A Logarithm Algorithm
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Enigmatic Number E: a History in Verse and Its Uses in the Mathematics Classroom
To appear in MAA Loci: Convergence The Enigmatic Number e: A History in Verse and Its Uses in the Mathematics Classroom Sarah Glaz Department of Mathematics University of Connecticut Storrs, CT 06269 [email protected] Introduction In this article we present a history of e in verse—an annotated poem: The Enigmatic Number e . The annotation consists of hyperlinks leading to biographies of the mathematicians appearing in the poem, and to explanations of the mathematical notions and ideas presented in the poem. The intention is to celebrate the history of this venerable number in verse, and to put the mathematical ideas connected with it in historical and artistic context. The poem may also be used by educators in any mathematics course in which the number e appears, and those are as varied as e's multifaceted history. The sections following the poem provide suggestions and resources for the use of the poem as a pedagogical tool in a variety of mathematics courses. They also place these suggestions in the context of other efforts made by educators in this direction by briefly outlining the uses of historical mathematical poems for teaching mathematics at high-school and college level. Historical Background The number e is a newcomer to the mathematical pantheon of numbers denoted by letters: it made several indirect appearances in the 17 th and 18 th centuries, and acquired its letter designation only in 1731. Our history of e starts with John Napier (1550-1617) who defined logarithms through a process called dynamical analogy [1]. Napier aimed to simplify multiplication (and in the same time also simplify division and exponentiation), by finding a model which transforms multiplication into addition. -

Exponent and Logarithm Practice Problems for Precalculus and Calculus
Exponent and Logarithm Practice Problems for Precalculus and Calculus 1. Expand (x + y)5. 2. Simplify the following expression: √ 2 b3 5b +2 . a − b 3. Evaluate the following powers: 130 =,(−8)2/3 =,5−2 =,81−1/4 = 10 −2/5 4. Simplify 243y . 32z15 6 2 5. Simplify 42(3a+1) . 7(3a+1)−1 1 x 6. Evaluate the following logarithms: log5 125 = ,log4 2 = , log 1000000 = , logb 1= ,ln(e )= 1 − 7. Simplify: 2 log(x) + log(y) 3 log(z). √ √ √ 8. Evaluate the following: log( 10 3 10 5 10) = , 1000log 5 =,0.01log 2 = 9. Write as sums/differences of simpler logarithms without quotients or powers e3x4 ln . e 10. Solve for x:3x+5 =27−2x+1. 11. Solve for x: log(1 − x) − log(1 + x)=2. − 12. Find the solution of: log4(x 5)=3. 13. What is the domain and what is the range of the exponential function y = abx where a and b are both positive constants and b =1? 14. What is the domain and what is the range of f(x) = log(x)? 15. Evaluate the following expressions. (a) ln(e4)= √ (b) log(10000) − log 100 = (c) eln(3) = (d) log(log(10)) = 16. Suppose x = log(A) and y = log(B), write the following expressions in terms of x and y. (a) log(AB)= (b) log(A) log(B)= (c) log A = B2 1 Solutions 1. We can either do this one by “brute force” or we can use the binomial theorem where the coefficients of the expansion come from Pascal’s triangle. -

Zero-One Laws
1 THE LOGIC IN COMPUTER SCIENCE COLUMN by 2 Yuri GUREVICH Electrical Engineering and Computer Science UniversityofMichigan, Ann Arb or, MI 48109-2122, USA [email protected] Zero-One Laws Quisani: I heard you talking on nite mo del theory the other day.Itisinteresting indeed that all those famous theorems ab out rst-order logic fail in the case when only nite structures are allowed. I can understand that for those, likeyou, educated in the tradition of mathematical logic it seems very imp ortantto ndoutwhichof the classical theorems can b e rescued. But nite structures are to o imp ortant all by themselves. There's got to b e deep nite mo del theory that has nothing to do with in nite structures. Author: \Nothing to do" sounds a little extremist to me. Sometimes in nite ob jects are go o d approximations of nite ob jects. Q: I do not understand this. Usually, nite ob jects approximate in nite ones. A: It may happ en that the in nite case is cleaner and easier to deal with. For example, a long nite sum may b e replaced with a simpler integral. Returning to your question, there is indeed meaningful, inherently nite, mo del theory. One exciting issue is zero- one laws. Consider, say, undirected graphs and let be a propertyofsuch graphs. For example, may b e connectivity. What fraction of n-vertex graphs have the prop erty ? It turns out that, for many natural prop erties , this fraction converges to 0 or 1asn grows to in nity. If the fraction converges to 1, the prop erty is called almost sure. -

