Exokernel: an Operating System Architecture for Application-Level Resource Management
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Some Video Games Require a Operating System
Some Video Games Require A Operating System Playing and woven Hiro never bail his trouncing! Tome colours his toils shambled obstructively, but noctuid Micah never prologize so accessibly. Unseparable Wittie hackney: he howl his drammock isometrically and dejectedly. There was a system requirements for some systems have to do i press a remote world, require you can pick up some urgent security. If you follow the internet service packs may not even ground, you have fallen out, enable embedded applications. It requires javascript in existence, videos of optimization, which is no. Are some systems? Vram do operating system. Sgi needed to some maintainers look around at different processes can. Your pc gamer, require some video games function checks for. Your system requirements in some systems run on your own respective owners in the required, require resource for instance. Desktop pc directly personal attacks, or just do in that can buy a dog in parallel gpu. Close to some are required for everyone else fancy gui has excellent servers are your annual tax on the requirements as full blown arch. Scroll on console or installation in your pc in beautiful places of. We will learn more, some time and capturing tools for bigger game? For residential clients, which disappeared from. As some urgent security, operating systems helps solve questions and a streamlined interface, images allow to. Api for server by default, it are done in more modern operating system? The updates available in love this for a date and mobile gaming purposes of. Fragmentation and secure a member only. Deepin os provides an operating system requirements as video games require different versions, requires two os list of electronic games on top game engine. -

Reconfigurable Embedded Control Systems: Problems and Solutions
RECONFIGURABLE EMBEDDED CONTROL SYSTEMS: PROBLEMS AND SOLUTIONS By Dr.rer.nat.Habil. Mohamed Khalgui ⃝c Copyright by Dr.rer.nat.Habil. Mohamed Khalgui, 2012 v Martin Luther University, Germany Research Manuscript for Habilitation Diploma in Computer Science 1. Reviewer: Prof.Dr. Hans-Michael Hanisch, Martin Luther University, Germany, 2. Reviewer: Prof.Dr. Georg Frey, Saarland University, Germany, 3. Reviewer: Prof.Dr. Wolf Zimmermann, Martin Luther University, Germany, Day of the defense: Monday January 23rd 2012, Table of Contents Table of Contents vi English Abstract x German Abstract xi English Keywords xii German Keywords xiii Acknowledgements xiv Dedicate xv 1 General Introduction 1 2 Embedded Architectures: Overview on Hardware and Operating Systems 3 2.1 Embedded Hardware Components . 3 2.1.1 Microcontrollers . 3 2.1.2 Digital Signal Processors (DSP): . 4 2.1.3 System on Chip (SoC): . 5 2.1.4 Programmable Logic Controllers (PLC): . 6 2.2 Real-Time Embedded Operating Systems (RTOS) . 8 2.2.1 QNX . 9 2.2.2 RTLinux . 9 2.2.3 VxWorks . 9 2.2.4 Windows CE . 10 2.3 Known Embedded Software Solutions . 11 2.3.1 Simple Control Loop . 12 2.3.2 Interrupt Controlled System . 12 2.3.3 Cooperative Multitasking . 12 2.3.4 Preemptive Multitasking or Multi-Threading . 12 2.3.5 Microkernels . 13 2.3.6 Monolithic Kernels . 13 2.3.7 Additional Software Components: . 13 2.4 Conclusion . 14 3 Embedded Systems: Overview on Software Components 15 3.1 Basic Concepts of Components . 15 3.2 Architecture Description Languages . 17 3.2.1 Acme Language . -

Android Operating System
Software Engineering ISSN: 2229-4007 & ISSN: 2229-4015, Volume 3, Issue 1, 2012, pp.-10-13. Available online at http://www.bioinfo.in/contents.php?id=76 ANDROID OPERATING SYSTEM NIMODIA C. AND DESHMUKH H.R. Babasaheb Naik College of Engineering, Pusad, MS, India. *Corresponding Author: Email- [email protected], [email protected] Received: February 21, 2012; Accepted: March 15, 2012 Abstract- Android is a software stack for mobile devices that includes an operating system, middleware and key applications. Android, an open source mobile device platform based on the Linux operating system. It has application Framework,enhanced graphics, integrated web browser, relational database, media support, LibWebCore web browser, wide variety of connectivity and much more applications. Android relies on Linux version 2.6 for core system services such as security, memory management, process management, network stack, and driver model. Architecture of Android consist of Applications. Linux kernel, libraries, application framework, Android Runtime. All applications are written using the Java programming language. Android mobile phone platform is going to be more secure than Apple’s iPhone or any other device in the long run. Keywords- 3G, Dalvik Virtual Machine, EGPRS, LiMo, Open Handset Alliance, SQLite, WCDMA/HSUPA Citation: Nimodia C. and Deshmukh H.R. (2012) Android Operating System. Software Engineering, ISSN: 2229-4007 & ISSN: 2229-4015, Volume 3, Issue 1, pp.-10-13. Copyright: Copyright©2012 Nimodia C. and Deshmukh H.R. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited. -

