Topic 2005-06 Infiniband on Demand Secure Routing Protocol Resilient To
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

IBM Websphere Application Server V8 Concepts, Planning, and Design Guide
IBM® WebSphere® Front cover IBM WebSphere Application Server V8 Concepts, Planning, and Design Guide Includes details about end-to-end planning for WebSphere implementations Defines WebSphere concepts and preferred practices Addresses distributed and z/OS platforms Margaret Ticknor Alan Corcoran Balazs Csepregi-Horvath Addison Goering José Pablo Hernandez Julien Limodin Sergio Straessli Pinto ibm.com/redbooks International Technical Support Organization IBM WebSphere Application Server V8 Concepts, Planning, and Design Guide August 2011 SG24-7957-00 Note: Before using this information and the product it supports, read the information in “Notices” on page xiii. First Edition (August 2011) This edition applies to Version 8.0 of IBM WebSphere Application Server. © Copyright International Business Machines Corporation 2011. All rights reserved. Note to U.S. Government Users Restricted Rights -- Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Notices . xiii Trademarks . xiv Preface . .xv The team who wrote this book . .xv Become a published author, too! . xvii Comments welcome. xvii Stay connected to IBM Redbooks publications . xviii Chapter 1. Introduction to WebSphere Application Server V8 . 1 1.1 Java Platform, Enterprise Edition . 2 1.2 Overview of WebSphere Application Server . 3 1.2.1 Application server purpose . 3 1.2.2 Evolving Java application development standards . 4 1.2.3 Enhanced management . 5 1.2.4 Broader integration . 7 1.2.5 Advanced tooling and extensions . 9 1.3 Packaging . 10 1.3.1 WebSphere Application Server - Express V8 . 11 1.3.2 WebSphere Application Server V8 . 11 1.3.3 WebSphere Application Server for Developers V8 . 12 1.3.4 WebSphere Application Server Network Deployment V8 . -

2010–2011 Our Mission
ANNUAL REPORT 2010–2011 OUR MISSION The Indianapolis Museum of Art serves the creative interests of its communities by fostering exploration of art, design, and the natural environment. The IMA promotes these interests through the collection, presentation, interpretation, and conservation of its artistic, historic, and environmental assets. FROM THE CHAIRMAN 02 FROM THE MELVIN & BREN SIMON DIRECTOR AND CEO 04 THE YEAR IN REVIEW 08 EXHIBITIONS 18 AUDIENCE ENGAGEMENT 22 PUBLIC PROGRAMS 24 ART ACQUISITIONS 30 LOANS FROM THE COLLECTION 44 DONORS 46 IMA BOARD OF GOVERNORS 56 AFFILIATE GROUP LEADERSHIP 58 IMA STAFF 59 FINANCIAL REPORT 66 Note: This report is for fiscal year July 2010 through June 2011. COVER Thornton Dial, American, b. 1928, Don’t Matter How Raggly the Flag, It Still Got to Tie Us Together (detail), 2003, mattress coils, chicken wire, clothing, can lids, found metal, plastic twine, wire, Splash Zone compound, enamel, spray paint, on canvas on wood, 71 x 114 x 8 in. James E. Roberts Fund, Deaccession Sculpture Fund, Xenia and Irwin Miller Fund, Alice and Kirk McKinney Fund, Anonymous IV Art Fund, Henry F. and Katherine DeBoest Memorial Fund, Martha Delzell Memorial Fund, Mary V. Black Art Endowment Fund, Elizabeth S. Lawton Fine Art Fund, Emma Harter Sweetser Fund, General Endowed Art Fund, Delavan Smith Fund, General Memorial Art Fund, Deaccessioned Contemporary Art Fund, General Art Fund, Frank Curtis Springer & Irving Moxley Springer Purchase Fund, and the Mrs. Pierre F. Goodrich Endowed Art Fund 2008.182 BACK COVER Miller House and Garden LEFT The Wood Pavilion at the IMA 4 | FROM THE CHAIRMAN FROM THE CHAIRMAN | 5 RESEARCH LEADERSHIP From the In addition to opening the new state-of-the-art Conservation Science Laboratory this past March, the IMA has fulfilled the challenge grant from the Andrew W. -

