Copyrighted Material
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Active@ UNDELETE Documentation
Active @ UNDELETE Users Guide | Contents | 2 Contents Legal Statement.........................................................................................................5 Active@ UNDELETE Overview............................................................................. 6 Getting Started with Active@ UNDELETE.......................................................... 7 Active@ UNDELETE Views And Windows...................................................................................................... 7 Recovery Explorer View.......................................................................................................................... 8 Logical Drive Scan Result View..............................................................................................................9 Physical Device Scan View......................................................................................................................9 Search Results View...............................................................................................................................11 File Organizer view................................................................................................................................ 12 Application Log...................................................................................................................................... 13 Welcome View........................................................................................................................................14 Using -

RAID, LVM, WSS, Verschlüsselung)
Hochschule Wismar University of Applied Sciences Technology, Business and Design Fakultät für Ingenieurwissenschaften, Bereich EuI Projektarbeit Aufbereitung besonderer Speicherkonfigurationen als analysefähiges Material (RAID, LVM, WSS, Verschlüsselung) Eingereicht am: 6. Juli 2019 von: Melanie Wetzig Sven Lötgering Tom Gertenbach Stefan Depping Inhaltsverzeichnis Inhaltsverzeichnis 1 Vorüberlegungen4 1.1 Motivation und Zielstellung.......................4 1.2 Anforderung an den Ermittlungsprozess.................4 1.3 Einordnung in Ermittlungsprozess....................6 1.4 Write-Blocker...............................6 1.5 Software..................................7 1.5.1 Rohdatenformat (RAW).....................7 1.5.2 Expert Witness Format (EWF).................8 1.5.3 Advanced Forensic Format (AFF)................8 1.5.4 Xmount..............................8 2 Rechtliche Betrachtung9 2.1 Einleitung.................................9 2.2 Private Ermittlungen........................... 10 2.3 Behördliche Ermittlungen........................ 11 2.4 Zusammenfassung............................. 11 3 Speichermedien 13 3.1 Einleitung................................. 13 3.2 Magnetspeicher.............................. 13 3.2.1 Speicherung auf einer HDD................... 14 3.2.2 Löschen von Daten auf einer HDD............... 15 3.2.3 Forensische Relevanz....................... 15 3.3 Flash-Speicher............................... 15 3.3.1 Speicherung auf einer Solid-State-Drive (SSD)......... 16 3.3.2 Löschen von Daten auf einer SSD............... -

SLDXA /T /L1 – SLX Component List
SLDXA /T /L1 – SLX Component List SLDXA.exe ver 1.0 Copyright (c) 2004-2006 SJJ Embedded Micro Solutions, LLC All Rights Reserved SLXDiffC.exe ver 2.0 / SLXtoTXTC.exe ver 2.0 www.sjjmicro.com Processing... File1 to TXT file. Opening XSL File Reading RTF for final conversion F:\SLXTEST\LOCKDOWN_DEMO2.SLX has the following Components Total Count is: 577 -------------------------------------------------- .NET Framework 1.1 - Security Update KB887998 Accessibility Control Panel Accessibility Core ACPI Fixed Feature Button Active Directory Service Interface (ADSI) Core Active Directory Service Interface (ADSI) LDAP Provider Active Directory Service Interface (ADSI) Windows NT Provider Active Template Library (ATL) Add Hardware Control Panel Add/Remove Programs Control Panel Administration Support Tools Administrator Account Advanced Configuration and Power Interface (ACPI) PC Analog TV Application Compatibility Core Audio Codecs Audio Control Panel Base Component Base Performance Counters Base Support Binaries CD-ROM Drive Certificate Request Client & Certificate Autoenrollment Certificate User Interface Services Class Install Library - Desk Class Install Library - Mdminst Class Install Library - Mmsys Class Install Library - Msports Class Install Library - Netcfgx Class Install Library - Storprop Class Install Library - System Devices Class Installer - Computer Class Installer - Disk drives Class Installer - Display adapters Class Installer - DVD/CD-ROM drives Class Installer - Floppy disk controllers Class Installer - Floppy disk drives -

Active @ UNDELETE Users Guide | TOC | 2
Active @ UNDELETE Users Guide | TOC | 2 Contents Legal Statement..................................................................................................4 Active@ UNDELETE Overview............................................................................. 5 Getting Started with Active@ UNDELETE........................................................... 6 Active@ UNDELETE Views And Windows......................................................................................6 Recovery Explorer View.................................................................................................... 7 Logical Drive Scan Result View.......................................................................................... 7 Physical Device Scan View................................................................................................ 8 Search Results View........................................................................................................10 Application Log...............................................................................................................11 Welcome View................................................................................................................11 Using Active@ UNDELETE Overview................................................................. 13 Recover deleted Files and Folders.............................................................................................. 14 Scan a Volume (Logical Drive) for deleted files..................................................................15 -

