Team Software Process for Secure Systems Development James W
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Automated Software Process Performance Analysis and Improvement Recommendation
FACULDADE DE ENGENHARIA DA UNIVERSIDADE DO PORTO Automated Software Process Performance Analysis and Improvement Recommendation Mushtaq Raza MAP-i Doctoral Program in Computer Science Supervisor: João Pascoal Faria June 27, 2017 c Mushtaq Raza, 2017 Automated Software Process Performance Analysis and Improvement Recommendation Mushtaq Raza MAP-i Doctoral Program in Computer Science Dissertation submitted to the Faculty of Engineering, University of Porto in partial fulfillment of the requirements for the degree of Doctor of Philosophy Approved by: President: Dr. Eugénio da Costa Oliveira Referee: Dr. António Manuel Ferreira Rito da Silva Referee: Dr. Paulo Jorge dos Santos Gonçalves Ferreira Referee: Dr. Fernando Manuel Pereira da Costa Brito e Abreu Referee: Dr. Ademar Manuel Teixeira de Aguiar Supervisor: Dr. João Pascoal Faria June 27, 2017 Abstract Software development processes can generate significant amounts of data that can be periodically analyzed to identify performance problems, determine their root causes and devise improvement actions. However, there is a lack of methods and tools for helping in that kind of analysis. Con- ducting the analysis manually is challenging because of the potentially large amount of data to analyze, the effort and expertise required and the lack of benchmarks for comparison. Hence, the goal of this dissertation is to develop methods, models and tools for automating the analysis of process performance data and identifying and ranking performance problems and their root causes, reducing effort and errors and improving user satisfaction as compared to previous approaches. The main contributions of the dissertation are a novel method for process performance analysis and improvement recommendation (the ProcessPAIR method), a support tool (the ProcessPAIR tool), and a performance model for instantiating ProcessPAIR for the Personal Software Process (the ProcessPAIR model for the PSP). -

Stephan Goericke Editor the Future of Software Quality Assurance the Future of Software Quality Assurance Stephan Goericke Editor
Stephan Goericke Editor The Future of Software Quality Assurance The Future of Software Quality Assurance Stephan Goericke Editor The Future of Software Quality Assurance Editor Stephan Goericke iSQI GmbH Potsdam Germany Translated from the Dutch Original book: ‘AGILE’, © 2018, Rini van Solingen & Manage- ment Impact – translation by tolingo GmbH, © 2019, Rini van Solingen ISBN 978-3-030-29508-0 ISBN 978-3-030-29509-7 (eBook) https://doi.org/10.1007/978-3-030-29509-7 This book is an open access publication. © The Editor(s) (if applicable) and the Author(s) 2020 Open Access This book is licensed under the terms of the Creative Commons Attribution 4.0 Inter- national License (http://creativecommons.org/licenses/by/4.0/), which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence and indicate if changes were made. The images or other third party material in this book are included in the book’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the book’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. The use of general descriptive names, registered names, trademarks, service marks, etc. in this publication does not imply, even in the absence of a specific statement, that such names are exempt from the relevant protective laws and regulations and therefore free for general use. -