Web 2.0 and Restful Applications with Websphere Smash and PHP Roland Barcia ‐ STSM, Websphere Lab Services, Lead Web 2.0 Architect Agenda
Web 2.0 and RESTful Applications with WebSphere sMash and PHP Roland Barcia ‐ STSM, WebSphere Lab Services, Lead Web 2.0 Architect Agenda • WebSphere sMash • WebSphere sMash Programming Model • PHP in WebSphere sMash • PHP Applications • Demonstrations 2 Agenda • WebSphere sMash • WebSphere sMash Programming Model • PHP in WebSphere sMash • PHP Applications • Demonstrations 3 What is WebSphere sMash? • WebSphere sMash is a new Agile Web Application Platform – Leveraging Dynamic Scripting Languages – Optimized for Producing.... • REST-based Services • Integration Applications • Mash-ups • Rich Web interfaces 44 sMash Core Values Speed • Dynamic Scripting Support • Rich User Interfaces Support Agility Simplicity • Integrated runtime • End to end web-based tooling • Pre-built services • Visual & programmatic editors 55 Dynamic Scripting • WebSphere sMash is a dynamic scripting platform • Application logic is created in a scripting language – Groovy (for people that prefer Java) – PHP (for the millions of existing PHP programmers) • Java is positioned as the “system” language 66 Application Centric Runtime • WebSphere sMash is an application-centric runtime – You create an application and run it – Each application runs in its own process (JVM) – Runtime is designed to be short lived • WebSphere sMash is a full runtime stack – Everything needed to run the application is provided • including the HTTP stack – No external proxy or web server is required 77 Simple Deployment • The deployment is essentially ZIP and Copy • No machine specific information -

Download Vol 8, No 3&4, Year 2015
The International Journal on Advances in Systems and Measurements is published by IARIA. ISSN: 1942-261x journals site: http://www.iariajournals.org contact: [email protected] Responsibility for the contents rests upon the authors and not upon IARIA, nor on IARIA volunteers, staff, or contractors. IARIA is the owner of the publication and of editorial aspects. IARIA reserves the right to update the content for quality improvements. Abstracting is permitted with credit to the source. Libraries are permitted to photocopy or print, providing the reference is mentioned and that the resulting material is made available at no cost. Reference should mention: International Journal on Advances in Systems and Measurements, issn 1942-261x vol. 8, no. 3 & 4, year 2015, http://www.iariajournals.org/systems_and_measurements/ The copyright for each included paper belongs to the authors. Republishing of same material, by authors or persons or organizations, is not allowed. Reprint rights can be granted by IARIA or by the authors, and must include proper reference. Reference to an article in the journal is as follows: <Author list>, “<Article title>” International Journal on Advances in Systems and Measurements, issn 1942-261x vol. 8, no. 3 & 4, year 2015, http://www.iariajournals.org/systems_and_measurements/ IARIA journals are made available for free, proving the appropriate references are made when their content is used. Sponsored by IARIA www.iaria.org Copyright © 2015 IARIA International Journal on Advances in Systems and Measurements Volume 8, Number -

