Tackling Bufferbloat in 3G/4G Mobile Networks
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A Comparison of Mechanisms for Improving TCP Performance Over Wireless Links
A Comparison of Mechanisms for Improving TCP Performance over Wireless Links Hari Balakrishnan, Venkata N. Padmanabhan, Srinivasan Seshan and Randy H. Katz1 {hari,padmanab,ss,randy}@cs.berkeley.edu Computer Science Division, Department of EECS, University of California at Berkeley Abstract the estimated round-trip delay and the mean linear deviation from it. The sender identifies the loss of a packet either by Reliable transport protocols such as TCP are tuned to per- the arrival of several duplicate cumulative acknowledg- form well in traditional networks where packet losses occur ments or the absence of an acknowledgment for the packet mostly because of congestion. However, networks with within a timeout interval equal to the sum of the smoothed wireless and other lossy links also suffer from significant round-trip delay and four times its mean deviation. TCP losses due to bit errors and handoffs. TCP responds to all reacts to packet losses by dropping its transmission (conges- losses by invoking congestion control and avoidance algo- tion) window size before retransmitting packets, initiating rithms, resulting in degraded end-to-end performance in congestion control or avoidance mechanisms (e.g., slow wireless and lossy systems. In this paper, we compare sev- start [13]) and backing off its retransmission timer (Karn’s eral schemes designed to improve the performance of TCP Algorithm [16]). These measures result in a reduction in the in such networks. We classify these schemes into three load on the intermediate links, thereby controlling the con- broad categories: end-to-end protocols, where loss recovery gestion in the network. is performed by the sender; link-layer protocols, that pro- vide local reliability; and split-connection protocols, that Unfortunately, when packets are lost in networks for rea- break the end-to-end connection into two parts at the base sons other than congestion, these measures result in an station. -

Application Note Pre-Deployment and Network Readiness Assessment Is
Application Note Contents Title Six Steps To Getting Your Network Overview.......................................................... 1 Ready For Voice Over IP Pre-Deployment and Network Readiness Assessment Is Essential ..................... 1 Date January 2005 Types of VoIP Overview Performance Problems ...... ............................. 1 This Application Note provides enterprise network managers with a six step methodology, including pre- Six Steps To Getting deployment testing and network readiness assessment, Your Network Ready For VoIP ........................ 2 to follow when preparing their network for Voice over Deploy Network In Stages ................................. 7 IP service. Designed to help alleviate or significantly reduce call quality and network performance related Summary .......................................................... 7 problems, this document also includes useful problem descriptions and other information essential for successful VoIP deployment. Pre-Deployment and Network IP Telephony: IP Network Problems, Equipment Readiness Assessment Is Essential Configuration and Signaling Problems and Analog/ TDM Interface Problems. IP Telephony is very different from conventional data applications in that call quality IP Network Problems: is especially sensitive to IP network impairments. Existing network and “traditional” call quality Jitter -- Variation in packet transmission problems become much more obvious with time that leads to packets being the deployment of VoIP service. For network discarded in VoIP -

Lecture 8: Overview of Computer Networking Roadmap
Lecture 8: Overview of Computer Networking Slides adapted from those of Computer Networking: A Top Down Approach, 5th edition. Jim Kurose, Keith Ross, Addison-Wesley, April 2009. Roadmap ! what’s the Internet? ! network edge: hosts, access net ! network core: packet/circuit switching, Internet structure ! performance: loss, delay, throughput ! media distribution: UDP, TCP/IP 1 What’s the Internet: “nuts and bolts” view PC ! millions of connected Mobile network computing devices: server Global ISP hosts = end systems wireless laptop " running network apps cellular handheld Home network ! communication links Regional ISP " fiber, copper, radio, satellite access " points transmission rate = bandwidth Institutional network wired links ! routers: forward packets (chunks of router data) What’s the Internet: “nuts and bolts” view ! protocols control sending, receiving Mobile network of msgs Global ISP " e.g., TCP, IP, HTTP, Skype, Ethernet ! Internet: “network of networks” Home network " loosely hierarchical Regional ISP " public Internet versus private intranet Institutional network ! Internet standards " RFC: Request for comments " IETF: Internet Engineering Task Force 2 A closer look at network structure: ! network edge: applications and hosts ! access networks, physical media: wired, wireless communication links ! network core: " interconnected routers " network of networks The network edge: ! end systems (hosts): " run application programs " e.g. Web, email " at “edge of network” peer-peer ! client/server model " client host requests, receives -