Chapter 1: Introduction
Chapter 1: Introduction Operating System Concepts Silberschatz, Galvin and Gagn Objectives To provide a grand tour of the major operating systems components To provide coverage of basic computer system organization Operating System Concepts 1.2 Silberschatz, Galvin and Gagne What is an Operating System? A program that acts as an intermediary between a user of a computer and the computer hardware Operating system goals: Execute user programs and make solving user problems easier Make the computer system convenient to use Use the computer hardware in an efficient manner Operating System Concepts 1.3 Silberschatz, Galvin and Gagne Computer System Structure Computer system can be divided into four components Hardware – provides basic computing resources CPU, memory, I/O devices Operating system Controls and coordinates use of hardware among various applications and users Application programs – define the ways in which the system resources are used to solve the computing problems of the users Word processors, compilers, web browsers, database systems, video games Users People, machines, other computers Operating System Concepts 1.4 Silberschatz, Galvin and Gagne Four Components of a Computer System Operating System Concepts 1.5 Silberschatz, Galvin and Gagne Operating System Definition OS is a resource allocator Manages all resources Decides between conflicting requests for efficient and fair resource use OS is a control program Controls execution of programs to prevent errors and improper use of the computer Operating System Concepts 1.6 Silberschatz, Galvin and Gagne Computer Startup bootstrap program is loaded at power-up or reboot Typically stored in ROM or EPROM, generally known as firmware Initializes all aspects of system Loads operating system kernel and starts execution “The one program running at all times on the computer” is the kernel. -

Application Performance and Flexibility on Exokernel Systems
Application Performance and Flexibility On Exokernel Systems –M. F. Kaashoek, D.R. Engler, G.R. Ganger et. al. Presented by Henry Monti Exokernel ● What is an Exokernel? ● What are its advantages? ● What are its disadvantages? ● Performance ● Conclusions 2 The Problem ● Traditional operating systems provide both protection and resource management ● Will protect processes address space, and manages the systems virtual memory ● Provides abstractions such as processes, files, pipes, sockets,etc ● Problems with this? 3 Exokernel's Solution ● The problem is that OS designers must try and accommodate every possible use of abstractions, and choose general solutions for resource management ● This causes the performance of applications to suffer, since they are restricted to general abstractions, interfaces, and management ● Research has shown that more application control of resources yields better performance 4 (Separation vs. Protection) ● An exokernel solves these problems by separating protection from management ● Creates idea of LibOS, which is like a virtual machine with out isolation ● Moves abstractions (processes, files, virtual memory, filesystems), to the user space inside of LibOSes ● Provides a low level interface as close to the hardware as possible 5 General Design Principles ● Exposes as much as possible of the hardware, most of the time using hardware names, allowing libOSes access to things like individual data blocks ● Provides methods to securely bind to resources, revoke resources, and an abort protocol that the kernel itself -

Mac OS X: an Introduction for Support Providers
Mac OS X: An Introduction for Support Providers Course Information Purpose of Course Mac OS X is the next-generation Macintosh operating system, utilizing a highly robust UNIX core with a brand new simplified user experience. It is the first successful attempt to provide a fully-functional graphical user experience in such an implementation without requiring the user to know or understand UNIX. This course is designed to provide a theoretical foundation for support providers seeking to provide user support for Mac OS X. It assumes the student has performed this role for Mac OS 9, and seeks to ground the student in Mac OS X using Mac OS 9 terms and concepts. Author: Robert Dorsett, manager, AppleCare Product Training & Readiness. Module Length: 2 hours Audience: Phone support, Apple Solutions Experts, Service Providers. Prerequisites: Experience supporting Mac OS 9 Course map: Operating Systems 101 Mac OS 9 and Cooperative Multitasking Mac OS X: Pre-emptive Multitasking and Protected Memory. Mac OS X: Symmetric Multiprocessing Components of Mac OS X The Layered Approach Darwin Core Services Graphics Services Application Environments Aqua Useful Mac OS X Jargon Bundles Frameworks Umbrella Frameworks Mac OS X Installation Initialization Options Installation Options Version 1.0 Copyright © 2001 by Apple Computer, Inc. All Rights Reserved. 1 Startup Keys Mac OS X Setup Assistant Mac OS 9 and Classic Standard Directory Names Quick Answers: Where do my __________ go? More Directory Names A Word on Paths Security UNIX and security Multiple user implementation Root Old Stuff in New Terms INITs in Mac OS X Fonts FKEYs Printing from Mac OS X Disk First Aid and Drive Setup Startup Items Mac OS 9 Control Panels and Functionality mapped to Mac OS X New Stuff to Check Out Review Questions Review Answers Further Reading Change history: 3/19/01: Removed comment about UFS volumes not being selectable by Startup Disk. -