Powering SOA Solutions with IMS
Front cover Powering SOA Solutions with IMS Introduce yourself to how SOA concepts apply to IMS Identify SOA implementation steps Understand the newest SOA enhancements from IMS Gary Wicks Egide Van Aerschot Omar Badreddin Knut Kubein Kevin Lo Daphne Steele ibm.com/redbooks International Technical Support Organization Powering SOA Solutions with IMS March 2009 SG24-7662-00 Note: Before using this information and the product it supports, read the information in “Notices” on page xi. First Edition (March 2009) This edition applies to Version 10 (program number 5635-A01) and Version 11 Quality Partnership Program (QPP) level (program number 5635-A02) of IBM Information Management System. © Copyright International Business Machines Corporation 2009. All rights reserved. Note to U.S. Government Users Restricted Rights -- Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Notices . xi Trademarks . xii Preface . xiii The team that wrote this book . xiii Become a published author . .xv Comments welcome. .xv Part 1. SOA and IMS: A powerful business combination . 1 Chapter 1. SOA and IMS: The big picture . 3 1.1 What is service-oriented architecture . 4 1.1.1 Major components of SOA . 4 1.1.2 Major roles and activities in a SOA . 5 1.1.3 SOA and standards. 6 1.2 Terminology . 7 1.3 The value of including existing IMS assets into SOA . 11 1.3.1 IMS Connect and IMS Connect Extensions . 15 1.3.2 The IMS SOA Integration Suite. 16 1.3.3 IMS SOAP Gateway . 16 1.3.4 IMS TM Resource Adapter . -
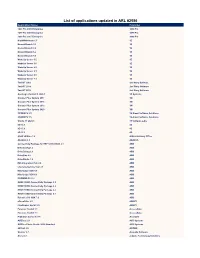
List of Applications Updated in ARL #2586
List of applications updated in ARL #2586 Application Name Publisher 1099 Pro 2005 Enterprise 1099 Pro 1099 Pro 2006 Enterprise 1099 Pro 1099 Pro 2007 Enterprise 1099 Pro NightWatchman 6.5 1E Nomad Branch 5.2 1E Nomad Branch 6.0 1E Nomad Branch 6.2 1E Nomad Branch 6.3 1E WakeUp Server 5.5 1E WakeUp Server 5.6 1E WakeUp Server 6.0 1E WakeUp Server 6.1 1E WakeUp Server 6.5 1E WakeUp Server 7.1 1E TaxACT 2002 2nd Story Software TaxACT 2014 2nd Story Software TaxACT 2018 2nd Story Software Geomagic Control X 2020.1 3D Systems Grouper Plus System 2017 3M Grouper Plus System 2018 3M Grouper Plus System 2019 3M Grouper Plus System 2020 3M CODESYS 2.3 3S-Smart Software Solutions CODESYS 3.5 3S-Smart Software Solutions Studio 3T 2020.9 3T Software Labs 4D 15.1 4D 4D 15.3 4D 4D 16.3 4D ASAP Utilities 7.8 A Must in Every Office AbaStart 2.5 ABACUS Connectivity Package for REF 541/543/545 2.1 ABB DriveConfig 1.2 ABB DriveDebug 2.9 ABB DriveSize 4.9 ABB DriveStudio 1.5 ABB IMS Integration Hub 2.8 ABB Lifecycle Service Tool 2.1 ABB MineScape SDK 5.1 ABB MineScape SDK 6.1 ABB PROMOD IV 11.2 ABB REM615 IED Connectivity Package 2.1 ABB REM615 IED Connectivity Package 2.2 ABB REU615 IED Connectivity Package 2.2 ABB REU615 IED Connectivity Package 5.1 ABB Robotics PC SDK 7.0 ABB eFormFiller 2.5 ABBYY FineReader Sprint 5.0 ABBYY Forensic Toolkit 7.1 AccessData Forensic Toolkit 7.1 AccessData PrizmDoc Server 13.14 AccuSoft ACDSee 2.0 ACD Systems ACDSee Photo Studio 2019 Standard ACD Systems dBTrait 5.5 ACOEM Soulver 2.7 Acqualia Software Arena 4.1 acQuire -