TCP Congestion Control: Overview and Survey of Ongoing Research
Purdue University Purdue e-Pubs Department of Computer Science Technical Reports Department of Computer Science 2001 TCP Congestion Control: Overview and Survey Of Ongoing Research Sonia Fahmy Purdue University, [email protected] Tapan Prem Karwa Report Number: 01-016 Fahmy, Sonia and Karwa, Tapan Prem, "TCP Congestion Control: Overview and Survey Of Ongoing Research" (2001). Department of Computer Science Technical Reports. Paper 1513. https://docs.lib.purdue.edu/cstech/1513 This document has been made available through Purdue e-Pubs, a service of the Purdue University Libraries. Please contact [email protected] for additional information. TCP CONGESTION CONTROL: OVERVIEW AND SURVEY OF ONGOING RESEARCH Sonia Fahmy Tapan Prem Karwa Department of Computer Sciences Purdue University West Lafayette, IN 47907 CSD TR #01-016 September 2001 TCP Congestion Control: Overview and Survey ofOngoing Research Sonia Fahmy and Tapan Prem Karwa Department ofComputer Sciences 1398 Computer Science Building Purdue University West Lafayette, IN 47907-1398 E-mail: {fahmy,tpk}@cs.purdue.edu Abstract This paper studies the dynamics and performance of the various TCP variants including TCP Tahoe, Reno, NewReno, SACK, FACK, and Vegas. The paper also summarizes recent work at the lETF on TCP im plementation, and TCP adaptations to different link characteristics, such as TCP over satellites and over wireless links. 1 Introduction The Transmission Control Protocol (TCP) is a reliable connection-oriented stream protocol in the Internet Protocol suite. A TCP connection is like a virtual circuit between two computers, conceptually very much like a telephone connection. To maintain this virtual circuit, TCP at each end needs to store information on the current status of the connection, e.g., the last byte sent. -

Bit & Baud Rate
What’s The Difference Between Bit Rate And Baud Rate? Apr. 27, 2012 Lou Frenzel | Electronic Design Serial-data speed is usually stated in terms of bit rate. However, another oft- quoted measure of speed is baud rate. Though the two aren’t the same, similarities exist under some circumstances. This tutorial will make the difference clear. Table Of Contents Background Bit Rate Overhead Baud Rate Multilevel Modulation Why Multiple Bits Per Baud? Baud Rate Examples References Background Most data communications over networks occurs via serial-data transmission. Data bits transmit one at a time over some communications channel, such as a cable or a wireless path. Figure 1 typifies the digital-bit pattern from a computer or some other digital circuit. This data signal is often called the baseband signal. The data switches between two voltage levels, such as +3 V for a binary 1 and +0.2 V for a binary 0. Other binary levels are also used. In the non-return-to-zero (NRZ) format (Fig. 1, again), the signal never goes to zero as like that of return- to-zero (RZ) formatted signals. 1. Non-return to zero (NRZ) is the most common binary data format. Data rate is indicated in bits per second (bits/s). Bit Rate The speed of the data is expressed in bits per second (bits/s or bps). The data rate R is a function of the duration of the bit or bit time (TB) (Fig. 1, again): R = 1/TB Rate is also called channel capacity C. If the bit time is 10 ns, the data rate equals: R = 1/10 x 10–9 = 100 million bits/s This is usually expressed as 100 Mbits/s. -

Latency and Throughput Optimization in Modern Networks: a Comprehensive Survey Amir Mirzaeinnia, Mehdi Mirzaeinia, and Abdelmounaam Rezgui
READY TO SUBMIT TO IEEE COMMUNICATIONS SURVEYS & TUTORIALS JOURNAL 1 Latency and Throughput Optimization in Modern Networks: A Comprehensive Survey Amir Mirzaeinnia, Mehdi Mirzaeinia, and Abdelmounaam Rezgui Abstract—Modern applications are highly sensitive to com- On one hand every user likes to send and receive their munication delays and throughput. This paper surveys major data as quickly as possible. On the other hand the network attempts on reducing latency and increasing the throughput. infrastructure that connects users has limited capacities and These methods are surveyed on different networks and surrond- ings such as wired networks, wireless networks, application layer these are usually shared among users. There are some tech- transport control, Remote Direct Memory Access, and machine nologies that dedicate their resources to some users but they learning based transport control, are not very much commonly used. The reason is that although Index Terms—Rate and Congestion Control , Internet, Data dedicated resources are more secure they are more expensive Center, 5G, Cellular Networks, Remote Direct Memory Access, to implement. Sharing a physical channel among multiple Named Data Network, Machine Learning transmitters needs a technique to control their rate in proper time. The very first congestion network collapse was observed and reported by Van Jacobson in 1986. This caused about a I. INTRODUCTION thousand time rate reduction from 32kbps to 40bps [3] which Recent applications such as Virtual Reality (VR), au- is about a thousand times rate reduction. Since then very tonomous cars or aerial vehicles, and telehealth need high different variations of the Transport Control Protocol (TCP) throughput and low latency communication. -

