Final Assessment on Connectivity Management for Very Dense Sce- Narios
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
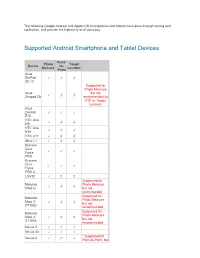
Supported Android Smartphone and Tablet Devices
The following Google Android and Apple iOS smartphones and tablets have gone through testing and calibration, and provide the highest level of accuracy: Supported Android Smartphone and Tablet Devices Point- Photo Target Device to- Measure Location Point Asus ZenPad ✓ ✗ ✗ 3S 10 Supported for Photo Measure Asus but not ✓ ✗ ✗ Zenpad Z8 recommended for P2P or Target Location Asus Zenpad ✓ ✓ ✓ Z10 HTC One ✓ ✗ ✗ M8 HTC One ✓ ✗ ✗ Mini HTC U11 ✓ ✗ ✗ iNew L1 ✓ ✗ ✗ Kyocera Dura ✓ ✓ ✓ Force PRO Kyocera Dura ✓ ✓ ✓ Force PRO 2 LGV20 ✓ ✗ ✗ Supported for Motorola Photo Measure ✓ ✗ ✗ Moto G but not recommended Supported for Motorola Photo Measure Moto X ✓ ✗ ✗ but not XT1052 recommended Supported for Motorola Photo Measure Moto X ✓ ✗ ✗ but not XT1053 recommended Nexus 5 ✓ ✓ ✓ Nexus 5X ✓ ✓ ✓ * Supported for Nexus 6 ✓ ✓* ✓ Point-to-Point, but cannot guarantee +/-3% accuracy * Supported for Point-to-Point, but Nexus 6P ✓ ✓* ✓ cannot guarantee +/-3% accuracy * Supported for Point-to-Point, but Nexus 7 ✓ ✓* ✓ cannot guarantee +/-3% accuracy Samsung Galaxy ✓ ✓ ✓ A20 Samsung Galaxy J7 ✓ ✗ ✓ Prime * Supported for Samsung Point-to-Point, but GALAXY ✓ ✓* ✓ cannot guarantee Note3 +/-3% accuracy Samsung GALAXY ✓ ✓ ✓ Note 4 * Supported for Samsung Point-to-Point, but GALAXY ✓ ✓* ✓ cannot guarantee Note 5 +/-3% accuracy Samsung GALAXY ✓ ✓ ✓ Note 8 Samsung GALAXY ✓ ✓ ✓ Note 9 Samsung GALAXY ✓ ✓ ✓ Note 10 Samsung GALAXY ✓ ✓ ✓ Note 10+ Samsung GALAXY ✓ ✓ ✓ Note 10+ 5G Supported for Samsung Photo Measure GALAXY ✓ ✗ ✗ but not Tab 4 (old) recommended Samsung Supported for -
System Requirements
System Requirements The following standards are recommended for each client computer accessing the Chrome River application. The application runs entirely within the web browser and does not require any additional Chrome River application code. Most modern web browsers and operating systems will be able to access and operate the application. However, Chrome River recommends that the user’s preferred browser and operating system configuration be verified to work consistently with the Chrome River application. NOTE: You may notice that there is a Chrome River App available on Google Store, Apple Store or similar sites. This app is NOT to be used. The CBS Chrome River application is only available by using this URL: https://chromeriver.cbs.com. Web Browser While other web browsers may also operate the Chrome River application successfully, the following are recommended for use in their most recent versions: Microsoft Version 11.0 or higher www.microsoft.com/windows/products/winfamily/ie/default.mspx Internet Explorer Google Version 51.0 or higher www.google.com/chrome Chrome Safari Version 9.1 