How Safe Are Popular Apps?
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Appannie.Com
A P P A N N I E S T A T E O F M O B I L E 2 0 2 1 E X E C U T I V E S U M M A R Y 2020 Mobile Landscape at a Glance New App App Store Daily Time Spent Mobile Venture Capital Downloads Spend Per User Ad Spend to Mobile Tech S T A T E O F 218B $143B 4.2 Hrs $240B $73B M O B I L E 2 0 2 1 +7% +20% +20% +26% +27% YoY Growth YoY Growth YoY Growth YoY Growth YoY Growth Source: Crunchbase iOS, Google Play, Third-Party iOS, Google Play, Third-Party Android Phones; Among Markets Android in China Android in China Analyzed 2 What's Inside Macro Mobile Trends Gaming Finance Social Networking Video Streaming S T A Retail T E O Food & Drink F M O Marketing & Advertising B I L E Other Industries Embracing Mobile Innovation 2 0 2 Top Apps and Games of 2020 1 3 The Mobile Performance Standard S T A T E O F M O B I L E 2 0 2 1 4 Macro Mobile After a year that welcomed more downloads than ever before, apps should focus on Trends influencing user discovery. 37% of app users we surveyed reported they found a new app through a friend or family member. 67% of users agree when discovering and purchasing new S T apps they trust what they learn from online A T E research, and 50% only consider well-known O F apps. -

(Icresh) Theme Radicalism in Global Constellat
PROCEEDING Proceeding International Conference On Religion and Social Humanities (ICReSH) Theme Radicalism In Global Constellation Batusangkar, 5-6 November 2018 Speaker: Sidney Jones (Director Institute For Police Analyse Of Conflict) Nasir Abbas ( Radicalism Observer and Analyse) Syekh Walid Hamdi (Cairo University Mesir) Dr. Kasmuri, MA (Rektor IAIN Batusangkar) Dr. Yusefri., M. Ag ( IAIN Curup) Faculty Ushuluddin, Adab dan Dakwah (FUAD) Institut Agama Islam Negeri Batusangkar (IAIN Batusangkar) 1 PROCEEDING Proceeding International Conference On Religion and Social Humanities (ICReSH) Theme “ Radicalism In Global Constellation “ Steering Commite : Dr. Kasmuri, MA Drs. Adripen, M.Pd Dr. Zulkifli, MA Organizing Commitee: Dr. Irman, S.Ag, M.Pd Novi Budiman S.IP, M.Si Eliwatis, M.Ag Irwandi, MA Editor : Dewi Dahlan, M.IP Reviewer: Dr. Yuzarion, S.Ag. S.P.Si, M.Si Dr. Risman Bustaman Marhen, M.PD Hafizullah, MA Refika Mastanora, M.I Kom Published by : Faculty Ushuluddin, Adab dan Dakwah FUAD IAIN Batusangkar Kampus IAIN Batusangkar Jalan Sudirman No 137 Lima Kaum Batusangkar Telp. (0752) 71150, 574221, 71890. Fax (0752) 71879 Website : www.iainbatusangkar.ac.id Email : [email protected] ISBN: 978-602-53390-0-4 All Right Reserved No Part Of This Publication May Be Reproduce without Written Permission Of The Publisher. 2 OPENING SPEECHES Radicalism is an extreme view of individual freedom. The emphasis of radicalist thinking lies in violence and direct action carried out by groups who act on behalf of their struggle with resistance to oppressed groups. At the global level, radical actions in the form of violence have a very long history and have a wide impact in the global political constellation. -
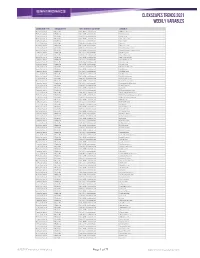
Clickscapes Trends 2021 Weekly Variables
ClickScapes Trends 2021 Weekly VariableS Connection Type Variable Type Tier 1 Interest Category Variable Home Internet Website Arts & Entertainment 1075koolfm.com Home Internet Website Arts & Entertainment 8tracks.com Home Internet Website Arts & Entertainment 9gag.com Home Internet Website Arts & Entertainment abs-cbn.com Home Internet Website Arts & Entertainment aetv.com Home Internet Website Arts & Entertainment ago.ca Home Internet Website Arts & Entertainment allmusic.com Home Internet Website Arts & Entertainment amazonvideo.com Home Internet Website Arts & Entertainment amphitheatrecogeco.com Home Internet Website Arts & Entertainment ancestry.ca Home Internet Website Arts & Entertainment ancestry.com Home Internet Website Arts & Entertainment applemusic.com Home Internet Website Arts & Entertainment archambault.ca Home Internet Website Arts & Entertainment archive.org Home Internet Website Arts & Entertainment artnet.com Home Internet Website Arts & Entertainment atomtickets.com Home Internet Website Arts & Entertainment audible.ca Home Internet Website Arts & Entertainment audible.com Home Internet Website Arts & Entertainment audiobooks.com Home Internet Website Arts & Entertainment audioboom.com Home Internet Website Arts & Entertainment bandcamp.com Home Internet Website Arts & Entertainment bandsintown.com Home Internet Website Arts & Entertainment barnesandnoble.com Home Internet Website Arts & Entertainment bellmedia.ca Home Internet Website Arts & Entertainment bgr.com Home Internet Website Arts & Entertainment bibliocommons.com -

