The Role of Technology in Maritime Security: a Survey of Its Development, Application, and Adequacy
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Ankit Love Nominates Dr. Karan Singh, 90 and Prof. Bhim Singh, 79 for President and Vice President of India
ANKIT LOVE PRESS RELEASE: FOR IMMEDIATE RELEASE: JUNE 22, 2021 ANKIT LOVE NFT ARTIST WORLD PEACE ACTIVIST WWW.ANKITLOVE.COM Ankit Love Nominates Dr. Karan Singh, 90 and Prof. Bhim Singh, 79 for President and Vice President of India LONDON, ENGLAND — (June 22, 2021) — Ankit Love appeals to the esteemed Electoral College of India, to take the opportunity and elevate the prestige of the nation internationally as never witnessed before in the upcoming 2022 Indian Presidential Elections, by electing the most exciting and illustrious candidates Dr. Karan Singh, 90 and Prof. Bhim Singh, 79 as President and Vice President of the nation. The two best men alive for the job. Recently, Prime Minister Modi and Dr. Karan Singh jointly released manuscripts pertaining to the Gita in March 2021, and on Thursday June 24, 2021, Prof. Bhim Singh has been invited by Prime Minister Modi to discuss the restoration of the statehood of Jammu and Kashmir. Ankit Love had held an hour long electric and charged interview with Dr. Karan Singh on the matter at his residence in Chanakyapuri, New Delhi perviously. Where Ankit Love while proposing his nomination to Dr. Karan Singh, discovered that the veteran statesman was as able and sharp as ever, with still a deep and most passionate desire to be President of India, and was in fact by far the most deserving and qualified to hold the position, above and beyond anyone else alive today. Following which Ankit Love met and lobbied Indian government ministers Harsh Vardhan, and Arjun Ram Meghwal to nominate Dr. Karan Singh and Prof. -

Primo.Qxd (Page 1)
DAILY EXCELSIOR, JAMMU FRIDAY, NOVEMBER 21, 2014 (PAGE 5) Chief Minister Omar Abdullah at Beerwah, Haj & Auquaf Minister Peerzada Sayeed at Kokernag, PDP leader Dr Haseeb Drabu at Rajpora, BJP candidate Mushtaq Ahmad Mir at Uri, NC leader Yawar Masoodi at Pampore and NC candidate Gh Mohi-ud-Din Mir filing nomination papers on Thursday. -Excelsior pics by Amin War, Aabid Nabi & Sajjad Dar CS reviews post flood Sham lambasts BJP over rehabilitation measures issue of PoJK DPs Excelsior Correspondent that Public Works Department is Excelsior Correspondent said that BJP should clarify Centre. This will have a seri- constructing 503 residential struc- its stand on Article 370 and ous repercussion as lakhs of SRINAGAR, Nov 20: Chief tures for flood victims in the AKHNOOR, Nov 20: PoJK refugees settlement. He displaced persons, who are Secretary, Mohammad Iqbal Valley, besides various NGOs are Lambasting BJP on the issue said that BJP shall not be fighting for their cause, will Khanday today convened a high also constructing residential struc- of Displaced Persons of allowed to destabilize the teach a lesson to the BJP. level meeting at Winter tures for flood victims in the PoJK, senior Congress leader constitutional dimensions in Stating that the issue of Secretariat to review the ongoing Valley which include 107 sheds in and Minister for PHE, the political sensitive State PoJK displaced persons relief measures being undertaken Srinagar city, 38 sheds in Shopian Irrigation & Flood Control, like Jammu and Kashmir remained hanging in the air by the Government for rehabilita- and 15 sheds each in Pulwama Sham Lal Sharma today said for over six decades, Mr tion of flood victims of Kashmir and Anantnag districts. -