Lab 6: Understanding Traditional TCP Congestion Control (HTCP, Cubic, Reno)
NETWORK TOOLS AND PROTOCOLS Lab 6: Understanding Traditional TCP Congestion Control (HTCP, Cubic, Reno) Document Version: 06-14-2019 Award 1829698 “CyberTraining CIP: Cyberinfrastructure Expertise on High-throughput Networks for Big Science Data Transfers” Lab 6: Understanding Traditional TCP Congestion Control Contents Overview ............................................................................................................................. 3 Objectives............................................................................................................................ 3 Lab settings ......................................................................................................................... 3 Lab roadmap ....................................................................................................................... 3 1 Introduction to TCP ..................................................................................................... 3 1.1 TCP review ............................................................................................................ 4 1.2 TCP throughput .................................................................................................... 4 1.3 TCP packet loss event ........................................................................................... 5 1.4 Impact of packet loss in high-latency networks ................................................... 6 2 Lab topology............................................................................................................... -

A QUIC Implementation for Ns-3
This paper has been submitted to WNS3 2019. Copyright may be transferred without notice. A QUIC Implementation for ns-3 Alvise De Biasio, Federico Chiariotti, Michele Polese, Andrea Zanella, Michele Zorzi Department of Information Engineering, University of Padova, Padova, Italy e-mail: {debiasio, chiariot, polesemi, zanella, zorzi}@dei.unipd.it ABSTRACT One of the most important novelties is QUIC, a transport pro- Quick UDP Internet Connections (QUIC) is a recently proposed tocol implemented at the application layer, originally proposed by transport protocol, currently being standardized by the Internet Google [8] and currently considered for standardization by the Engineering Task Force (IETF). It aims at overcoming some of the Internet Engineering Task Force (IETF) [6]. QUIC addresses some shortcomings of TCP, while maintaining the logic related to flow of the issues that currently affect transport protocols, and TCP in and congestion control, retransmissions and acknowledgments. It particular. First of all, it is designed to be deployed on top of UDP supports multiplexing of multiple application layer streams in the to avoid any issue with middleboxes in the network that do not same connection, a more refined selective acknowledgment scheme, forward packets from protocols other than TCP and/or UDP [12]. and low-latency connection establishment. It also integrates cryp- Moreover, unlike TCP, QUIC is not integrated in the kernel of the tographic functionalities in the protocol design. Moreover, QUIC is Operating Systems (OSs), but resides in user space, so that changes deployed at the application layer, and encapsulates its packets in in the protocol implementation will not require OS updates. Finally, UDP datagrams. -

Adaptive Method for Packet Loss Types in Iot: an Naive Bayes Distinguisher
electronics Article Adaptive Method for Packet Loss Types in IoT: An Naive Bayes Distinguisher Yating Chen , Lingyun Lu *, Xiaohan Yu * and Xiang Li School of Computer and Information Technology, Beijing Jiaotong University, Beijing 100044, China; [email protected] (Y.C.); [email protected] (X.L.) * Correspondence: [email protected] (L.L.); [email protected] (X.Y.) Received: 31 December 2018; Accepted: 23 January 2019; Published: 28 January 2019 Abstract: With the rapid development of IoT (Internet of Things), massive data is delivered through trillions of interconnected smart devices. The heterogeneous networks trigger frequently the congestion and influence indirectly the application of IoT. The traditional TCP will highly possible to be reformed supporting the IoT. In this paper, we find the different characteristics of packet loss in hybrid wireless and wired channels, and develop a novel congestion control called NB-TCP (Naive Bayesian) in IoT. NB-TCP constructs a Naive Bayesian distinguisher model, which can capture the packet loss state and effectively classify the packet loss types from the wireless or the wired. More importantly, it cannot cause too much load on the network, but has fast classification speed, high accuracy and stability. Simulation results using NS2 show that NB-TCP achieves up to 0.95 classification accuracy and achieves good throughput, fairness and friendliness in the hybrid network. Keywords: Internet of Things; wired/wireless hybrid network; TCP; naive bayesian model 1. Introduction The Internet of Things (IoT) is a new network industry based on Internet, mobile communication networks and other technologies, which has wide applications in industrial production, intelligent transportation, environmental monitoring and smart homes. -