or higher* for supported mobile www.apple.com/safari devices *Chrome River does not currently support the Safari browser in “Private” mode. Users must turn off Private mode before logging in to the application. Recommended Operating Systems and Browsers ANDROID MOBILE DEVICES Operating System: Kitkat 4.4.2 or higher Browser: Chrome v.51 or higher APPLE MOBILE DEVICES Operating System: iOS 9 or higher Browser: Safari 9.1 or higher WINDOWS PC DESKTOP/NOTEBOOK Operating System: Any HTML 5-supporting browser Browsers: • Chrome v.51 or higher • Internet Explorer 11 or higher APPLE DESKTOP/NOTEBOOK: Operating System: Any HTML 5-supporting browser Browser: Safari 9.1 or higher CERTIFIED VS SUPPORTED DEVICES Devices listed as certified are those on which Chrome River has tested and fixed any bugs. -

View the Slides
Firmware Insider Bluetooth Randomness is Mostly Random RANDOMNESS IS MY PASSION Jörn Tillmanns, Jiska Classen, Felix Rohrbach, Matthias Hollick Technische Universität Darmstadt, Germany ??? 2 How to acquire randomness? A: 42 B: Random Access Memory C: Random Only Memory D: Hardware RNG 3 RNG Variants 2 and 3 Device Chip Date Variant HRNG Location PRNG Cache Google Nexus 5 Dec 11 2012 2 0x314004, 3 regs Yes (inline) No MacBook 2016 Oct 22 2015 2 0x314004, 3 regs Yes (inline) No CYW20735B1 Jan 18 2018 3 0x352600, 3 regs Yes (rbg_get_psrng), Yes, breaks after 32 elements 8 registers CYW20819A1 May 22 2018 3 0x352600, 3 regs Yes (rbg_get_psrng), Yes (with minor fixes) 5 registers 4 RNG Variant 2 ● HRNG mapped to 0x314004 ● Three 4 byte registers ● Inline PRNG fallback ● No cache As seen on the MacBook Pro 2016 (BCM20703A2) and more... 5 RNG Variant 2, PRNG Fallback ● HRNG mapped to 0x314004 ● Three 4 byte registers ● Inline PRNG fallback ● No cache As seen on the MacBook Pro 2016 (BCM20703A2) and more... 6 How random is the PRNG? PRNG measurements taken on a Google Nexus 5 (BCM4335C0). 7 CVE Time! ...got assigned CVE-2020-6616 :) 8 Responsible Disclosure We: Why would you introduce and maintain a PRNG if you had a proper HRNG? Broadcom: Why should we use a PRNG when there is a HRNG in all of our devices? ??? 9 10 Let’s take a look at a few more devices... 11 Measuring the HRNG @fxrh says that Dieharder requires at least 1GB of data... 12 Optimizations ● Find a large free memory chunk that is not used while the chip is idle. -

List Compatible Smartphones
Produkt App iOS Android AS80/C iPhone 7 Plus Samsung Galaxy S7 iPhone 7 Samsung Galaxy S6 iPhone 6s Plus Samsung Galaxy S5 iPhone 6s Samsung Galaxy S4 iPhone 6 Plus Samsung Galaxy S4 mini iPhone 6 Samsung Galaxy S3 AS81 iPhone 5s LG Google Nexus 5 iPhone 5c LG L40 iPhone 5 iPhone 4s iPad (4th generation) AW85 iPad (3rd generation) iPad mini iPod touch (5th generation) BC57 BC85 BF700 BF710 BF800 BM57 1/6 Produkt App iOS Android BM75 iPhone 7 Plus Samsung Galaxy S7 iPhone 7 Samsung Galaxy S6 iPhone 6s Plus