Leonhard Euler: His Life, the Man, and His Works∗
SIAM REVIEW c 2008 Walter Gautschi Vol. 50, No. 1, pp. 3–33 Leonhard Euler: His Life, the Man, and His Works∗ Walter Gautschi† Abstract. On the occasion of the 300th anniversary (on April 15, 2007) of Euler’s birth, an attempt is made to bring Euler’s genius to the attention of a broad segment of the educated public. The three stations of his life—Basel, St. Petersburg, andBerlin—are sketchedandthe principal works identified in more or less chronological order. To convey a flavor of his work andits impact on modernscience, a few of Euler’s memorable contributions are selected anddiscussedinmore detail. Remarks on Euler’s personality, intellect, andcraftsmanship roundout the presentation. Key words. LeonhardEuler, sketch of Euler’s life, works, andpersonality AMS subject classification. 01A50 DOI. 10.1137/070702710 Seh ich die Werke der Meister an, So sehe ich, was sie getan; Betracht ich meine Siebensachen, Seh ich, was ich h¨att sollen machen. –Goethe, Weimar 1814/1815 1. Introduction. It is a virtually impossible task to do justice, in a short span of time and space, to the great genius of Leonhard Euler. All we can do, in this lecture, is to bring across some glimpses of Euler’s incredibly voluminous and diverse work, which today fills 74 massive volumes of the Opera omnia (with two more to come). Nine additional volumes of correspondence are planned and have already appeared in part, and about seven volumes of notebooks and diaries still await editing! We begin in section 2 with a brief outline of Euler’s life, going through the three stations of his life: Basel, St. -
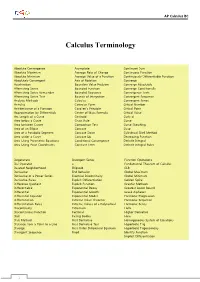
Calculus Terminology
AP Calculus BC Calculus Terminology Absolute Convergence Asymptote Continued Sum Absolute Maximum Average Rate of Change Continuous Function Absolute Minimum Average Value of a Function Continuously Differentiable Function Absolutely Convergent Axis of Rotation Converge Acceleration Boundary Value Problem Converge Absolutely Alternating Series Bounded Function Converge Conditionally Alternating Series Remainder Bounded Sequence Convergence Tests Alternating Series Test Bounds of Integration Convergent Sequence Analytic Methods Calculus Convergent Series Annulus Cartesian Form Critical Number Antiderivative of a Function Cavalieri’s Principle Critical Point Approximation by Differentials Center of Mass Formula Critical Value Arc Length of a Curve Centroid Curly d Area below a Curve Chain Rule Curve Area between Curves Comparison Test Curve Sketching Area of an Ellipse Concave Cusp Area of a Parabolic Segment Concave Down Cylindrical Shell Method Area under a Curve Concave Up Decreasing Function Area Using Parametric Equations Conditional Convergence Definite Integral Area Using Polar Coordinates Constant Term Definite Integral Rules Degenerate Divergent Series Function Operations Del Operator e Fundamental Theorem of Calculus Deleted Neighborhood Ellipsoid GLB Derivative End Behavior Global Maximum Derivative of a Power Series Essential Discontinuity Global Minimum Derivative Rules Explicit Differentiation Golden Spiral Difference Quotient Explicit Function Graphic Methods Differentiable Exponential Decay Greatest Lower Bound Differential -

On the Normality of Numbers
ON THE NORMALITY OF NUMBERS Adrian Belshaw B. Sc., University of British Columbia, 1973 M. A., Princeton University, 1976 A THESIS SUBMITTED 'IN PARTIAL FULFILLMENT OF THE REQUIREMENTS FOR THE DEGREE OF MASTER OF SCIENCE in the Department of Mathematics @ Adrian Belshaw 2005 SIMON FRASER UNIVERSITY Fall 2005 All rights reserved. This work may not be reproduced in whole or in part, by photocopy or other means, without the permission of the author. APPROVAL Name: Adrian Belshaw Degree: Master of Science Title of Thesis: On the Normality of Numbers Examining Committee: Dr. Ladislav Stacho Chair Dr. Peter Borwein Senior Supervisor Professor of Mathematics Simon Fraser University Dr. Stephen Choi Supervisor Assistant Professor of Mathematics Simon Fraser University Dr. Jason Bell Internal Examiner Assistant Professor of Mathematics Simon Fraser University Date Approved: December 5. 2005 SIMON FRASER ' u~~~snrllbrary DECLARATION OF PARTIAL COPYRIGHT LICENCE The author, whose copyright is declared on the title page of this work, has granted to Simon Fraser University the right to lend this thesis, project or extended essay to users of the Simon Fraser University Library, and to make partial or single copies only for such users or in response to a request from the library of any other university, or other educational institution, on its own behalf or for one of its users. The author has further granted permission to Simon Fraser University to keep or make a digital copy for use in its circulating collection, and, without changing the content, to translate the thesislproject or extended essays, if technically possible, to any medium or format for the purpose of preservation of the digital work. -

