Face Off LAW ENFORCEMENT USE of FACE RECOGNITION TECHNOLOGY
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Indiana Jane’ Pens Another Florence Book / Indianapolis Star
‘Indiana Jane’ pens another Florence Book / Indianapolis Star 'Indiana Jane' pens another Florence book It would be difficult to find someone who loves Florence, Italy, more than Indianapolis philanthropist Jane Fortune . Fortune lives there with her partner, Bob Hesse , about four months out of the year. As evidence of her soft spot for the city, she has done everything from penning “To Florence con Amore,” a 2007 book about the art-filled city’s best behind- the-scenes places, to starting a foundation aimed at restoring and preserving Florentine female artists’ work — pieces Fortune says have been largely overlooked. She added to that list last month when her latest book came out: “Invisible Women: Forgotten Artists of Florence,” an art history book that spotlights the work of women. Fortune is known as “Indiana Jane” for her efforts in the Italian city, where her culture column shows up in “The Florentine,” a biweekly publication for English speakers. In Indianapolis, she is better known for her recent support of the inaugural performance of the Indianapolis City Ballet. “Invisible Women,” ($28, The Florentine Press) made its debut in Indianapolis this month. To celebrate, Fortune’s local friends (and Hesse, to whom the book is dedicated) gathered for a book- signing party Dec. 8 at the Indianapolis Museum of Art. Fortune explained that the proceeds of both books are channeled to her foundation, which helps advance Italian female artists. The IMA gift store carries both of Fortune’s books, and they can also be ordered online at shop.imamuseum.org. Equal access to holiday fun The Italianate home of Ken Ramsay and Joe Everhart on the Old Northside created some holiday magic for Indiana Equality this month. -

Semifinalists to Face Off for Beef Loving Texans' Best Butcher in Texas
FOR IMMEDIATE RELEASE Contact: Sarah Flores, Hahn Public for Texas Beef Council 512-344-2045 [email protected] SEMIFINALISTS TO FACE OFF FOR BEEF LOVING TEXANS’ BEST BUTCHER IN TEXAS Texas Beef Council Selects Competitors to Battle for Coveted Finalist Spots AUSTIN, Texas – Feb. 23, 2017 –Texas Beef Council announces the top Semifinalists who will move on to compete in the Beef Loving Texans’ Best Butcher in Texas regional competition. The challenge, which pits butchers from across Texas against each other for the chance to win cash prizes and the esteemed title of Beef Loving Texans’ Best Butcher in Texas, has brought some of the state’s most talented butchers together – representing an art form that has been important to Texas’ cultural heritage. Regional semifinal rounds will be held throughout the state in Houston on March 4, Dallas on March 18 and San Antonio on April 1. In each city, Semifinalists will partake in a three-part challenge, which tests competitors on cut identification, along with their skills to cut to order and cut beef for retail merchandising. Each competitor will be equipped with Victorinox Swiss Army boning knives, a breaking knife, a cut resistant glove, a steel and a knife roll, to ensure everyone starts on an even playing field. Competitors will receive top marks based on their technique, creativity, presentation and consumer interaction. With culinary influencer/personality Jess Pryles emceeing, top industry professionals and culinary experts will weigh in in each region to determine the top three competitors who will move on to the final round at the Austin Food + Wine Festival on April 29. -

Political History of Nevada: Chapter 1
Political History of Nevada Chapter 1 Politics in Nevada, Circa 2016 37 CHAPTER 1: POLITICS IN NEVADA, CIRCA 2016 Nevada: A Brief Historiography By EMERSON MARCUS in Nevada Politics State Historian, Nevada National Guard Th e Political History of Nevada is the quintessential reference book of Nevada elections and past public servants of this State. Journalists, authors, politicians, and historians have used this offi cial reference for a variety of questions. In 1910, the Nevada Secretary of State’s Offi ce fi rst compiled the data. Th e Offi ce updated the data 30 years later in 1940 “to meet a very defi nite and increasing interest in the political history of Nevada,” and has periodically updated it since. Th is is the fi rst edition following the Silver State’s sesquicentennial, and the State’s yearlong celebration of 150 years of Statehood in 2014. But this brief article will look to examine something other than political data. It’s more about the body of historical work concerning the subject of Nevada’s political history—a brief historiography. A short list of its contributors includes Dan De Quille and Mark Twain; Sam Davis and James Scrugham; Jeanne Wier and Anne Martin; Richard Lillard and Gilman Ostrander; Mary Ellen Glass and Effi e Mona Mack; Russell Elliott and James Hulse; William Rowley and Michael Green. Th eir works standout as essential secondary sources of Nevada history. For instance, Twain’s Roughing It (1872), De Quille’s Big Bonanza (1876) and Eliot Lord’s Comstock Mining & Mines (1883) off er an in-depth and anecdote-rich— whether fact or fi ction—glance into early Nevada and its mining camp way of life. -