Samsung Galaxy S5 iPhone 6s Samsung Galaxy S4 iPhone 6 Plus Samsung Galaxy S4 mini iPhone 6 Samsung Galaxy S3 BM77 iPhone 5s LG Google Nexus 5 iPhone 5c LG L40 iPhone 5 iPhone 4s iPad (4th generation) BM 85 iPad (3rd generation) iPad mini iPod touch (5th generation) GL50EVO BLE GL50EVO NFC GS485 PO60 Systemvoraussetzung: Bluetooth® 4.0, iOS ab 8.0 Bluetooth® 4.0, Android™ ab 4.4 Android™ ab Version 4.1 mit NFC-Funktion (Near Field Communication) 2/6 Produkt App iOS Android KS800 iPhone 7 Plus iPhone 7 iPhone 6s Plus iPhone 6s iPhone 6 Plus iPhone 6 iPhone 5s iPhone 5c iPhone 5 iPhone 4s iPad (4th generation) iPad (3rd generation) iPad mini Systemvoraussetzung: Bluetooth® 4.0, iOS ab 8.0 Produkt App iOS Android AS80/C iPhone 7 Plus Samsung Galaxy S7 iPhone 7 Samsung Galaxy S6 iPhone 6s Plus Samsung Galaxy S5 iPhone 6s Samsung Galaxy S4 iPhone 6 Plus Samsung Galaxy S4 mini iPhone 6 Samsung Galaxy S3 AS81 iPhone 5s LG Google Nexus 5 iPhone 5c LG L40 iPhone 5 iPhone 4s iPad (4th generation) BF700 iPad (3rd generation) iPad mini iPod touch -
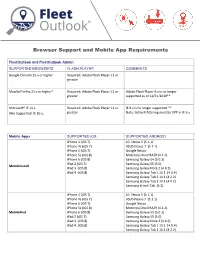
Browser Support and Mobile App Requirements
Browser Support and Mobile App Requirements FleetOutlook and FleetOutlook Admin SUPPORTED BROWSERS FLASH PLAYER COMMENTS Google Chrome 25.x or higher Required: Adobe Flash Player 11 or greater Mozilla Firefox 21.x or higher* Required: Adobe Flash Player 11 or Adobe Flash Player 9.x is no longer greater supported as of 12/31/2010** Microsoft® IE 11.x Required: Adobe Flash Player 11 or IE 9.x is no longer supported ** Also Supported: IE 10.x, greater Note: ActiveX Filtering must be OFF in IE 9.x Mobile Apps SUPPORTED iOS SUPPORTED ANDROID iPhone 4 (iOS 7) LG Nexus 5 (5.1.1) iPhone 4s (iOS 7) ASUS Nexus 7 (5.1.1) iPhone 5 (iOS 7) Google Nexus iPhone 5s (iOS 8) Motorola Droid RAZR (4.1.2) iPhone 6 (iOS 8) Samsung Galaxy S4 (5.0.1) iPad 2 (iOS 7) Samsung Galaxy S5 (5.0) MobileInstall iPad 3 (iOS 8) Samsung Galaxy Note 2 (4.4.2) iPad 4 (iOS 8) Samsung Galaxy Tab 1 10.1 (4.0.4) Samsung Galaxy Tab 2 10.1 (4.2.2) Samsung Galaxy Tab 3 10.1 (4.4.2) Samsung 8-inch Tab (4.2) iPhone 4 (iOS 7) LG Nexus 5 (5.1.1) iPhone 4s (iOS 7) ASUS Nexus 7 (5.1.1) iPhone 5 (iOS 7) Google Nexus iPhone 5s (iOS 8) Motorola Droid RAZR (4.1.2) MobileFind iPhone 6 (iOS 8) Samsung Galaxy S4 (5.0.1) iPad 2 (iOS 7) Samsung Galaxy S5 (5.0) iPad 3 (iOS 8) Samsung Galaxy Note 2 (4.4.2) iPad 4 (iOS 8) Samsung Galaxy Tab 1 10.1 (4.0.4) Samsung Galaxy Tab 2 10.1 (4.2.2) Samsung Galaxy Tab 3 10.1 (4.4.2) Samsung S3 (4.0.4) Samsung 8-inch Tab (4.2) iPhone 4 (iOS 6) LG Nexus 5 (5.1.1) iPhone 4s (iOS 6) ASUS Nexus 7 (5.1.1) iPhone 5 (iOS 7) Google Nexus iPhone 5s (iOS 8) Motorola Droid RAZR (4.1.2) iPhone 6 (iOS 8) Samsung Galaxy S4 (5.0.1) iPad 2 (iOS 7) Samsung Galaxy S5 (5.0) MobileNav iPad 3 (iOS 8) Samsung Galaxy Note 2 (4.4.2) iPad 4 (iOS 8) Samsung Galaxy Tab 1 10.1 (4.0.4) Samsung Galaxy Tab 2 10.1 (4.2.2) Samsung Galaxy Tab 3 10.1 (4.4.2) Samsung S3 (4.0.4) Samsung 8-inch Tab (4.2) ! Important: For all browsers you must enable JavaScript, cookies and SSL 3.0. -