Veeam Backup 7 Release Notes
VEEAM BACKUP & REPLICATION 7.0 RELEASE NOTES This Release Notes document provides last-minute information about Veeam Backup & Replication 7.0, including system requirements, installation and upgrade procedure, as well as relevant information on technical support, documentation, online resources and so on. The current version of Veeam Backup & Replication 7.0 is available for download at: http://www.veeam.com/vmware-esx-backup/download.html starting from August 15, 2013. See next: • System Requirements • Known Issues • Installing Veeam Backup & Replication • Uninstalling Veeam Backup & Replication • Upgrading Veeam Backup & Replication • Licensing • Updating Veeam Backup & Replication License • Technical Documentation References • Technical Support • Contacting Veeam Software 1 | Veeam Backup & Replication 7.0.0.690 | RELEASE NOTES System Requirements VMware Infrastructure Platforms • vSphere 5.0, 5.1 • vSphere 4.x • Infrastructure 3.5 (VI3.5) Hosts • ESXi 5.0, 5.1 • ESX(i) 4.x • ESX(i) 3.5 Software • vCenter Server 5.0, 5.1 (optional) • vCenter Server 4.x (optional) • Virtual Center 2.5 (optional) VMware Virtual Machines Virtual Hardware • All types of virtual hardware are supported. • Virtual machines with disks engaged in SCSI bus sharing are not supported, because VMware does not support snapshotting such VMs. • RDM virtual disks in physical mode, Independent disks and disks connected via in-guest iSCSI initiator are not supported, and are skipped from processing automatically. OS • All operating systems supported by VMware. • Application-aware -

Jim Allchin on Longhorn, Winfs, 64-Bit and Beyond Page 34 Jim
0805red_cover.v5 7/19/05 2:57 PM Page 1 4 Scripting Solutions to Simplify Your Life Page 28 AUGUST 2005 WWW.REDMONDMAG.COM MrMr WindowsWindows Jim Allchin on Longhorn, WinFS, 64-Bit and Beyond Page 34 > $5.95 05 • AUGUST Make Room for Linux Apps Page 43 25274 867 27 Active Directory Design Disasters Page 49 71 Project1 6/16/05 12:36 PM Page 1 Exchange Server stores & PSTs driving you crazy? Only $399 for 50 mailboxes; $1499 for unlimited mailboxes! Archive all mail to SQL and save 80% storage space! Email archiving solution for internal and external email Download your FREE trial from www.gfi.com/rma Project1 6/16/05 12:37 PM Page 2 Get your FREE trial version of GFI MailArchiver for Exchange today! GFI MailArchiver for Exchange is an easy-to-use email archiving solution that enables you to archive all internal and external mail into a single SQL database. Now you can provide users with easy, centralized access to past email via a web-based search interface and easily fulfill regulatory requirements (such as the Sarbanes-Oxley Act). GFI MailArchiver leverages the journaling feature of Exchange Server 2000/2003, providing unparalleled scalability and reliability at a competitive cost. GFI MailArchiver for Exchange features Provide end-users with a single web-based location in which to search all their past email Increase Exchange performance and ease backup and restoration End PST hell by storing email in SQL format Significantly reduce storage requirements for email by up to 80% Comply with Sarbanes-Oxley, SEC and other regulations. -

Acronis® Disk Director® 12 User's Guide
User Guide Copyright Statement Copyright © Acronis International GmbH, 2002-2015. All rights reserved. "Acronis", "Acronis Compute with Confidence", "Acronis Recovery Manager", "Acronis Secure Zone", Acronis True Image, Acronis Try&Decide, and the Acronis logo are trademarks of Acronis International GmbH. Linux is a registered trademark of Linus Torvalds. VMware and VMware Ready are trademarks and/or registered trademarks of VMware, Inc. in the United States and/or other jurisdictions. Windows and MS-DOS are registered trademarks of Microsoft Corporation. All other trademarks and copyrights referred to are the property of their respective owners. Distribution of substantively modified versions of this document is prohibited without the explicit permission of the copyright holder. Distribution of this work or derivative work in any standard (paper) book form for commercial purposes is prohibited unless prior permission is obtained from the copyright holder. DOCUMENTATION IS PROVIDED "AS IS" AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. Third party code may be provided with the Software and/or Service. The license terms for such third-parties are detailed in the license.txt file located in the root installation directory. You can always find the latest up-to-date list of the third party code and the associated license terms used with the Software and/or Service at http://kb.acronis.com/content/7696 Acronis patented technologies Technologies, used in this product, are covered and protected by one or more U.S. -