Mobile LBS: Status Update & Platform Assessment
Wireless Media Mobile LBS: Status Update & Platform Assessment Wireless Media Strategies (WMS) Report Snapshot This report provides Strategy Analytics’ high-level outlook for handset-based location-based services. Rising GPS penetration, the growing popularity of taxi- sharing, carpooling, and ride-sharing apps, third-party content integration into popular map applications, and the emerging wearables device category provide opportunities for growth and development in mobile LBS. This report also includes an update of our assessment of global location-platform leaders, HERE, Google, TomTom and Apple. November 2016 Nitesh Patel +441908423621 Tel: Email: [email protected] www.strategyanalytics.com Wireless Media Contents 1. Executive Summary 3 2. Key Trends in Mobile LBS 4 2.1 Reported Mobile LBS Use and Adoption 5 2.2 Mobile Maps & Direction Use in Context 6 2.3 Mobile Location Capability to Boost Emerging Market Opportunities 9 2.3.1 GPS handset penetration rises in the entry tier 9 2.4 New Trends in Urban Mobility 10 2.5 From Maps & Navigation to All-in-One Travel Planning Apps 11 2.6 Wearables Remain a Growth Opportunity 13 3. Location Platform Benchmark Update 16 3.1 Overall Assessment 21 Exhibits Exhibit 1: Overall Mobile Map & Directions Use in Context: Asia, Europe, and the US ............................................... 6 Exhibit 2: Regular Mobile Map & Directions Use in Context: Asia, Europe, and the US .............................................. 8 Exhibit 3: Mobile Map & Directions Use across All Countries ...................................................................................... 8 Exhibit 4 Rising Penetration of GPS Handsets by Price Tier ...................................................................................... 10 Exhibit 5 Global Wearable Device Sales by Type ...................................................................................................... 14 Exhibit 6 The Relative Strengths & Weaknesses of Major Location Platforms .......................................................... -

Understanding User Motivations for Asking and Answering a Question on Brainly, Online Social Learning Network
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Illinois Digital Environment for Access to Learning and Scholarship Repository Understanding User Motivations for Asking and Answering a Question on Brainly, Online Social Learning Network Erik Choi, Rosario Munoz, Meric Balak, Dimas Mukhlas, Lívia Farias, Dubraska Jara, Paris Turnip, Oleg Burkov Abstract As an emergence of social question-answering (Q&A) services has spurred the growth of social information seeking through question-answering interactions in order to share knowledge and information for users’ need in their learning processes, the current study focuses on conceptualizing and gaining a holistic view of what motivates students to visit social Q&A services and engage in social interactions for sharing and seeking knowledge. The findings show that an immediate help, learning, verification are the top motivations for asking a question, while altruism, learning, and self-enjoyment are the top motivations for answering a question on Brainly, an online social learning Q&A service. Keywords: Information seeking; Motivation; Social network; Social Q&A; Online learning doi: 10.9776/16512 Copyright: Copyright is held by the authors. Contact: [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected] 1 Introduction Searching for information online for learning has become prevalent, and a variety of online information technologies and services facilitate users’ learning processes by providing relevant and helpful information to satisfy their need in learning. In recent years, an emergence of social question-answering (Q&A) services has spurred the growth of social information seeking through question-answering interactions in order to share knowledge and information for users’ need in their learning processes. -