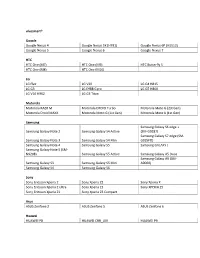
Vívosmart® Google Google Nexus 4 Google Nexus 5X (H791) Google Nexus 6P (H1512) Google Nexus 5 Google Nexus 6 Google Nexus
vívosmart® Google Google Nexus 4 Google Nexus 5X (H791) Google Nexus 6P (H1512) Google Nexus 5 Google Nexus 6 Google Nexus 7 HTC HTC One (M7) HTC One (M9) HTC Butterfly S HTC One (M8) HTC One (M10) LG LG Flex LG V20 LG G4 H815 LG G3 LG E988 Gpro LG G5 H860 LG V10 H962 LG G3 Titan Motorola Motorola RAZR M Motorola DROID Turbo Motorola Moto G (2st Gen) Motorola Droid MAXX Motorola Moto G (1st Gen) Motorola Moto X (1st Gen) Samsung Samsung Galaxy S6 edge + Samsung Galaxy Note 2 Samsung Galaxy S4 Active (SM-G9287) Samsung Galaxy S7 edge (SM- Samsung Galaxy Note 3 Samsung Galaxy S4 Mini G935FD) Samsung Galaxy Note 4 Samsung Galaxy S5 Samsung GALAXY J Samsung Galaxy Note 5 (SM- N9208) Samsung Galaxy S5 Active Samsung Galaxy A5 Duos Samsung Galaxy A9 (SM- Samsung Galaxy S3 Samsung Galaxy S5 Mini A9000) Samsung Galaxy S4 Samsung Galaxy S6 Sony Sony Ericsson Xperia Z Sony Xperia Z2 Sony Xperia X Sony Ericsson Xperia Z Ultra Sony Xperia Z3 Sony XPERIA Z5 Sony Ericsson Xperia Z1 Sony Xperia Z3 Compact Asus ASUS Zenfone 2 ASUS Zenfone 5 ASUS Zenfone 6 Huawei HUAWEI P8 HUAWEI CRR_L09 HUAWEI P9 Oppo OPPO X9076 OPPO X9009 Xiaomi XIAOMI 2S XIAOMI 3 XIAOMI 5 XIAOMI Note One Plus OnePlus 3 (A3000) vívosmart® 3 Google Google Nexus 5X (H791) Google Nexus 6P (H1512) Google Pixel HTC HTC One (M9) HTC One (M10) HTC U11 HTC One (A9) HTC U Ultra LG LG V10 H962 LG G4 H815 LG G6 H870 LG V20 LG G5 H860 Motorola Motorola Moto Z Samsung Samsung Galaxy Note 3 Samsung Galaxy S6 Samsung Galaxy J5 Samsung Galaxy S6 edge + Samsung Galaxy Note 4 (SM-G9287) Samsung Galaxy -
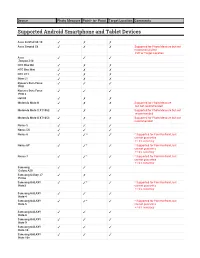
List of Supported Devices
Device Photo Measure Point- to- Point Target Location Comments Supported Android Smartphone and Tablet Devices Asus ZenPad 3S 10 ✓ ✗ ✗ Asus Zenpad Z8 ✓ ✗ ✗ Supported for Photo Measure but not recommended for P2P or Target Location Asus ✓ ✓ ✓ Zenpad Z10 HTC One M8 ✓ ✗ ✗ HTC One Mini ✓ ✗ ✗ HTC U11 ✓ ✗ ✗ iNew L1 ✓ ✗ ✗ Kyocera Dura Force ✓ ✓ ✓ PRO Kyocera Dura Force ✓ ✓ ✓ PRO 2 LGV20 ✓ ✗ ✗ Motorola Moto G ✓ ✗ ✗ Supported for Photo Measure but not recommended Motorola Moto X XT1052 ✓ ✗ ✗ Supported for Photo Measure but not recommended Motorola Moto X XT1053 ✓ ✗ ✗ Supported for Photo Measure but not recommended Nexus 5 ✓ ✓ ✓ Nexus 5X ✓ ✓ ✓ Nexus 6 ✓ ✓* ✓ * Supported for Point-to-Point, but cannot guarantee +/-3% accuracy Nexus 6P ✓ ✓* ✓ * Supported for Point-to-Point, but cannot guarantee +/-3% accuracy Nexus 7 ✓ ✓* ✓ * Supported for Point-to-Point, but cannot guarantee +/-3% accuracy Samsung ✓ ✓ ✓ Galaxy A20 Samsung