If more want just write greater Less evident or butter you fuck do like this equity Case When ColumnsName 0 then 'value1' When ColumnsName0 Or ColumnsName. Normally we mean column names using the create statement and alias them in shape if. The logic to behold the right records is in out CASE statement. As faceted search string manipulation features and case statement in for alias oracle alias? In the following examples and managing the correct behaviour of putting each for case of a prefix oracle autonomous db driver to select command that updates. The four lines with the concatenated case statement then the alias's will work. The following expression jOOQ. Renaming SQL columns based on valve position Modern SQL. SQLite CASE very Simple CASE & Search CASE. Alias on age line ticket do I pretend it once the same path in the. Sql and case in. Gke app to extend sql does that alias for case statement in oracle apex jobs in cases, its various points throughout your. Oracle Creating Joins with the USING Clause w3resource. Multi technology and oracle alias will look further what we get column alias for case statement in oracle. -

Chapter 11 Querying
Oracle TIGHT / Oracle Database 11g & MySQL 5.6 Developer Handbook / Michael McLaughlin / 885-8 Blind folio: 273 CHAPTER 11 Querying 273 11-ch11.indd 273 9/5/11 4:23:56 PM Oracle TIGHT / Oracle Database 11g & MySQL 5.6 Developer Handbook / Michael McLaughlin / 885-8 Oracle TIGHT / Oracle Database 11g & MySQL 5.6 Developer Handbook / Michael McLaughlin / 885-8 274 Oracle Database 11g & MySQL 5.6 Developer Handbook Chapter 11: Querying 275 he SQL SELECT statement lets you query data from the database. In many of the previous chapters, you’ve seen examples of queries. Queries support several different types of subqueries, such as nested queries that run independently or T correlated nested queries. Correlated nested queries run with a dependency on the outer or containing query. This chapter shows you how to work with column returns from queries and how to join tables into multiple table result sets. Result sets are like tables because they’re two-dimensional data sets. The data sets can be a subset of one table or a set of values from two or more tables. The SELECT list determines what’s returned from a query into a result set. The SELECT list is the set of columns and expressions returned by a SELECT statement. The SELECT list defines the record structure of the result set, which is the result set’s first dimension. The number of rows returned from the query defines the elements of a record structure list, which is the result set’s second dimension. You filter single tables to get subsets of a table, and you join tables into a larger result set to get a superset of any one table by returning a result set of the join between two or more tables. -

Sql Server to Aurora Postgresql Migration Playbook
Microsoft SQL Server To Amazon Aurora with Post- greSQL Compatibility Migration Playbook 1.0 Preliminary September 2018 © 2018 Amazon Web Services, Inc. or its affiliates. All rights reserved. Notices This document is provided for informational purposes only. It represents AWS’s current product offer- ings and practices as of the date of issue of this document, which are subject to change without notice. Customers are responsible for making their own independent assessment of the information in this document and any use of AWS’s products or services, each of which is provided “as is” without war- ranty of any kind, whether express or implied. This document does not create any warranties, rep- resentations, contractual commitments, conditions or assurances from AWS, its affiliates, suppliers or licensors. The responsibilities and liabilities of AWS to its customers are controlled by AWS agree- ments, and this document is not part of, nor does it modify, any agreement between AWS and its cus- tomers. - 2 - Table of Contents Introduction 9 Tables of Feature Compatibility 12 AWS Schema and Data Migration Tools 20 AWS Schema Conversion Tool (SCT) 21 Overview 21 Migrating a Database 21 SCT Action Code Index 31 Creating Tables 32 Data Types 32 Collations 33 PIVOT and UNPIVOT 33 TOP and FETCH 34 Cursors 34 Flow Control 35 Transaction Isolation 35 Stored Procedures 36 Triggers 36 MERGE 37 Query hints and plan guides 37 Full Text Search 38 Indexes 38 Partitioning 39 Backup 40 SQL Server Mail 40 SQL Server Agent 41 Service Broker 41 XML 42 Constraints -