Week Assignment
https://www.halvorsen.blog Week Assignment Project Kick-off & Planning Hans-Petter Halvorsen All Documents, Code, etc. should be uploaded to Teams/Azure DevOps! Week Assignment 1. Project Start: Define Teams & Roles. Make CV 2. Create a Software Development Plan (SDP) 3. Team Brainstorming (What/How?) 4. Development Tools – Install necessary Software – Get Started with “Azure DevOps”* *Previously Visual Studio Team Services (VSTS) See Next Slides for more details... Textbooks (Topics this Week) Software Engineering, Ian Sommerville Ch.1: Introduction Ch.2: Software Processes Ch.23: Project Planning (with SDP example) Video: What is Software Engineering and Why do we need it? https://youtu.be/R3NzTt0BTWE Video: Introduction to Software Engineering (10 Questions to Introduce Software Engineering) https://youtu.be/gi5kxGslkNc Video: FundaMental Activities of Software Engineering https://youtu.be/Z2no7DxDWRI Office Hours: Tirsdager 10:15-14:00 “The Office” Fredager: 10:15-14:00 Lunch 11:30-12:15 Det er meningen at dere skal være tilstede på kontoret i kontortiden – selv om ikke “sjefene” (les «lærerne») er der. Dvs. det er ikke behov for å tilkalle lærerne hvis de ikke C-139a skulle dukke opp hver gang. Når dere ankommer “kontoret” (C-139a), begynner dere å jobbe videre med prosjektet. Dere trenger ikke å sitte å vente på at dere skal få beskjed Team 2 om hva dere skal gjøre, da dere er selvstendige Team som har ansvaret for hvert deres prosjekt og fremdriften av dette. Slik er det i arbeidslivet, og slik er det her. Team 1 Management Team 3 Dere er Midlertidig ansatt (5 Måneders prøvetid) soM systemutviklere i firmaet “USN Software AS”. -

Agile Project Management with Kanban
Praise for Agile Project Management with Kanban “I have been fortunate to work closely with Eric for many years. In that time he has been one of the most productive, consistent, and efficient engineering leaders at Xbox. His philosophy and approach to software engineering are truly successful.” —Kareem Choudhry, Partner Director of Software Engineering for Xbox “Eric easily explains why Kanban has proven itself as a useful method for managing and tracking complicated work. Don’t expect this book to be an overview, however. Eric channels his deep understanding and experiences using Kanban at Microsoft to help you identify and avoid many of the common difficulties and risks when implementing Kanban.” —Richard Hundhausen, President, Accentient Inc. “Learning how Xbox uses Kanban on large-scale development of their platform lends real credibility to the validity of the method. Eric Brechner is a hands-on software development management practitioner who tells it like it is—solid, practical, pragmatic advice from someone who does it for a living.” —David J. Anderson, Chairman, Lean Kanban Inc. “As a software development coach, I continuously search for the perfect reference to pragmatically apply Kanban for continuous software delivery. Finally, my search is over.” —James Waletzky, Partner, Crosslake Technologies “Kanban has been incredibly effective at helping our team in Xbox manage shifting priorities and requirements in a very demanding environment. The concepts covered in Agile Project Management with Kanban give us the framework to process our work on a daily basis to give our customers the high- quality results they deserve.” —Doug Thompson, Principal Program Manager, Xbox Engineering “An exceptional book for those who want to deliver software with high quality, predictability, and flexibility. -
UNIT-I: Software Engineering & Process Models
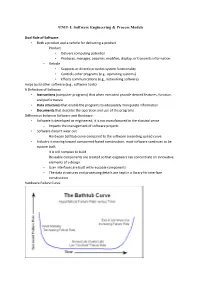
UNIT-I: Software Engineering & Process Models Dual Role of Software • Both a product and a vehicle for delivering a product – Product • Delivers computing potential • Produces, manages, acquires, modifies, display, or transmits information – Vehicle • Supports or directly provides system functionality • Controls other programs (e.g., operating systems) • Effects communications (e.g., networking software) Helps build other software (e.g., software tools) A Definition of Software • Instructions (computer programs) that when executed provide desired features, function, and performance • Data structures that enable the programs to adequately manipulate information • Documents that describe the operation and use of the programs Differences between Software and Hardware • Software is developed or engineered; it is not manufactured in the classical sense – Impacts the management of software projects • Software doesn't wear out – Hardware bathtub curve compared to the software ascending spiked curve • Industry is moving toward component-based construction, most software continues to be custom built – it is still complex to build – Reusable components are created so that engineers can concentrate on innovative elements of a design – User interfaces are built with reusable components – The data structures and processing details are kept in a library for interface construction Hardware Failure Curve Software Failure Curve Changing Nature of Software • System software • Application software • Engineering/scientific software • Embedded software • -