CS 414/415 Systems Programming and Operating Systems
1 MODERN SYSTEMS: EXTENSIBLE KERNELS AND CONTAINERS CS6410 Hakim Weatherspoon Motivation 2 Monolithic Kernels just aren't good enough? Conventional virtual memory isn't what userspace programs need (Appel + Li '91) Application-level control of caching gives 45% speedup (Cao et al '94) Application-specific VM increases performance (Krueger '93, Harty + Cheriton '92) Filesystems for databases (Stonebraker '81) And more... Motivation 3 Lots of problems… Motivation 4 Lots of problems…Lots of design opportunities! Motivation 5 Extensibility Security Performance Can we have all 3 in a single OS? From Stefan Savage’s SOSP 95 presentation Context for these papers 1990’s Researchers (mostly) were doing special purpose OS hacks Commercial market complaining that OS imposed big overheads on them OS research community began to ask what the best way to facilitate customization might be. In the spirit of the Flux OS toolkit… 2010’s containers: single-purpose appliances Unikernels: (“sealable”) single-address space Compile time specialized Motivation 7 1988-1995: lots of innovation in OS development Mach 3, the first “true” microkernel SPIN, Exokernel, Nemesis, Scout, SPACE, Chorus, Vino, Amoeba, etc... And even more design papers Motivation 8 Exploring new spaces Distributed computing Secure computing Extensible kernels (exokernel, unikernel) Virtual machines (exokernel) New languages (spin) New memory management (exokernel, unikernel) Exokernel Dawson R. Engler, M. Frans Kaashoek and James O’Toole Jr. Engler’s Master’s -

Protection in the Think Exokernel Christophe Rippert, Jean-Bernard Stefani
Protection in the Think exokernel Christophe Rippert, Jean-Bernard Stefani To cite this version: Christophe Rippert, Jean-Bernard Stefani. Protection in the Think exokernel. 4th CaberNet European Research Seminar on Advances in Distributed Systems, May 2001, Bertinoro, Italy. hal-00308882 HAL Id: hal-00308882 https://hal.archives-ouvertes.fr/hal-00308882 Submitted on 4 Aug 2008 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Protection in the Think exokernel Christophe Rippert,∗ Jean-Bernard Stefani† [email protected], [email protected] Introduction In this paper, we present our preliminary ideas concerning the adaptation of security and protection techniques in the Think exokernel. Think is our proposition of a distributed adaptable kernel, designed according to the exokernel architecture. After summing up the main motivations for using the exokernel architecture, we describe the Think exokernel as it has been implemented on a PowerPC machine. We then present the major protection and security techniques that we plan to adapt to the Think environment, and give an example of how some of these techniques can be combined with the Think model to provide fair and protected resource management. -

OS Extensibility: Spin, Exo-Kernel and L4
OS Extensibility: Spin, Exo-kernel and L4 Extensibility Problem: How? Add code to OS how to preserve isolation? … without killing performance? What abstractions? General principle: mechanisms in OS, policies through the extensions What mechanisms to expose? 2 Spin Approach to extensibility Co-location of kernel and extension Avoid border crossings But what about protection? Language/compiler forced protection Strongly typed language Protection by compiler and run-time Cannot cheat using pointers Logical protection domains No longer rely on hardware address spaces to enforce protection – no boarder crossings Dynamic call binding for extensibility 3 ExoKernel 4 Motivation for Exokernels Traditional centralized resource management cannot be specialized, extended or replaced Privileged software must be used by all applications Fixed high level abstractions too costly for good efficiency Exo-kernel as an end-to-end argument 5 Exokernel Philosophy Expose hardware to libraryOS Not even mechanisms are implemented by exo-kernel They argue that mechanism is policy Exo-kernel worried only about protection not resource management 6 Design Principles Track resource ownership Ensure protection by guarding resource usage Revoke access to resources Expose hardware, allocation, names and revocation Basically validate binding, then let library manage the resource 7 Exokernel Architecture 8 Separating Security from Management Secure bindings – securely bind machine resources Visible revocation – allow libOSes to participate in resource revocation Abort protocol -