Northern Conference Playoff Teams
Game Notes brought to you by: TONIGHT’S GAME – The Colorado Eagles take on the Stockton Heat tonight for just the second time in team history. THE SEASON SERIES – The Heat lead the season series 1-0 after Stockton’s 5-4 OT victory over Colorado last night. The Eagles will face Stockton a total of eight times during the regular season, with four of those eight games set to take place at the Budweiser Events Center. THE ALL-TIME SERIES – Tonight marks the second meeting between the Eagles and Heat, both teams are members of the AHL’s Pacific Division of the Western Conference. EAGLES’ LAST GAME (11/13) – The Stockton Heat scored with 1:22 remaining in regulation and netted the game-winner 2:48 into overtime to rally for a 5-4 victory over the Colorado Eagles on Tuesday. Eagles forward Logan O’Connor scored a pair of goals, while fellow forward Martin Kaut registered a three-point night in the loss. Colorado scored two shorthanded goals in the contest, giving the team at least one shorthanded goal in each of their last three contests. HEAT’S LAST GAME (11/13) – Same as above. LAST MEETING (11/13) – Same as above. UP NEXT FOR THE EAGLES –Colorado travels to face the Bakersfield Condors on Saturday, November 17th at 8:00pm MT at Rabobank Arena in Bakersfield, California. UP NEXT FOR THE HEAT – Stockton returns home to host the Tucson Roadrunners on Friday, November 16th. **Tune in to 96.9 in the arena to listen to the “Voice of the Eagles” Kevin McGlue’s live play-by-play! ---------------------------------NOTES & NUMBERS--------------------------------- FIRST GLANCE- This week’s games between Colorado and Stockton will be the first-ever meetings in team history. -
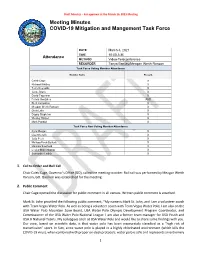
Agenda Item #3 Draft COVID-19 Mitigation and Management Task
Draft Minutes – For approval at the March 16, 2021 Meeting Meeting Minutes COVID-19 Mitigation and Mangement Task Force DATE March 4, 2021 TIME 10:00 A.M. Attendance METHOD Video-Teleconference RECORDER Tanya Benitez/Meagan Werth Ranson Task Force Voting Member Attendance Member Name Present Caleb Cage X Richard Whitley X Terry Reynolds X Jaime Black X David Fogerson X Felicia Gonzales ABS Brett Compston X Meagan Werth Ranson X Chris Lake X Dagny Stapleton X Wesley Harper X Mark Pandori X Task Force Non-Voting Member Attendance Kyra Morgan X Lisa Sherych X Julia Peek X Melissa Peek-Bullock X Malinda Southard X Lesley Mohlenkamp X Samantha Ladich X 1. Call to Order and Roll Call Chair Caleb Cage, Governor’s Office (GO), called the meeting to order. Roll call was performed by Meagan Werth Ranson, GO. Quorum was established for the meeting. 2. Public Comment Chair Cage opened the discussion for public comment in all venues. Written public comment is attached. Mark St. John provided the following public comment, “My name is Mark St. John, and I am a volunteer coach with Team Vegas Water Polo. As well as being a volunteer coach with Team Vegas Water Polo; I am also on the USA Water Polo Mountain Zone Board, USA Water Polo Olympic Development Program Coordinator, and Commissioner of the USA Water Polo National League. I am also a former team manager for USA Youth and USA Jr National Teams. My colleagues and I at USA Water Polo and would like to share some findings with you. -