TSP Teams Transform Test
TSP Teams Transform Test 2009 QUEST Chicago James D. McHale Software Engineering Institute Carnegie Mellon University Pittsburgh, PA 15213 [email protected] © 2008-09 Carnegie Mellon University A Nightmare Scenario The development team has been promising their “final” code drop for weeks, ever since their latest due date (months after the original date). Your test team has been filling in with clean-up, make-work tasks for most of that time. Every day represents one less day for your test team to complete their work, since the final ship date is not moving. Finally an email arrives handing off the code. All the proper links to the configuration management system are there… But they point to software that doesn’t build. A few more days pass. Another email. The software builds this time. The first day of testing cannot complete due to irrecoverable defects… and management wants you to commit to the original ship date. TSP Teams Transform Test James D. McHale, 2009 QUEST Chicago 2 © 2008-09 Carnegie Mellon University Current Test Reality Requirements, Design, Code, TEST, TEST, TEST, TEST… The focus is on writing code and getting it into test. Most working software developers learned this model implicitly, either in school or on the job, and have no other mental model available. Counting ALL of the testing costs for most modern-day applications still shows that 50% or more of development effort is spent in debugging. Is the purpose of testing to find defects? Or to verify function? TSP Teams Transform Test James D. McHale, 2009 QUEST Chicago 3 © 2008-09 Carnegie Mellon University The Problem With Testing Overload Hardware Configuration failure Good region = tested (shaded) Unknown region = untested (unshaded) Resource Operator contention error Data error TSP Teams Transform Test James D. -

Using Simulation for Understanding and Reproducing Distributed Software Development Processes in the Cloud
Using Simulation for Understanding and Reproducing Distributed Software Development Processes in the Cloud M. Ilaria Lunesu1, Jürgen Münch2, Michele Marchesi3, Marco Kuhrmann4 1Department of Electrical and Electronic Engineering, University of Cagliari, Italy 2Herman Hollerith Center, Böblingen & Reutlingen University, Germany 3Department of Mathematics and Computer Science University of Cagliari, Italy 4Clausthal University of Technology, Institute for Applied Software Systems Engineering, Germany Corresponding Contact: E-Mail: [email protected] © Elsevier 2018. Preprint. This is the author's version of the work. The definite version was accepted in Information and Software Technology journal, Issue assignment pending, The final version is available at https://www.journals.elsevier.com/information-and-software-technology Using Simulation for Understanding and Reproducing Distributed Software Development Processes in the Cloud M. Ilaria Lunesua,,Jurgen¨ Munch¨ b, Michele Marchesic, Marco Kuhrmannd aDepartment of Electrical and Electronic Engineering, University of Cagliari, Italy bHerman Hollerith Center, B¨oblingen & Reutlingen University, Germany cDepartment of Mathematics and Computer Science University of Cagliari, Italy dClausthal University of Technology, Institute for Applied Software Systems Engineering, Germany Abstract Context: Organizations increasingly develop software in a distributed manner. The Cloud provides an environment to create and maintain software-based products and services. Currently, it is unknown which software processes are suited for Cloud-based development and what their e↵ects in specific contexts are. Objective: We aim at better understanding the software process applied to distributed software development using the Cloud as development environment. We further aim at providing an instrument, which helps project managers comparing di↵erent solution approaches and to adapt team processes to improve future project activities and outcomes. -