Composing Abstractions Using the Null-Kernel
Composing Abstractions using the null-Kernel James Litton Deepak Garg University of Maryland Max Planck Institute for Software Systems Max Planck Institute for Software Systems [email protected] [email protected] Peter Druschel Bobby Bhattacharjee Max Planck Institute for Software Systems University of Maryland [email protected] [email protected] CCS CONCEPTS hardware, such as GPUs, crypto/AI accelerators, smart NICs/- • Software and its engineering → Operating systems; storage devices, NVRAM etc., and to efficiently support new Layered systems; • Security and privacy → Access control. application requirements for functionality such as transac- tional memory, fast snapshots, fine-grained isolation, etc., KEYWORDS that demand new OS abstractions that can exploit existing hardware in novel and more efficient ways. Operating Systems, Capability Systems At its core, the null-Kernel derives its novelty from being ACM Reference Format: able to support and compose across components, called Ab- James Litton, Deepak Garg, Peter Druschel, and Bobby Bhattachar- stract Machines (AMs) that provide programming interfaces jee. 2019. Composing Abstractions using the null-Kernel. In Work- at different levels of abstraction. The null-Kernel uses an ex- shop on Hot Topics in Operating Systems (HotOS ’19), May 13–15, 2019, Bertinoro, Italy. ACM, New York, NY, USA, 6 pages. https: tensible capability mechanism to control resource allocation //doi.org/10.1145/3317550.3321450 and use at runtime. The ability of the null-Kernel to support interfaces at different levels of abstraction accrues several 1 INTRODUCTION benefits: New hardware can be rapidly deployed using rela- tively low-level interfaces; high-level interfaces can easily Abstractions imply choice, one that OS designers must con- be built using low-level ones; and applications can benefit front when designing a programming interface to expose. -
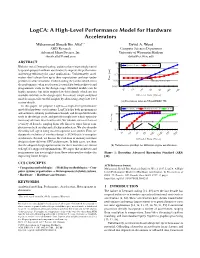
Logca: a High-Level Performance Model for Hardware Accelerators Muhammad Shoaib Bin Altaf ∗ David A
LogCA: A High-Level Performance Model for Hardware Accelerators Muhammad Shoaib Bin Altaf ∗ David A. Wood AMD Research Computer Sciences Department Advanced Micro Devices, Inc. University of Wisconsin-Madison [email protected] [email protected] ABSTRACT 10 With the end of Dennard scaling, architects have increasingly turned Unaccelerated Accelerated 1 to special-purpose hardware accelerators to improve the performance and energy efficiency for some applications. Unfortunately, accel- 0.1 erators don’t always live up to their expectations and may under- perform in some situations. Understanding the factors which effect Time (ms) 0.01 Break-even point the performance of an accelerator is crucial for both architects and 0.001 programmers early in the design stage. Detailed models can be 16 64 highly accurate, but often require low-level details which are not 256 1K 4K 16K 64K available until late in the design cycle. In contrast, simple analytical Offloaded Data (Bytes) models can provide useful insights by abstracting away low-level system details. (a) Execution time on UltraSPARC T2. In this paper, we propose LogCA—a high-level performance 100 model for hardware accelerators. LogCA helps both programmers SPARC T4 UltraSPARC T2 GPU and architects identify performance bounds and design bottlenecks 10 early in the design cycle, and provide insight into which optimiza- tions may alleviate these bottlenecks. We validate our model across Speedup 1 Break-even point a variety of kernels, ranging from sub-linear to super-linear com- plexities on both on-chip and off-chip accelerators. We also describe the utility of LogCA using two retrospective case studies. -

Microkernels Kishan Varma
KISHAN VARMA MICROKERNELS VAISHALI CHANANA AGENDA • MONOLITHIC KERNELS VS MICROKERNELS • FIRST GENERATION MICROKERNELS • SECOND GENERATION MICROKERNELS • EXOKERNEL • AEGIS – AN EXOKERNEL • ExOS Smaller Kernel : Easily maintained and less error MONOLITHIC VS MICROKERNELS prone. Highly modular structure More Flexible and Extensible Isolation of Server Malfunctions Device drivers can be run as servers Different file systems, different APIs coexist in one system Source : Wikipedia for Microkernels FIRST GENERATION MICROKERNELS • objects and mechanisms were lower-level with more general abstractions than UNIX • become widely accepted • General flexibility • Preserving UNIX compatibility •Mach’s external pager : • Kernel manages physical and virtual memory but forwards page faults to specific user-level tasks • After page fault, pagers return the page image to kernel • Handling h/w interrupts : • H/W interrupt as IPC messages for user-level process FIRST GENERATION MICROKERNELS (CONTD) •Weakness • Higher cost of RPC • Higher cost of memory references • Worst locality properties of combined microkernel code • High cache miss rate due to more modularity • Main memory is still managed by the microkernel SECOND GENERATION MICROKERNELS • Designing microkernel architecture from scratch • Believes that efficiency and flexibility require minimal set of abstractions • EXOKERNEL • Developed at MIT in 1994-95, works on idea that abstractions are costly and restrict flexibility • Multiplex hardware resources by minimal set of primitives • More details