Buffer De-Bloating in Wireless Access Networks
Buffer De-bloating in Wireless Access Networks by Yuhang Dai A thesis submitted to the University of London for the degree of Doctor of Philosophy School of Electronic Engineering & Computer Science Queen Mary University of London United Kingdom Sep 2018 TO MY FAMILY Abstract Excessive buffering brings a new challenge into the networks which is known as Bufferbloat, which is harmful to delay sensitive applications. Wireless access networks consist of Wi-Fi and cellular networks. In the thesis, the performance of CoDel and RED are investigated in Wi-Fi networks with different types of traffic. Results show that CoDel and RED work well in Wi-Fi networks, due to the similarity of protocol structures of Wi-Fi and wired networks. It is difficult for RED to tune parameters in cellular networks because of the time-varying channel. CoDel needs modifications as it drops the first packet of queue and thehead packet in cellular networks will be segmented. The major contribution of this thesis is that three new AQM algorithms tailored to cellular networks are proposed to alleviate large queuing delays. A channel quality aware AQM is proposed using the CQI. The proposed algorithm is tested with a single cell topology and simulation results show that the proposed algo- rithm reduces the average queuing delay for each user by 40% on average with TCP traffic compared to CoDel. A QoE aware AQM is proposed for VoIP traffic. Drops and delay are monitored and turned into QoE by mathematical models. The proposed algorithm is tested in NS3 and compared with CoDel, and it enhances the QoE of VoIP traffic and the average end- to-end delay is reduced by more than 200 ms when multiple users with different CQI compete for the wireless channel. -
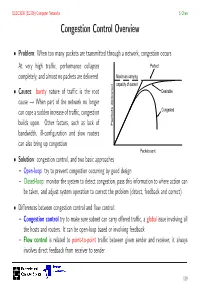
Congestion Control Overview
ELEC3030 (EL336) Computer Networks S Chen Congestion Control Overview • Problem: When too many packets are transmitted through a network, congestion occurs At very high traffic, performance collapses Perfect completely, and almost no packets are delivered Maximum carrying capacity of subnet • Causes: bursty nature of traffic is the root Desirable cause → When part of the network no longer can cope a sudden increase of traffic, congestion Congested builds upon. Other factors, such as lack of Packets delivered bandwidth, ill-configuration and slow routers can also bring up congestion Packets sent • Solution: congestion control, and two basic approaches – Open-loop: try to prevent congestion occurring by good design – Closed-loop: monitor the system to detect congestion, pass this information to where action can be taken, and adjust system operation to correct the problem (detect, feedback and correct) • Differences between congestion control and flow control: – Congestion control try to make sure subnet can carry offered traffic, a global issue involving all the hosts and routers. It can be open-loop based or involving feedback – Flow control is related to point-to-point traffic between given sender and receiver, it always involves direct feedback from receiver to sender 119 ELEC3030 (EL336) Computer Networks S Chen Open-Loop Congestion Control • Prevention: Different policies at various layers can affect congestion, and these are summarised in the table • e.g. retransmission policy at data link layer Transport Retransmission policy • Out-of-order caching -

An Experimental Evaluation of Low Latency Congestion Control for Mmwave Links
An Experimental Evaluation of Low Latency Congestion Control for mmWave Links Ashutosh Srivastava, Fraida Fund, Shivendra S. Panwar Department of Electrical and Computer Engineering, NYU Tandon School of Engineering Emails: fashusri, ffund, [email protected] Abstract—Applications that require extremely low latency are −40 expected to be a major driver of 5G and WLAN networks that −45 include millimeter wave (mmWave) links. However, mmWave −50 links can experience frequent, sudden changes in link capacity −55 due to obstructions in the signal path. These dramatic variations RSSI (dBm) in link capacity cause a temporary “bufferbloat” condition −60 0 25 50 75 100 during which delay may increase by a factor of 2-10. Low Time (s) latency congestion control protocols, which manage bufferbloat Fig. 1: Effect of human blocker on received signal strength of by minimizing queue occupancy, represent a potential solution a 60 GHz WLAN link. to this problem, however their behavior over links with dramatic variations in capacity is not well understood. In this paper, we explore the behavior of two major low latency congestion control protocols, TCP BBR and TCP Prague (as part of L4S), using link Link rate: 5 packets/ms traces collected over mmWave links under various conditions. 1ms queuing delay Our evaluation reveals potential problems associated with use of these congestion control protocols for low latency applications over mmWave links. Link rate: 1 packet/ms Index Terms—congestion control, low latency, millimeter wave 5ms queuing delay Fig. 2: Illustration of effect of variations in link capacity on I. INTRODUCTION queueing delay. Low latency applications are envisioned to play a significant role in the long-term growth and economic impact of 5G This effect is of great concern to low-delay applications, and future WLAN networks [1].