Boys Lacrosse, Girls Lacrosse and Girls Soccer at All Times
OVERVIEW OF IMPORTANT RETURN-TO-PLAY TOPICS This document was updated on March 24, 2021. Over time, this document will change. Please check back frequently for updates. The first four pages of this document feature easy-to-understand overviews of Spring 2020-21 COVID-docu- ment-related guidelines. For more detailed answers, read this entire packet. Spring athletics will not be risk-free, but by following the guidance in this document, we all can help mitigate those risks. You should also consider your interactions outside of sports during this season in order to limit the potential for exposure in other portions of your daily routine. PROTOCOL FOR POSITIVE CASES: A detailed and more complete version of these protocols can be found on page 4 of this document (“What to Do When Someone Gets Sick”). 1. Contact health department and follow guidance. 2. Close contacts MAY have to quarantine for 14 days; follow health department guidance. “Close contact” is de- fined as someone who was within six feet of an infected person for a cumulative total of 15 minutes or more over a 24-hour period, starting from two days before illness onset. 3. Notify all schools, families and officials involved without identifying the person involved. 4. Students, coaches, officials and others at the event but NOT in close contact should be closely monitored for symptoms and may not need testing. Follow health department guidance. 5. Clean the area. FACE MASKS: The March 2, 2021 order issued by the Michigan Department of Health and Human Services (MDHHS), as amended, mandates that masks are to be worn during practice and competition for outdoor contact sports. -
![Archons (Commanders) [NOTICE: They Are NOT Anlien Parasites], and Then, in a Mirror Image of the Great Emanations of the Pleroma, Hundreds of Lesser Angels](https://docslib.b-cdn.net/cover/8862/archons-commanders-notice-they-are-not-anlien-parasites-and-then-in-a-mirror-image-of-the-great-emanations-of-the-pleroma-hundreds-of-lesser-angels-438862.webp)
Archons (Commanders) [NOTICE: They Are NOT Anlien Parasites], and Then, in a Mirror Image of the Great Emanations of the Pleroma, Hundreds of Lesser Angels
A R C H O N S HIDDEN RULERS THROUGH THE AGES A R C H O N S HIDDEN RULERS THROUGH THE AGES WATCH THIS IMPORTANT VIDEO UFOs, Aliens, and the Question of Contact MUST-SEE THE OCCULT REASON FOR PSYCHOPATHY Organic Portals: Aliens and Psychopaths KNOWLEDGE THROUGH GNOSIS Boris Mouravieff - GNOSIS IN THE BEGINNING ...1 The Gnostic core belief was a strong dualism: that the world of matter was deadening and inferior to a remote nonphysical home, to which an interior divine spark in most humans aspired to return after death. This led them to an absorption with the Jewish creation myths in Genesis, which they obsessively reinterpreted to formulate allegorical explanations of how humans ended up trapped in the world of matter. The basic Gnostic story, which varied in details from teacher to teacher, was this: In the beginning there was an unknowable, immaterial, and invisible God, sometimes called the Father of All and sometimes by other names. “He” was neither male nor female, and was composed of an implicitly finite amount of a living nonphysical substance. Surrounding this God was a great empty region called the Pleroma (the fullness). Beyond the Pleroma lay empty space. The God acted to fill the Pleroma through a series of emanations, a squeezing off of small portions of his/its nonphysical energetic divine material. In most accounts there are thirty emanations in fifteen complementary pairs, each getting slightly less of the divine material and therefore being slightly weaker. The emanations are called Aeons (eternities) and are mostly named personifications in Greek of abstract ideas. -

2005-04-07.Pdf
SI3 f'l *********«CAR-RT LOT»*C015 t 3 Wl SIFIELI) MEMORIAL LIBRARY 550 fc BROAD ST WESTHEID NJ 07090-2116 07090211650 IWMaWBHWBlgl 3b flopiilos. ilon abmis. tkrbrmmus LSPS MMNI2II I’ublKhi^l t im Ihurvlm Mint Vplrm hrr .3, UNO OUR 115th YEAR - ISSUE NO. 14-2005 Thursday, April 7,2005 (908) 232-4407 Periodical - Postage Paid at Westfield, N J. ww w .goleader.com press («' goieader.com SIXTY CENTS Five BOE Hopefuls Face-Off In Candidates Night Forum By El) COONEY Steven Dorry noted that "excellence more, involvement with the commu Specialty Written for The Westfield tedder comes at a price." and that “we have nity. WESTFIELD - All five candi to pay teachers what they’re worth." Ms. Ormsby-Cary suggested a dates running for seats on the He also said that teacher salaries policy be put in place mandating that Westfield Board of Education (BOE) fixed by the collective bargaining each guidance counselor at Westfield participated in Candidates Night at agreement currently in place, coupled High School take at least three trips a Westfield High School last Wednes w ith the increasing cost of special year to different universities in order day. education and insurance for teachers to foster relationships advantageous The event, hosted by the Westfield and staff, make it difficult to keep to Westfield students seeking admis League of Women Voters, gave the spending down. sion. candidates an opportunity to answer Gary McCready, another challenger Ms. Ormsby-Cary. who has expe questions on several important issues for one of the three available seats on rience in the field of public relations, sutrounding this year's election. -