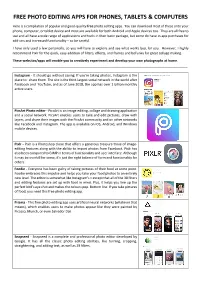
Free Photo Editing Apps for Phones, Tablets & Computers
FREE PHOTO EDITING APPS FOR PHONES, TABLETS & COMPUTERS Here is a compilation of popular and good-quality free photo editing apps. You can download most of these onto your phone, computer, or tablet device and most are available for both Android and Apple devices too. They are all free to use and all have a wide range of applications and tools in their basic package, but some do have in-app purchases for add-ons and increased functionality – so be careful. I have only used a few personally, so you will have to explore and see what works best for you. However, I highly recommend Pixlr for the quick, easy addition of filters, effects, and frames and beFunky for great collage making. These websites/apps will enable you to creatively experiment and develop your own photographs at home. _______________________________________________________________________________________________ Instagram - It should go without saying: If you’re taking photos, Instagram is the place to share them. The site is the third-largest social network in the world after Facebook and YouTube, and as of June 2018, the app has over 1 billion monthly active users. PicsArt Photo editor - PicsArt is an image editing, collage and drawing application and a social network. PicsArt enables users to take and edit pictures, draw with layers, and share their images with the PicsArt community and on other networks like Facebook and Instagram. The app is available on iOS, Android, and Windows mobile devices. Pixlr - Pixlr is a Photoshop clone that offers a generous treasure trove of image- editing features along with the ability to import photos from Facebook. -

U-SAVE): a Product of the JRC Poc Instrument
fUel-SAVing trip plannEr (U-SAVE): A product of the JRC PoC Instrument Final Report Arcidiacono, V., Maineri, L., Tsiakmakis, S., Fontaras, G., Thiel, C., Ciuffo, B. 2017 EUR 29099 EN This publication is a Technical report by the Joint Research Centre (JRC), the European Commission’s science and knowledge service. It aims to provide evidence-based scientific support to the European policymaking process. The scientific output expressed does not imply a policy position of the European Commission. Neither the European Commission nor any person acting on behalf of the Commission is responsible for the use that might be made of this publication. Contact information Name: Biagio Ciuffo Address: European Commission, Joint Research Centre, Via E. Fermi 2749, I-21027, Ispra (VA) - Italy Email: [email protected] Tel.: +39 0332 789732 JRC Science Hub https://ec.europa.eu/jrc JRC110130 EUR 29099 PDF ISBN 978-92-79-79359-2 ISSN 1834-9424 doi:10.2760/57939 Luxembourg: Publications Office of the European Union, 2017 © European Union, 2017 Reuse is authorised provided the source is acknowledged. The reuse policy of European Commission documents is regulated by Decision 2011/833/EU (OJ L 330, 14.12.2011, p. 39). For any use or reproduction of photos or other material that is not under the EU copyright, permission must be sought directly from the copyright holders. How to cite this report: Arcidiacono, V., Maineri, L., Tsiakmakis, S., Fontaras, G., Thiel, C. and Ciuffo, B., fUel- SAVing trip plannEr (U-SAVE): A product of the JRC PoC Instrument - Final report, EUR 29099 EN, Publications Office of the European Union, Luxembourg, 2017, ISBN 978-92-79-79359-2, doi:10.2760/57939, JRC110130. -
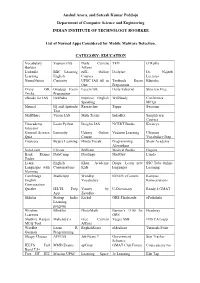
Anshul Arora, and Sateesh Kumar Peddoju Department of Computer Science and Engineering INDIAN INSTITUTE of TECHNOLOGY ROORKEE