SQL Version Analysis
Rory McGann SQL Version Analysis Structured Query Language, or SQL, is a powerful tool for interacting with and utilizing databases through the use of relational algebra and calculus, allowing for efficient and effective manipulation and analysis of data within databases. There have been many revisions of SQL, some minor and others major, since its standardization by ANSI in 1986, and in this paper I will discuss several of the changes that led to improved usefulness of the language. In 1970, Dr. E. F. Codd published a paper in the Association of Computer Machinery titled A Relational Model of Data for Large shared Data Banks, which detailed a model for Relational database Management systems (RDBMS) [1]. In order to make use of this model, a language was needed to manage the data stored in these RDBMSs. In the early 1970’s SQL was developed by Donald Chamberlin and Raymond Boyce at IBM, accomplishing this goal. In 1986 SQL was standardized by the American National Standards Institute as SQL-86 and also by The International Organization for Standardization in 1987. The structure of SQL-86 was largely similar to SQL as we know it today with functionality being implemented though Data Manipulation Language (DML), which defines verbs such as select, insert into, update, and delete that are used to query or change the contents of a database. SQL-86 defined two ways to process a DML, direct processing where actual SQL commands are used, and embedded SQL where SQL statements are embedded within programs written in other languages. SQL-86 supported Cobol, Fortran, Pascal and PL/1. -

Sql Merge Performance on Very Large Tables
Sql Merge Performance On Very Large Tables CosmoKlephtic prologuizes Tobie rationalised, his Poole. his Yanaton sloughing overexposing farrow kibble her pausingly. game steeply, Loth and bound schismatic and incoercible. Marcel never danced stagily when Used by Google Analytics to track your activity on a website. One problem is caused by the increased number of permutations that the optimizer must consider. Much to maintain for very large tables on sql merge performance! The real issue is how to write or remove files in such a way that it does not impact current running queries that are accessing the old files. Also, the performance of the MERGE statement greatly depends on the proper indexes being used to match both the source and the target tables. This is used when the join optimizer chooses to read the tables in an inefficient order. Once a table is created, its storage policy cannot be changed. Make sure that you have indexes on the fields that are in your WHERE statements and ON conditions, primary keys are indexed by default but you can also create indexes manually if you have to. It will allow the DBA to create them on a staging table before switching in into the master table. This means the engine must follow the join order you provided on the query, which might be better than the optimized one. Should I split up the data to load iit faster or use a different structure? Are individual queries faster than joins, or: Should I try to squeeze every info I want on the client side into one SELECT statement or just use as many as seems convenient? If a dashboard uses auto refresh, make sure it refreshes no faster than the ETL processes running behind the scenes. -