State Tournament Pairings Announced for Boys Basketball Indiana Pacers, Indiana Fever Are Presenting Sponsors of State Tournament
February 21, 2016 State Tournament Pairings Announced for Boys Basketball Indiana Pacers, Indiana Fever Are Presenting Sponsors of State Tournament Three hundred ninety‐eight (398) teams were drawn today and placed into brackets for the 106th Annual IHSAA Boys Basketball State Tournament presented by the Indiana Pacers and Indiana Fever. This is the third year that both of the state’s professional basketball franchises have been presenting sponsors of the boys and girls high school state tournaments. Sectional games are scheduled to begin Tuesday, March 1, and run through Saturday, March 5, with the regional round slated for March 12 and semi‐ states on March 19. The four state championship games that make up the state finals will be played at Bankers Life Fieldhouse in Indianapolis on Saturday, March 26. New Albany is the top‐ranked team in both the Associated Press Class 4A poll and the single class poll from the Indiana Basketball Coaches Association. The Bulldogs will begin their quest for a third consecutive sectional championship after earning a first round bye. They’ll await the Seymour‐New Albany winner in Sectional 15 at Seymour. Class 3A’s No. 1 team Griffith, last year’s state runner‐up, will host Hammond Clark in Sectional 17. In Class 2A, top‐ranked Lapel will play host to Muncie Burris in the six‐team Sectional 42 opener. Liberty Christian, the No. 1 team in the Class A poll, will begin its charge toward a fifth consecutive sectional title when it meets tournament newcomer Anderson Preparatory Academy in Sectional 55 at Wes‐Del. -

Baseball Celebrates Centennial
Volume LXXXIII, Issue XXVII St. Louis University High School | Friday, May 3, 2019 sluh.org/prepnews Local media Six seniors make final decisions in 100 years in the gets lacrosse pursuit of collegiate athletics making: Baseball story wrong celebrates centennial BY Justin Koesterer BY Paul Gillam SPORTS EDITOR time. To say that I was a little EDITOR IN CHIEF overwhelmed with the night fter Easter break, an as- eaturing a ceremony hon- would be an understatement. Asistant coach of the St. Foring Steve Nicollerat, It was one of the nicest nights Louis U. High varsity lacrosse SLUH baseball coach of 40 of my life,” said Nicollerat. team was dismissed from the years, the SLUH baseball pro- Around 6:30, the guests program on grounds of con- gram celebrated 100 years of were called down to take their suming alcohol with play- rich history and storied tradi- places at tables set up at the ers at an off campus unof- tion in the baseball centennial north end of the lower level of ficial team event. On April event held at SLUH on Satur- the Field House. Dinner was 25, more than a week after day night. served, and then the ceremo- the separation, Fox 2 News The event was held in ny began. and Channel 11 published a the Danis Field House last The ceremony began story containing what many Saturday evening, and hosted with a panel of speakers who players and SLUH admin- about 100 people—teachers, discussed SLUH baseball istrators called a false nar- Jesuits, personal friends, and in the 1950s, ’60s, ’70s, ’80s rative of the incident. -

Model Sign Ordinance a Comprehensive, Content-Neutral Approach to Local Sign Control
Prepared by the Montgomery County Planning Commission A comprehensive, content-neutral approach to local sign control NewModel town Sign mixed Ordinance use district Montgomery County Commissioners Josh Shapiro, Chair Leslie S. Richards, Vice Chair Bruce L. Castor, Jr. MMontgomeryontgomery County Planning Commission Board Marc D. Jonas, Esq., Chair Dulcie F. Flaharty, Vice Chair Robert E. Blue, Jr. Jill Blumhardt Scott Exley Roy Rodriguez, Jr. Charles J. Tornetta Pastor John West Rachel Yoka Jody L. Holton, AICP, Executive Director Model Sign Ordinance A comprehensive, content-neutral approach to local sign control Prepared by the Montgomery County Planning Commission 2014 introduction ii model sign ordinance Table of Contents Introduction ........................................................................................................................................ vii Hot Topics in Signage Reference Guide ................................................................................ix Part 1: Purpose of Signs ............................................................................................................. 1 Part 2: Community Impact of Signs Safety Issues .......................................................................................................................... 9 Public Welfare and Aesthetics Issues .................................................................................. 10 Environmental Issues .......................................................................................................... -

Hockey Rules
HOCKEY RULES // QUICK LINKS Player Eligibility // Game Play // Golden Rule // General Policies // PLAYER ELIGIBILITY 1. All Players must be at least 21 years of age and have current, adequate health insurance. 2. All players must be properly registered on a team during the season for which they are playing. a. If a player is registered on more than one team within the league, they may only play for one team in the playoffs. b. All players must agree to the Fray Liability Waiver as described in the Fray Terms and Conditions section of Player Registration. 3. Any use of an ineligible player will result in a forfeit. // GAME PLAY 1. Each game will consist of two 20-minute halves with a 4-minute half time between periods. Game times may vary based on a specific location. Copyright 2020 // United Fray Last Updated // January 2020 a. The clock will run continuously during the first half and all but the final two minutes of the second half. During this time, the clock will stop only on an injury, time out, or penalty shot. b. During the final two minutes of the second half, the clock will stop on all whistles (only if the margin is 2 goals or fewer). c. Teams will switch goals at the end of each period. 2. Time Outs: Each team will receive one time out per game. Unused time outs do not carry over into subsequent periods. Time outs can only be called by a captain or alternate captain during a stoppage of play. Time outs are not permitted during overtime.