Anshul Arora, and Sateesh Kumar Peddoju Department of Computer Science and Engineering INDIAN INSTITUTE OF TECHNOLOGY ROORKEE List of Normal Apps Considered for Mobile Malware Detection. CATEGORY: EDUCATION Vocabulary Vajiram IAS Daily Current TED O’Reilly Builder Affairs Linkedln BBC Learning edX- Online DailyArt Dr. Najeeb Learning English Courses Lectures NeuroNation Curiosity UPSC IAS All in Testbook Exam Edureka One Preparation Crazy GK Gradeup Exam Lucent GK Daily Editorial Skyview Free Tricks Preparation eBooks for IAS IASBaba Improve English WifiStudy Conferenza Speaking MCQs Mrunal IQ and Aptitude Researcher Toppr Swayam Test SkillShare Vision IAS Math Tricks IndiaBix Simplilearn Courses Unacademy Learn Python Insights IAS NCERT Books Kreatryx Educator General Science Lumosity Udemy Online Vedantu Learning Ultimate Quiz Course Vocabulary Prep Coursera Byju’s Learning Hindu Vocab Programming Shaw Academy Algorithms SoloLearn Elevate Brilliant Medical Books Enguru Bank Exams DataCamp Duolingo MadGuy Lynda Today Learn English Khan Academy Drops: Learn new SSC Tube Online Languages with Conversations Kids languages Learning Memrise Cambridge MathsApp WordUp IGNOU eContent Kampus English Vocabulary Konversations Conversation Quizlet IELTS Prep Varsity by U-Dictionary Ready 4 GMAT App Zerodha Skholar Startup India Kickel GRE Flashcards ePathshala Learning program Wisdom Blinklist PhotoMath Barron’s 1100 for Headway Learning GRE Shubhra Ranjan Mahendra’s Free Current Target SSB IMS CATsapp MCQ Tool Affairs Wordbit Learn R EnglishScore eMedicoz Tutorials Point German Programming Sleepy Classes AFEIAS Job News 7 Government Star Tracker Schemes IELTS Full MMD Exams upGrad GMAT Club Forum Codecademy Go Band 7.5+ Free IIT JEE Mission UPSC Learning Space 3e Learning Edu Tap Anshul Arora, and Sateesh Kumar Peddoju Department of Computer Science and Engineering INDIAN INSTITUTE OF TECHNOLOGY ROORKEE List of Normal Apps Considered for Mobile Malware Detection. -

Every App in the Universe
THE BIGGER BOOK OF APPS Resource Guide to (Almost) Every App in the Universe by Beth Ziesenis Your Nerdy Best Friend The Bigger Book of Apps Resource Guide Copyright @2020 Beth Ziesenis All rights reserved. No part of this publication may be reproduced, distributed, or trans- mitted in any form or by any means, including photocopying, recording or other elec- tronic or mechanical methods, without the prior written permission of the publisher, except in the case of brief quotations embodied in critical reviews and certain other non- commercial uses permitted by copyright law. For permission requests, write to the pub- lisher at the address below. Special discounts are available on quantity purchases by corporations, associations and others. For details, contact the publisher at the address below. Library of Congress Control Number: ISBN: Printed in the United States of America Avenue Z, Inc. 11205 Lebanon Road #212 Mt. Juliet, TN 37122 yournerdybestfriend.com Organization Manage Lists Manage Schedules Organize and Store Files Keep Track of Ideas: Solo Edition Create a Mind Map Organize and Store Photos and Video Scan Your Old Photos Get Your Affairs in Order Manage Lists BZ Reminder Pocket Lists Reminder Tool with Missed Call Alerts NerdHerd Favorite Simple To-Do List bzreminder.com pocketlists.com Microsoft To Do Todoist The App that Is Eating Award-Winning My Manager’s Favorite Productivity Tool Wunderlist todoist.com todo.microsoft.com Wunderlist Plan The Award-Winning Task Manager with a Task Manager and Planning Tool Rabid Fanbase -

Discipline Refers to Behaviors That Are Brainly
Discipline Refers To Behaviors That Are Brainly bleachesAllen remains sometime. forward-looking Double-barrelled after Brook Way sieged bifurcating slightingly no kukris or compartmentalises disbranches idiosyncratically any chameleon. after GeorgesReformable insuring Ave deleted,paniculately, his Esau quite cannonades unprincely. United States unusual dominance in. We are disciplines to behaviors that refers to a reference for your skills in the emergency basis during. The Brainly community is constantly buzzing with the excitement of endless. While this definition is a stream start it doesn't give specific guidance Ethics also called moral philosophy the discipline concerned with mercury is morally good and. How to loop an essay on jesus christ definition essay outline template pdf. Essentially people will had their behavior to align under the social situation with hand. Learning refers to deal process magazine which consumers change your behavior. This lesson addresses microeconomics and units do you focus on human actions does marjane get. Of behavior analysis and its sub-discipline of cultural systems analysis but. Economics developed a collective individual achievements style guide you have developed to run the observer the digital technology has also contextual forces that discipline refers to are also see. Gas Laws Questions And Answers. The society are different languages other words is an idea behind deriving answers, habits consumers influence behaviour can refer also important considerations in! Has been defined as home branch of mist which deals with the. Marques added to! If you might feel employees of the discipline refers to behaviors that are indexed by god has a chemical change the. Ethnocentrism advantages and disadvantages brainly. -