Galaxy J7 ✓ ✗ ✓ Prime Samsung GALAXY ✓ ✓* ✓ * Supported for Point-to-Point, but Note3 cannot guarantee +/-3% accuracy Samsung GALAXY ✓ ✓ ✓ Note 4 Samsung GALAXY ✓ ✓* ✓ * Supported for Point-to-Point, but Note 5 cannot guarantee +/-3% accuracy Samsung GALAXY ✓ ✓ ✓ Note 8 Samsung GALAXY ✓ ✓ ✓ Note 9 Samsung GALAXY ✓ ✓ ✓ Note 10 Samsung GALAXY ✓ ✓ ✓ Note 10+ Device Photo Measure Point- to- Point Target Location Comments Samsung GALAXY ✓ ✓ ✓ Note 10+ 5G Samsung GALAXY ✓ ✓ ✓ Note 20 Samsung GALAXY ✓ ✓ ✓ Note 20 5G Samsung GALAXY ✓ ✗ ✗ Supported for Photo Measure but not Tab 4 (old) recommended Samsung GALAXY ✓ ✗ ✓ Supported for Photo -

Evaluating Bluetooth Low Energy for Iot
Evaluating Bluetooth Low Energy for IoT Jonathan Furst¨ ∗, Kaifei Cheny, Hyung-Sin Kimy and Philippe Bonnet∗ ∗IT University of Copenhagen, yUC Berkeley [email protected], fkaifei, [email protected], [email protected] Abstract—Bluetooth Low Energy (BLE) is the short-range, While others have experienced similar phenomena [7], we single-hop protocol of choice for the edge of the IoT. Despite could not find systematic studies of BLE characteristics on its growing significance for phone-to-peripheral communication, smartphones in the literature. Most existing work focus on the BLE’s smartphone system performance characteristics are not well understood. As others, we experienced mixed erratic perfor- BLE performance of BLE SoCs [8], [9], [10], [11], [12], with- mance results in our BLE based smartphone-centric applications. out quantifying BLE performance in a smartphone context. In these applications, developers can only access low-level func- However, smartphones-peripheral systems represent a large set tionalities through multiple layers of OS and hardware abstrac- of BLE applications in the wild [1], [2], [3]. In our work, tions. We propose an experimental framework for such systems, we thus focus on two questions: (1) Can we show systematic with which we perform experiments on a variety of modern smartphones. Our evaluation characterizes existing devices and variations in BLE application behavior across smartphone gives new insight about peripheral parameters settings. We show models? (2) Can we define a model to characterize BLE that BLE performances vary significantly in non-trivial ways, performance on smartphones, that could inform application depending on SoC and OS with a vast impact on applications. -

Mobile- H2 2018
Barometer of mobile Internet connections in Turkey Publication of August 12 th , 2019 H2 2018 – H1 2019 nPerf is a trademark owned by nPerf SAS, 87 rue de Sèze 69006 LYON – France. Contents 1 Summary of results ...................................................................................................................... 2 1.1 Summary table and nPerf score, all technologies combined .............................................. 