NTP Contact Information
Country NTP Manager Title E-mail Afghanistan Dr. Mohmmad Khaled Seddiq NTP Manager [email protected] Albania Donika Mema Manager National Program Tuberculosis [email protected] Algeria SOFIANE ALIHALASSA National Tuberculosis Program Manager [email protected] Andorra Clara Palma Jordana Técnico en Salud Pública [email protected] Angola Ambrosio DISADIDI Coordenador do Programa Nacional [email protected] de Controlo da Tuberculose Anguilla Aisha Andrewin Chief Medical Officer [email protected] Argentina Marcela Natiello Coordinadora [email protected] Armenia Lusine Kocharyan NTC Director [email protected] Aruba Wilmer Salazar MD; medical advisor [email protected] Dept. Public Health Aruba Australia National Tuberculosis Australian Government [email protected] Advisory Committee Department of Health [email protected] Azerbaijan Viktor Gasimov NTP manager [email protected] Bahamas JACQUELYN NEWBOLD TB -PROGRAMME -COORDINATOR [email protected] Bahrain Ebrahim AlRomaihi Consultant Internist & NTP Manager [email protected] Bangladesh Md. Shamiul Islam Director MBDC & [email protected] Line Director TB, Leprosy & ASP Barbados RAJAMANICKAM MANOHAR SINGH NATIONAL TB CONTROL OFFICER [email protected] [email protected] Belarus Геннадий Гуревич Директор ГУ [email protected] "РНПЦ пульмонологии и фтизиатрии" Belize Francis Morey Deputy Director of Health Services [email protected] Benin AFFOLABI Dissou Professeur [email protected] -

Statistical Report General Election
STATISTICAL REPORT ON GENERAL ELECTION, 1962 TO THE LEGISLATIVE ASSEMBLY OF MADHYA PRADESH ELECTION COMMISSION OF INDIA NEW DELHI Election Commission of India - General Election, 1962 to the Legislative Assembly of Madhya Pradesh STATISTICAL REPORT CONTENTS SUBJECT Page no. 1. List of Participating Political Parties and Abbreviation 1 2. Other Abbreviations in the Report 2 3. Highlights 3 4. List of Successful Candidates 4 – 10 5. Performance of Political Parties 11 6. Electors Data Summary – Summary on Electors, voters votes Polled and Polling Stations 12 7. Women Candidates 13 - 15 8. Constituency Data Summary 16– 303 9. Detailed Result 304 - 349 Election Commission of India-State Elections,1962 to the Legislative Assembly of Madhya Pradesh LIST OF PARTICIPATING POLITICAL PARTIES SR NO ABBREVIATION PARTY 1 SWA SWATANTRA 2 SOC SOCIALIST 3 PSP PRAJA SOCIALIST PARTY 4 JS JAN SANGH 5 INC INDIAN NATIONAL CONGRESS 6 CPI COMMUNIST PARTY OF INDIA 7 RRP RAM RAJYA PARISHAD 8 REP REPUBLICAN 9 HMS HINDU MAHASABHA 10 FB FORWARD BLOC 11 IND INDEPENDENT rptListOfParticipatingPoliticalParties - Page 1 of 1 1 1 Election Commission of India - State Election, 1962 to the Legislative Assembly of Madhya Pradesh OTHER ABBREVIATIONS AND DESCRIPTION ABBREVIATION DESCRIPTION FD Forfeited Deposits Gen General Constituency SC Reserved for Scheduled Castes ST Reserved for Scheduled Tribes M Men W Women T Total N National Party S State Party R Recognised Political Party U Registered (Unrecognised) Party Z Independent rptOtherAbbreviations - Page 1 of 1 2 Election Commission of India - State Election, 1962 to the Legislative Assembly of Madhya Pradesh HIGHLIGHTS 1. NO. OF CONSTITUENCIES TYPE OF CONSTITUENCY GEN SC ST TOTAL NO. -
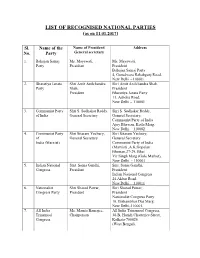
LIST of RECOGNISED NATIONAL PARTIES (As on 11.01.2017)