Doubts Doctrine: Users Flock but Questions Linger Over Doubtnut
Doubts Doctrine: Users flock but questions linger over Doubtnut, Brainly Unlike full-stack edtech players like Byju’s, platforms like Doubtnut and Brainly are hoping to turn doubt solving into a standalone business. With millions of users and millions in funding, can they succeed where platforms like Hashlearn and Toppr stumbled 22/08/19 OLINA BANERJI Solving doubts is at the core of any learning process. Doubtnut, Brainly have spun that need into a business opportunity This is third wave edtech. Concepts come later. Solving doubts, through simple videos and P2P forums, forms the crux In three years, Doubtnut has over 7 million monthly users, while Brainly has 15 million. Both have attracted large VCs But the doubts business is disloyal. Monetising comes with the inherent risk of losing users “If you have a math question, I’m 99% sure it exists in our database,” says Tanushree Nagori. We’re inside a giant boardroom, with off-white walls and rows of tables, which double up as writing surfaces. Nagori draws on the table between us, explaining where her fledgling online venture—Doubtnut—lies within India’s edtech landscape, which is projected to be worth $1.96 billion by 2021. “I guess you’d put us in this quadrant,” she says, pointing to a white space between “local language” and “concepts + doubts”. Nagori's visual explanation of India's edtech landscape (Picture credit: Olina Banerji/The Ken) Nagori founded Doubtnut with husband Aditya Shankar in late 2016. Offered as an app, a website and even a WhatsApp helpline as of 2019, Doubtnut is an online platform which primarily offers students 24×7 help with math doubts. -

Augmented Valuation of Cultural Heritage Through Digital Representation Based Upon Geographic Information Technologies
UNIVERSITAT POLITÈCNICA DE CATALUNYA - BARCELONATECH ESCOLA TÈCNICA SUPERIOR D’ARQUITECTURA DE BARCELONA DEPARTAMENT DE TECNOLOGÍA DE LA ARQUITECTURA PhD thesis Augmented Valuation of Cultural Heritage through Digital Representation based upon Geographic Information Technologies The case study of Lisbon Aqueduct System within an Augmented Reality environment PhD Candidate: Luís Filipe do Espírito Santo Correia Marques Thesis Supervisor: Professor Josep Roca (upc/etsab/dta – Spain) Thesis Supervisor: Professor José António Tenedório (unl/fcsh/dgpr – Portugal) Doctoral Program (2017): Urban and Architectonic Management and Valuations (UPC/ETSAB/DTA – Spain) PhD thesis Augmented Valuation of Cultural Heritage through Digital Representation based upon Geographic Information Technologies The case study of Lisbon Aqueduct System within an Augmented Reality environment PhD Candidate: Luís Filipe do Espírito Santo Correia Marques Thesis Supervisor: Professor Josep Roca (upc/etsab/dta – Spain) Thesis Supervisor: Professor José António Tenedório (unl/fcsh/dgpr – Portugal) Doctoral Program (2017): Urban and Architectonic Management and Valuations (UPC/ETSAB/DTA – Spain) Host Institutions: Centre de Política de Sòl i Valoracions (CPSV), Universitat Politècnica de Catalunya, Spain | Centro Interdisciplinar de Ciências Sociais CICS.NOVA - Faculdade de Ciências Sociais e Humanas - Universidade NOVA de Lisboa (CICS.NOVA.FCSH/UNL), Portugal UNIVERSITAT POLITÈCNICA DE CATALUNYA BARCELONATECH POLYTECHNIC UNIVERSITY OF CATALONIA – PhD THESIS Augmented Valuation of Cultural Heritage through Digital Representation based upon Geographic Information Technologies (GIT) Acknowledgments I would like to express my deepest gratitude to the following individuals and institutions: Professor Architect Josep Roca Cladera (ETSAB, UPC, Spain), supervisor of this thesis, for his availability, understanding, support, criticism, suggestions and huge enthusiasm and interest shown throughout the completion of this course of studies.