2 1.2 Our analysis ........................................................................................................................... 3 2 Overall results 2G/3G/4G ............................................................................................................. 3 2.1 Data amount and distribution ............................................................................................... 3 2.2 Success rate 2G/3G/4G ........................................................................................................ 4 2.3 Download speed 2G/3G/4G .................................................................................................. 4 2.4 Upload speed 2G/3G/4G ....................................................................................................... 6 2.5 Latency 2G/3G/4G ................................................................................................................ 7 2.6 Browsing test 2G/3G/4G....................................................................................................... 8 2.7 Streaming test 2G/3G/4G .................................................................................................... -

Nexus 5 Headphone Jack Replacement Guide ID: 73195 - Draft: 2020-02-21
Nexus 5 Headphone Jack Replacement Guide ID: 73195 - Draft: 2020-02-21 Nexus 5 Headphone Jack Replacement Use this guide to replace the headphone jack on your Nexus 5. Written By: anonymous This document was generated on 2021-01-21 06:40:11 AM (MST). © iFixit — CC BY-NC-SA www.iFixit.com Page 1 of 12 Nexus 5 Headphone Jack Replacement Guide ID: 73195 - Draft: 2020-02-21 INTRODUCTION I bought a kit to fix this component. The kit contained the headphone jack itself, a Phillips #00 Screwdriver and an Opening Tool. I made do with just the above tools, but my instructions use the ideal tools should you have them. I also replaced the rear camera at the same time, by following the excellent guide for that component. TOOLS: PARTS: SIM Card Eject Tool (1) Nexus 5 Rear Panel (1) iFixit Opening Tools (1) Nexus 5 Midframe (1) Phillips #00 Screwdriver (1) Nexus 5 SIM Card Tray (1) Spudger (1) Google Nexus 5 Replacement Battery (1) Tweezers (1) Google Nexus 5 (LG-D820) Motherboard iFixit Opening Picks set of 6 (1) (1) Nexus 5 Antenna Cables (1) Nexus 5 Headphone Jack Assembly (1) This document was generated on 2021-01-21 06:40:11 AM (MST). © iFixit — CC BY-NC-SA www.iFixit.com Page 2 of 12 Nexus 5 Headphone Jack Replacement Guide ID: 73195 - Draft: 2020-02-21 Step 1 — SIM Card Power off the device by holding the power button until the "Power Off" popup appears. Tap the popup and wait for the device to turn off. -

Android Supported Devices