LIST OF RECOGNISED NATIONAL PARTIES (as on 11.01.2017) Sl. Name of the Name of President/ Address No. Party General secretary 1. Bahujan Samaj Ms. Mayawati, Ms. Mayawati, Party President President Bahujan Samaj Party 4, Gurudwara Rakabganj Road, New Delhi –110001. 2. Bharatiya Janata Shri Amit Anilchandra Shri Amit Anilchandra Shah, Party Shah, President President Bharatiya Janata Party 11, Ashoka Road, New Delhi – 110001 3. Communist Party Shri S. Sudhakar Reddy, Shri S. Sudhakar Reddy, of India General Secretary General Secretary, Communist Party of India Ajoy Bhawan, Kotla Marg, New Delhi – 110002. 4. Communist Party Shri Sitaram Yechury, Shri Sitaram Yechury, of General Secretary General Secretary India (Marxist) Communist Party of India (Marxist) ,A.K.Gopalan Bhawan,27-29, Bhai Vir Singh Marg (Gole Market), New Delhi - 110001 5. Indian National Smt. Sonia Gandhi, Smt. Sonia Gandhi, Congress President President Indian National Congress 24,Akbar Road, New Delhi – 110011 6. Nationalist Shri Sharad Pawar, Shri Sharad Pawar, Congress Party President President Nationalist Congress Party 10, Bishambhar Das Marg, New Delhi-110001. 7. All India Ms. Mamta Banerjee, All India Trinamool Congress, Trinamool Chairperson 30-B, Harish Chatterjee Street, Congress Kolkata-700026 (West Bengal). LIST OF STATE PARTIES (as on 11.01.2017) S. No. Name of the Name of President/ Address party General Secretary 1. All India Anna The General Secretary- No. 41, Kothanda Raman Dravida Munnetra in-charge Street, Chennai-600021, Kazhagam (Tamil Nadu). (Puratchi Thalaivi Amma), 2. All India Anna The General Secretary- No.5, Fourth Street, Dravida Munnetra in-charge Venkatesware Nagar, Kazhagam (Amma), Karpagam Gardens, Adayar, Chennai-600020, (Tamil Nadu). -

Floral Tributes Paid to Atal Bihari Vajpayee Ji
JAMMU & KASHMIR THE SHADOW 3 JAMMU, SATURDAY, DECEMBER 26, 2020 NPP holds party conference in memory BJP organised ‘Sushasan Divas’ programmes on Atal ji’s birthday 96th birthday of Atal Bihari Vajpayee Shadow Correspondent Arora, remembered Atal ji. gramme to pay tributes, JAMMU, DEC, 25 Union MoS Dr. Jitendra former Minister Ajay Shadow Correspondent JAMMU, DEC, 25 On the occasion of the Singh, former Deputy Nanda and Kuldeep Raj Prof.Bhim Singh, Chief Patron, National Panthers birthday of former Prime Chief Minister Dr. Nirmal Dubey in Reasi, Pardeep Minister, Atal Bihari Vaj- Party and Member, National Integration Council, 96th Singh, Vice President Yud- Sharma and Sunil Gupta in conference his memory of the former Prime Minister of payee, Jammu and Kash- hvir Sethi, party leaders Poonch and Vikram Rand- mir BJP organised ‘Good India, Atal Bihari Vajpayee on his birthday. Vijay Sharma and Rashpal hawa chaired similar pro- In his unusual compliments to Atal Bihari Vajpayee, Governance Day’ Verma paid tributes to grammes in Jammu dis- (Sushasan Divas) pro- the Panthers Party Chief recollected his interaction with Atal ji in different Mandals trict to pay tributes. grammes in 128 Mandals the former Prime Minister of India during the past 30 of Kathua district. across the UT, wherein the Twenty programmes in years which the Panthers Party Chief had with Atal Bi- party senior leaders led the Lok Sabha MP Jugal Basohli, fourteen in Now- hari Vajpayee. party activists in remem- Kishore Sharma, Rajya shera-Sunderbani district, The Panthers Party Chief recollected that Atal Bihari bering Atal ji and his Sabha MP Shamsher Singh nine each in Ramban and Vajpayee once visited Kashmir in 1973 when group of splendid contribution in Manhas and others took Udhampur, five pro- boys tried to create this order in his public meeting in Iqbal Park. -