Software Engineering
SOFTWARE ENGINEERING PERSONAL SOFTWARE PROCESS Personal software process is a software development process by the developers to help themselves improve their performance and efficiency by following a personal disciplined framework that facilitates to plan, design, manage and measure their work. LEARNING OBJECTIVES • To consistently improve the performance, engineers must use well-defined and measured processes. • To produce quality products, engineers must feel personally responsible for the quality. • It costs less to find and fix defects earlier in a process than later. • The right way is always the fastest and cheapest way to do a job. Better Programmer Better programmer can be achieved by, More training ◦ Know how to use tools. ◦ Have seen some problems before. ◦ Know how things fit together. Familiar with language ◦ Object, semaphore, recursion, etc.. Better process Examples of Better Processes Incremental coding ◦ Code a little, test a little ◦ Compare to writing entire program and testing Error prevention versus debugging ◦ Cheaper and easier to prevent than to find bugs Point of Processes The point of processes is to learn from mistakes so that we never make the same mistake twice. It incorporates best practices as something works better than another. A process executes routine standard tasks, when once the task is done it right once and then it is reused. Another major point of having processes is predictability. PERSONAL SOFTWARE PROCESS Personal software process is a software development process by the developers to help themselves improve their performance and efficiency by following a personal disciplined framework that facilitates to plan, design, manage and measures their work. PSP helps you to manage your work & assess/build your talents/skills. -

Software Development Processes: from the Waterfall to the Unified
Software development processes: from the waterfall to the Unified Process Paul Jackson School of Informatics University of Edinburgh The Waterfall Model Image from Wikipedia 2 / 17 Pros, cons and history of the waterfall + better than no process at all { makes clear that requirements must be analysed, software must be tested, etc. − inflexible and unrealistic { in practice, you cannot follow it: e.g., verification will show up problems with requirements capture. − slow and expensive { in an attempt to avoid problems later, end up \gold plating" early phases, e.g., designing something elaborate enough to support the requirements you suspect you've missed, so that functionality for them can be added in coding without revisiting Requirements. Introduced by Winston W. Royce in a 1970 paper as an obviously flawed idea! 3 / 17 Domains of use for waterfall-like models embedded systems : Software must work with specific hardware: Can't change software functionality later. safety critical systems : Safety and security analysis of whole system is needed up front before implementation some very large systems : Allows for independent development of subsystems 4 / 17 Spiral model Barry Boehm. 1988. Cumulative cost 1.Determine Progress 2. Identify and objectives resolve risks Review Requirements Operational plan Prototype 1 Prototype 2 prototype Concept of Concept of operation requirements Detailed Requirements Draft design Development Verification Code plan & Validation Integration Test plan Verification & Validation Test Implementation 4. Plan the Release next iteration 3. Development and Test 5 / 17 Spiral model Successive loops involve more advanced activities: - checking feasibility, - gathering requirements, - design development, - integration and test . Phases of single loop: 1. -

Agile Methodologies in Mission Critical Software Development and Maintenance
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Repositório Aberto da Universidade do Porto FACULDADE DE ENGENHARIA DA UNIVERSIDADE DO PORTO Agile Methodologies in Mission Critical Software Development and Maintenance Antonieta Ponce de Leão Integrated Master in Informatics and Computing Engineering Supervisor: João Carlos Pascoal Faria, Ph.D. June, 2014 © Antonieta Ponce de Leão, 2014 Agile Methodologies in Mission Critical Software Development and Maintenance Maria Antonieta Dias Ponce de Leão e Oliveira Integrated Master in Informatics and Computing Engineering Approved in public trials, by jury: President: Nuno Honório Rodrigues Flores (Ph.D.) External Vowel: Alberto Manuel Rodrigues da Silva (Ph.D.) Supervisor: João Carlos Pascoal Faria (Ph.D.) ____________________________________________________ July, 17th 2014 Abstract Software development depends on people and because of this many issues arise specially regarding consistency and quality. Guaranteeing quality, accurate estimation, and high- performance knowledge workers is not an easy job, and for this there are many methodologies and processes that help. This is not a new issue; many software development companies, somewhere along their lifetime passed through this hassle, and with the study of their victories and defeats as well as worldwide recognized best practices, were able to improve their processes and performance. ALERT, is an example of a software development company that is continuously striving to improve, and their goal, at the moment, is to increase quality, productivity and estimation accuracy. The goal of this project is to identify any exiting issues in the current software development processes and practices at the organization, propose a hybrid and customized proposal of agile and classical methodologies that will help to optimize the performance of the knowledge workers, never forgetting that the productivity of knowledge workers is deeply connected with their motivation. -