IBM Distributed Software Passport Advantage & Documentation & Media Date Last Updated: 09-Mar-10 Country/Currency: USA/USD
IBM Distributed Software Passport Advantage & Documentation & Media Date Last Updated: 09-Mar-10 Country/Currency: USA/USD Part Description SRP INFORMATION MANAGEMENT ACTIVE CONTENT EDITION FILENET ACTIVE CONTENT EDITION STANDARD PRODUCT BQ00KML IBM FILENET ACTIVE CONTENT EDITION 4.0 MULTILINGUAL MULTIPLATFORM MEDIA PACK 115.00 C8 BANKING RISK PERFORMANCE C8 BANKING RISK PERFORMANCE STANDARD PRODUCT B501MML IBM COGNOS 8 BANKING PERFORMANCE CREDIT-RISK VERSION 8.4.0 FOR MULTIPLATFORMS 115.00 MULTILINGUAL CD ROM 128 BIT ENCRYPTION MEDIA PACK C8 BI ANALYSIS C8 BI ANALYSIS STANDARD PRODUCT B500CML IBM COGNOS 8 BUSINESS INTELLIGENCE ANALYSIS FOR MICROSOFT EXCEL VERSION 8.3 FOR 115.00 WINDOWS MULTILINGUAL CD ROM 128 BIT ENCRYPTION MEDIA PACK B500DML IBM COGNOS 8 BUSINESS INTELLIGENCE ANALYSIS FOR MICROSOFT EXCEL VERSION 8.4 FOR 115.00 WINDOWS MULTILINGUAL CD ROM 128 BIT ENCRYPTION MEDIA PACK B5019ML IBM COGNOS 8 BUSINESS INTELLIGENCE ANALYSIS VERSION 8.3 FOR MULTIPLATFORMS 115.00 MULTILINGUAL CD ROM 128 BIT ENCRYPTION MEDIA PACK B501BML IBM COGNOS 8 BUSINESS INTELLIGENCE ANALYSIS VERSION 8.4 FOR MULTIPLATFORMS 115.00 MULTILINGUAL CD ROM 128 BIT ENCRYPTION MEDIA PACK B502IML IBM COGNOS 8 BUSINESS INTELLIGENCE ANALYSIS VERSION 8.4.1 FOR MULTIPLATFORMS 115.00 MULTILINGUAL MEDIA PACK B502MML IBM COGNOS 8 BUSINESS INTELLIGENCE ANALYSIS FOR MICROSOFT EXCEL VERSION 8.4.1 FOR 115.00 WINDOWS MULTILINGUAL MEDIA PACK C8 BI FOR LINUX ON SYSTEM Z ADD ON C8 BI FOR LINUX ON SYSTEM Z ADD-ON STANDARD PRODUCT B5004ML IBM COGNOS 8 BUSINESS INTELLIGENCE FOR LINUX -
![Cloud Computing a Practical Approach [2010]](https://docslib.b-cdn.net/cover/1849/cloud-computing-a-practical-approach-2010-4201849.webp)
Cloud Computing a Practical Approach [2010]
Cloud Computing: A Practical Approach Anthony T. Velte Toby J. Velte, Ph.D. Robert Elsenpeter New York Chicago San Francisco Lisbon London Madrid Mexico City Milan New Delhi San Juan Seoul Singapore Sydney Toronto Copyright © 2010 by The McGraw-Hill Companies. All rights reserved. Except as permitted under the United States Copyright Act of 1976, no part of this publication may be reproduced or distributed in any form or by any means, or stored in a database or retrieval system, without the prior written permission of the publisher. ISBN: 978-0-07-162695-8 MHID: 0-07-162695-6 The material in this eBook also appears in the print version of this title: ISBN: 978-0-07-162694-1, MHID: 0-07-162694-8. All trademarks are trademarks of their respective owners. Rather than put a trademark symbol after every occurrence of a trademarked name, we use names in an editorial fashion only, and to the benefit of the trademark owner, with no intention of infringement of the trademark. Where such designations appear in this book, they have been printed with initial caps. McGraw-Hill eBooks are available at special quantity discounts to use as premiums and sales promotions, or for use in corporate training programs. To contact a representative please e-mail us at [email protected]. Information has been obtained by McGraw-Hill from sources believed to be reliable. However, because of the possibility of human or mechanical error by our sources, McGraw-Hill, or others, McGraw-Hill does not guarantee the accuracy, adequacy, or completeness of any information and is not responsible for any errors or omissions or the results obtained from the use of such information. -

Debugging PHP Using Eclipse and PDT Use Xdebug Or Zend Debugger to Boost Your Productivity When Fixing Bugs in PHP Applications
Debugging PHP using Eclipse and PDT Use XDebug or Zend Debugger to boost your productivity when fixing bugs in PHP applications Skill Level: Intermediate Nathan A. Good ([email protected]) Senior Information Engineer Consultant 17 Jun 2008 The PHP Development Tools (PDT) plug-in, when installed with Eclipse Europa, gives you that ability to quickly write and debug PHP scripts and pages. PDT supports two debugging tools: XDebug and the Zend Debugger. Learn how to configure PDT for debugging PHP scripts and discover which perspectives you use when taking closer looks at your scripts. Section 1. Before you start About this tutorial This tutorial demonstrates how to configure the PHP Development Tools (PDT) plug-in for Eclipse to debug your PHP scripts. It also introduces the perspectives you'll use (namely, PHP Debug) when taking closer looks at your PHP scripts. Objectives After completing this tutorial, you'll be able to set up either XDebug — an open source project that allows you to debug executable scripts and scripts running on a Web server — or the Zend Debugger in Eclipse using the PDT project to develop Debugging PHP using Eclipse and PDT © Copyright IBM Corporation 1994, 2008. All rights reserved. Page 1 of 35 developerWorks® ibm.com/developerWorks PHP applications. You'll understand the various parts of the PDT project's PHP Debug perspective and learn how to set up, view, and work with breakpoints. You also learn how to inspect the values of variables as you are stepping through the code, as well as how to debug PHP Web applications on your local server so you can run through your PHP Web application with the debugger. -