Page5 Local.Qxd (Page 1)
DAILY EXCELSIOR, JAMMU SUNDAY, NOVEMBER 8, 2020 (PAGE 5) Dheeraj inspects progress on Ensure supply of fertilizers multi level car parking project to farmers: Sukhnandan Excelsior Correspondent keep in view that the winter Excelsior Correspondent asked JDA Engineering Wing & crops are not only a key crop executing agency to gear up the JAMMU, Nov 7: Former cycle for farmers but is equally JAMMU, Nov 7: Principal work for early commissioning of Minister, ex-MLA Marh & important for the growth of Secretary, Housing & Urban the project aimed at deconges- chairman Panchayati Raj Cell Jammu and Kashmir's economy Development Department, tion of traffic in the city. BJP, JKUT, Ch Sukhnandan which largely depends on the Dheeraj Gupta, today inspected Instructions were also issued Cong leaders led by PCC chief G A Mir launching signature DSSP chairman Choudhary Lal Singh addressing party today urged the Government to agricultural and horticulture sec- progress on upcoming multi for face lifting of old General campaign at Gole Market, Gandhi Nagar in Jammu on Saturday. workers at Kathua. ensure availability of fertilizers tors. level car parking cum shopping Bus Stand Complex, premixing —Excelsior/ Rakesh specially DAP in Jammu divi- Due to non-availability of complex at General Bus Stand. of the approaching roads, repair sion as due to the shortage of DAP fertilizer, the farmers in The Jammu Development & face lifting of overhead foot DSSP to unite all nationalistic DAP fertilizer farmers in this Jammu division would lose Cong intensifies signature campaign Authority project is aimed at bridge, dismantling and recon- area are facing problems. crops and the overall crop pro- meeting the parking space struction of old damaged retain- In a press statement issued duction would be drastically requirement to de-congest traffic ing wall & other minor repair forces of region: Lal Singh against new J&K land laws, farm bills on Jammu city roads. -

India's COVID-19 Tally Nears 37 Lakh
K K M " " #! "# "# "!" " # M Y !% "!" !" ! $ ! ! ! "!$ Y C C JAMMU, WEDNESDAY, SEPTEMBER 2 , 2020 VOL. 36 | NO.242 | REGD. NO. : JM/JK 118/15 /17 | E-mail : [email protected] |www.glimpsesoffuture.com | Price : Rs. 2.00 India's COVID-19 tally nears 37 President, VP, Prime Minister pay last respects to Mukherjee lakh; recovery rate 76.94% . $"#( B0<?;4B 70E4 144= &A4B834=C (0< $0C7 . $"#( C4BC43D?C>D6DBC >5 !>E8=3,824&A4B834=C# C74<>=#>=30H %5C74 5A4B7 ,4=:0807 $083D &A8<4 -8C7 ?4>?;4 C4BC8=6 340C7B F4A4 A4?>AC43 5A>< #8=8BC4A $0A4=3A0 #>38 ?>B8C8E45>A2>A>=0E8ADB8=542C8>= #070A0B7CA0 5A><!0A=0C0:0 0=327845B>5C7A443454=24 >=*D4B30H=380B%, C0; 5A>< *0<8; $03D 5A>< B4AE824B F4A4 0<>=6 C74 ;H<>D=C43C> F78;4A4 =37A0 &A034B7 5A>< +CC0A 386=8C0A84BF7>?083C748A 2>E4A84B BDA643 C> &A034B7 5A><-4BC4=60; ;0BC A4B?42CB C> 5>A<4A ?DB78=6C74A42>E4AHA0C4C> 5A>< &D=901 5A>< #037H0 ?A4B834=C &A0=01 ?4A 24=C 022>A38=6 C> +=8>= &A034B7 5A><4;78 5A>< #D:74A944 >= *D4B30H 40;C7#8=8BCAH30C0 *74340C7 D90A0C 5A>< (090BC70= <>A=8=6 #D:74A944B C>;;<40=F78;42;8<143C> 5A>< +CC0A0:70=3 0=3 4027 <>AC0; A4<08=B F4A4 A<H 7845 4= # # =>D=2430B4E4=30HBC0C4 F8C7 =4F50C0;8C84B148=6A4 5A><BB0<%38B700=3*A8?DA0 1A>D67CC>78BA4B834=24 $0A0E0=4 8A 7845 <>DA=8=60B0<0A:>5A4 ?>AC438=0B?0=>5 7>DABC74 $8=450C0;8C84B402770E4144=A4 (09098#0A640A;84AC> #0AB70;(!)7030DA80 B?42C5>AC745>A<4A?A4B8 30C0D?30C430C0<B7>F43 *74 ?>AC435A><>0*4;0=60=00=3 30H5A><C740A<H7>B?8C0; 0=3 $0EH 7845 3<8A0; 34=C #D:74A944 >=4 >5 %, 20B450C0;8CHA0C470B34 -