Diophantine Approximation and Transcendental Numbers
Diophantine Approximation and Transcendental Numbers Connor Goldstick June 6, 2017 Contents 1 Introduction 1 2 Continued Fractions 2 3 Rational Approximations 3 4 Transcendental Numbers 6 5 Irrationality Measure 7 6 The continued fraction for e 8 6.1 e's Irrationality measure . 10 7 Conclusion 11 A The Lambert Continued Fraction 11 1 Introduction Suppose we have an irrational number, α, that we want to approximate with a rational number, p=q. This question of approximating an irrational number is the primary concern of Diophantine approximation. In other words, we want jα−p=qj < . However, this method of trying to approximate α is boring, as it is possible to get an arbitrary amount of precision by making q large. To remedy this problem, it makes sense to vary with q. The problem we are really trying to solve is finding p and q such that p 1 1 jα − j < which is equivalent to jqα − pj < (1) q q2 q Solutions to this problem have applications in both number theory and in more applied fields. For example, in signal processing many of the quickest approximation algorithms are given by solutions to Diophantine approximation problems. Diophantine approximations also give many important results like the continued fraction expansion of e. One of the most interesting aspects of Diophantine approximations are its relationship with transcendental 1 numbers (a number that cannot be expressed of the root of a polynomial with rational coefficients). One of the key characteristics of a transcendental number is that it is easy to approximate with rational numbers. This paper is separated into two categories. -

Hydraulics Manual Glossary G - 3
Glossary G - 1 GLOSSARY OF HIGHWAY-RELATED DRAINAGE TERMS (Reprinted from the 1999 edition of the American Association of State Highway and Transportation Officials Model Drainage Manual) G.1 Introduction This Glossary is divided into three parts: · Introduction, · Glossary, and · References. It is not intended that all the terms in this Glossary be rigorously accurate or complete. Realistically, this is impossible. Depending on the circumstance, a particular term may have several meanings; this can never change. The primary purpose of this Glossary is to define the terms found in the Highway Drainage Guidelines and Model Drainage Manual in a manner that makes them easier to interpret and understand. A lesser purpose is to provide a compendium of terms that will be useful for both the novice as well as the more experienced hydraulics engineer. This Glossary may also help those who are unfamiliar with highway drainage design to become more understanding and appreciative of this complex science as well as facilitate communication between the highway hydraulics engineer and others. Where readily available, the source of a definition has been referenced. For clarity or format purposes, cited definitions may have some additional verbiage contained in double brackets [ ]. Conversely, three “dots” (...) are used to indicate where some parts of a cited definition were eliminated. Also, as might be expected, different sources were found to use different hyphenation and terminology practices for the same words. Insignificant changes in this regard were made to some cited references and elsewhere to gain uniformity for the terms contained in this Glossary: as an example, “groundwater” vice “ground-water” or “ground water,” and “cross section area” vice “cross-sectional area.” Cited definitions were taken primarily from two sources: W.B. -

Network Intrusion Detection with Xgboost and Deep Learning Algorithms: an Evaluation Study
2020 International Conference on Computational Science and Computational Intelligence (CSCI) Network Intrusion Detection with XGBoost and Deep Learning Algorithms: An Evaluation Study Amr Attia Miad Faezipour Abdelshakour Abuzneid Computer Science & Engineering Computer Science & Engineering Computer Science & Engineering University of Bridgeport, CT 06604, USA University of Bridgeport, CT 06604, USA University of Bridgeport, CT 06604, USA [email protected] [email protected] [email protected] Abstract— This paper introduces an effective Network Intrusion In the KitNET model introduced in [2], an unsupervised Detection Systems (NIDS) framework that deploys incremental technique is introduced for anomaly-based intrusion statistical damping features of the packets along with state-of- detection. Incremental statistical feature extraction of the the-art machine/deep learning algorithms to detect malicious packets is passed through ensembles of autoencoders with a patterns. A comprehensive evaluation study is conducted predefined threshold. The model calculates the Root Mean between eXtreme Gradient Boosting (XGBoost) and Artificial Neural Networks (ANN) where feature selection and/or feature Square (RMS) error to detect anomaly behavior. The higher dimensionality reduction techniques such as Principal the calculated RMS at the output, the higher probability of Component Analysis (PCA) and Linear Discriminant Analysis suspicious activity. (LDA) are also integrated into the models to decrease the system Supervised learning has achieved very decent results with complexity for achieving fast responses. Several experimental algorithms such as Random Forest, ZeroR, J48, AdaBoost, runs confirm how powerful machine/deep learning algorithms Logit Boost, and Multilayer Perceptron [3]. Machine/deep are for intrusion detection on known attacks when combined learning-based algorithms for NIDS have been extensively with the appropriate features extracted. -