CICS Dynamic Scripting: Application Presentation Layer Options
CICS Dynamic Scripting: the Presentation Layer Dennis Weiand IBM Advanced Technical Skills March 16, 2012 Session Number #10291 © 2012 IBM Corporation Abstract • CICS Dynamic Scripting provides an agile environment for quick development of situational applications. Your application's presentation layer (web browser interaction) is an important part of a situational application and you need to know the basics concepts and capabilities to get started. This topic discusses the available options when developing the presentation layer of your CICS Dynamic Scripting application, along with the accompanying concepts. Areas of discussion will include serving HTML, Cascading StyleSheets, and JavaScript, along with AJAX, Dojo, RESTful interactions, and security. 2 © 2012 IBM Corporation Trademarks • The following terms are trademarks of the International Business Machines Corporation or/and Lotus Development Corporation in the United States, other countries, or both: • Redbooks(logo)™, AIX®, alphaWorks®, CICS®, DB2®, IBM®, IMS™, Informix®, MQSeries®, VisualAge®, WebSphere® • The following terms are trademarks of other companies: • Microsoft , Windows , Windows NT , and the Windows logo are trademarks of Microsoft Corporation. • Java and all Java-based trademarks and logos are trademarks or registered trademarks of Oracle, Inc. • CORBA , CORBAServices , and IIOP are trademarks of the Object Management Group, Inc. • UNIX is a registered trademark of The Open Group in the United States and other countries. • Other company, product, and service names may be trademarks or service marks of others. 3 © 2012 IBM Corporation Notices • This information was developed for products and services offered in the U.S.A. IBM may not offer the products, services, or features discussed in this presentation in other countries. -

P8, IBM's PHP on Java Virtual Machinetm Project
P8, IBM’s PHP on Java Virtual MachineTM Project Rob Nicholson [email protected] Why Build PHP on the JVM? • 20M+ web domains use PHP • 3M+ Programmers know PHP • Huge repository of reusable modules, snippets, extensions. • Easy language to learn -> Mashups • Language has evolved to be easy to use TIOBE Programming Community Index (Sep 2008) •Same-process interaction Java <-> PHP. •Combine Java and PHP assets. •Combine Java and PHP programmers. •Data sharing without copies. •Extend Java with PHP. •Benefit from vast investment in Java VM •IBM WebSphere sMash has Groovy +P8 2 © 2008 IBM Corporation What is PHP? • Procedural and OO language. Scripts Applications • Engine and Extensions Implemented in C. Modules Frameworks • Frameworks, Modules, Applications HTTP server implemented in PHP. Zend Engine Apache • Large and active open source communities. Virtual Machine C Extensions Databases •No specification •Incomplete documentation •Incomplete tests •No Unicode •Reference Implementation based language 3 © 2008 IBM Corporation What is P8? CLI PZ Http PHP Scripts • PHP 5 on Java 5 SE or later. SAPI-J • Hand crafted lexer, LPG generated parser. • Started as Interpreter -> transitioning to compiler. PHP Engine • Maintain the illusion of interpreter. Debug (DBGp) • Extensibility via XAPI Parser IR P8 Runtime • XAPI-C for C extensions from php.net • XAPI-J for Java extensions, native libraries Interpreter/Compiler Cache invoked over JNI and Project Zero interface • Java Bridge Runtime • Extend Java classes in PHP. XAPI-J • Implement Java Interfaces in PHP. XAPI-C Java • PHP proxies over Java Classes C Extensions Native Extensions code • Debug using via DBGp using Eclipse with PDT 4 © 2008 IBM Corporation How applications are supported. -
Implement a Facebook Photo Album Using the Flex SDK Skill Level: Intermediate
Implement a Facebook photo album using the Flex SDK Skill Level: Intermediate Joe Lennon ([email protected]) Software Developer Core International 18 Nov 2008 Adobe® has released the free, open source Flex SDK framework to enable developers to create Rich Internet Applications (RIAs). The Flex framework provides you with a method of creating cross-browser, cross-platform Web applications that is quick and simple. Flex applications run in the Flash player, which is installed on the majority of Internet-connected computers, but Flex also provides you with an object-oriented user interface framework similar to Java™ Swing. In this tutorial, develop a Facebook application in Adobe Flex that displays a slideshow of a user's Facebook photo albums. The Facebook application will contain a profile box listing all of the user's photo albums, each a link to a Flex slideshow of that album. The Flex application will use the Facebook REST API to fetch the photos of the selected Facebook album and dynamically generate the slideshow. Section 1. Before you start This tutorial is for Web developers who are looking to create interactive Facebook applications using the free Adobe Flex SDK. Although not required, a basic knowledge of PHP, HTML, and Web application development would be of great benefit to readers. No prior experience with Flex development or Facebook development is required. About this tutorial This tutorial provides you with a foundation in developing Facebook applications Implement a Facebook photo album using the Flex SDK © Copyright IBM Corporation 1994, 2008. All rights reserved. Page 1 of 49 developerWorks® ibm.com/developerWorks using the Adobe Flex SDK and the Facebook development platform.