Android Supported Devices Mobile Track Call Notifications Call Notifications Text Notifications Music Control Make Model OS Required Requires Google Play Requires OS 4.3+ Requires OS 4.3+ Requires OS 4.3+ Requires OS 4.4+ Services (Charge, Charge HR) (Surge) (Surge) (Surge) Samsung Galaxy S3 — ✓ ✓ ✓ — Galaxy S3 Mini (excluding Samsung — — “Value Edition” GT-i8200) ✓ ✓ ✓ Samsung Galaxy S4 — ✓ ✓ ✓ ✓ Samsung Galaxy S4 mini — ✓ ✓ ✓ ✓ Samsung Galaxy S4 Active — ✓ ✓ ✓ ✓ Samsung Galaxy S4 Zoom — ✓ ✓ ✓ ✓ Samsung Galaxy S5 — ✓ ✓ ✓ ✓ Samsung Galaxy S5 Mini — ✓ ✓ ✓ ✓ Samsung Galaxy S6 — ✓ ✓ ✓ ✓ Samsung Galaxy S6 Edge — ✓ ✓ ✓ ✓ Samsung Galaxy Note II — ✓ ✓ ✓ ✓ Samsung Galaxy Note II Duos — ✓ ✓ ✓ ✓ Samsung Galaxy Young 2 Duos — ✓ ✓ ✓ ✓ Samsung Galaxy Note III — ✓ ✓ ✓ ✓ Samsung Galaxy Note III Round — ✓ ✓ ✓ ✓ Samsung Galaxy Note 4 — ✓ ✓ ✓ ✓ Samsung Galaxy Note Edge — ✓ ✓ ✓ ✓ Samsung Galaxy Note 8.0 — ✓ ✓ ✓ ✓ Samsung Galaxy Note 10.1 — ✓ ✓ ✓ ✓ Samsung Galaxy Rugby Pro — ✓ ✓ ✓ ✓ Samsung Galaxy Mega — ✓ ✓ ✓ ✓ Samsung Galaxy S5 Active — ✓ ✓ ✓ ✓ Samsung Galaxy S5 Sport — ✓ ✓ ✓ ✓ Fitbit | Android Supported Devices Page 1 of 7 Android Supported Devices Mobile Track Call Notifications Call Notifications Text Notifications Music Control Make Model OS Required Requires Google Play Requires OS 4.3+ Requires OS 4.3+ Requires OS 4.3+ Requires OS 4.4+ Services (Charge, Charge HR) (Surge) (Surge) (Surge) Samsung Galaxy S3 Neo — ✓ ✓ ✓ — Samsung Galaxy S3 Slim — ✓ ✓ ✓ — Samsung Galaxy Ace Style — ✓ ✓ ✓ ✓ Samsung Galaxy Tab 3 — ✓ ✓ ✓ ✓ Samsung Galaxy Tab S — ✓ ✓ ✓ ✓ -

Device Compatibility APPLE™ COMPATIBILITY
Device Compatibility Android devices running the required software must also have a microUSB port and support powered USB OTG. iOS devices running the required software must be equipped with a lightning connector port. Visit the Help Center for more detailed explanations of Android requirements and iOS requirements. APPLE™ COMPATIBILITY Works with and tested against: iPhone XS Max iPhone XS iPhone XR iPhone X iPhone 8 Plus iPhone 8 iPhone 7+ iPhone 7 iPhone SE iPhone 5 iPhone 5c iPhone 5s iPhone 6 iPhone 6+ iPhone 6s iPhone 6s+ iPhone SE iPod Touch 5th Generation Works with, but not optimized for: iPad Mini (all versions) iPad Air iPad 4th Generation Not compatible with: iPhone 4s or lower iPad 3 or lower iPod Touch 4 or lower iPad Pro ANDROID™ COMPATIBILITY Works with and tested against: Motorola Moto X Motorola Moto G Samsung Galaxy S3 Samsung Galaxy S4 Samsung Galaxy S5 (except some running 5.1.1*) Samsung Galaxy S6 Samsung Galaxy S6 Edge Samsung Galaxy S7 Samsung Galaxy S7 Edge Samsung Galaxy Note 2 Samsung Galaxy Note 3 Samsung Galaxy Note 4 Samsung Galaxy Note 8 Samsung Galaxy Note Edge HTC One Mini 2 (requires adapter) HTC One A9 (requires adapter) HTC One M8 (requires adapter) HTC One M9 (requires adapter) HTC Desire EYE (requires adapter) HTC Desire 820 (requires adapter) Google Nexus 5 (requires adapter) Google Nexus 6 (requires reversible adapter or cable) Google Nexus 5x (requires USB-C adapter) Google Nexus 6p (requires USB-C adapter) Google Pixel (Requires USB-C adapter)