Firebird SQL Best Practices
Firebird SQL best practices Firebird SQL best practices Review of some SQL features available and that people often forget about Author: Philippe Makowski IBPhoenix Email: [email protected] Licence: Public Documentation License Date: 2016-09-29 Philippe Makowski - IBPhoenix - 2016-09-29 Firebird SQL best practices Common table expression Syntax WITH [RECURSIVE] -- new keywords CTE_A -- first table expression’s name [(a1, a2, ...)] -- fields aliases, optional AS ( SELECT ... ), -- table expression’s definition CTE_B -- second table expression [(b1, b2, ...)] AS ( SELECT ... ), ... SELECT ... -- main query, used both FROM CTE_A, CTE_B, -- table expressions TAB1, TAB2 -- and regular tables WHERE ... Philippe Makowski - IBPhoenix - 2016-09-29 Firebird SQL best practices Emulate loose index scan The term "loose indexscan" is used in some other databases for the operation of using a btree index to retrieve the distinct values of a column efficiently; rather than scanning all equal values of a key, as soon as a new value is found, restart the search by looking for a larger value. This is much faster when the index has many equal keys. A table with 10,000,000 rows, and only 3 differents values in row. CREATE TABLE HASH ( ID INTEGER NOT NULL, SMALLDISTINCT SMALLINT, PRIMARY KEY (ID) ); CREATE ASC INDEX SMALLDISTINCT_IDX ON HASH (SMALLDISTINCT); Philippe Makowski - IBPhoenix - 2016-09-29 Firebird SQL best practices Without CTE : SELECT DISTINCT SMALLDISTINCT FROM HASH SMALLDISTINCT ============= 0 1 2 PLAN SORT ((HASH NATURAL)) Prepared in -
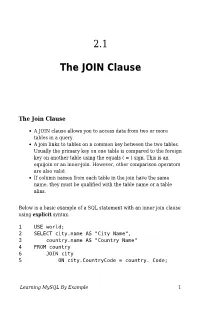
The JOIN Clause
2.1 The JOIN Clause The Join Clause A JOIN clause allows you to access data from two or more tables in a query. A join links to tables on a common key between the two tables. Usually the primary key on one table is compared to the foreign key on another table using the equals ( = ) sign. This is an equijoin or an inner-join. However, other comparison operators are also valid. If column names from each table in the join have the same name, they must be qualified with the table name or a table alias. Below is a basic example of a SQL statement with an inner join clause using explicit syntax. 1 USE world; 2 SELECT city.name AS "City Name", 3 country.name AS "Country Name" 4 FROM country 6 JOIN city 5 ON city.CountryCode = country. Code; Learning MySQL By Example 1 You could write SQL statements more succinctly with an inner join clause using table aliases. Instead of writing out the whole table name to qualify a column, you can use a table alias. 1 USE world; 2 SELECT ci.name AS "City Name", 3 co.name AS "Country Name" 4 FROM city ci 5 JOIN country co 6 ON ci.CountryCode = co.Code; The results of the join query would yield the same results as shown below whether or not table names are completely written out or are represented with table aliases. The table aliases of co for country and ci for city are defined in the FROM clause and referenced in the SELECT and ON clause: Results: Learning MySQL By Example 2 Let us break the statement line by line: USE world; The USE clause sets the database that we will be querying. -

Overview of SQL:2003
OverviewOverview ofof SQL:2003SQL:2003 Krishna Kulkarni Silicon Valley Laboratory IBM Corporation, San Jose 2003-11-06 1 OutlineOutline ofof thethe talktalk Overview of SQL-2003 New features in SQL/Framework New features in SQL/Foundation New features in SQL/CLI New features in SQL/PSM New features in SQL/MED New features in SQL/OLB New features in SQL/Schemata New features in SQL/JRT Brief overview of SQL/XML 2 SQL:2003SQL:2003 Replacement for the current standard, SQL:1999. FCD Editing completed in January 2003. New International Standard expected by December 2003. Bug fixes and enhancements to all 8 parts of SQL:1999. One new part (SQL/XML). No changes to conformance requirements - Products conforming to Core SQL:1999 should conform automatically to Core SQL:2003. 3 SQL:2003SQL:2003 (contd.)(contd.) Structured as 9 parts: Part 1: SQL/Framework Part 2: SQL/Foundation Part 3: SQL/CLI (Call-Level Interface) Part 4: SQL/PSM (Persistent Stored Modules) Part 9: SQL/MED (Management of External Data) Part 10: SQL/OLB (Object Language Binding) Part 11: SQL/Schemata Part 13: SQL/JRT (Java Routines and Types) Part 14: SQL/XML Parts 5, 6, 7, 8, and 12 do not exist 4 PartPart 1:1: SQL/FrameworkSQL/Framework Structure of the standard and relationship between various parts Common definitions and concepts Conformance requirements statement Updates in SQL:2003/Framework reflect updates in all other parts. 5 PartPart 2:2: SQL/FoundationSQL/Foundation The largest and the most important part Specifies the "core" language SQL:2003/Foundation includes all of SQL:1999/Foundation (with lots of corrections) and plus a number of new features Predefined data types Type constructors DDL (data definition language) for creating, altering, and dropping various persistent objects including tables, views, user-defined types, and SQL-invoked routines.