The Team Software Processsm (TSPSM)
The Team Software ProcessSM (TSPSM) Watts S. Humphrey November 2000 TECHNICAL REPORT CMU/SEI-2000-TR-023 ESC-TR-2000-023 Pittsburgh, PA 15213-3890 The Team Software ProcessSM (TSPSM) CMU/SEI-2000-TR-023 ESC-TR-2000-023 Watts S. Humphrey November 2000 Team Software Process Initiative Unlimited distribution subject to the copyright. This report was prepared for the SEI Joint Program Office HQ ESC/DIB 5 Eglin Street Hanscom AFB, MA 01731-2116 The ideas and findings in this report should not be construed as an official DoD position. It is published in the interest of scientific and technical information exchange. FOR THE COMMANDER Joanne E. Spriggs Contracting Office Representative This work is sponsored by the U.S. Department of Defense. The Software Engineering Institute is a federally funded research and development center sponsored by the U.S. Department of Defense. Copyright 2000 by Carnegie Mellon University. NO WARRANTY THIS CARNEGIE MELLON UNIVERSITY AND SOFTWARE ENGINEERING INSTITUTE MATERIAL IS FURNISHED ON AN "AS-IS" BASIS. CARNEGIE MELLON UNIVERSITY MAKES NO WARRANTIES OF ANY KIND, EITHER EXPRESSED OR IMPLIED, AS TO ANY MATTER INCLUDING, BUT NOT LIMITED TO, WARRANTY OF FITNESS FOR PURPOSE OR MERCHANTABILITY, EXCLUSIVITY, OR RESULTS OBTAINED FROM USE OF THE MATERIAL. CARNEGIE MELLON UNIVERSITY DOES NOT MAKE ANY WARRANTY OF ANY KIND WITH RESPECT TO FREEDOM FROM PATENT, TRADEMARK, OR COPYRIGHT INFRINGEMENT. Use of any trademarks in this report is not intended in any way to infringe on the rights of the trademark holder. Internal use. Permission to reproduce this document and to prepare derivative works from this document for internal use is granted, provided the copyright and "No Warranty" statements are included with all reproductions and derivative works. -

CMMI with Agile, Lean, Six Sigma, and Everything Else
CMU SEI CERT Division Digital Library Blogs A-Z Index HOME OUR WORK ENGAGE WITH US PRODUCTS & SERVICES LIBRARY NEWS CAREERS ABOUT US BLOG Library Search the Library Browse by Topic Browse by Type CMMI with Agile, Lean, Six Sigma, and Please note that current and future CMMI Everything Else research, training, and information has been transitioned to the CMMI Institute, a wholly- NEWS AT SEI owned subsidiary of Carnegie Mellon University. Author Mike Phillips Related Links News This library item is related to the following area(s) of work: SEI to Co-Sponsor 26th Annual IEEE Software Technology Conference CMMI SEI Cosponsors Agile for Government Summit Process Improvement Training This article was originally published in News at SEI on: January 1, 2008 See more related courses » Events Team Software Process (TSP) Symposium 2014 I repeatedly encounter those seeking the one solution that will solve the problems in their organization. Such a search is often commissioned by a boss who wants the single Nov 3 - 6 answer and a quick fix to the organization’s problems. In this column, I try to describe how to relate some of these answers rather than trying to make any of them—even CMMI—a single solution. The Choices There are a wide range of improvement approaches that are often mentioned as the solution to problems confronting organizations that recognize a need to improve. For years, various standards and modelscaptured principles for process improvement, often called best practices. ISO 15288 and ISO 12207 are likely standards that are familiar to you if you are faced with complex, software intensive systems development.