AIPP Elected Office Bearers/Members to Continue Till Dec 2024: Mishra NHPC Distributing Dry Ration to Needy People in Jammu PM
NORTH IN NEWS JAMMU LOCAL JAMMU, FRIDAY 25, JUNE, 2021 5 BJP leader Baldev Singh Billawaria along with Food eatry AIPP elected office bearers/members former councilor Paramjit Singh visited ward 58 closed for to continue till dec 2024: Mishra NIN NEWS SERVICE JAMMU, JAMMU 24 neglecting NIN NEWS SERVICE the AIPP Executive Gupta-Ex President JKPP BJP leader Baldev Singh JAMMU, JAMMU 24 Committee, elected in the and now In-charge J&K, Billawaria along with To dispel the confusion General Elections of All Ladakh UTs Unit of AIPP, former councilor Paramjit sanitary, and chaos, uncertainty and India Panchayat Parishad Member AIPP Executive Singh visited ward 58 slackness creeping up in (AIPP) Delhi held in the Committee shall continue Green Avenue in Gandhi hygienic t h e Parishad premises on 19th to be so till 2024. Dr Nagar constituency area organisational/administra December'2019, shall be Kuldeep Sharma-President and took stock of the tive system, a reviewal till 18th December'2024," JKPP who has been problems being faced by parameters thought has been applied said Sh. S. S. Vijai Mishra advised to hold elections of the local residents due to at the apex level by the General Secretary (H.Q) the JKUT UNIT within Chief General Secretary at and Election Officer, AIPP. three months to give more the poor condition of the NIN NEWS SERVICE AIPP Head Quarters. He also said that Ex - representation to the road. Local residents told JAMMU, JAMMU 24 Accordingly, a number of President Gujarat State elected representatives of Billawaria that these road Acting swiftly on a specific steps/initiatives/clarificat Panchayat Parishad and 3tier PRIs including DDCs was in bad condition for a complaint, Food Safety ions have been announced now Member Zila shall continue to hold long time. -

Pinky 3(1).Pdf
PAPER FOR CONFERENCE INITIATIVES TOWARDS PEACE PROCESS IN THE JAMMU AND KASHMIR STATE IN THE POST-KARGIL ERA 3. Introduction This paper is related to the post-Kargil phase when dialogue and peace process was initiated in J&K to restore democratic process. It explores in detail the external and internal factors which led to changes in the Kashmir policy. It also assesses the changes in policies towards Kashmir at various levels. The J&K Assembly election in 2002 marked a significant point of departure for the state. These elections and their impact on the state politics of J&K have also been discussed and analysed. The regional as well as communal polarisation in Jammu and Kashmir (J&K) was reflected more sharply in its state politics during the decade of the nineties, especially in the background of militancy and political upsurge. Rekha Chowdhary mentions that the alienation of Kashmiris had the effect of bringing into focus the divergence of political aspirations between Kashmir on the one hand and Jammu and Ladakh on the other. This divergence was politicised in both the regions during 1990-1996 when normal political processes were suspended in the valley. During this period there was intensification of political deliberations around the regional aspirations in both the areas. The issue of ‘regional autonomy’ had become the most vocal issue of these regions by 1996.1 3.1 The Agenda for Autonomy The State Autonomy Committee (SAC) and Regional Autonomy Committee (RAC) were set up by the Farooq Abdullah government in November 1996 to outline the prospects of greater autonomy for J&K. -