Federal Implementation Guideline for Electronic Data Interchange
NIST RESEARCH LIBRARY NIST Special Publication 881-38 APR 6 " 1998 Federal Implementation Guideline for Electronic Data Interchange ASC X12 Version/Release 003070 FEDERAL CONVENTIONS FOR USING ASC XI 2 TRANSACTION SETS Implementation Convention Nisr U.S. DEPARTMENT OF COMMERCE Technology Administration National Institute of Standards and Technology rhe National Institute of Standards and Technology was established in 1988 by Congress to "assist industry in the development of technology . , . needed to improve product quality, to modernize manufacturing processes, to ensure product reliability . and to facilitate rapid commercialization ... of products based on new scientific discoveries." NIST, originally founded as the National Bureau of Standards in 1901, works to strengthen U.S. industry's competitiveness; advance science and engineering; and improve public health, safety, and the environment. One of the agency's basic functions is to develop, maintain, and retain custody of the national standards of measurement, and provide the means and methods for comparing standards used in science, engineering, manufacturing, commerce, industry, and education with the standards adopted or recognized by the Federal Government. As an agency of the U.S. Commerce Department's Technology Administration, NIST conducts basic and applied research in the physical sciences and engineering, and develops measurement techniques, test methods, standards, and related services. The Institute does generic and precompetitive work on new and advanced technologies. -
![Drobo Dashboard Release Notes Release Date: May 14, 2013 VERSION INFORMATION Drobo Dashboard: Version 2.5.2 [64171] (Mac) Version 2.5.2 [64171] (Windows)](https://docslib.b-cdn.net/cover/6977/drobo-dashboard-release-notes-release-date-may-14-2013-version-information-drobo-dashboard-version-2-5-2-64171-mac-version-2-5-2-64171-windows-1076977.webp)
Drobo Dashboard Release Notes Release Date: May 14, 2013 VERSION INFORMATION Drobo Dashboard: Version 2.5.2 [64171] (Mac) Version 2.5.2 [64171] (Windows)
Drobo Dashboard Release Notes Release Date: May 14, 2013 VERSION INFORMATION Drobo Dashboard: Version 2.5.2 [64171] (Mac) Version 2.5.2 [64171] (Windows) KEY HIGHLIGHTS This is a new release version of Drobo Dashboard for Mac and Windows. Key highlights of this release are: This version of Drobo Dashboard is compatible with all Drobo models - Drobo Gen 2, Drobo FS, Drobo S, DroboPro, DroboPro FS, B800fs, DroboElite, B800i, B1200i, Drobo 5D, Drobo Mini and Drobo 5N. Fixed iSCSI connectivity issues due to Java update on Mac OSX 10.8.x hosts Localization improvements Fixed unexpected quit on Mac OSX 10.8.x hosts KNOWN ISSUES All Operating Systems Symptom: Attempting to install multiple versions of Drobo Dashboard at the same time, will fail. Condition: Installing a different (newer or older) Drobo Dashboard version over the existing Drobo Dashboard version installed on the host system, will overwrite the existing version. Workaround: Always use the latest supported version of Drobo Dashboard. Symptom: Attempting to log in with an incorrect iSCSI CHAP password will return generic error. Condition: When logging in a volume with an incorrect CHAP password, Drobo Dashboard will report “Operation failed” error. Workaround: Enter the correct password. If you do not remember the correct password, you can reset the password by logging in as administrator in Drobo Dashboard, disabling CHAP password and re-enabling CHAP password by entering a new value in the password field. Symptom: Formatting volumes when connected to Drobo B1200i via the management port is not available. Condition: When connected to Drobo B1200i via the management port, Drobo Dashboard can be used for changing device settings and creating or deleting volumes. -
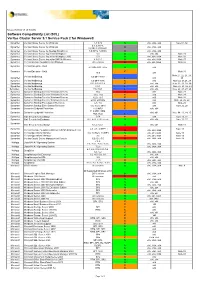
Wxrt VCS for Windows 5.1 SCL Based GA Version
Release Revision 1.6 25 Oct 2012 Software Compatibility List (SCL) Veritas Cluster Server 5.1 Service Pack 2 for Windows® Symantec Veritas Cluster Server for Windows 5.1 SP2 S x86, IA64, x64 Note 01, 02 5.1, 5.1AP1, Symantec Veritas Cluster Server for Windows U x86, IA64, x64 5.1SP1,5.1SP1AP1 Symantec Veritas Cluster Server for NetApp SnapMirror 5.0 RP1a, 5.0RP2 U x86, IA64, x64 Symantec Veritas Cluster Server Agent for Websphere 5.1 S x86, x64 Note 05 Symantec Veritas Cluster Server Agent for Websphere MQ 5.0 S x86, x64, IA64 Note 06 Symantec Veritas Cluster Server Agent for SAP NetWeaver 4.3.01.0 S x86, x64, IA64 Note 07 Symantec Veritas Storage Foundation for Windows All versions X x86, x64, IA64 Note 02 Symantec Veritas Enterprise Vault 8.0 SP1-SP5, 9.0.x S x86 Symantec Veritas Enterprise Vault C Note 31 10.0 x86 Note 21, 22, 23, 28, Veritas NetBackup 6.0 MP1-MP3 Symantec L x86 29 Symantec Veritas NetBackup 6.0 MP4-MP6 C x86 Note 22, 23,28, 29 Symantec Veritas NetBackup 6.5, 6.5.2-6.5.4 C x86, x64 Note 22, 23, 28, 29 Symantec Veritas NetBackup 6.5.1 L x86, x64 Note 22, 23, 28, 29 Symantec Veritas NetBackup 7.0, 7.0.1 L x86, x64 Note 22, 23, 27, 28 Symantec Symantec Backup Exec for Windows Servers 10.x X x86 Note 28 Symantec Symantec Backup Exec for Windows Servers 11.0, 11d C x86 Note 28 Symantec Symantec Backup Exec for Windows Servers 12.0, 12.5 C x86 Note 28 Symantec Symantec Backup Exec for Windows Servers 2010, 2010 R2 L x86 Note 24, 25, 28 Symantec Symantec Backup Exec System Recovery 6.5, 7.0 C x86 Note 28 Symantec Symantec -