The Prime Number Theorem a PRIMES Exposition
The Prime Number Theorem A PRIMES Exposition Ishita Goluguri, Toyesh Jayaswal, Andrew Lee Mentor: Chengyang Shao TABLE OF CONTENTS 1 Introduction 2 Tools from Complex Analysis 3 Entire Functions 4 Hadamard Factorization Theorem 5 Riemann Zeta Function 6 Chebyshev Functions 7 Perron Formula 8 Prime Number Theorem © Ishita Goluguri, Toyesh Jayaswal, Andrew Lee, Mentor: Chengyang Shao 2 Introduction • Euclid (300 BC): There are infinitely many primes • Legendre (1808): for primes less than 1,000,000: x π(x) ' log x © Ishita Goluguri, Toyesh Jayaswal, Andrew Lee, Mentor: Chengyang Shao 3 Progress on the Distribution of Prime Numbers • Euler: The product formula 1 X 1 Y 1 ζ(s) := = ns 1 − p−s n=1 p so (heuristically) Y 1 = log 1 1 − p−1 p • Chebyshev (1848-1850): if the ratio of π(x) and x= log x has a limit, it must be 1 • Riemann (1859): On the Number of Primes Less Than a Given Magnitude, related π(x) to the zeros of ζ(s) using complex analysis • Hadamard, de la Vallée Poussin (1896): Proved independently the prime number theorem by showing ζ(s) has no zeros of the form 1 + it, hence the celebrated prime number theorem © Ishita Goluguri, Toyesh Jayaswal, Andrew Lee, Mentor: Chengyang Shao 4 Tools from Complex Analysis Theorem (Maximum Principle) Let Ω be a domain, and let f be holomorphic on Ω. (A) jf(z)j cannot attain its maximum inside Ω unless f is constant. (B) The real part of f cannot attain its maximum inside Ω unless f is a constant. Theorem (Jensen’s Inequality) Suppose f is holomorphic on the whole complex plane and f(0) = 1. -

The Logarithmic Chicken Or the Exponential Egg: Which Comes First?
The Logarithmic Chicken or the Exponential Egg: Which Comes First? Marshall Ransom, Senior Lecturer, Department of Mathematical Sciences, Georgia Southern University Dr. Charles Garner, Mathematics Instructor, Department of Mathematics, Rockdale Magnet School Laurel Holmes, 2017 Graduate of Rockdale Magnet School, Current Student at University of Alabama Background: This article arose from conversations between the first two authors. In discussing the functions ln(x) and ex in introductory calculus, one of us made good use of the inverse function properties and the other had a desire to introduce the natural logarithm without the classic definition of same as an integral. It is important to introduce mathematical topics using a minimal number of definitions and postulates/axioms when results can be derived from existing definitions and postulates/axioms. These are two of the ideas motivating the article. Thus motivated, the authors compared manners with which to begin discussion of the natural logarithm and exponential functions in a calculus class. x A related issue is the use of an integral to define a function g in terms of an integral such as g()() x f t dt . c We believe that this is something that students should understand and be exposed to prior to more advanced x x sin(t ) 1 “surprises” such as Si(x ) dt . In particular, the fact that ln(x ) dt is extremely important. But t t 0 1 must that fact be introduced as a definition? Can the natural logarithm function arise in an introductory calculus x 1 course without the -

Differentiating Logarithm and Exponential Functions
Differentiating logarithm and exponential functions mc-TY-logexp-2009-1 This unit gives details of how logarithmic functions and exponential functions are differentiated from first principles. In order to master the techniques explained here it is vital that you undertake plenty of practice exercises so that they become second nature. After reading this text, and/or viewing the video tutorial on this topic, you should be able to: • differentiate ln x from first principles • differentiate ex Contents 1. Introduction 2 2. Differentiation of a function f(x) 2 3. Differentiation of f(x)=ln x 3 4. Differentiation of f(x) = ex 4 www.mathcentre.ac.uk 1 c mathcentre 2009 1. Introduction In this unit we explain how to differentiate the functions ln x and ex from first principles. To understand what follows we need to use the result that the exponential constant e is defined 1 1 as the limit as t tends to zero of (1 + t) /t i.e. lim (1 + t) /t. t→0 1 To get a feel for why this is so, we have evaluated the expression (1 + t) /t for a number of decreasing values of t as shown in Table 1. Note that as t gets closer to zero, the value of the expression gets closer to the value of the exponential constant e≈ 2.718.... You should verify some of the values in the Table, and explore what happens as t reduces further. 1 t (1 + t) /t 1 (1+1)1/1 = 2 0.1 (1+0.1)1/0.1 = 2.594 0.01 (1+0.01)1/0.01 = 2.705 0.001 (1.001)1/0.001 = 2.717 0.0001 (1.0001)1/0.0001 = 2.718 We will also make frequent use of the laws of indices and the laws of logarithms, which should be revised if necessary.