5-Udhampur Parliamentary Constituency S.No
FORM 7-A [See rule 10 (1)] LIST OF CONTESTING CANDIDATES Election to the House of the People from 5-Udhampur Parliamentary Constituency S.No. Name of Address of @ Party affiliation Symbol Candidate Candidate allotted (i) Candidates of recognized National and State Political Parties 1 Adrees Ahmad Behera Tehsil Communist Party of Ears of Corn Tabbasum Mendhar, Distt. India and Sickle Poonch 2 Balbir Singh Vill. Rampur Tehsil J&K People’s Ink Pot and Billawar Distt. Democratic Party Pen Kathua 3 Prof.Bhim Singh Panthers Lodge J&K National Panthers Bicycle Canal Road, Jammu Party 4 Rakesh Wazir Kun Drorian, Kalka Bahujan Samaj Party Elephant Nagar, Katra Tehsil & Distt. Reasi 5 Ch. Lal Singh Kothi No.01, Indian National Congress Hand W.No.02 Kathua 6 Dr. Nirmal Singh 24-A New Campus, Bharatiya Janata Party Lotus University of Jammu, Jammu (ii) Candidates of registered political parties (other than recognized National and State Political Parties) 7 Bodh Raj Vill. Padyari, Tehsil Backward Classes Sewing & Distt. Kathua Democratic Party J&K Machine (BDP) 8 Rajesh Manchanda 80/3 Chhani Himmat, Rashtriya Krantikari Railway Jammu Samajwadi Party Engine 9 Kanchan Sharma H.No.105-F, Janipur Bharatiya Bahujan Party Gas Cylinder Housing Colony, Jammu 10 Master William Mohalla Christan All India Forward Bloc Lion Gill Basti, Residency Road, Jammu (iii) Other Candidates 11 Atul Sharma W.No.14 Salian Independent Ceiling Fan Talab, Udhampur 12 Dev Raj Lakhnote, PO Independent Blackboard Saidpur (Parole), Tehsil and Distt. Kathua 13 Mohd. Yousuf Maithra, Tehsil Independent Candles Ramban, Distt. Ramban 14 Naresh Dogra H.No. -

STAR CAMPAIGNERS of POLITICAL PARTIES for the GENERAL ELECTION to KLA 2011 INDIAN NATIONAL CONGRESS Sl.No
GE to KLA 2011 STAR CAMPAIGNERS OF POLITICAL PARTIES FOR THE GENERAL ELECTION TO KLA 2011 INDIAN NATIONAL CONGRESS Sl.No. Name of Leader 1 Sonia Gandhi 2 Dr. Manmohan Singh 3 Pranab Mukherjee 4 Rahul Gandhi 5 Madhusudan Mistry 6 Oscar Fernandes 7 Ramesh Chennithala 8 Oommen Chandy 9 A.K. Antony 10 Vayalar Ravi 11 Thennala Balakrishna Pillai 12 C.V. Padmarajan 13 P.P. Thankachan 14 M.M. Hassan 15 K. Muraleedharan 16 Mullappally Ramachandran 17 Thalekunnil Basheer 18 Prof. P.J. Kurien 19 Dr. Shashi Tharoor 20 N. Peethambara Kurup 21 Anto Antony 22 Kodikkunnil Suresh 23 K.C. Venugopal 24 K.V. Thomas 25 P.T. Thomas 26 K.P. Dhanapalan 27 P.C. Chacko 28 M.I. Shanavas 29 M.K. Raghavan 30 K. Sudhakaran 31 Charles Dias 32 Neyyattinkara Sanal 33 Rosakutty Teacher 34 P. Sankaran 35 N. Venugopal 36 Dr. M.A. Kuttappan 37 A.C. Jose 38 Prof. G. Balachandran 39 V.M. Sudheeran 40 R. Chandrasekharan Page No : 1 of 10 GE to KLA 2011 STAR CAMPAIGNERS OF POLITICAL PARTIES FOR THE GENERAL ELECTION TO KLA 2011 COMMUNIST PARTY OF INDIA (MARXIST) 1 Prakash Karat 2 S. Ramachandran Pillai 3 Sitaram Yechury 4 Manik Sarkar 5 Brinda Karat 6 Pinarayi Vijayan 7 Kodiyeri Balakrishnan 8 V.S. Achuthanandan 9 Subhashini Ali 10 M.A. Baby 11 Vaikom Viswan 12 Thomas Issac 13 E.P. Jayarajan 14 P. Karunakaran 15 P.K. Srimathi 16 M.C. Josephine 17 P.K. Gurudasan 18 A. Vijayaraghavan 19 Paloli Mohd. Kutty 20 K.N.