AIX V4.3 and Windows 2000, Side by Side
AIX V4.3 and Windows 2000, Side by Side Laurent Vanel, Leonardo Antonelli, Angela Keelan, Miha Music International Technical Support Organization www.redbooks.ibm.com SG24-4784-01 SG24-4784-01 International Technical Support Organization AIX V4.3 and Windows 2000, Side by Side April 2000 Take Note! Before using this information and the product it supports, be sure to read the general information in Appendix A, “Special notices” on page 521. Second Edition (April 2000) This edition applies to AIX Version 4.3.3, Program Number 5765-C34. This document was created or updated on April 14, 2000. Comments may be addressed to: IBM Corporation, International Technical Support Organization Dept. JN9B Building 003 Internal Zip 2834 11400 Burnet Road Austin, Texas 78758-3493 When you send information to IBM, you grant IBM a non-exclusive right to use or distribute the information in any way it believes appropriate without incurring any obligation to you. © Copyright International Business Machines Corporation 2000. All rights reserved. Note to U.S Government Users – Documentation related to restricted rights – Use, duplication or disclosure is subject to restrictions set forth in GSA ADP Schedule Contract with IBM Corp. Contents Figures....................................................ix Tables....................................................xv Preface.................................................. xvii The team that wrote this redbook. ................................. xvii Commentswelcome............................................xviii -

Spectrum Reference Manual
Apple® IIGS Spectrum™ 2.5.6 Reference Manual Notes on Freeware Edition From an initial inception as a IIgs communications program called Impala, Spectrum was developed and released under the guidance of Dave Hecker of Seven Hills International. Originally released back in 1991, it was sold by Seven Hills until their eventual closure. Seven Hills agreed I could continue to sell Spectrum, so I asked Eric Shepherd of Syndicomm to sell Spectrum on my behalf. In 2011 Tony Diaz took over Syndicomm and continued to sell it for me. With the declining sales over the years, I finally decided that the time had come in 2012 to make Spectrum Freeware. To coincide with its reclassification, this PDF manual has been compiled from the original Seven Hills manuals. I have changed a few words and links here and there, and added new screen shots and illustrations. Ewen Wannop - 2012 2 Spectrum About Seven Hills Software No Copy Protection We don’t believe in copy protection—all it does is impair the honest user’s ability to use software to its fullest. We strive to provide high quality products at reasonable prices. We hope you will support our efforts by not allowing your family or friends to copy this software. Questions and Comments We always welcome feedback—if you have any questions, or suggestions for improving this product, please let us know. In addition, we would like to hear your ideas for new programs. Copyrights and Trademarks This manual and the software (computer program) described in it are copyrighted with all rights reserved.